Risky Bulletin Newsletter
March 11, 2024
Risky Biz News: The aftermath of Microsoft's SVR hack is rearing its ugly head
Written by

News Editor
This newsletter is brought to you by Yubico. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Microsoft says that Russian state-sponsored hackers successfully gained access to some of its internal systems and source code repositories.
The intrusions are the latest part of a security breach that began in November of last year and which Microsoft first disclosed in mid-January.
Initially, the company said hackers breached corporate email servers and stole inboxes from the company's senior leadership, legal, and cybersecurity teams.
In an update on the same incident posted late Friday afternoon—as is the practice of every respectable corporate company—Microsoft says it found new evidence over the past weeks that the Russian hackers were now weaponizing the stolen information.
The Redmond-based giant initially attributed the attack to Midnight Blizzard, a group also known as Nobelium, one of the cyber units inside Russia's Foreign Intelligence Service (SVR).
Microsoft says that since exposing the intrusion, Midnight Blizzard has increased its activity against its systems.
Per the company's blog post, Midnight Blizzard password sprays increased in February 10 times compared to the "already large volume [it] saw in January 2024."
Furthermore, if we read between the lines, the group is now also targeting Microsoft customers. While Microsoft's legalese makes it clear that no customer-facing systems were compromised, the company weaselly confirmed that customers have been "targeted".
Emails stolen by the Russian group also contained infrastructure secrets (aka secret tokens, passwords, API keys, etc.), which Midnight Blizzard has been seen attempting to use.
Microsoft didn't say if customers were hacked, but a week after its initial disclosure, HPE told the SEC that Midnight Blizzard hacked its cloud infrastructure.
The intrusion led the Five Eyes cyber agencies to issue a joint advisory about the SVR's latest pivot to attacking cloud environments.
Just this week, the NSA also published a list of the Top 10 mitigations that can be used to counter the most common misconfigurations in cloud environments.
With the news that the SVR—the same hackers behind the SolarWinds incident—has now gained access to Microsoft source code and internal servers, security researcher @SimonTsui raised a valid point about the possibility of a supply chain attack using Microsoft software taking place. If that has taken place already, we're probably gonna learn about it on a late Friday afternoon.
Breaches, hacks, and security incidents
Doctor office hacks: Hackers are breaking into backends used by US doctors and pharmacists to prescribe controlled substances for their own profits. The threat actors are also using access to these powerful backends to create Telegram bots that can dox and reveal the private information of any US citizen. Hackers advertise both schemes on Telegram. The price for doxing someone is $15, while on-demand prescriptions for drugs like Adderall and oxyCODONE can vary between $250 and $1,200. [Additional coverage in 404 Media]
Interior Health breach: Canada's police agency has discovered a security breach at Interior Health, the health authority for the British Columbia Interior Ministry. Individuals who worked at the agency between 2003 and 2009 had their data stolen. The incident is believed to have impacted at least 20,000 people. [Additional coverage in CBC]
UniCredit fine: Italy's data protection agency has fined UniCredit Bank €2.8 million for a 2018 security breach. The incident was a misconfiguration in the bank's mobile banking platform that exposed the personal data of 778,000 customers. The data was provided in HTTP responses to anyone querying the portal. UniCredit is Italy's second-largest bank. [Additional coverage in Reuters]
Xplain ransomware attack: The Swiss cyber-security agency has confirmed that classified information was stolen in a ransomware attack last year. The incident took place in June of last year at Xplain, an IT contractor for the Swiss government. The Swiss NCSC says the Play ransomware group stole and later leaked more than 1.3 million files from Xplain's network. The leak impacted the Swiss Army, multiple cantonal police forces, and the Federal Office of Police. 121 of the leaked had a classified designation.
Glosbe leak: Online dictionary and translation service Glosbe has leaked the details of almost seven million registered users. The leak occurred in December of last year via a misconfigured MongoDB database. Exposed data included emails, usernames, social media identifiers, and encrypted passwords. [Additional coverage in CyberNews]
WOOFi crypto-heist: A threat actor has stolen $8.75 million worth of crypto-assets from DeFi platform WOOFi. The company described the hack as a sequence of flash loans. The hacker borrowed large sums from the platform and then repaid the loan at much lower prices. WOOFi has offered a white-hat bounty to the attacker, allowing them to keep 10% if they returned the stolen assets.
CISA hacked in Ivanti attacks: Hackers breached CISA systems through vulnerabilities in Ivanti products. The breach took place in February and impacted only two of CISA's Ivanti VPN servers. The agency says there was no operational impact and declined to attribute the attack. A source told The Record the servers were CISA's systems related to the chemical sector.
