Risky Bulletin Newsletter
May 16, 2025
Risky Bulletin: Chrome will de-elevate itself when run with admin privileges
Written by

News Editor
This newsletter is brought to you by Corelight . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
Google Chrome will inherit a security feature from Microsoft Edge that will automatically prevent Windows users from launching the browser with elevated admin privileges.
The new feature stops and relaunches the browser with normal user-level permissions every time a user tries to run it as an Administrator.
Chrome will only run with admin rights if passed special command-line arguments or when it's started in Automation Mode—to prevent the browser from breaking complex software automation chains.
The same feature has been present in Edge since 2019 , and Microsoft is donating the code to the Chromium project, the base for Google Chrome, Opera, Vivaldi, and most of today's browsers.

The main benefit of this new feature is to bolster user security. Files downloaded and executed through Chrome inherit the browser's permissions and access level. Malware downloaded and executed through Chrome will gain full access to a system and lead to easy compromise of home systems or entire corporate networks.
Having Chrome, or any other browser, run in admin mode is generally frowned upon in corporate environments, and this is a new feature that most sysadmins will most likely enjoy.
The new admin de-elevation feature is already live in Chrome Canary , according to Reddit user Leopeva64 , who first spotted the feature two months ago.

Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Nucor halts steel plants over cyberattack: The US' largest steel producer halted production at several plants following a cyberattack this week. Nucor told investors it concluded an investigation and was restarting the affected plants. The company operates 26 steel mills across the US.
Coinbase discloses rogue insider breach: A cybercrime group bribed Coinbase overseas support agents to steal customer data to use in social engineering attacks. Coinbase says some of the attacks were successful but plans to reimburse customers who lost funds. The cryptocurrency exchange disclosed the hacks on Thursday after the group also tried to extort the company itself. Coinbase has declined to pay a $20 million ransom and is instead putting the same money in a reward fund for identifying the attackers.
GovDelivery abused for toll scams: A threat actor has abused the GovDelivery platform to send unpaid toll scams to Indiana residents. [ Additional coverage in TechCrunch ]
M&S insurance claim: Insurance companies Allianz and Beazley will most likely have to foot a bill of up to £100 million for the cyber-attack that crippled British retailer Marks & Spencer. [ Additional coverage in the Grocery Gazette ]
AHRC leak: The Australian Human Rights Commission has leaked documents and the personal data of users who contacted the agency through its website. The agency confirmed that over 670 documents were left exposed online via a server misconfiguration. The exposure lasted over a week in April, and some documents were indexed by search engines.
PrepHero leak: High school sports company PrepHero has leaked the personal details of thousands of students after it left an internal database exposed on the internet without a password. The database contained extremely sensitive data, such as ID scans, personal emails, and private conversations. PrepHero is based out of Chicago and helps high school athletes build sports resumes so they can be recruited by top colleges. The leak potentially exposes students to extortion and hacks since many will end up earning high figures as college or even professional athletes. [ Additional coverage in vpnMentor ]
General tech and privacy
Android Key Verifier: Google is adding a cryptographic key verification system to the Google Messages app. The system will help users verify another person's identity when users change devices. This is one of the many new features to be added in Android 16 later this year. We covered most of them already in previous editions of the newsletter, but you can check all of them out in one place on Google's blog .
Office apps to be supported until 2028: Microsoft has backtracked on its decision to end support for Office apps on Windows 10 on October 14 this year, when Windows 10 reached its EOL. The OS maker says it will continue supporting the apps for three more years until October 10, 2028 .
Microsoft retires Bing APIs: Microsoft will retire the Bing Search APIs on August 11, 2025 , and replace them with Azure AI Agents. The AI enshitification continues.
macOS clipboard privacy: Apple is introducing new macOS features that will allow users to block apps from accessing their clipboard. A similar feature has been available in iOS since 2020. The new clipboard privacy feature is scheduled for macOS 16, to be released later this year. [ Additional coverage in 9to5Mac ]
Apple adds scareware popups for EU users: Apple has added a scary warning popup for all apps in the EU that use an external payment system. I guess Apple is mad it can't leech and siphon off 30% of all sales anymore while also literally treating its developer ecosystem as the scum of the earth. [ Additional coverage in The Verge ]
ECH standard finalized: According to this blog post from Alphabet's Jigsaw division, the ECH standard is finalized, and IETF is expected to publish it in the coming weeks.
