Risky Bulletin Newsletter
October 13, 2025
Risky Bulletin: Microsoft revamps Edge's "IE Mode" after zero-day attacks
Written by

News Editor
This newsletter is brought to you by Nebulock . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
A mysterious threat actor is abusing the legacy Internet Explorer mode in Microsoft Edge to run malicious code in a user's browser and take over their device.
The attacks have been going on since at least August, according to the Microsoft Edge security team .
The Internet Explorer legacy mode, or IE Mode, is a separate website execution environment in Edge. It works by reloading a web page but running its code inside the old Internet Explorer engines.
Microsoft added IE mode to Edge after it retired its former web browser. It allowed old websites and government portals coded decades ago to still render and work for Edge users after Microsoft stop shipping IE with recent Windows releases.
The mode doesn't run by default, and users must press a button or menu option to reload the page from Edge into the old IE execution environment.
Microsoft says it received " credible " reports that hackers were using clones of legitimate websites to instruct users to reload the clones in the Edge IE Mode, where they ran an exploit chain targeting the old Chakra JavaScript engine that was used in older versions of IE and Edge.
The exploit chain contained a Chakra zero-day that allowed them to run malicious code, and a second exploit to elevate privileges and take over the entire user platform.
Microsoft did not share a CVE or did not release a patch, but instead overhauled the entire IE Mode.
The Edge security team has now completely removed all the dedicated buttons that could refresh and relaunch a website in IE Mode. This includes the dedicated toolbar button, the context menu option, and the hamburger (main) menu item.
Users who want to relaunch a website in IE Mode will now have to go into the browser's settings and specifically enable the feature from there, relaunch their browser, and then manually add the URL of a website to an allowlist of sites permitted to be reloaded in IE Mode.
Microsoft believes the extra steps to enable IE Mode should now give users more chances to spot fake URLs and think twice before enabling it.
Risky Business Podcasts
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about the Clop ransomware gang. It is interesting because the group has arrived at a strategy that rinses a whole lot of enterprises at once and comes with a decent payday. But it's actually the least damaging kind of ransomware. Tom wonders why more gangs can't be like Clop?
Breaches, hacks, and security incidents
Fast Track breach impacts crypto world: Hackers have breached iGaming platform Fast Track and stolen data from two of its customers. The targets were two cryptocurrency casinos, Shuffle and Roobet . Attackers are believed to have made off with names, emails, home addresses, and past bets. The breach took place earlier this month.
Another Paragon victim identified: The CEO of UniCredit, one of Italy's largest banks, was also targeted with Paragon's Graphite spyware, according to Italian media. Andrea Orcel is the second major Italian businessman to have been identified as a victim of spying after Francesco Gaetano Caltagirone , the owner of a major investing and holding company.
Vietnam Airlines data leaked: The Scattered Lapsus$ Hunters group has leaked 7.3 million details from the Vietnam Airlines customer loyalty program. This was taken from the company's Salesforce account.
Qantas Airlines data leak: The same group also leaked customer data from Australia's Qantas Airlines , and several more .
General tech and privacy
Apple introduces age checks in Texas: Apple is introducing age verification checks for Texas users to comply with upcoming state laws. All users under the age of 18 will be required to join a family plan in order to use Apple products. In addition, Apple is releasing age verification tools for its developer ecosystem. The company has published a new Declared Age Range API to help developers ascertain the age of their users and implement their own age verification management systems. Texas' new age verification law enters into effect next year.
Microsoft in trouble in Austria over privacy: Austria's data protection agency has found that Microsoft tracked students via the Microsoft 365 Education for its business purposes, against EU GDPR privacy rules.
YouTube Second Chance program: Google has announced Second Chance , a new program for YouTube content creators that will allow previously banned accounts to request a "second chance" on the platform.
Chrome will revoke old site permissions: Google Chrome will revoke notification permissions for websites that users haven't visited in a while. The decision is meant to reduce notification spam. It is expected to be useful for non-technical users who don't know how to unsubscribe. Google said that internal data shows that websites that send a low volume of notifications usually see increased interaction.
