Risky Bulletin Newsletter
July 07, 2025
Risky Bulletin: Chinese researchers claim to find new North American APT
Written by

News Editor
This newsletter is brought to you by Knocknoc . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
Chinese security firm QiAnXin claims it discovered a new cyber-espionage group targeting China's high-tech sectors and operating out of North America.
QiAnXin's PanGu and RedDrip teams presented their findings at the CYDES security conference in Malaysia last week and published a technical report on GitHub on Friday.

Researchers describe the new NightEagle group (aka APT-Q-95 and APT-C-78 ) as extremely stealthy and very sophisticated.
The group uses novel malware, unique server infrastructure for each victim, and may be in possession of a suspected Microsoft Exchange zero-day.
There is no info on how the group gains access to a target's network, but once inside, they drop a modified version of the Chisel tunnelling software that pings a remote command and control (C&C) domain every few hours.
The DNS records for any of the C&C domains are down 99% of the time, configured to point to a dead-end IP address, such as 127.0.0.1, 0.0.0.0, 0.0.0.1, 1.0.0.0, and 114.114.114.114.
Apparently, C&C server domains are activated and allowed to resolve to a real IP address only when operators are active, and are immediately shut down after.
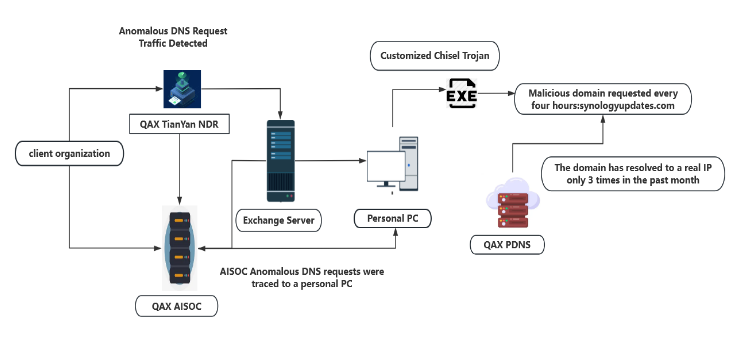
When the C&C domains are active, QiAnXin says they've seen NightEagle interact with local Microsoft Exchange servers and drop fileless in-memory implants.
Researchers haven't figured this out, but this is apparently done with what they think is an Exchange zero-day exploit chain.
NightEagle uses the in-memory implant to steal emails from an organization's Exchange inboxes.
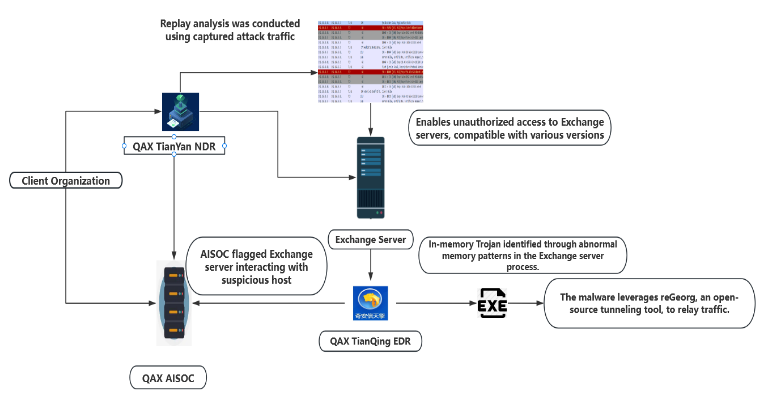
Besides emails, QiAnXin says the group also targeted source code repositories and backup storage systems.
The group appears to have been active since 2023, and targets typically included companies in China's high-tech sector, such as chipmakers, quantum technology firms, AI companies, and China's military industrial complex.