General tech and privacy
OpenAI Sora investigation: Italy's data protection agency has opened an investigation into OpenAI's new Sora AI model. OpenAI claims Sora can create realistic and imaginative scenes from short text instructions. Italian officials have asked OpenAI to provide more details on how the model was trained, how it plans to handle the personal data of EU citizens, and how it plans to train the model going forward.
Windows 11 CLAT support: Microsoft has expanded its support for CLAT (Customer-side transLATor) in Windows 11. This is a client-side component that converts IPv4 to IPv6 packets and vice versa. In theory, this should make IPv6 communications work easier on a wider set of channels and configurations.
Apple audio fingerprint bypass: Analytics company FingerprintJS has bypassed Apple's audio fingerprint protection. The protection works by adding random noise to audio produced by a browser. The random noise prevents online trackers from using short inaudible audio bursts to fingerprint a user's device. Apple introduced advanced audio fingerprinting protection in Safari 17, released in June of last year.
Government, politics, and policy
Document 79: The Chinese government has issued a secret directive in September of 2022 designed to remove American and foreign software from its critical sectors. The directive is named Document 79 but is informally known as "Delete A," short for Delete America. It mandates that state-owned companies replace US and foreign software in their IT systems by 2027. Beijing has used Document 79 to target American hardware companies such as Cisco, IBM, and Dell. According to the Wall Street Journal, the same directive is now also being used to go after Microsoft and Oracle's presence in China.
Malta to strip spyware exec's citizenship: The Maltese government has started the process to revoke citizenship from Tal Dilian, the CEO of spyware maker Intellexa. Officials started the process a week after the US imposed sanctions on Dilian and his company. The 52-year-old Dilian obtained citizenship through Malta's investor program. [Additional coverage in The Malta Independent]
US surveillance report: The US House Judiciary Committee and its Select Subcommittee on the Weaponization of the Federal Government has published a report on how US intelligence agencies are using financial institutions for surveillance purposes. This is Jim Jordan's subcommittee, so be aware the findings contain loads of partisan viewpoints and conclusions.
CISA understaffed: A report from the US Government and Accountability Office has found that the country's cybersecurity agency is understaffed in its OT team. CISA says its staff is comprised of four federal employees and five contractors. The nine are tasked with providing threat hunting and incident response for cyberattacks on OT systems across the entire US. GAO says the lack of skilled staff has impacted the agency's effectiveness when dealing with both federal and non-federal partners. [Additional coverage in CyberScoop]
NSA cloud mitigation guidance: The NSA has published a list of Top 10 mitigations to counter the most common cloud misconfigurations.

Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Derek Hanson, Yubico’s VP of Solutions Architecture and Alliances. Derek covers the different reasons organisations are investing in Passkeys, what organisations need to know to deploy them successfully, and warns that too often current deployments are too focused on authorisation rather than looking at the end user holistically.

Cybercrime and threat intel
Deepfake porn creators charged: US authorities have arrested two Florida teenage boys for allegedly creating deepfake nude images of their classmates. The two boys are aged 13 and 14, and allegedly used AI tools to generate nude images of both male and female students. Tech news outlet Wired says these are the first arrests and criminal charges as a result of alleged sharing of AI-generated nude images in the US.
KZ Team Reborn: Threat intel analyst g0njxa has published a profile of KZ Team Reborn, a traffer team specialized in working with infostealers.
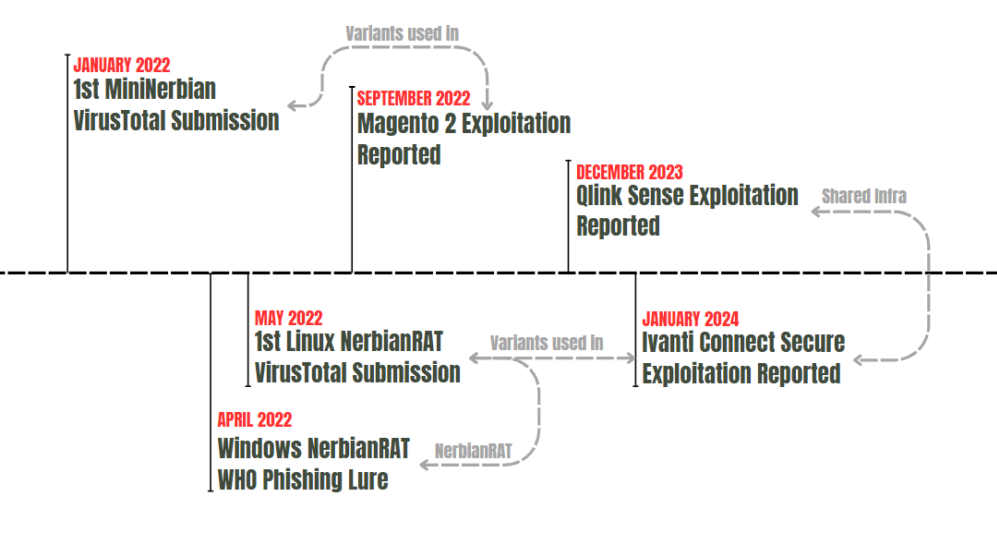
Magnet Goblin: A financially motivated threat actor named Magnet Goblin is targeting public-facing servers with one-day vulnerabilities. The group has attacked Ivanti, Magento, Qlink Sense, and Apache ActiveMQ servers. Some of the attacks took place within a day after proof-of-concept code was published for some vulnerabilities. According to Check Point, the group deploys Linux backdoors and credential stealers on compromised hosts. It is believed the group operates as an initial access broker.