Government, politics, and policy
FCC warns of future crackdown: American retailers have started removing sanctioned Chinese electronic products from their online stores. The move comes days after the FCC warned of upcoming regulations. The agency plans to enforce stricter import controls and ban a larger class of devices and components. [ Additional coverage in Reuters ]
White House rescinds NSA chief nomination: The Trump administration will not nominate Army Lt. Gen. William Hartman for the chief of Cyber Command and the National Security Agency. Gen. Hartman has been acting chief for both agencies since April, when the White House dismissed Air Force General Timothy Haugh from both roles. He emerged as the favorite for the role after gaining the backing of Defense Secretary Pete Hegseth and Director of National Intelligence Tulsi Gabbard. According to The Record , the White House did not go through with the nomination because it wants to split the two roles.
It’s unclear who the administration will now choose for the job. One name is Reid Novotny, who served as director of intelligence & cyber effects operations for the National Guard & is the senior military policy adviser at the Office of the National Cyber Director. therecord.media/william-hart...
— Martin Matishak (@martinmatishak.bsky.social) 2025-10-11T00:57:28.719Z
White House lays off 176 CISA workers: The White House has laid off 176 CISA employees following the shutdown of the US government. The Trump administration fired more than 4,000 workers last week in total. According to NBC News , the DHS was the least affected agency where layoffs took place. Many other CISA workers were also reassigned to help other agencies with immigration enforcement. Those who refused were terminated. This is the Trump admin's third round of CISA layoffs this year.
Sponsor section
In this Risky Business sponsored interview , Tom Uren talks to Damien Lewke, CEO and founder of Nebulock about countering adversary use of AI… with AI. They talk about how threat actors are rapidly adopting AI and what defenders should be doing in response.
Arrests, cybercrime, and threat intel
FBI seizes Salesforce extortion site: The FBI has seized a website that was being used to extort Salesforce and its customers. The site was seized two days before hackers were expected to leak stolen Salesforce data. The site was named after the former BreachForums hacking community and was operated by a group calling itself Scattered Lapsus$ Hunters. Its dark web version is still up. [ Additional coverage in DataBreaches.net ]
Nigerian scammer arrested in Argentina: Argentinian officials have arrested a Nigerian man wanted by Interpol for alleged romance scam operations. Ikechukwu N. is Argentina's first arrest based on an Interpol Red Notice alert. The suspect was also in Interpol's Silver Notice database, a new Interpol project launched this year and aimed at recovering criminal assets. [ Additional coverage in The Guardian Nigeria ]
Another scam compound raided in Cambodia: Cambodian police have raided a cyber scam compound in the country's capital, Phnom Penh. Authorities arrested 76 foreigners and five locals. The group operated out of the Morgan Tower building, a place previously raided for similar crypto scam activity earlier this year . [ Additional coverage in FreshAsiaNews ] [ h/t CyberScamMonitor ]
PowerSchool sentencing: The sentencing of Matthew D. Lane, the man who hacked educational platform PowerSchool, is scheduled for this week, and prosecutors are seeking a seven-year prison sentence. [ Additional coverage in The Record ]
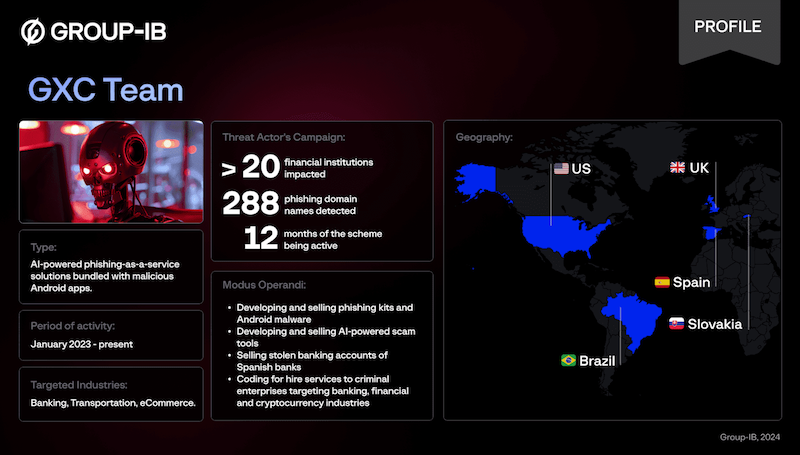
Spain arrests major phishing provider: Spanish authorities have arrested a Brazilian national who was behind a major phishing platform. The 25-year-old suspect went online as GoogleXcoder. He allegedly ran GXC Team , an online phishing service that served the Spanish-speaking cybercrime underground. His phishing-as-a-service platform could bypass 2FA and also came with ready-made Android malware for targeting banks and crypto services. The suspect was living in Spain under a digital nomad visa and constantly moving between homes in different provinces.
