Risky Bulletin Newsletter
June 18, 2025
Risky Bulletin: Chrome gets a new prompt to prevent sneaky local network attacks
Written by

News Editor
This newsletter is brought to you by enterprise browser maker Island . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
Google Chrome is adding a new prompt that will ask for permissions when websites or mobile apps want to connect to a user's localhost or access devices hosted on their internal local network (LAN).
The new prompt is designed to block a rising trend on the internet, where threat actors lure users to malicious sites that access and relay malicious code through their browsers.
This code can contain CSRF (cross-site request forgery) exploits that hack local routers and IoT devices sitting on the same network and abuse them for ad fraud or other types of botnets.
Shady mobile apps, and even respectable ones , can also connect and create secret tunnels via localhost that can be abused to exchange data, deanonymize and even track users.
The new prompt is meant to block such attacks by preventing the automatic execution of these types of malicious code until users approve sites to access their local resources.
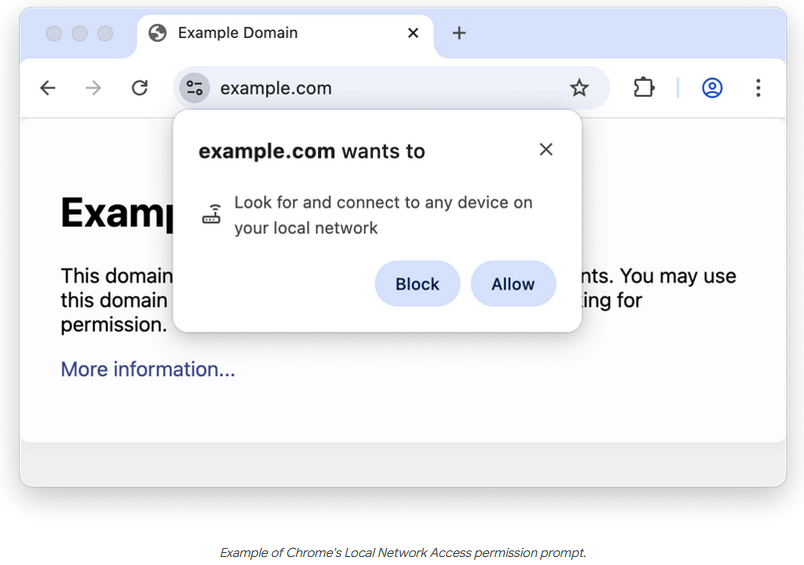
The new prompt is part of a new Chrome security feature named Local Network Access . The feature is replacing an older similar feature named Private Network Access that was also meant to block access to local resources by default. Google put the PNA feature on hold last year after encountering several compatibility problems in enterprise environments.
The user-prompting approach fixes PNA's overly broad blocks by allowing users local connections when they are absolutely needed.
The new feature will ship for initial testing in Chrome 138, scheduled to be released this week .
Users can go to the Chrome flags section and switch the " chrome://flags/#local-network-access-check " flag to " Enabled (Blocking) " to test the feature.
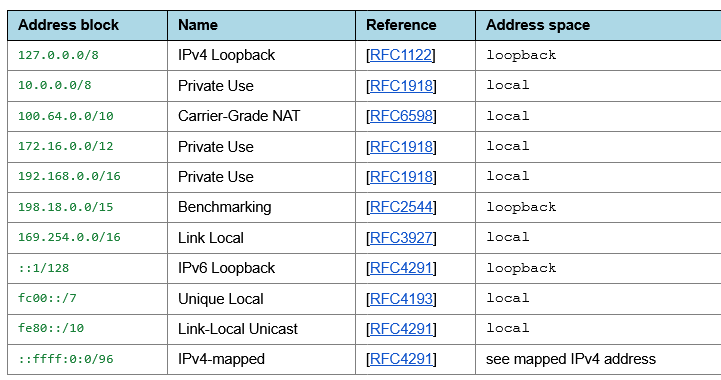
Once enabled, the prompt will appear for any websites that makes connections to the following IP address blocks, along with requests for " .local " domains.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
DDoS attacks hit Thailand: A huge wave of DDoS attacks has hit Thai organizations over the past months. Per Radware , the attacks have been conducted by AnonSecKh (aka ANON-KH, aka Bl4ckCyb3r) in response to the death of a Cambodian soldier during an incident with Thai soldiers near the Thai border.