ICANN drops DEI: ICANN has dropped its diversity, equity, and inclusion (DEI) program following pressure from the US government. [ Additional coverage in DomainIncite ]
Major EU ruling in online advertising case: The Belgian Court of Appeal has ruled that the Transparency & Consent Framework (TCF), a system used by big tech companies to obtain consent for showing personalized ads online, is illegal under EU GDPR. The court ruled that the unique string assigned to users when they consent to tracking is personal data and can be used for tracking. The ruling basically confirmed that TCF is a sham meant to still allow big tech firms to track users across different websites in spite of the GDPR—and also another case of malicious compliance from a tech giant. [ Additional coverage in Heise ]
Government, politics, and policy
Tajikistan abolishes controversial social media law: Tajikistan abolished a controversial law that criminalized likes and reposts on social media networks. The law passed in 2018 and allowed authorities to prosecute users who commented, liked, or reposted content the state deemed terrorist and extremist in nature. Offenders faced up to 10-15 years in prison, and more than 1,500 people are currently serving prison sentences. President Emomali Rahmon asked for the law to be abolished last year after what he described as groundless and unreasonable criminal cases. [ Additional coverage in Gazeta.uz ]
Russia to fine game makers: The Russian Duma is deliberating a law that would fine gaming companies with up to 5 million rubles (~$65,000) for putting "anti-Russian" content in their games. [ Additional coverage in Izvestia ]
EU parties block spyware victims testimony: Italian victims of mercenary spyware were blocked from testifying in front of an EU civil liberties committee this week following objections from the EPP and ECR party blocks. [ Additional coverage in EU Observer ]
Hearing on spyware in Italy: Meloni Government spyed on civil society and journalists. EPP and ECR refused to hear from the victims. Our house owes them an apology @fcancellato.bsky.social @davidyambio.bsky.social @beppecaccia.bsky.social @lucacasarini.bsky.social @mattiaferraresi.bsky.social
— Saskia Bricmont (@saskiabricmont.bsky.social) 2025-05-13T13:52:55.485Z
TikTok broke EU DSA rules: The EU has charged TikTok with breaching the Digital Services Act by failing to publish information on its online ads. The EU says the company's failure has prevented researchers from detecting online scams, hybrid threat campaigns, and coordinated influence operations. Under the DSA, the company faces a fine of up to 6% of its global annual turnover. The preliminary ruling is in an investigation started in February last year. TikTok faces a second investigation into its role in Romania's canceled presidential election last year.
EU tells 19 countries to hurry up on NIS2: The European Commission has called on 19 member states to finish transposing the NIS2 cybersecurity directive into their national laws. States have two months to finish the process. The Commission says it will refer states that fail to meet their obligations to the EU Court of Justice.
US cancels misinformation study grants: The Trump administration has canceled research grants for US universities that focused on online censorship and disinformation. Officials claimed, without evidence, that the research was being used to censor American conservatives online. According to the New York Times , many of the cuts seemed arbitrary and even cut funding for tools designed to help Chinese users evade the Great Firewall and tools designed to detect AI-manipulated media.
Rogue devices in Chinese solar inverters: Security experts have found rogue undocumented communications devices in some Chinese solar power inverters deployed across the US power grid. Sources told Reuters the devices were not mentioned in the power inverter's documentation. Similar undocumented communication devices, including cellular radios, were also previously found in some Chinese solar batteries. US energy officials are allegedly re-assessing the risk posed by Chinese equipment installed on the US power grid.