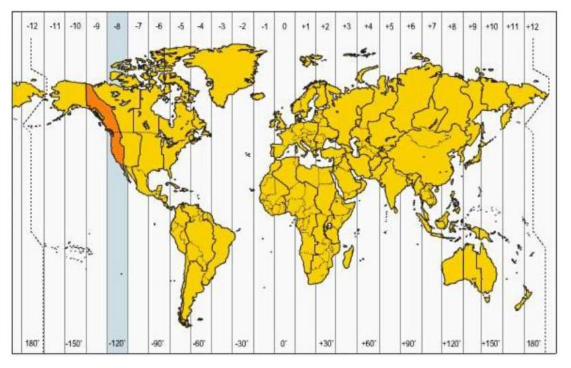
QiAnXin says it named the group NightEagle because the group only operates during China's nighttime, from 9:00 PM to 6:00 AM, Beijing time.
The group allegedly never operates outside these hours, and researchers believe the strict schedule puts the group on the North American West Coast timezone.
QiAnXin has not formally linked the APT to a country, but the "Eagle" moniker is clearly a jab at the US.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
C&M hack linked to malicious insider: Brazilian authorities have arrested a 48-year-old programmer in connection with the hack of software company C&M and six Brazilian banks. João Nazareno Roque allegedly sold his work credentials to hackers for $900 and then received another $1,800 to run malicious commands on the company's network. Roque said he was recruited in a bar and talked to the hackers by phone. The hackers used access to C&M's systems to steal $185 million from six Brazilian banks. [ Additional coverage in Globo ]
SEC and SolarWinds seek settlement: The US Securities and Exchange Commission and software maker SolarWinds are seeking a settlement to end an ongoing investigation. The SEC sued SolarWinds in 2023 over a 2020 security breach that allowed Russian hackers to deploy malware on its customers' networks. A judge dismissed some charges against the company and its CISO last year for post-breach disclosures and poor security posture. The only charges left are related to securities fraud for the company's public statements. [ Additional coverage in Hunton ] [ h/t DataBreaches.net ]
Idealab breach: American tech incubator Idealab says it was hacked last October and hackers stole the personal data of almost 2,800 individuals.
Louis Vuitton breach: A hacker has stolen customer data from the South Korean branch of luxury fashion house Louis Vuitton. The breach took place on June 8. Hackers also breached the South Korean units of Christian Dior and Tiffany's a month earlier, in May. Other luxury and fashion brands hacked over the past two months also include Cartier, Victoria's Secret, and Adidas. [ Additional coverage Reuters ]
IU breach: Most of Indiana University's public-facing websites have been down for three weeks due to an unspecified cybersecurity incident. Officials said security vulnerabilities were at fault but declined to provide other details. No sensitive data was allegedly compromised in the hack. [ Additional coverage in the Indiana Public Media ]
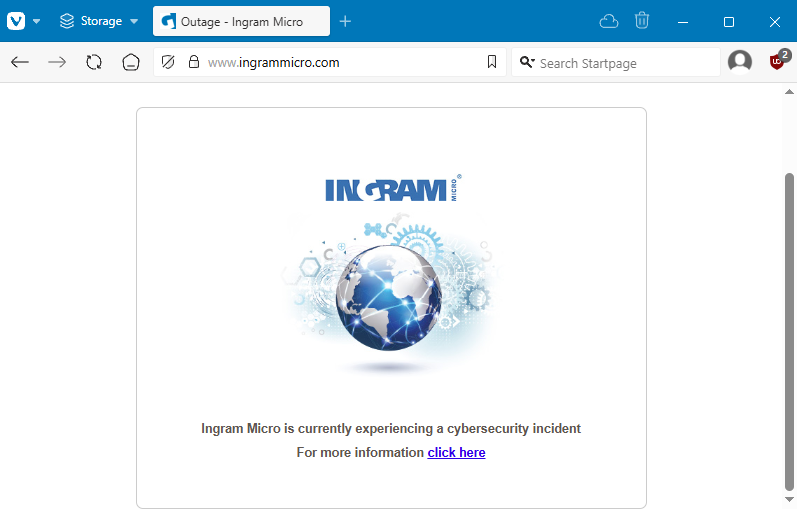
Ingram Micro ransomware attack: A ransomware attack has disrupted the activity of American IT distributor Ingram Micro . The company's network has been down for days as Ingram engineers work to restore systems. The attack has been claimed by a relatively new ransomware operation known as SafePay . [ Additional coverage in Bleeping Computer ]
General tech and privacy
PowerShell 2.0 deprecation: PowerShell 2.0 is now deprecated in Windows 11 Insider builds.