Predatory Sparrow claims Iran bank hack: A hacktivist group named Predatory Sparrow (Gonjeshke Darande) has hacked and wiped the server of Iranian bank Sepah. The hack took down ATMs, POS payment systems, and bank account access. The bank also handles salary payments for Iranian government employees. The incident took place while Israel launched a military operation targeting Iran's nuclear and military assets. The group, which is believed to be linked to Israel, also leaked subscriber data from mobile operator IranCell . [ Additional coverage in TechCrunch ]
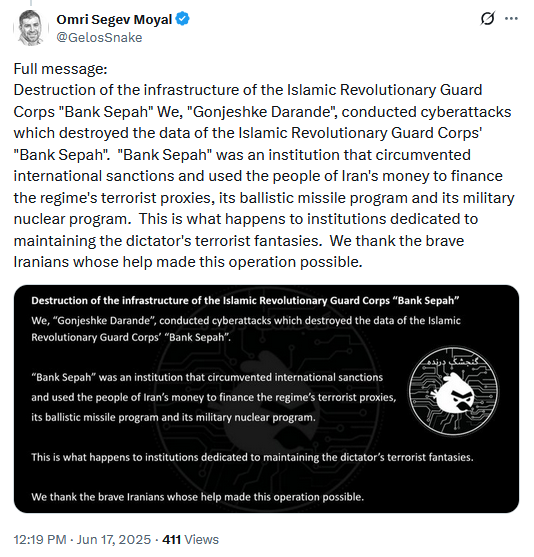
Someone claiming to be Gonjeshke Darande (Predatory Sparrow) has posted ~2GB of what *appears to be* IranCell subscriber data, covering the 935-939 prefixes. #privacy #breach #mobile #iran
— Snorre Fagerland (@snoffle.bsky.social) 2025-06-17T15:54:53.000Z
SK Telecom resumes user sign-ups: South Korean mobile operator SK Telecom has resumed new user sign-ups. The company suffered a major breach in April after hackers stole the eSIM data of all its users. SK paused new user registrations to replace all affected users' SIM cards. [ Additional coverage in Korea Times ]
SafeMoon hack funds recovered: The FBI has recovered $680,000 in crypto-assets stolen from the SafeMoon cryptocurrency platform in 2023. The hacker stole almost $9 million in assets but returned $7 million as part of a so-called "white-hat reward" with the platform. Despite the agreement, SafeMoon reported the incident to authorities. The FBI says it has not yet identified the attacker's identity. The seized funds were added to a bankruptcy trust after SafeMoon went under seven months after the hack.
Kazakhstan leak: The personal information of more than 16 million Kazakh citizens was leaked on Telegram . The data covers almost 80% of the country's population and appears to originate from a government database. The data includes full names, phone numbers, ID numbers, and home addresses. Kazakh police detained over 140 suspects earlier this month for selling citizens data on Telegram. [ Additional coverage in Orda ]
Napkin company goes under after ransomware attack: A 100-year-old napkin company from Germany filed for insolvency after a cyberattack. Fasana fell victim to a ransomware attack on May 21 and says it lost millions of euros from unfulfilled orders. The company resumed operations three weeks after the attack, but after most of the financial damage was done. Fasana was founded in 1919 and has over 240 employees. [ Additional coverage in WDR / English coverage in DataBreaches.net ]
Some of the very real consequences of ransomware. We highlighted this, the UK blood drive, and food supply chain disruptions in this week's @gate15.bsky.social ransomware report. Frustrating real impacts.
— andy jabbour (@andyjabbour.bsky.social) 2025-06-17T11:55:43.978Z
2FA codes interception: A Lighthouse Reports investigation found that 2FA codes for various online services passed through the network of Swiss telecom Fink, a known provider of location tracking services to government agencies
VirtualMacOSX breach: Over 10k records have been stolen and leaked from macOS cloud provider VirtualMacOSX .
CCC data for sale: A hacker has listed for sale the personal data of 9.1 million customers from US-based cash recovery service the Credit Control Corporation. [ Additional coverage in DataBreaches.net ]
Helsinki breach IR report: The city of Helsinki has published a post-mortem report of a security breach of its Department of Education it disclosed last year. The tl;dr of the entire report is in mine and Janne's BlueSky posts below. [ h/t to our anonymous reader ]
In May last year, the city of Helsinki disclosed a data breach. The IR post-mortem report is now live: www.turvallisuustutkinta.fi/en/index/tut... -entry via unpatched Cisco ASA -attackers stole 2TB of data -breach costs went over €1mil -attacker stole data on 150,000 students and 38,000 employees
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-06-17T11:54:57.382Z
It was a depressing read. They, for example, saw the first signs of an attack but somehow took five days to inform the responsible IT department. And they knew the VPN router was a risk because they had bought a replacement but hadn't deployed it.