NSA cyber director to retire: Dave Luber, the head of the National Security Agency's Cybersecurity Directorate, will retire at the end of the month. [ Additional coverage in The Record ]
US CFPB kills data broker protection rule: The US has scrapped new rules intended to limit the ability of US data brokers to sell the personal information of American citizens. The new rules were proposed last December by the US Consumer Financial Protection Bureau's previous leadership. Under the new Trump administration, CFPB acting director Russell Vought said the proposed rules are no longer "necessary or appropriate." The now-scrapped rules were introduced at the request of the US intelligence community, which argued data brokers could be abused by foreign actors to track Americans. [ Additional coverage in WIRED ]
"The agency withdrew the proposal & published a notice in the Federal Register declaring the rule no longer “necessary or appropriate.” 😳 The killed proposal's importance speaks for itself —titled “Protecting Americans from Harmful Data Broker Practices.” 🧾 Wired: www.wired.com/story/cfpb-q...
— Pam Spaulding (@pamspaulding.bsky.social) 2025-05-14T17:16:23.528Z
Sponsor section
In this Risky Bulletin sponsor interview, James Pope, Director of Technical Enablement, talks to Tom Uren about his experience running networks and security centers at Black Hat conferences around the world. Pope talks about the challenges of running a SOC at a hacker conference, how conference networks around the world have a different character and talks about all the weird and wonderful security snafus he has found.
Arrests, cybercrime, and threat intel
Europol dismantles scam network: Europol has dismantled a criminal network that ran fake investment websites and stole over €3 million from victims. The takedown took place across two phases, one in 2022 and one this week. Authorities arrested two suspects in the first raids and another one this week in Cyprus. Europol also identified and is still looking for seven other members of the gang.
Four sextortionists arrested: Authorities in Côte d'Ivoire have arrested four men who ran sextortion schemes across the globe. At least one teenager committed suicide after being extorted by the group, per the US Justice Department .
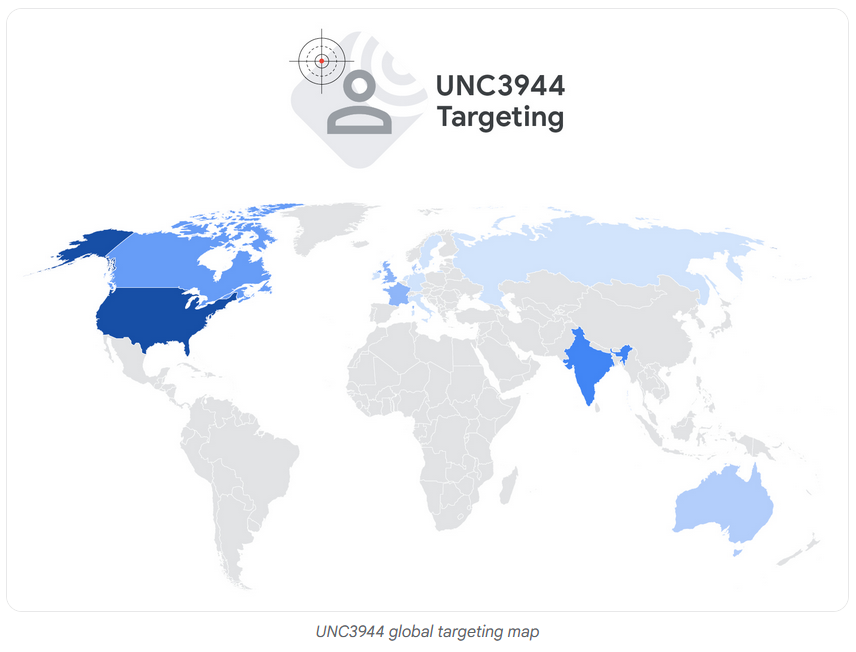
Scattered Spider shifts to US retailers: The hacking group that crippled the operations of three UK retail chains has now shifted its attention to American retailers. Google says it spotted recent Scattered Spider campaigns targeting the US, India, and other English-speaking countries. The group's new attacks come after a prolonged break following the arrest of some members early last year. Google's security team says the group laid low to establish new connections in the criminal underground and retool its arsenal before this year's campaign. [ Additional coverage in The Guardian ]
Novel legal strategy against hackers: Brian Krebs looks at a novel tactic used by a legal firm, which added the name of a hacker to a class-action lawsuit against a healthcare provider after the hacker was publicly named and detained by US authorities.
