Risky Bulletin Newsletter
April 26, 2024
Risky Biz News: Cisco zero-day fun time is here!
Written by

News Editor
This newsletter is brought to you by Trail of Bits . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed . On Apple Podcasts:

A suspected state-backed hacking group is exploiting two zero-days in Cisco ASA security appliances as part of a campaign targeting government networks globally.
Cisco confirmed the attacks earlier this week when it also released patches for the two zero-days.
The company linked the attacks to a group it tracks as UAT4356 . Cisco says the group has also targeted perimeter network devices from other vendors, as well as Microsoft Exchange email servers.
No other vendor has come forward as of yet, and we should expect more information on these attacks in the coming weeks or months.
According to a timeline published in a blog post this week by Cisco's Talos security division, the part of the campaign targeting Cisco ASA devices began in July last year with the preparation phase. Actual attacks began in early January this year and continued throughout 2024.
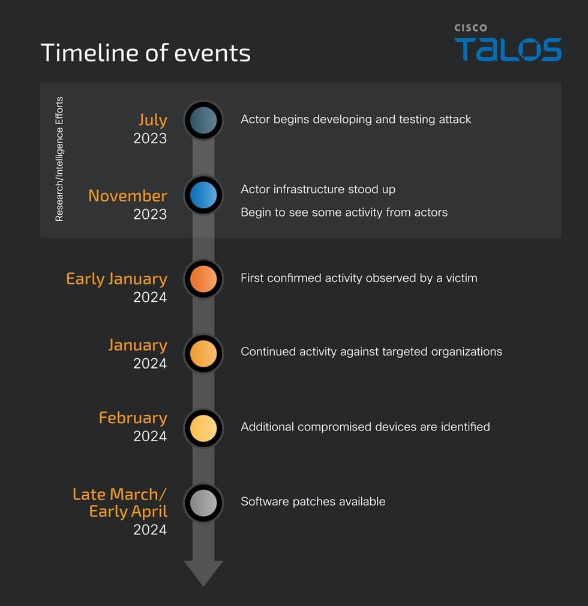
Cisco says it detected the first exploitation attempts and, as it gathered more data, began working with other vendors and cybersecurity agencies to investigate the attackers and the intrusions.
Since we had coordinated alerts published at the same time from cybersecurity agencies in the US , UK , Canada , Australia , and New Zealand , we presume some of the victims are located there.
The modus operandi of the attacks appears to be to compromise an edge device (in this case, a Cisco ASA appliance), gain persistence, and then move laterally across a victim's network.
Cisco says it still doesn't know how attackers gained control over the Cisco ASA appliances. The two zero-days ( CVE-2024-20353 and CVE-2024-20359 ) were used during post-infection steps to install two malware strains named Line Dancer and Line Runner.
Cisco described Line Dancer as a memory implant that the group later used to deploy Line Runner, a backdoor that can run commands on the infected devices. Besides the Cisco report, the UK NCSC has also published technical report on both Line Dancer [ PDF ] and Line Runner [ PDF ].
Of note is that Cisco mentioned that Microsoft is also tracking the group under its own taxonomy as STORM-1849—so expect a report from MSTIC in the coming days or weeks as well.
Cisco has not attributed the attacks to any state, but all of this smells of China's usual edge device hacking tactics.
Breaches, hacks, and security incidents
Chivo Wallet hack: A hacker has leaked the source code of Chivo Wallet, the cryptocurrency wallet and ATM platform used by the country of El Salvador. The leak is the latest in a long list of hacks against the El Salvador government by the CiberInteligenciaSV. Previously, the same group also leaked the personal data of 5.1 million Salvadorians. That leak accounted for most of the country's adult population. [ Additional coverage in CoinTelegraph ]
Nothing data breach: Smartphone maker Nothing has confirmed a security breach of its online community forum. The breach took place in 2022 but came to light this week after some Nothing customers spotted their forum data online. The company says the breach took place after a threat actor exploited a bug in its forum to collect user data such as names and emails. Nothing says that only 2,000 users were impacted and that no passwords were exposed in the hack. [ Additional coverage in AndroidCentral ]
Meduza DDoS attack: Qurium researchers have linked recent DDoS attacks against Russian independent media outlet Meduza to the infrastructure of three residential proxy providers. The most recent of these attacks took place on April 15 and lasted 48 consecutive hours. Attacks were linked to Plainproxies, Min Proxy, and RapidSeedBox. Qurium says the same providers were also behind coordinated DDoS attacks on independent Hungarian news sites last year.