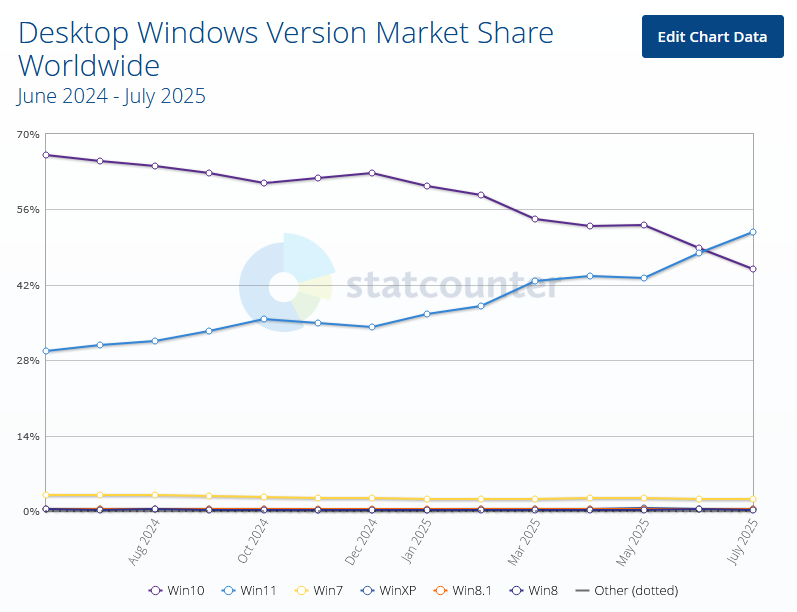
Win 11 overtakes Win 10: Windows 11 has overtaken Windows 10 to become the most popular version of Windows for the first time.
Government, politics, and policy
Taiwan warns against Chinese mobile apps: Taiwan's national intelligence agency has warned citizens to exercise caution when installing Chinese mobile apps on their devices. The agency says a recent audit of five apps (RedNote, Weibo, TikTok, WeChat, and Baidu Cloud) found multiple security issues, excessive collection of personal data, and abuse of system permissions. The warning comes as China appears to be preparing to wage war on the island nation.
Australia introduces age verification for search engines: The Australian government is introducing age verification checks for online search engines. Search engines like Google and Bing will have to verify the age of all Australians who are using their services while logged into their account. The new rules will go into effect later this year. They are designed to prevent children from accidentally running into violent and pornographic material while searching the internet. [ Additional coverage in Technology.org ]
EU to send "cyber reserve" to Moldova: The European Union will send a group of cybersecurity experts from the private sector to Moldova in September. The group will help local authorities defend their parliamentary elections against Russian interference. The mission represents a test for the so-called EU "cyber reserve" group, which is set to officially launch in December. [ Additional coverage in Politico Europe ]
Sponsor section
In this sponsored interview, Patrick Gray chats with the CEO of Knocknoc, Adam Pointon.
They talk about the woeful state of internal enterprise networks and how many control system networks aren’t appropriately segmented.
Adam also explains why Knocknoc released a very simple identity aware proxy: For too long the Zero Trust “industry” has focussed on securing access to critical applications, while everything else is left behind to get owned. This is Zero Trust for crappy apps! Zero Trust for the rest of us!