RDP attack wave targets US: A massive botnet has launched a coordinated attack on RDP endpoints located in the US. More than 100,000 unique IPs have participated in the attack since October 8. GreyNoise discovered the botnet after noticing an unusual spike in Brazilian internet traffic.
Aisuru gets US-heavy: A major DDoS botnet is now drawing its firepower from hacked IoT devices based in the US. The Aisuru botnet launched in August last year. It was discovered by Chinese security firms after it infected local ISPs and cloud providers. According to KrebsOnSecurity , the botnet has now grown to more than 300,000 infected systems, with most bots located on US networks. Aisuru currently holds the record for the largest DDoS attack ever recorded.
New npm malware: Four hundred forty malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details .
npm abuse: On the same note, Snyk and Socket Security look at a phishing campaign that abuses npm server infrastructure to store malicious payloads.
"Threat actors seeded more than 175+ throwaway packages as disposable hosting for JavaScript that auto-redirects victims to credential-harvesting sites when opened from crafted HTML 'business documents.' According to Socket, who initially shared the news and provided first data points, the targets in this attack span 135+ organizations (industrial, tech, and energy, mainly in Europe)."
Scattered Lapsus$ Hunters profile: Palo Alto Networks has published a profile on the Scattered Lapsus$ Hunters that has recently extorted Salesforce customers. PAN tracks the group as Bling Libra.
New leak site: The Brotherhood group launched a leak site last week. Currently lists only 11 victims. It's also unclear if the group engages in ransomware or just data extortion.
Malware technical reports
ClayRat: A sprawling malware operation is targeting Russian users with a new Android spyware strain. The spyware is distributed using fake versions of popular apps shared via Telegram. Zimperium says it has spotted hundreds of samples and variations over the past three months. The new ClayRat malware can steal SMS messages, call logs, notifications, take pictures, and make phone calls.
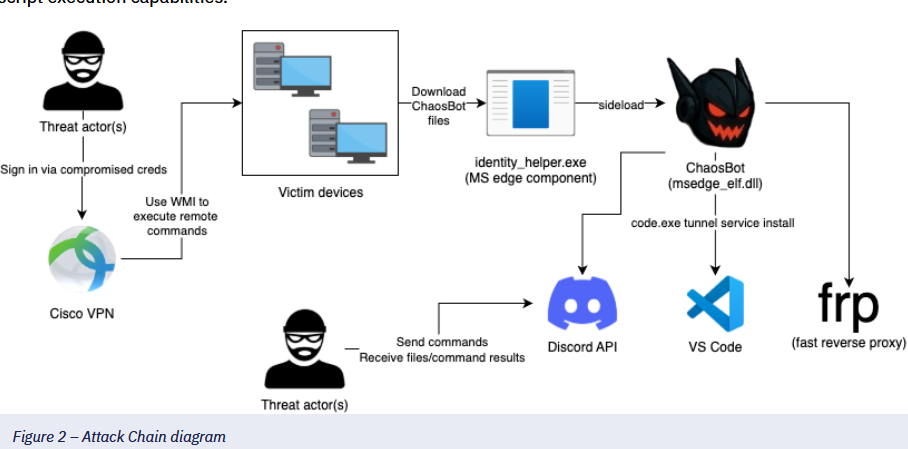
ChaosBot: eSentire has discovered a new Rust-based malware strain named ChaosBot that uses Discord as a command-and-control channel. Most of the ChaosBot victims are based in Vietnam.
Astaroth: McAfee has spotted an Astaroth banking trojan campaign abusing GitHub services as a secondary C&C channel.