Coast Guard Reserve breach: The Coast Guard Reserve alerted thousands of its personnel of a data breach last week after someone improperly sent their PII to unapproved recipients. [ Additional coverage in C4ISRNET ]
Lincoln Project BEC scam: Anti-Trump and anti-GOP super PAC the Lincoln Project says it lost $35,000 to a BEC scam. [ Additional coverage in The Independent ]
General tech and privacy
Google delays end of 3rd-party cookies: Google has delayed the phase-out of third-party cookies from its Chrome browser to early 2025. The company delayed the removal of third-party cookies at the request of UK authorities. Support for third-party cookies was supposed to be removed from Chrome at the end of the year.
Ring settlement: The FTC is refunding $5.6 million to Ring users as part of a settlement the agency reached with the company last year—when Ring admitted that employees accessed its customers' videos without consent.
WhatsApp passkeys: Meta has rolled out passkey support for its iOS app.
GitHub 2FA: GitHub says that 95% of users who contribute code on the platform have now enabled 2FA for their accounts. The company made 2FA mandatory for code contributors last year. Passkeys saw a spike in adoption after support was added while SMS use fell by 25%.
Windows Secure Boot rotation: Microsoft has entered phase II of its plan to rotate Secure Boot digital certificates. We covered the first phase back in February.
Government, politics, and policy
Welcome back, net neutrality: The US FCC has voted to reinstate net neutrality rules for US ISPs. [ Additional coverage in Engadget ]
US bans non-competes: The Federal Trade Commission has voted to ban employment agreements that typically prevent workers from leaving their companies for competitors or starting competing businesses of their own—also known as non-compete clauses. [ Additional coverage in NPR ]
EU Right-to-Repair: The EU Parliament passed Right-to-Repair legislation in a massive 584 to 3 vote. The directive now goes to the EU Council. If approved, member states will have two years to enforce it.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Dan Guido, the CEO of security research company Trail of Bits. Dan and Tom discuss DARPA' upcoming AI cyber challenge, in which Trail of Bits will compete to solve very difficult bug discovery challenges. They also talk about Trail of Bits' approach to making some of its own tools available to the community.

Cybercrime and threat intel
Samourai Wallet takedown: US authorities and Europol have taken down cryptocurrency mixing service Samourai Wallet. The service allegedly helped cybercriminals launder more than $100 million worth of assets from hacks, phishing operations, and illegal dark web markets. The site's two founders were also arrested in Portugal and the US. Authorities say the two founders openly invited users to launder funds through their site on social media. They also openly taunted law enforcement about their activities. In the aftermath of the takedown, the FBI has warned Americans not to use these types of shady services, as they risk losing access to their funds when takedowns happen.
BEC money launderer sentenced: A Florida court has sentenced a 50-year-old man to four years in prison for helping a BEC gang launder stolen money. Niselio Barros Garcia Jr. laundered more than $2.3 million for a Nigerian gang involved in BEC and romance scams. Officials say Garcia converted stolen funds to Bitcoin and sent the funds to his co-conspirators in Nigeria.
Scam call center disrupted: Czech and Ukrainian law enforcement have disrupted an illegal call center in the Ukrainian city of Odesa. Officials say the call center was involved in phone call scams that targeted and defrauded Czech citizens. Call center employees posed as Czech banks and tricked victims into installing remote access software on their devices. Officials say the group stole money from Czech bank accounts and transferred the funds to Ukraine, where they were cashed out through local ATMs.
Threat/trend reports : Chainalysis and Cisco Talos have recently published reports covering infosec industry threats and trends.
New Qiulong gang: Threat intel analyst Dominic Alvieri has spotted a new ransomware operation named Qiulong . The first post on their leak site is an extortion attempt against a plastic surgery clinic threatening to release patient nude photos.
Fake PoCs: Cloud security firm Uptycs discovered 16 fake PoCs for various vulnerabilities uploaded on GitHub.