— Janne Oksanen (@rocksanen.org) 2025-06-17T11:58:28.691Z
General tech and privacy
UK CMA closes Google probe: The UK's Competition and Markets Authority (CMA) has closed its investigation into Google's new Privacy Sandbox technology after Google canceled its rollout and went back to using third-party cookies in its browser.
UK fines 23andMe: The UK's privacy watchdog has fined genetic testing company 23andMe £2.31 million over its 2023 security breach. The company filed for bankruptcy earlier this year, so good luck getting the money.
Mastodon enforces minimum sign-up age: Mastodon, through its main instance, Mastodon.social, has updated its ToS to ban LLMs training and enforce a minimum age of 16 for new user accounts.
WhatsApp to get ads: Meta is adding online ads and promoted channels to its WhatsApp instant messaging service. Users will see ads based on their activity on Facebook and Instagram. Meta says the ads will not be based on user chats, which will remain private and separate from its advertising platform.
Ahhh, is *that* why Meta are suddenly running big ad campaigns about how they’re not able [citation required] to read your messages.
— Jon Wood (@jonwood.bsky.social) 2025-06-16T16:20:16.372Z
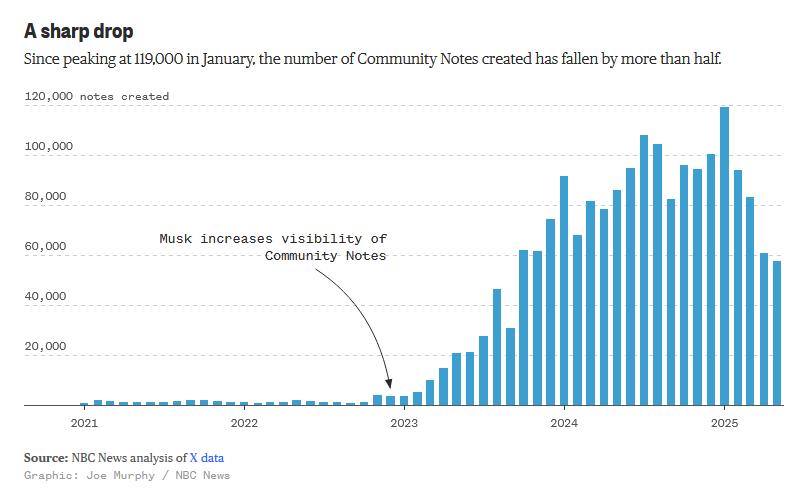
Twitter community notes participation plummets: An NBC News report found that participation in Twitter's Community Notes program has plummeted this year. This is likely explained by a change in algorithms that Twitter rolled out following the US Presidential Election, where it toned down the political content and election interference for meme videos, which rarely require community notes.
Government, politics, and policy
SEC scraps cybersecurity rules: The US Securities and Exchange Commission has withdrawn two proposed cybersecurity regulations targeting investment advisers and companies participating in securities markets . The agency did not provide a reason for the withdrawals. The two proposed rules sought to improve the cybersecurity practices of market participants. They were put forward in 2023 under the previous Biden administration. [ Additional coverage in CybersecurityDive ]
BIS cyber failures: The Department of Commerce's Office of Inspector General says the Bureau of Industry and Security needs to improve its cybersecurity and incident response procedures after the bureau failed to detect a simulated cyberattack and was running misconfigured systems. [ Additional coverage in FedScoop ]
FTC tells carmakers to protect user data: The US Federal Trade Commission has reminded carmakers that they need to implement information security programs to safeguard customer data.
PLA's use of genAI: Recorded Future has published a report on the Chinese army's use of generative AI.
"Likely realizing the intelligence limitations of general-purpose generative AI models, the PLA and China's defense industry are likely prioritizing the development and use of specialized models that have been fine-tuned for intelligence tasks. [...] PLA patent applications reveal that the PLA has designed methods and systems that use generative AI to facilitate intelligence tasks such as generating open-source intelligence (OSINT) products, processing satellite imagery, supporting event extraction, and processing event data."