"Jill Fertel is a former federal prosecutor who runs the cyber litigation practice at Cipriani & Warner, the law firm that represented Nonstop Health. Fertel told KrebsOnSecurity this is the first and only case where a cybercriminal or anyone related to the security incident was actually named in civil litigation."
Ransomware gangs jump on SAP zero-day: At least two ransomware gangs are now abusing a recent SAP NetWeaver zero-day to breach corporate networks. SAP patched the zero-day at the end of April after reports of abuse in the wild. Several security firms have now linked the initial attacks to a Chinese APT. Security firm ReliaQuest says the BianLian and RansomEXX ransomware gangs are now also exploiting this, along with many other threat actors.
What crimz do with their stolen money: Sophos has published a five-part series on what cybercriminals do with all their stolen funds, how they launder it, and how they invest it. CyberScoop has a good summary.
"Through an examination of thousands of forum posts, we discovered a dark underbelly of fraud, theft, money laundering, shell companies, stolen and counterfeit goods, counterfeit currency, pornography, sex work, stocks and shares, pyramid schemes, gold, diamonds, insider trading, construction, real estate, drugs, offshore banking, money mules (people hired by launderers to physically or virtually transport/transfer money), smurfs (people hired to conduct small transactions in order to launder a larger amount), tax evasion, affiliate advertising and traffic generation, restaurants, education, wholesaling, tobacco and vaping, pharmaceuticals, gambling – and, believe it or not, cybersecurity companies and services ."
Scammers target tariff anxiety: Cybercrime groups are exploiting the anxiety over the recent Trump tariffs to scam victims and collect their personal data. Security firm Forcepoint has detected a spike in fake online stores that advertise huge discounts and non-tariffed goods. The stores impersonate popular brands and exploit the frustration shoppers feel towards rising prices.
Scammers pose as US officials: The FBI says threat actors are posing as US officials in smishing and vishing campaigns targeting US citizens.
Colombian scam network: Check Point has uncovered an auto insurance scam network operating out of Colombia.
"Since the beginning of 2024, we have identified over 100 fraudulent websites linked to this scheme, each crafted with guile, meticulousness, and precision to be a digital double of legitimate services and exploit unsuspecting victims."
Malicious PyPI packages: ReversingLabs has found a malicious PyPI package that targets cryptocurrency developers and tries to exfiltrate source code and developer secrets from infected machines. The company also found a second malicious package disguised as a debug utility, which they linked to a pro-Ukrainian hacktivist group named DumpForums.
Malicious npm package: Veracode researchers have spotted a malicious npm package that used Unicode-based steganography to hide malicious commands inside images and Google Calendar as a C&C system.
Jiang Jintao profile: The Natto Team has published a profile on Jiang Jintao , one of China's early hackers.