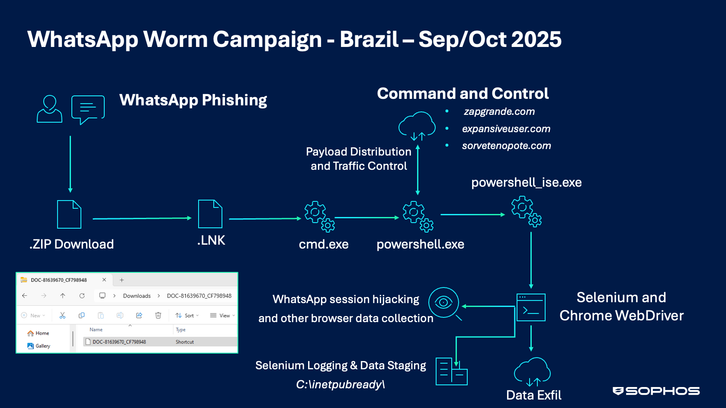
WhatsApp worm: Sophos researchers have taken a look at the WhatsApp worm that has hit Brazilian users over the past two months. Trend Micro published a report on this last week, calling the worm SORVEPOTEL .
Sponsor section
Agentic AI platform Nebulock pitches its product in one of our recent Snakeoilers episodes.
APTs, cyber-espionage, and info-ops
New APT35 leaks: The KittenBusters group has released new files (Episode 3) related to APT35, an Iranian cyber-espionage group. The new files are related to the group's BellaCiao backdoor. According to Hamid Kashfi , the leaked documents suggest the backdoor is still active on more than 300 systems. CloudSEK has published a summary of the leaks , and there's also a Gemini-translated version of the leak available.
OceanLotus: TahirSec has published a report on a recent OceanLotus (APT32) phishing campaign that drops Havoc payloads. This is the same campaign spotted by Qihoo 360 last month.
DPRK IT workers now target architects: North Korean IT workers are seeking remote jobs in the industrial design and architecture fields. Security firm KELA warns that the new pivot raises new concerns of access to sensitive infrastructure designs. It will also allow workers to spy on industrial design and gain access to a new class of tech IP.
Vulnerabilities, security research, and bug bounty
New Gladinet zero-day: Hackers are exploiting a zero-day in Gladinet CentreStack and Triofox file-sharing servers. Attackers are using the zero-day ( CVE-2025-11371 ) to steal the server's cryptographic key, which they later use for deserialization and code execution. Gladinet is aware of the attacks and is working on a patch. This is the second zero-day exploited in Gladinet file-sharing software this year.
Unpatched Ivanti Endpoint Manager bugs: Trend Micro's ZDI has reported 13 vulnerabilities in the Ivanti Endpoint Manager that are still unpatched after the vendor requested an extension until March next year.
OpenSSH RCE: David Leadbeater has published a write-up on an RCE he found in OpenSSH, a bug that could have enabled command injection if ProxyCommand is enabled. This was patched last week as CVE-2025-61984.
Telerik write-up: WatchTowr Labs has published a write-up on CVE-2025-3600, an initial DoS bug in Telerik UI that the company discovered could also be abused for RCE attacks.
Oracle patches new EBS bug: Oracle has released an out-of-band security update to patch a new critical vulnerability in its E-Business Suite platform. The new bug can allow remote attackers to access the platform without authentication. The bug impacts the same platform targeted by an extortion group over the past three months. Oracle didn't say if the bug was exploited.
Google OSV update: Socket security researcher Jonathan Leitschuh has found that Google's Open Source Vulnerabilities (OSV) database was ignoring and not listing vulnerabilities under the "disputed" status. Almost 600 new advisories have now been added to Google's OSV , including some that were under active exploitation .