EU Cybersecurity Index: The EU's cybersecurity agency ENISA has published the EU Cybersecurity Index , a report describing the cybersecurity posture of each member state and the EU.
Sponsor section
In this Risky Bulletin sponsor interview, Michael Leland, Field CTO of Island, talks about how Island manages risks from extensions, phishing, and infostealers. Even when credentials are stolen, it is still not game over, and there are still ways to prevent data loss and breaches.
Arrests, cybercrime, and threat intel
Police seize Archetyp Market: Europol has dismantled the Archetyp dark web market after a coordinated takedown across six countries. Archetyp launched in 2020 and was one of the few dark web markets that allowed the sale of fentanyl. The site had over 600,000 registered users and was linked to more than €250 million in illicit transactions. Officials seized the platform servers in the Netherlands and detained its admin in Spain—a 30-year-old German national.
Ransomware group detained in Thailand: Thai police have detained six Chinese nationals involved in ransomware attacks. The suspects targeted Chinese companies with malicious links that installed ransomware on their systems. The group operated from the eighth floor of a hotel in Pattaya and was part of a larger criminal network involved in illegal online gambling. [ Additional coverage in Khaosod English ]
Gotbit founder sentenced: A US judge has sentenced a Russian national to eight months in prison for manipulating cryptocurrency markets. Aleksei Andriunin was the CEO of Gotbit, a company that inflated trading volumes for cryptocurrency companies to boost the value of their assets. He was arrested last year in Portugal after the FBI set up a fake crypto token to expose his business.
Romance scams go over £100mil in the UK: The City of London's police says UK victims lost over £106 million to romance scams last year.
Watch out, insurance industry: Google Mandiant Chief Analyst John Hultquist says that Scattered Spider members are targeting the insurance industry. The attacks began around a week and a half ago, and several US insurance companies have already been hit. Individuals linked to the group have previously targeted the UK and US retail sector over the past months, breaching retail chains such as Coop and Marks & Spencer. [ Additional coverage in CybersecurityDive ]
Google's @hultquist.bsky.social says in an emailed statement that the company is seeing "multiple intrusions in the US" that bear the hallmarks of Scattered Spider activity and "now seeing incidents in the insurance industry." Google spox. confirmed there's more than one U.S.-based insurance victim.
— Zack Whittaker (@zackwhittaker.com) 2025-06-16T17:09:54.457Z
New Water Curse group active on GitHub: Trend Micro has spotted a new threat actor ( named Water Curse ) that uses boobytrapped GitHub repos to infect users for data exfiltration. This seems to be the same campaign documented by Sophos last week.
New SilverFox campaign: Fortinet has spotted a new campaign from SilverFox, a fin group known for targeting Chinese users. This campaign is different because it targets Taiwanese organizations with the HoldingHands RAT (also known as Gh0stBins) and sometimes the Gh0stCringe RAT.
Malicious PyPI packages: JFrog researchers have spotted a malicious Python package on PyPI that targeted users of the Chimera Sandbox .
SpyLoan on the Play Store: Check Point researchers have spotted the SpyLoan extortion malware inside a Google Play Store app named RapiPlata .
Zyxel exploitation: GreyNoise has spotted a spike in attacks targeting Zyxel routers using an older 2023 vulnerability (CVE-2023-28771).
Dangerous GitHub Actions found in popular projects: Sysdig has found multiple insecure GitHub actions being used by popular GitHub projects managed by MITRE, Splunk, and other major companies—exposing them to potential supply chain risks.