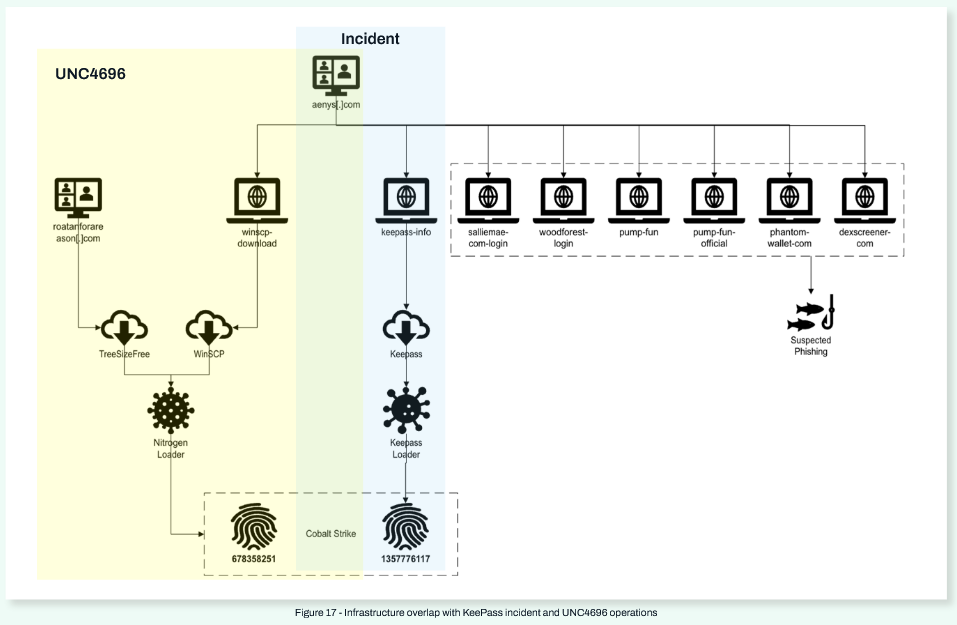
IAB spreads trojanized KeePass installer: An initial access broker and a known affiliate of the BlackBasta ransomware group is using malvertising to distribute a trojanized installer for the KeePass password manager. The purpose is to collect passwords stored in the modified KeePass app and then access corporate systems. According to WithSecure , the campaign has been taking place for at least eight months and has led to at least one successful ransomware attack.
Malware technical reports
Medusa ransomware: Intel471 has a report on the recent operations of the Medusa ransomware .
DarkCloud Stealer: God forbid we have a newsletter edition without an infostealer report. Today, it's DarkCloud Stealer . This infostealer has been around since 2022 but saw a resurgence in January and February.
FrigidStealer: macOS users snickering at Windows users, don't worry! You're not in the clear. Here's FrigidStealer , an infostealer that emerged in January and targeting your platform.
New PowerShell loader: Qualys has spotted a new PowerShell loader being used to deploy the Remcos RAT.
Skitnet/Bossnet: Prodaft has published a technical report on Skitnet (Bossnet), a new malware loader that has been sold under a MaaS model on underground forums since April 2024.
TransferLoader: Zscaler identified a new malware loader that we have named TransferLoader , which has been active since at least February 2025. For now, it's been used to deliver Morpheus ransomware.
Authentic Antics: The UK NCSC has published a malware analysis report on Authentic Antics, a piece of malware that runs in the Outlook process to show fake login screens and steal account credentials. [ Report PDF ]
Horabot: Fortinet says the Horabot malware is targeting users in Latin America. Horabot is a malware loader that also turns infected systems into spam senders.
Sponsor section
Volt Typhoon, a Chinese APT targeting critical infrastructure, is exploiting unmanaged appliances and evading EDR. Learn how the best defense against this and other advanced attacks is your network. Learn more .

APTs, cyber-espionage, and info-ops
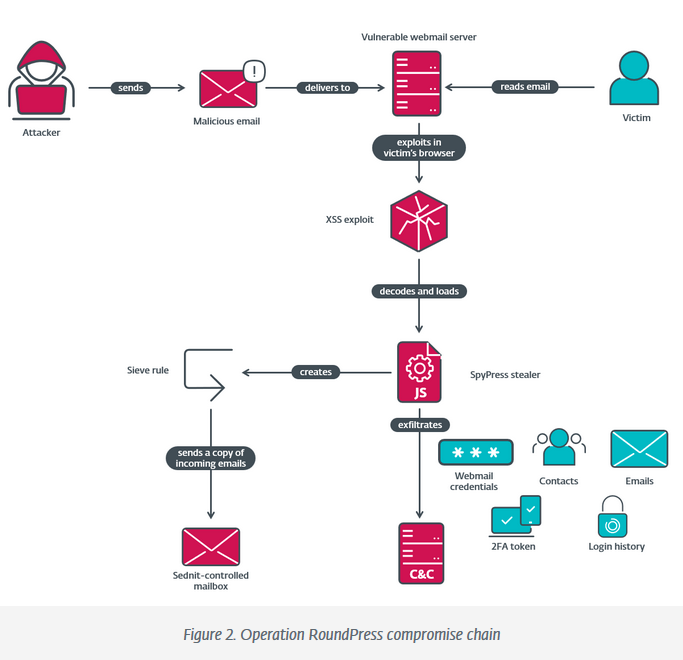
Operation RoundPress targets email servers: A Russian cyber-espionage campaign has targeted webmail servers with XSS vulnerabilities over the past two years. The campaign initially targeted RoundCube servers but has now expanded to include Horde, MDaemon, and Zimbra systems. The attacks involved malicious emails sent to a target's inbox and which contained XSS payloads. The exploits run when targets view their emails and typically collect and exfiltrate a victim's email credentials and content. Security firm ESET attributed the campaign to a group known as Sednit and APT28, linked to Russia's GRU military intelligence agency. The campaign mainly targeted Ukraine, its military defense industry, and its allies.