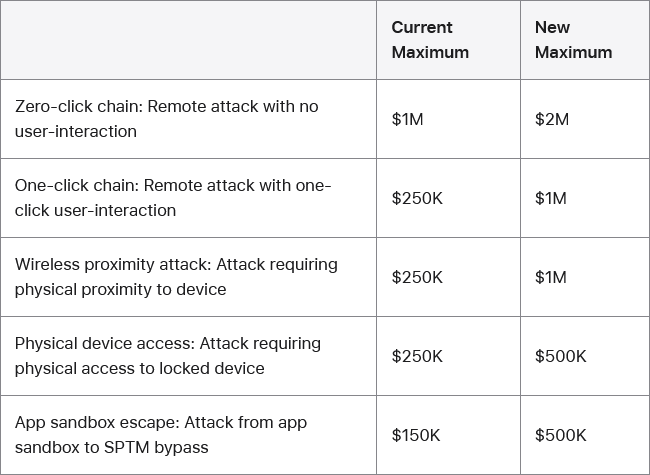
Apple doubles bug bounty rewards: Apple has doubled bug bounty rewards for top vulnerabilities and exploit chains. The new top reward can go up to $5 million for remote attacks on Lockdown Mode. The new rewards scheme will go into effect in November. The company will also add new bounty categories to cover more attack surfaces. Apple will also donate 1,000 new security-hardened iPhones to civil society organizations, which will distribute them to at-risk users.
Apple is planning a special initiative featuring iPhone 17 with Memory Integrity Enforcement. To rapidly make this defense available to those targeted by mercenary spyware, the company will provide a thousand iPhone 17 devices to civil society organizations. security.apple.com/blog/apple-s...
— ваят (@denbib.bsky.social) 2025-10-10T15:51:53.312Z
Backdooring AI is easy: It takes roughly 250 malicious documents to establish a "backdoor" in large language models. A new academic study disproves the idea that attackers need to control or poison a large portion of the training data to influence an LLM's output. Anthropic AI warns that this behavior makes LLM poisoning attacks far more accessible to potential attackers.
Anthropic AI tries to cheer us up a bit www.anthropic.com/research/sma...
— your #3 source for absurdist true crime 🔨 (@davidgerard.co.uk) 2025-10-09T20:02:45.827Z
Infosec industry
US investors acquire NSO Group: A group of US investors has acquired Israeli spyware maker NSO Group. The investor group is led by Hollywood producer Robert Simonds, who also tried to acquire the company in 2023. The deal is valued in the tens of millions of dollars. NSO will continue to operate out of Israel and remain subject to its export control regulations. The US Treasury Department added NSO Group to its list of banned entities in 2021. [ Additional coverage in Globes /English coverage in TechCrunch ]
BalCCon 2025 videos: Talks from the Balkan Computer Congress 2025 security conference, which took place last September, are available on YouTube .
New tool—Intune security recommendations: Microsoft published a dedicated page last week with recommended Intune security configurations.
New tool—PromptIntel: Microsoft security researcher Thomas Roccia has released PromptIntel , a database of adversarial AI prompts.
New tool—IAmAntimalware: Red teamer Two Seven One Three has released IAmAntimalware , a tool to inject code into antivirus processes.
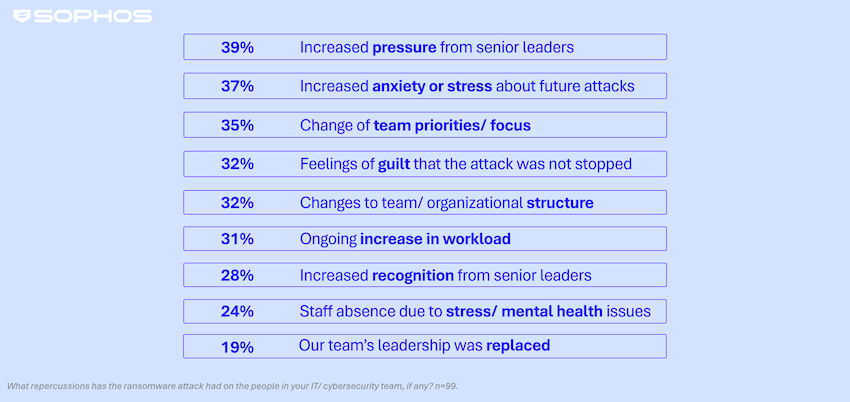
Threat/trend reports: Check Point , IronScales , Security Blueprints , and Sophos have recently published reports and summaries covering various threats and infosec industry trends.
Risky Business podcasts
In this edition of Between Two Nerds , Tom Uren and The Grugq talk about the zero-day mass exploitation of SharePoint and Exchange. This type of widespread hacking appears to be increasingly common... but is it?