Arrests, cybercrime, and threat intel
Cyber scammers arrested in Nepal: Nepalese authorities have arrested 52 suspects for allegedly running online dating and crypto investment scams. The group allegedly ran a call center and a dating app called METOO to approach victims. Six of the detained suspects are Chinese and are believed to have managed the operation. [ Additional coverage in the Kathmandu Post ]
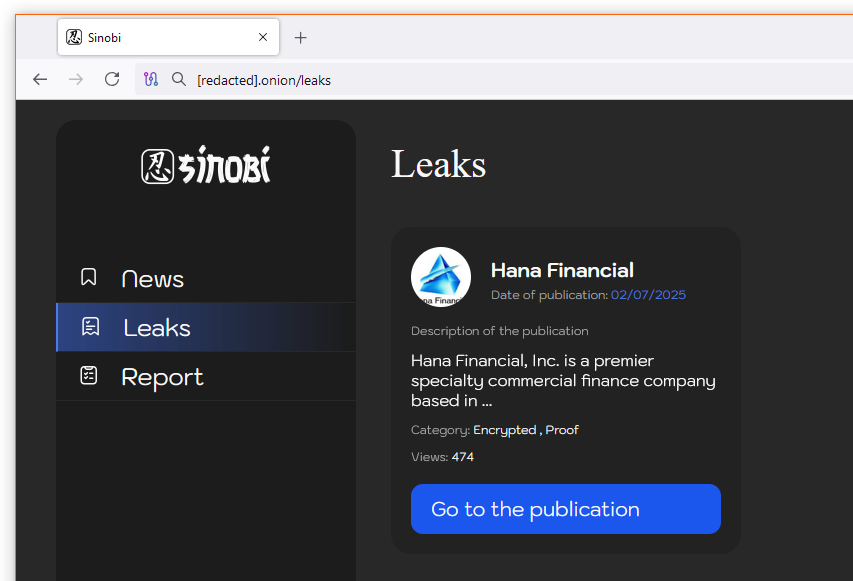
Lynx rebrands as Sinobi: The Lynx ransomware gang has allegedly rebranded as Sinobi.
New npm malware: One hundred seventy-four malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details .
JDWP abused for cryptomining: Threat actors are abusing JDWP (Java Debug Wire Protocol) ports left exposed on the internet to deploy cryptominers .
Azure Arc abuse: IBM's Dave Cossa looks at all the ways the Azure Arc could-to-local bridge could be abused by threat actors.
Signed drivers abuse: Per Group-IB , since 2020, over 620 drivers, 80+ certificates, and 60+ WHCP accounts have been spotted in threat actor campaigns.
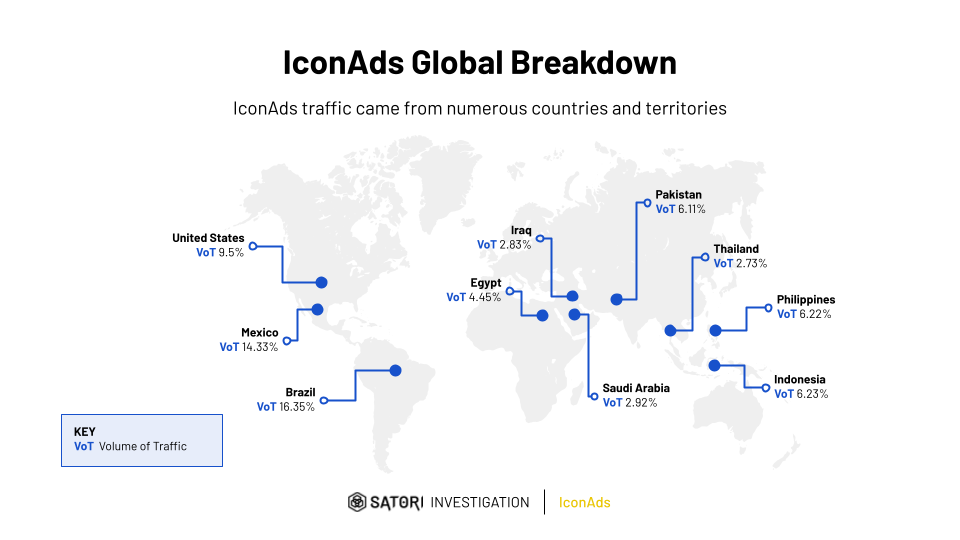
IconAds fraud operation disrupted: Google has removed 352 Android apps from the Play Store that were being used to show unwanted ads. The apps were part of an ad fraud botnet named IconAds that has been operating since 2023. According to Human Security, IconAds was showing up to 1.2 billion fraudulent ads per day.