Google TAG bulletin: Google has published its first quarter report on coordinated influence operations it spotted on its platforms. The report mentions campaigns out of Russia, campaigns targeting Romania's political landscape, and Azerbaijani campaigns critical of Armenia.
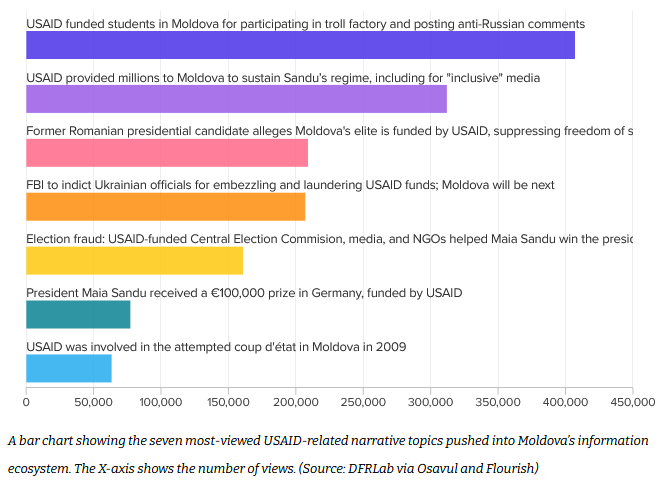
USAID info-op targets Moldova: A Russian influence operation is using the recent USAID shutdown to target Moldova's pro-EU parties and promote pro-Kremlin candidates ahead of the country's Parliamentary election this fall. DFRLab has linked the op to a Russian disinfo group known as Portal Kombat.
"Russian and Moldovan actors exploited cuts to USAID funding in a multifaceted approach that sought to delegitimize Sandu's administration and undermine democratic processes. The campaign portrayed Western support as a threat to Moldovan sovereignty by misrepresenting the US-funded programs as "troll factories" or mechanisms for election manipulation and media control."
Storm-1516 disinformation: One of Russia's elite disinformation units is behind a social media campaign designed to portray European leaders as drug addicts. According to security firm EclecticIQ , Russian disinformation group Storm-1516 used AI-generated content to claim the leaders of France, Germany, and the UK took drugs before visiting Kyiv this month. The manipulated images were widely pushed on Twitter and aimed to reduce public support for Ukraine and the nations that back it. The Russian Foreign Ministry and its spokesperson, Maria Zakharova, also boosted the campaign's themes in public messages and press conferences.

