Risky Bulletin Newsletter
February 26, 2024
Risky Biz News: Backdoor code found in Tornado Cash
Written by

News Editor
This newsletter is brought to you by no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

A malicious backdoor has been found inside the user interface component of the Tornado Cash cryptocurrency mixing project.
The code has been exploited in the wild to hijack assets deposited in Tornado Cash installations.
The malicious code was added to the project by one of its developers.
It works by sending copies of deposit notes to a third-party server.
The deposit notes, also called deposit certificates, work as private keys for funds placed inside a mixer and can be used to re-access assets once they've been mixed.
The malicious code was discovered by a security researcher known as Gas404 and confirmed by Yu Xian (Mr. Cos), the founder of the SlowMist blockchain security company.
All Tornado Cash servers deployed on the IPFS network since the start of the year (January 1) are believed to be impacted.
Tornado Cash is an open-source project that lets anyone run their cryptocurrency mixing service. Its codebase powered the original Tornado Cash cryptocurrency mixing service that was active in the early 2020s.
That iteration of the service was extremely popular with criminal groups, and especially with North Korean hackers, who used it to launder and obfuscate the origin of funds they stole from legitimate cryptocurrency platforms.
The US government sanctioned Tornado Cash in 2022 and charged its developers for money laundering and sanctions evasion violations.
US officials said the original Tornado Cash service helped laundered more than $1 billion worth of assets, including hundreds of millions for North Korean hackers.
Following the sanctions, the original Tornado Cash website was seized, but its codebase continued to exist separately and was used to host new shadowy mixing services.
This backdoor code incident is the second major security breach the project has seen over the past year. In May of last year, a hacker temporarily took control of the project's governance.
Due to the shadowy nature of Tornado Cash servers these days, it remains unclear how many funds were stolen in this latest incident.
Breaches, hacks, and security incidents
Change Healthcare cyberattack: A cyberattack disrupted the operations of pharmacies across the US last week. The incident impacted Change Healthcare, a prescriptions and payments processing platform operated by UnitedHealth. In an SEC filing, the company claimed "a suspected nation-state associated cyber security threat actor" gained access to some of the Change Healthcare IT systems. The company took down the platform to investigate the incident. Besides pharamcies, the outage also impacted operations at some hospitals and clinics.
RCMP cyber event: Canada's national police force was hit by a cyberattack on Friday. The Royal Canadian Mounted Police is investigating the breach's impact but said police operations were not affected. Officials have also notified employees of the incident and asked them to remain vigilant. [Additional coverage in CBC]
ROK Supreme Court hack: South Korean police have confiscated servers from the country's Supreme Court that were hacked last year by a North Korean hacking group. The servers were allegedly infected with malware used by the Lazarus Group. Officials believe hackers have had access to the Supreme Court's systems since at least February 2023. Investigators plan to analyze the confiscated servers to discover how Lazarus operators gained access to the court's network. [Additional coverage in NK News]
Malawi cyberattack: The Malawi government has suspended the issuing of new passports after a cyberattack hit the country's immigration service. The incident took place at the start of the month. Officials say the hackers asked for a ransom. The country's president said they do not plan to give in to the demand. [Additional coverage in the BBC]
U-Haul breach: Moving and logistics company U-Haul disclosed a security breach. The company says a hacker gained access to an employee's credentials and used them to access data on specific customers.
Insomniac Games hack: Sony has finally confirmed the Insomniac Games hack from December of last year.
General tech and privacy
Reddit gives away content to Google: Reddit and Google have signed a partnership to allow Google to use all of Reddit's content to train some soon-to-be-very-stupid AI thing.
Google Pay US shutdown: Google is shutting down the US version of its Google Pay app. The company has told users to move to its newer Google Wallet service.
Nevada AG moves against Meta: Nevada's Attorney General has filed a motion to block Meta from providing end-to-end encryption to users under 18 in the state. Officials claim they need access to unencrypted comms to combat predators and child sexual exploitation. Meta has provided end-to-end encryption for Messenger users since 2016. In December of last year, the company slowly started enabling encryption as the default setting. Nevada officials are looking for an injunction to block this rollout. The legal challenge does not target other Meta encrypted services like WhatsApp. [Additional coverage in Kim Zetter's Zero Day]
Government, politics, and policy
Contractors push back: US contractors are pushing back against two pieces of cybersecurity legislation that would grant government cybersecurity agencies full access to their networks during a security incident. [Additional coverage in FNN]
DOT port crane cybersecurity guidance: The US Department of Transportation has asked port operators to run Chinese-made port cranes on separate segments from their main networks. Officials have also asked port operators to monitor crane network traffic and limit remote access features. The new security advisory comes days after the White House published an executive order to boost cybersecurity at US ports. US security agencies have warned that China could use software on its cranes to spy on or disrupt US port activity. [via Simon Tsui]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Tines co-founder and CEO Eoin Hinchy about how the unique features of AI and ML algorithms are more suited to blue teamers and defending networks rather than attackers.