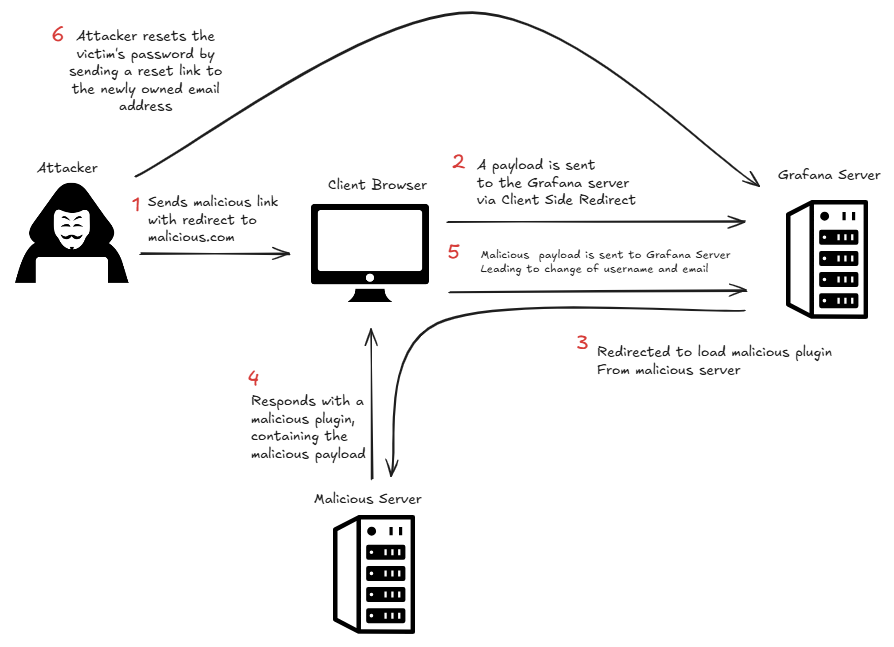
Third of Grafana servers exposed to attacks: A third of all public-facing Grafana servers are vulnerable to account takeovers. The servers are exposed to a vulnerability ( CVE-2025-4123 ) disclosed at the end of May. It allows attackers to force a Grafana server to use a malicious plugin that can then run malicious commands on their behalf. According to Ox Security , almost 46,000 servers of all the 128,000 Grafana instances connected to the internet have yet to be patched.
Malware technical reports
Bert ransomware: Threat intel analyst Rakesh Krishnan has published a technical analysis of the new Bert ransomware.

Magecart skimmer strain: HUMAN Security looks at a new Magento skimmer they've spotted in the wild. There's been little reporting on skimmers these days, but they are still very much active.
WormGPT variants: Cato Networks has spotted Grok and Mixtral-based versions of WormGPT, an AI-powered malware-writing tool released in 2023 and which was based on the GPT-J LLM.
RapperBot moves to DDoS extortion attacks: QiAnXin has spotted a new version of the RapperBot botnet , now demanding $5,000 from victims not to launch DDoS attacks against their servers. The botnet is currently at over 50,000 infected hosts.
Flodrix botnet: A threat actor is hacking Langflow AI servers to deploy Flodrix , a DDoS botnet malware strain.
SuperCard spreads to Europe and Russia: SuperCard , an Android banking trojan developed in China as a MaaS, is now being used in attacks against banks in Europe and Russia . The malware is one of the very few Android banking trojans that supports NFC cloning/relay attacks for emptying a victim's bank accounts.
GHOSTPULSE campaign: Elastic's security team has spotted a ClickFix campaign distributing the GHOSTPULSE loader , which was later used to deploy RATs and infostealers.
Katz Stealer: Picus Security has published a technical breakdown of the Katz Stealer infostealer, including a new feature that allows it to bypass Chrome's new Application Bound Encryption system.
KimJongRAT returns: PAN's Unit42 has spotted a new Powershell version of the old 2019-era KimJongRAT.
"This new analysis reveals the PowerShell variant's special focus on cryptocurrency, as it searches for an extensive list of browser wallet extensions. The continued development and deployment of KimJongRAT, featuring changing techniques such as using a legitimate CDN server to disguise its distribution, demonstrates a clear and ongoing threat."
AsyncRAT: Halcyon researchers have spotted a mass phishing campaign distributing AsyncRAT that employed a novel combination of Cloudflare and Batch and Python scripts to bypass endpoint detection.
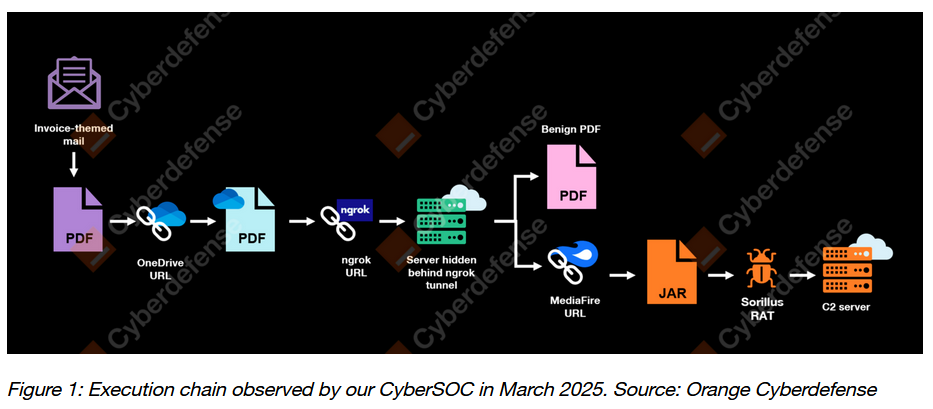
Sorillus RAT: Orange's security team has spotted a Brazilian-speaking threat actor targeting European organizations with a phishing campaign designed to deploy the Sorillus RAT .