New npm malware: Eight malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Radaris: Infosec reporter Brian Krebs has published a profile on US data broker Radaris and its two Russian co-CEOs.
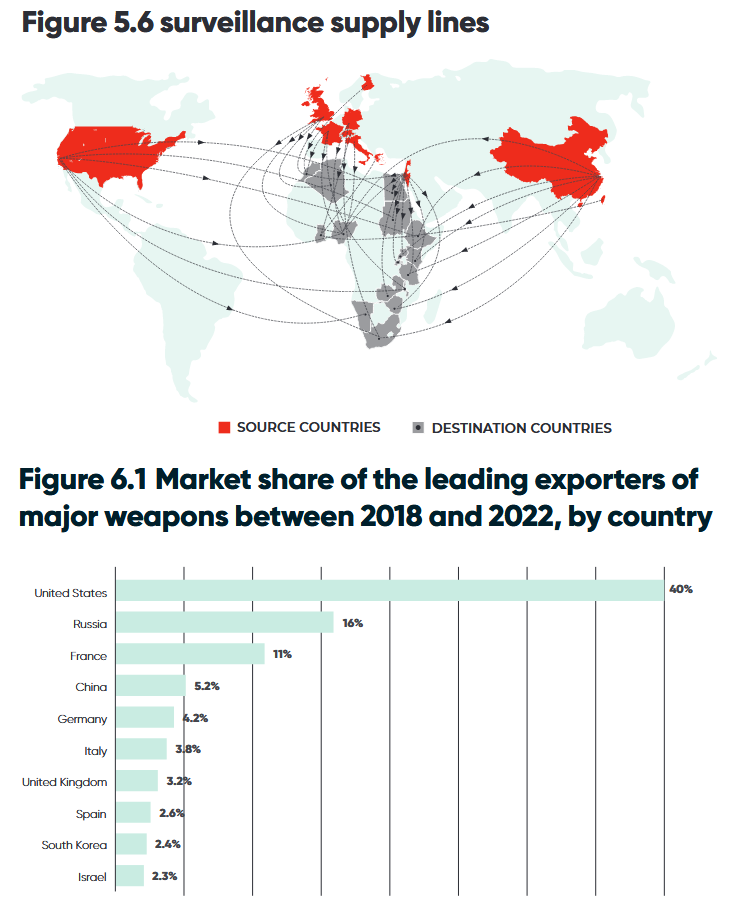
Spyware in Africa: Something we missed in September of last year was this report from the Institute of Development Studies that looked at who has been supplying spyware and surveillance tools to African countries.
Malware technical reports
Balada Injector: A new version of the Balada Injector has been deployed on more than 3,300 websites. Security firm Sucuri says the malware was deployed after exploiting an XSS vulnerability in the Popup Builder WordPress plugin.
Unknown Nim Loader: Walmart's security team has published a report on a new Nim-based loader they spotted in the wild.
BianLian ransomware: The BianLian ransomware is going after TeamCity servers, per a GuidePoint Security report.
Planet Stealer: InQuest researchers have published IOCs on Planet Stealer, a new Go-based infostealer that launched as a MaaS earlier this month.
Sponsor Section
YubiKeys slashes exposure to security breaches from phishing and credential thefts by 99.9% and reduces administrative overhead. Create your own customized Forrester Consulting Total Economic Impact™ study tailored for your organization here: Yubi.co/TEI
APTs, cyber-espionage, and info-ops
i-SOON leak: The Associated Press' Beijing and Hong Kong reporters have published a long read on the recent i-SOON leak.
Earth Kapre: Trend Micro has published a rather technical dive at a recent intrusion it linked to the Earth Kapre (RedCurl) APT.
Kimsuky PowerShell backdoor: Security researcher somedieyoungZZ has published a report on Kimsuky's new PowerShell backdoor.
MuddyWatter: Israel's CERT team has published an alert about ongoing MuddyWater phishing campaigns targeting local organizations.