Malware technical reports
Remcos RAT: Forcepoint researchers look at new versions of the Remcos RAT seen in the wild.
XWorm RAT: Cisco's Splunk team has published a technical report on the recent campaigns spreading the XWorm RAT, as well as its new evasion mechanisms.
Janela RAT: Walmart's security team has spotted a mysterious campaign spreading the Janela RAT but which also looks for local Chromium browsers to install an extension designed to steal browser data.
123 | Stealer: A new stealer named the " 123 | Stealer " is being advertised on underground hacking forums.
GOGLoader: ThreatMon researchers have published an analysis of a new C++-based malware loader named GOGLoader .
Pascal malware: Cisco's Splunk team looks at a malicious Pascal script that threat actors leveraged in a campaign designed to install the RedLine Stealer. Okta has also spotted a RedLine distribution campaign, but this one uses ClickFix as the initial infection vector.
Hpingbot botnet: Chinese security firm NSFOCUS has discovered a new botnet that is infecting IoT, Linux, and Windows devices. The new Hpingbot botnet is currently used to launch DDoS attacks. It is unique because it uses the hping3 open-source utility to launch the attacks and because it's written from scratch in Go. Most DDoS botnets are currently variations of the Mirai and Gafgyt malware strains.
RondoDox botnet: Fortinet has spotted a new botnet named RondoDox infecting TBK DVRs and Four-Faith routers.
Oyster/Broomstick backdoor: According to ArcticWolf, an SEO poisoning campaign for popular IT tools such as PuTTY and WinSCP has been pushing malicious apps laced with the Oyster/Broomstick backdoor .
SHELLTER framework: Several infostealer operations are using " an illicitly acquired " version of the commercial evasion framework SHELLTER in attacks. The Shellter project said it plans to work with law enforcement to track down the abuse.
We have identified the customer that may be associated with the information provided by Elastic. We are prepared to cooperate fully with law enforcement and provide additional information upon request. We do not condone illegal activities in any shape or form. https://t.co/XFU5vWCoXl
— Shellter (@shellterproject) July 3, 2025
Sponsor section
In this product demo, Knocknoc CEO Adam Pointon walks Patrick Gray through the Knocknoc secure access platform. Knocknoc is a platform that restricts network and service availability to authenticated users via existing network security equipment. Users don't need to install an agent. It also has an identity-aware proxy component that supports web applications and RDP.
APTs, cyber-espionage, and info-ops
Hive0154 (Mustang Panda): A Chinese cyber-espionage group known as Hive0154 has targeted members of the Tibetan community with the Pubload malware throughout the year, most likely ahead of the Dalai Lama's 90th birthday.
APT36 targets BOSS Linux: A suspected Pakistani APT group named Transparent Tribe (APT36) has developed malware to specifically target versions of BOSS Linux, an OS widely used by Indian government agencies.