Sponsor section
APTs, cyber-espionage, and info-ops
Kimsuky op: AhnLab has spotted a new Kimsuky phishing campaign spreading malware disguised in research papers.
Team46 linked to TaxOff: Russian security firm Positive Technologies has found more evidence linking the TaxOff and Team46 APTs—after an initial April 2025 report . The report also links a Chrome zero-day ( CVE-2025-2783 ) to the group's attacks earlier this year.
XDSpy's XDigo: Harfang Labs has spotted new attacks from the XDSpy APT group. The new campaigns targeted Eastern European and Russian governmental entities with the new XDigo Go-based backdoor.
ELN joins disinfo space: The Colombian National Liberation Army (ELN) has moved from kidnappings and killings to running fake news outlets, per a new DFRLab report .
Star Blizzard hacks UK expert: Keir Giles , a British researcher specializing in Russian policy, says he was hacked by a Russian APT group known as Star Blizzard. [ Additional coverage in The Record ]
CyberAv3ngers Mr. Soul reward: The US State Department is offering a $10 million reward for information on a hacker known as Mr. Soul. The individual is believed to have used the IOCONTROL malware in attacks against US critical infrastructure. They are allegedly a member of the CyberAv3ngers hacking group, which the State Department previously linked to Iran's Cyber-Electronic Command (IRGC-CEC). This is the second reward the US has offered for members of the CyberAv3ngers group after a similar one last August .

Vulnerabilities, security research, and bug bounty
Sitecore CMS vulnerabilities: Hackers can take over Sitecore CMS websites using a new exploit chain that abuses a hardcoded password. The password is just the letter "b" and allows attackers access to a user account that can inject malicious code into the site. Sitecore has released security updates for the three bugs part of the exploit chain. WatchTowr Labs , which discovered the bugs, says it is still working to get four other bugs patched. There are more than 22,000 instances currently available on the internet.
ZendTo vulnerabilities: Horizon3 has discovered a new path traversal vulnerability ( CVE-2025-34508 ) in the ZendTo file-sharing application that can allow malicious actors to bypass security controls and access or modify user files.
GerriScary vulnerability: Tenable has discovered a vulnerability in the Gerrit code-collaboration platform that allows unauthorized code submissions. Gerrit is a platform similar to GitHub and GitLab that was developed internally at Google. Tenable says the vulnerability could have been abused to submit malicious code to at least 18 official Google projects such as Chromium, ChromiumOS, the Dart programming language, and others.
AgentSmith vulnerability: Noma Security has discovered a vulnerability in the LangSmith observability platform that could have been abused to steal AI agent-related data, including prompts and API keys.
Veeam security updates: Backup software provider Veeam has released a security update to patch three security flaws.
Crowhammer attack: A team of academics has developed Crowhammer , a new attack that recovers Falcon encryption algorithm keys using one single Rowhammer bit flip.
Infosec industry
Threat/trend reports: Apiiro , ENISA , Eon , IANS , and Mindgard have recently published reports and summaries covering various infosec trends and industry threats.
AUSCERT 2025 videos: Videos from the AUSCERT 2025 security conference, which took place at the end of May, are available on YouTube [ Playlist 1 and Playlist 2 ].
Off-By-One 2025 videos: Videos from the Off-By-One 2025 security conference, which took place at the end of June, are available on YouTube [ Day 1 and Day 2 ].
Risky Business podcasts
In this edition of Seriously Risky Business , Tom Uren and Patrick Gray talk about how a Trump executive order has scaled back the government's cyber security ambitions. They also discuss North Korea's use of AI in its IT worker scam and the emergence of espionage-as-a-service... perhaps.
In this edition of Between Two Nerds , Tom Uren and The Grugq take a look at a new AI-powered covert influence campaign and compare it to World War 2 efforts.