Russian propaganda sites in the US: US academics have discovered at least five US news sites that are spreading Russian propaganda. The sites use logos and names that evoke a bygone era of American journalism. They publish legitimate news mixed with anti-Ukraine fake reports. Researchers believe the sites are operated by the remnants of Yevgeny Prigozhin's media empire. [Additional coverage in the NYT]
Russian propaganda sites in Europe: But while the NYT only scratches the surface, InfoNapalm researchers take a much deeper dive into how these pro-Russian and anti-West sites operate, lifting the lid on a giant network operating across Europe.
"Moscow's goal would be to bring radical forces, with whom it has warm relations, to power. This issue has become especially relevant a few months before the European Parliament elections. Such sites exert a much greater influence than the network of pro-Russian sites featuring the Russian word 'pravda' in their domain names or the network of fake pages and Kremlin bots on social media that were recently uncovered. After all, these networks either had a short period of existence, reached only a small audience, or were not credible in themselves. Many people already view Russian state media as compromised and untrustworthy propaganda outlets. Instead, websites that have been publishing for many years, with a specific audience and a format that resembles other Western media, are able to convince more readers of their narratives."
Bed bug PsyOp: The French government says Russia spread fake news and created a mass panic about bed bug infestations across France last year. Officials say Russian internet trolls artificially amplified reports of bed bug cases using social media in September and October of last year. French intelligence services say the Russian operation tried to link the arrival of Ukrainian refugees to the spread of the bed bugs in France. [Additional coverage in Le Monde]
Vulnerabilities, security research, and bug bounty
Ockam security audit: Trail of Bits has published a security audit it conducted on Ockam, a set of protocols for E2EE communications.
QNAP security updates: Taiwanese NAS vendor QNAP has released 11 security updates for its products.
Apple zero-days: Apple has ported fixes for two recent iOS zero-days to macOS versions.
Font vulns: Online design platform Canva has published details on thjree vulnerabilities it found in font-rendering libraries.
Fortinet bug: GreyNoise has published a report on CVE-2024-21762, one of the two Fortinet bugs disclosed at the start of February that came under active exploitation days after.
Fortinet bugs: BishopFox researchers break Fortinet's latest round of firmware encryption to understand the root causes of two recent vulnerabilities—CVE-2024-21762 and CVE-2024-23113—that have come under active exploitation.
Confluence fileless attacks: VulnCheck has published three proof-of-concept exploits that can execute arbitrary code within Confluence without touching the filesystem. The company says one of the PoCs is similar to exploits already used in the wild before its blog post.
Windows Themes vulnerability: Akamai's Tomer Peled has published a write-up covering CVE-2024-21320, a vulnerability he found in the Windows Themes component that can be abused to exfiltrate NTLM credentials from compromised hosts. All Windows versions are affected, and the bug was patched in January.
Secret Linux KASLR bypass: Security firm Trail of Bits has published a write-up on a KASLR bypass of the Linux kernel they reported back in 2020 but was never assigned a CVE identifier.
Sciener smart lock encryption downgrade: Aleph security researchers have discovered vulnerabilities in smart lock firmware developed by Chinese company Sciener. The vulnerabilities allow attackers to downgrade the encryption protocols used by the smart locks and their apps. Researchers say threat actors can use the bugs to compromise and open locks. The Sciener firmware has been found on smart locks from Israeli companies Kontrol and Elock. Attacks can be carried out with physical, adjacent, or Bluetooth connection proximity. There are currently no security fixes available.
GovQA platform: IT provider Granicus has rolled out fixes to GovQA, a US government online platform for managing public records requests. The issues were discovered by security researcher Jason Parker. They could have been used to retrieve sensitive information about request filers and sealed files. [Additional coverage in NextGov]
GitHub Actions password spray: Security researcher Daniel Underhay has published research on how threat actors could abuse GitHub Actions to rotate IP addresses during password spraying attacks and bypass any IP-based restrictions.
Infosec industry
DC Cyber Response Training Facility: IBM has opened a Cyber Response training facility in Washington, DC.
"The range includes new custom training exercises specifically designed to help US federal agencies, their suppliers and critical infrastructure organizations more effectively respond to persistent and disruptive cyberattacks, and threats posed by AI."
New tool—Indicator of Canary: TrustedSec's Justin Elze has open-sourced Indicator of Canary, a collection of PoCs from research on identifying canaries in various file formats.
New tool—Halberd: Vectra AI has open-sourced Halberd, an open-source security testing tool to proactively assess security measures by executing a comprehensive array of attack techniques across multiple surfaces.
New tool—Microsoft cybersecurity course: Microsoft has published a Cybersecurity for Beginners curriculum.

Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the shift that has taken place in Ukraine's cyber strategy as it has gone on the front foot and its cyber forces have launched multiple cyber strikes in the last few months. They discuss reasons why Ukraine might want to make this change and ask whether it makes sense.