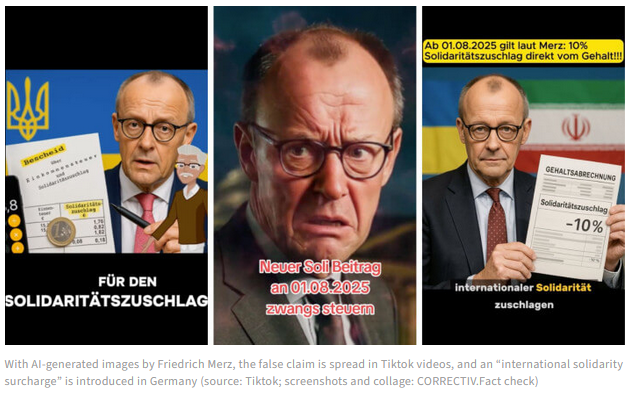
Massive AI disinfo hits Germany: Correctiv has spotted a massive TikTok disinformation campaign that uses AI-generated videos to attack Germany's current government and Chancellor Friedrich Merz. While there's no official attribution, the Russian group Matryoshka is typically involved in stuff like this, using the same tactics in Moldova and Romania this year. Politico Europe has recently published a deep dive looking at Russia's ever-increasing social media influence operations and how they don't even bother to hide what they want anymore.
Vulnerabilities, security research, and bug bounty
macOS SMB flaws: Supernetworks has discovered vulnerabilities in macOS Sequoia's SMB client.
"The worst of which can result in remote kernel code execution via an SMB URL delivered through any application that allows clickable URLs (e.g. messaging apps. Browsers, email client). This isn't necessarily a one click attack, as a user may need to click through some UI elements to trigger the exploit."
DjVuLibre fixes Linux attack: The DjVuLibre project has fixed a vulnerability that can allow attacks on Linux desktop users. The vulnerability can allow attackers to run malicious code when users open a maliciously crafted DjVu file. DjVu is a document format similar to PDF used on Linux environments, where the DjVuLibre library is widely used by multiple default apps.
New sudo vulns: Stratascale researchers have found two new elevation of privilege vulnerabilities ( CVE-2025-32462 , CVE-2025-32463 ) in the sudo Linux command-line utility. The two bugs allow attackers to elevate privileges and run commands as root. A PoC is public for one of the two issues. Exploitation criteria is pretty niche, and patches are available.
CitrixBleed 2 write-up: WatchTowr Labs has taken its own deep look at CVE-2025-5777, a recent Citrix NetScaler vulnerability that everyone is calling CitrixBleed 2 due to its ability to remotely leak memory from vulnerable VPN appliances.
Lenovo AppLocker bypass: TrustedSec researcher Oddvar Moe has found an AppLocker bypass on Lenovo laptops via a file in the C:\Windows directory with incorrect permissions. Lenovo has recommended removing the file.
Instagram's one-day certs: Security researcher Hereket looks at how Meta is rotating certificates on a daily basis for its Instagram service.
"Changing certificates daily could be an attempt from instagram reduce 'certificate life' to just one day instead of currently used mininum of about 90 days. It is hard for me to agree that it actually improves performance as the main attack vector of stealing private keys is still there if they are stored in close proximity and when somebody gets access to one they probably would have gotten access to all of them. But maybe they have some clever mechanism on the backend which stores them separately or somehow rotates access to them for the group of different people."
Infosec industry
HPE Juniper acquisition approved: HPE settled an antitrust lawsuit with the DOJ and will close its $14 billion acquisition of Juniper Networks announced last year. [ Additional coverage in Telecoms.com ]
Threat/trend reports: Cofense , Comparitech , Group-IB , Elliptic , NSFOCUS , and Raidiam have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Seriously Risky Business , Tom Uren and Patrick Gray discuss warnings about Iranian cyberattacks on US critical infrastructure. Despite many warnings, there have been no actual attacks, and they discuss the reasons why Iran would want to avoid escalatory cyber attacks.
In this edition of Between Two Nerds , Tom Uren and The Grugq talk about how Microsoft has embraced digital sovereignty and is bending over backward to satisfy European tech supply chain concerns.