Cybercrime and threat intel
Burke-Fox News hacking scandal: The FBI has arrested and charged journalist Tim Burke with allegedly hacking Fox News. Officials claim that Burke and an unnamed source compromised credentials to access and download data from Fox News' network. Burke allegedly used the files to produce news reports for HBO and ESPN. Some of the footage that Burke released exposed abusive behavior inside Fox News and led to the firing of network figurehead Tucker Carlson. Burke's legal team denied the charges and claimed he found the files unprotected on the internet. [Additional coverage in the Tampa Bay Times]
Mysterious Facebook account hacks: There have been a few reports over the weekend about Facebook and Oculus accounts getting hacked.
BreachedForums bans ransomware sales: The administrators of the BreachedForums hacking forums have banned the sale of any ransomware-related products or services. XSS and Exploit previously also banned ransomware before changing their minds and re-allowing the groups back on.
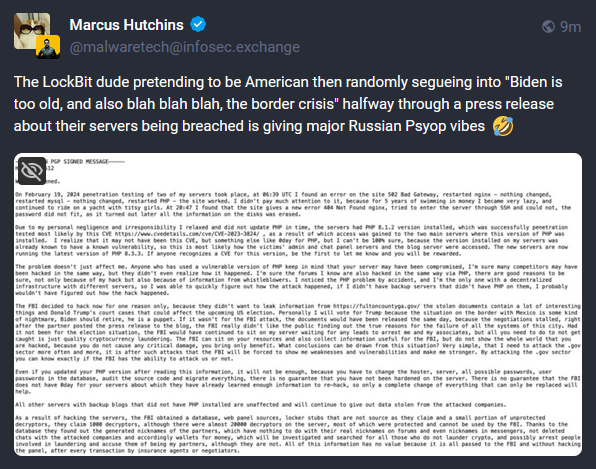
LockBit's response: LockbitSupp, the alleged admin of the LockBit ransomware, has posted a rambling reply to the FBI and NCA taking down their RaaS platform. And when I say rambling, I mean nonsensical garbage and disinfo attempts!
New npm malware: Nineteen malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Ransomware payment stats: A Cybereason survey of more than 1,000 enterprise IT professionals has found that all respondents suffered a security breach over the past two years. Eighty-four percent of respondents ended up paying a ransom to attackers, but only 47% said they got their data and services back and running uncorrupted. Eighty-two percent of respondents were hit again within a year.
Malware technical reports
AngelDrainer: GoDaddy's Sucuri looks at AngelDrainer, a phishing kit specifically designed to steal funds from cryptocurrency wallets. This is the same kit that was used in the Ledger Connect Kit incident last year. Sucuri says it found the kit installed on more than 5,700 domains over the past month, and the kit is still running on 432 sites.
CloudRouter proxy botnet: Cybersecurity firm Spur has linked a new residential proxy provider named CloudRouter to 911[.]re, a service that shut down last year after a major security breach.
RisePro leak: The source code of the RisePro v2 infostealer was leaked online months after v1 was also posted on hacking forums.
Lorenz ransomware: NCC Group researchers have published a report on recent updates they have spotted in the Lorenz ransomware source code.