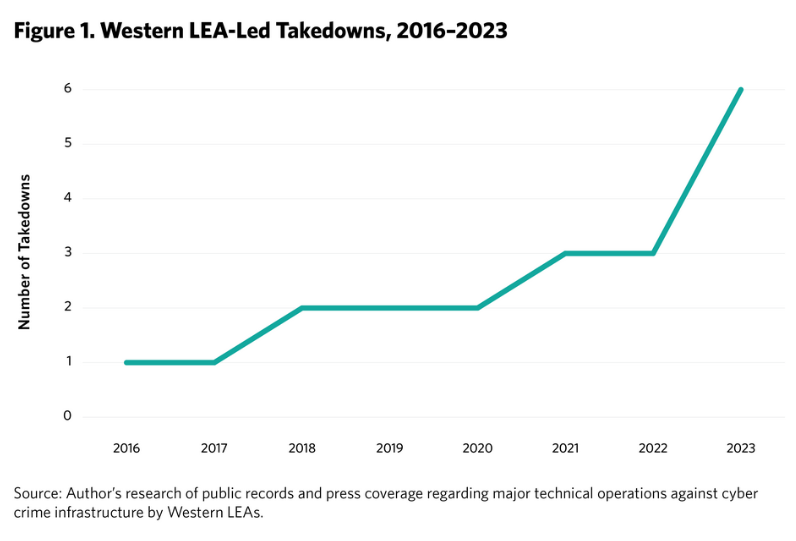
LEA cybercrime takedowns: The Carnegie Endowment for International Peace has published an analysis of recent law enforcement takedowns of cybercrime infrastructure and how governments and the private sector could help improve success rates.
Malware technical reports
Cactus ransomware: A group of Dutch security firms has published research looking at the Cactus ransomware's gang attacks on QlikSense servers. An English version of the research is available via Fox-IT .
SSLoad: Securonix has published details on FROZEN#SHADOW , a malware distribution campaign where the final payload was the new SSLoad malware (not to be confused with the older SLoader).
IDAT Loader: Morphisec has published a technical report on the most recent version of the IDAT Loader .
Sliver: Hunt & Hackett has published a paper on the ways to detect Sliver, a C2 framework abused by both cybercrime and APT groups. Hunt & Hackett calls it a "viable alternative to Cobalt Strike."
XZ backdoor: Kaspersky has published additional intel on the XZ backdoor incident, this time looking at the identities of Jia Tan and their secondary accounts.
Grandoreiro: Trend Micro has published an analysis on Grandoreiro, a banking trojan operated by a Brazilian gang. The gang was dismantled earlier this year, and Trend Micro says it played a crucial role in the Interpol operation. Researchers say the malware was designed by a new threat actor that calls itself Baron Samedit Marais.
Brokewell: Mobile security firm ThreatFabric has discovered a new Android banking trojan named Brokewell . The malware is still in development but combines the features of classic banking trojans, infostealers, and modern remote access toolkits.
Remcos RAT: Elastic's security team looks at the old REMCOS RAT malware, the RAT that won't die out.
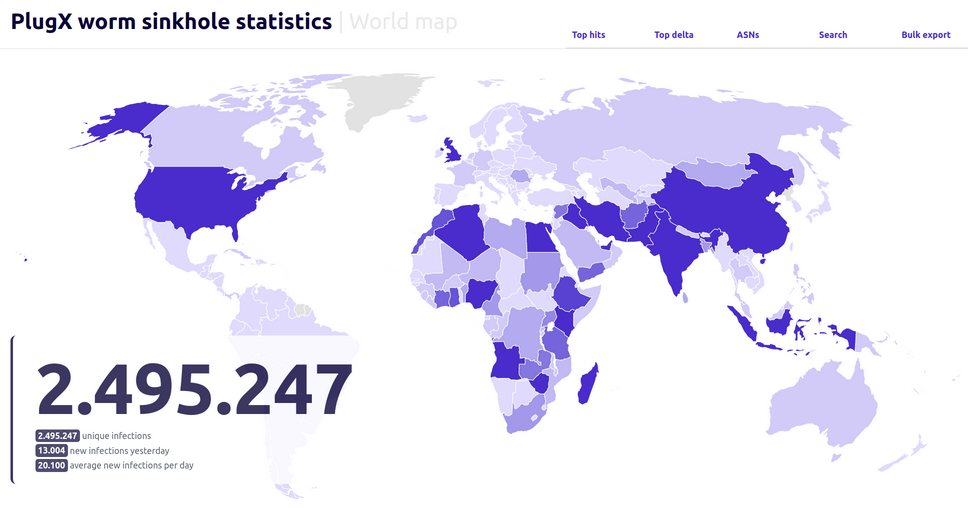
PlugX USB worm: French security firm Sekoia has sinkholed one of the command-and-control servers used by the PlugX USB worm. Almost 100,000 infected devices are still pinging the server for commands on a daily basis. The company says that over a period of six months, it saw more than 2.5 million distinct devices contact the server. Sekoia says the malware supports a remote uninstall command and has offered to help national CERT teams perform what it described as a "sovereign disinfection" of each country's IP space.