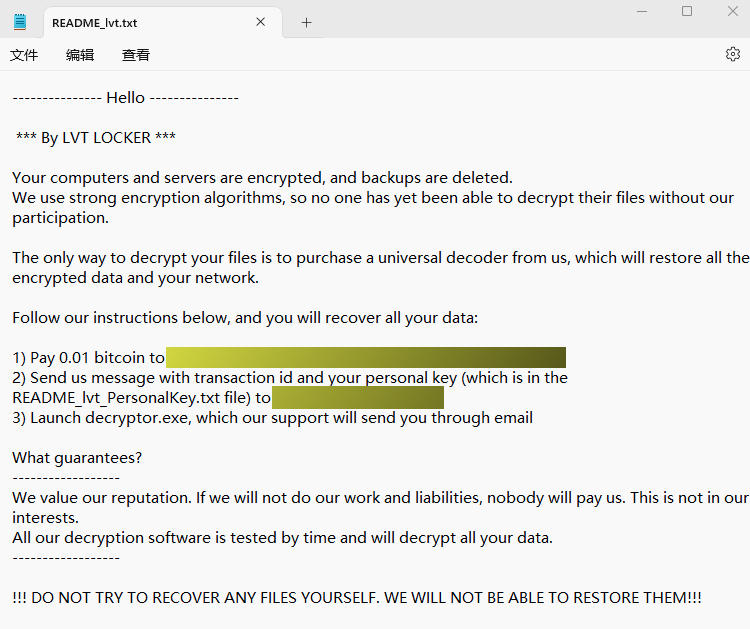
LvtLocker ransomware: A threat actor is deploying a new ransomware strain named LvtLocker on TerraMaster network-attached storage (NAS) devices. According to Chinese security firm Qihoo 360, the attackers are targeting unpatched devices with exploits for older vulnerabilities. The new LvtLocker appears to have been based on the leaked source code of the older Babuk ransomware. The attacker is asking for $500 from victims to decrypt their files. Several attacks have been reported on TerraMasters's user forum.
Sponsor Section
In this demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to RiskyBiz host Patrick Gray.
APTs, cyber-espionage, and info-ops
i-SOON leak: Analyses on the i-SOON leaks are coming in fast and hot. We now have reports from Palo Alto Networks, SentinelOne, Brian Krebs, and Will Thomas. Our own coverage is here.
Russian APT on the frontlines: Ukrainian intelligence officials say that Russia has moved some of its APT groups to the frontlines. SSU head Illia Vitiuk says these units are helping Russian troops hack into captured Ukrainian equipment. One of these teams has allegedly been stationed in the occupied city of Donetsk for more than a year. [Additional coverage in Politico]
UAC-0050: Ukraine's intelligence service has linked a threat actor tracked as UAC-0050 to "Russian law enforcement authorities."
SideWinder: Qihoo 360 researchers have published a report on recent SideWinder phishing campaigns targeting Bhutan, Myanmar, and Nepal. SideWidner, also known as Rattlesnake and APT-C-24, is a suspected Pakistani APT group.
Vulnerabilities, security research, and bug bounty
sPACE attack: Security researcher CtrlAlt has published a technical write-up on CVE-2024–23674, a vulnerability in the electronic ID (eID) scheme used by the German government.
"This vulnerability compromises the hardware security, enabling an attacker to effectively carry out scalable Man-In-The-Middle attacks. The attack does not require remote code execution, physical access, or similar approaches and can be executed through apps uploaded to the official app stores. Such attacks compromise access to services that rely on eID security, including government services, eHealth platforms, and banking systems. Additionally, the attacker can extract the personal data stored in the eID. This attack requires no special privileges and can be executed remotely."
VoltSchemer attack: Researchers from CertiK and the University of Florida have devised an attack named VoltSchemer that can feed malicious voice commands to nearby voice assistants using electromagnetic interferences caused by wireless charging stations.
Zyxel security updates: Zyxel has released a security update to patch four vulnerabilities in the company's firewalls and APs.
Comdex vulnerability: CyberArk researchers have found a vulnerability in the Comdex blockchain that could have been used to steal users' assets.
Apple Shortcuts vulnerability: Bitdefender researchers have published a detailed analysis of CVE-2024-23204, a vulnerability they found in Apple's Shortcuts app. Apple fixed the issue in January. The vulnerability can allow attackers to use malicious shortcuts to access sensitive data on a device.
Infosec industry
New tool—PyRIT: The Azure AI red team has open-sourced PyRIT (Python Risk Identification Tool), an automation framework to test the robustness of LLMs against various attacks.
New tool—Go-EPSS: Security researcher Kaan Sadik Karadag has published Go-EPSS, a Go library for interacting with FIRST's EPSS (Exploit Prediction Scoring System).
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine Russian cyber doctrine and how it was applied in the early days of its invasion of Ukraine. They mention a Human Rights Watch report that examined how international humanitarian law was applied in the 2003 invasion of Iraq.