Sponsor Section
Trail of Bits has released weAudit , a VSCode extension the company's security engineers use for source code reviews during their security audits. The company also released SARIF Explorer , another VSCode extension for triaging static analysis results.
APTs, cyber-espionage, and info-ops
DPRK npm campaign: DevSecOps company Phylum says that North Korean hackers have returned to uploading malicious packages on npm. They previously ran similar campaigns in November 2023 and January this year . The latest campaign expanded to target macOS devices on top of Windows users. Chinese security firm QiAnXin previously linked the campaign to the Lazarus Group.
Pakistani APTs: Indian security firm Seqrite has published a profile on SideCopy and Transparent Tribe , two Pakistani APTs targeting Indian organizations.
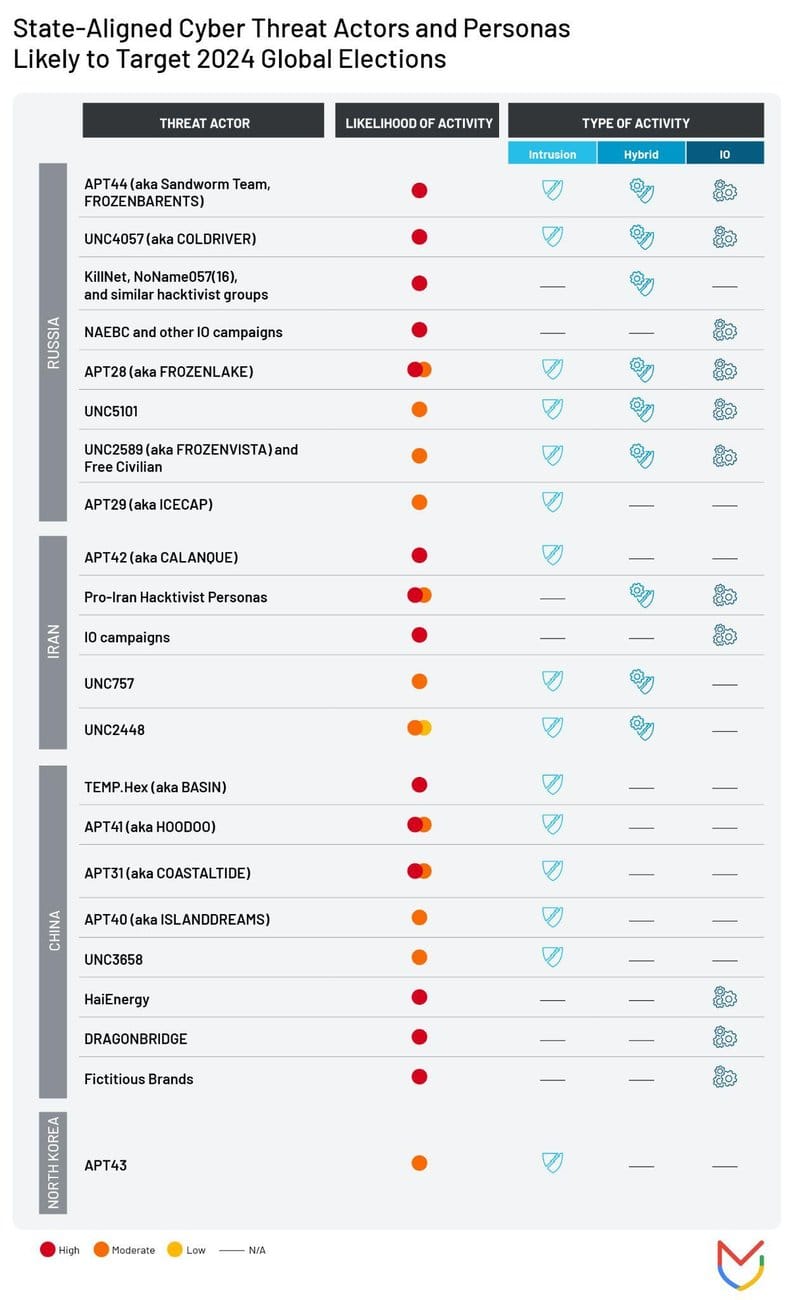
APT threat to elections: Google's Mandiant has published a list of state-sponsored groups likely to target election cycles across the world this year. It's quite the long list.
Vulnerabilities, security research, and bug bounty
Oracle VirtualBox PoC: Proof-of-concept code for an Oracle VirtualBox local privilege escalation bug was published on GitHub this week. The bug, tracked as CVE-2024-21111, was fixed earlier this month.
iSharing vulnerability: Security researcher Eric Daigle has found a vulnerability in the iSharing location tracking app that exposed the precise locations of all its (estimated 35 million) users.
ASUS security update: ASUS has published a security update for some of its routers and APs.
SourceForge vulnerability: Sonar researchers have identified and helped patch an issue in the SourceForge code-hosting platform. Researchers say the bug—residing in SourceForge's Apache Allura servers—would have allowed attackers to take full control of the platform.
Brocade vulnerabilities: Security researcher Pierre Kim has found 18 vulnerabilities in Brocade SANnav appliances. Kim reported the issues to Broadcom in September 2022, but only half were patched and received CVE identifiers. The vulnerabilities allow full compromise of SANnav devices. They vary from the use of hardcoded SSH keys to improper use of encryption.
Fortinet firmware: Security firm GreyNoise has published research on how security researchers can decrypt v7 of Fortinet's firmware. The company is known for encrypting its firmware as a way to prevent reverse engineering and security research. <sarcasm>Its encryption has been so good that threat actors have never been able to exploit its devices because they can't look at the code and search for bugs.</sarcasm>
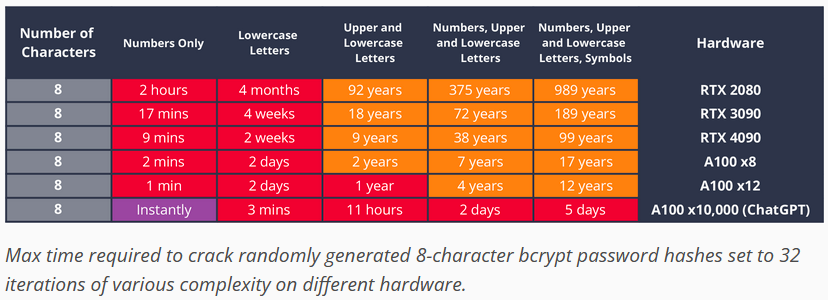
Bcrypt cracking: Research from Hive Systems warns that some bcrypt-hashed passwords may be quite easily crackable using modern GPUs. The time is here to start switching to longer passwords or passphrases.
" So even with benefit-of-the-doubt bcrypt, we’re still talkin’ 5 days tops if you have lots of cash. But for most budgets, up to 12 years seems decent if you’re also changing the password and it’s randomly generated. "
Infosec industry
Acquisition news: Security awareness training company KnowBe4 has agreed to acquire Egress, a provider of cloud email security tools.
American Sunlight Project: Former DHS disinformation expert Nina Jankowicz has founded the American Sunlight Project, a non-profit aiming to defend academic research against disinformation campaigns. [ Additional coverage in TechnicalTerrance ]
New tool—Poutine: Boost Security has open-sourced a new tool named Poutine that can scan and detect misconfigurations and vulnerabilities in build pipelines.
New tool—SAP Threat Modeling Tool: Security firm RedRays has released the SAP Threat Modeling Tool .
" This tool helps you analyze and visualize connections between your SAP systems, enabling identification of potential security risks and vulnerabilities. "
New tool—OSV-SCALIBR: Google has open-sourced OSV-SCALIBR , a file system scanner that can extract software inventory data and detect vulnerabilities.
New tool—Microsoft IR Guide: Microsoft has published a free guide [ PDF ] on using Windows Internals for forensic investigations.
Botconf 2024 videos: Talks from the Botconf 2024 security conference, which took place this week, are available on YouTube .
Risky Business Podcasts
In this special edition of the Risky Business podcast, Patrick Gray chats with former Facebook CSO Alex Stamos and founding CISA director Chris Krebs about sovereignty and technology.