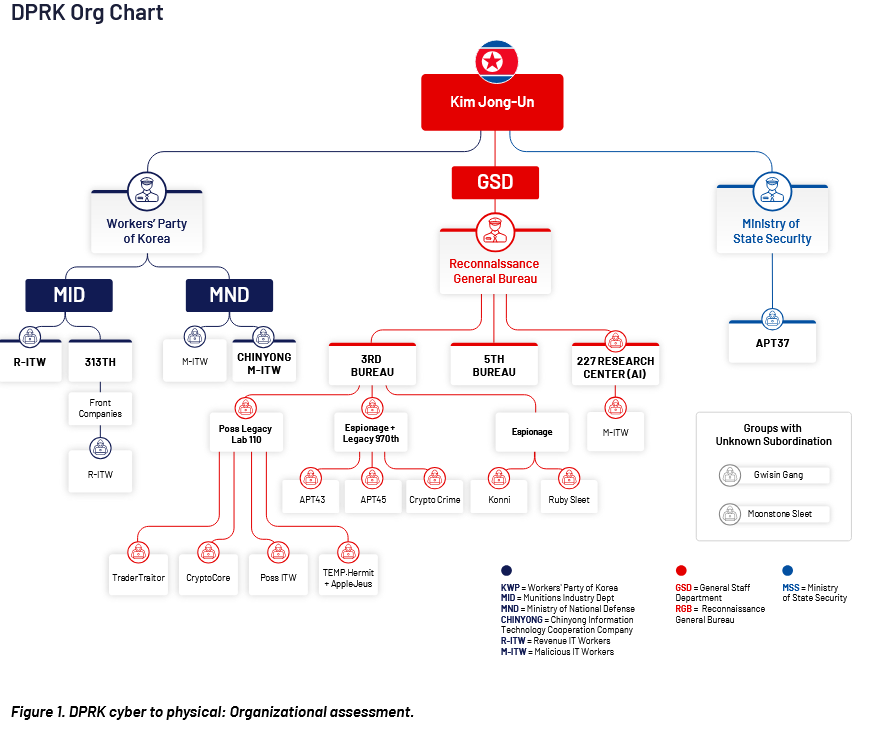
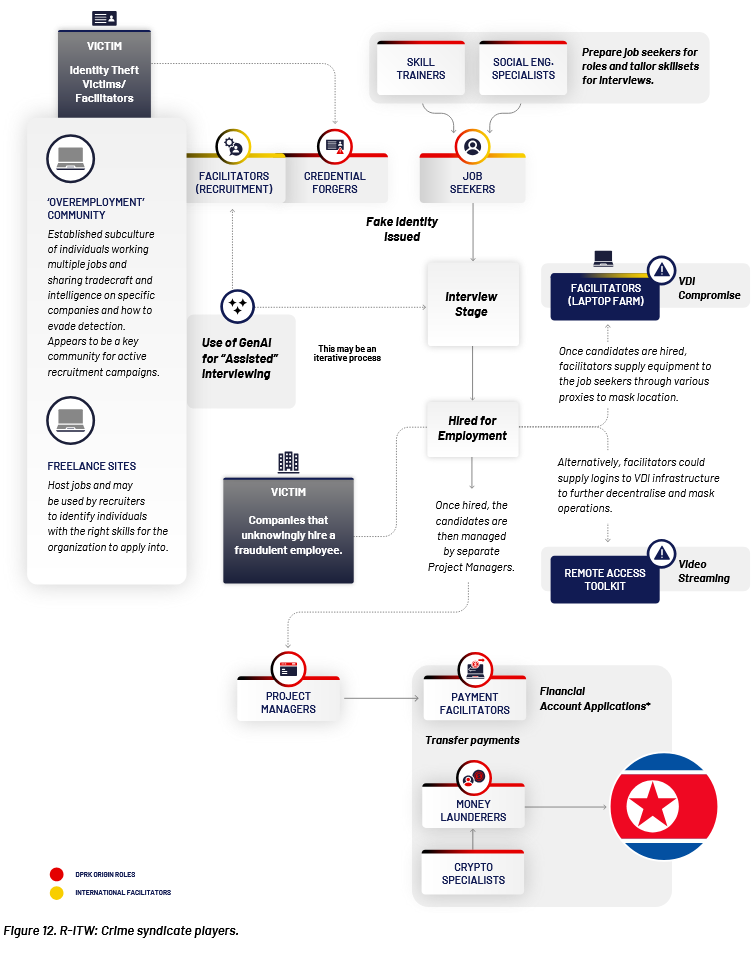
DPRK cyber and IT worker schemes: Security firm DTEX has published what is so far the most complete look at North Korea's cyber program and its foreign IT worker schemes. It's very hard for me to summarize the report, but if you want the most up-to-date look at North Korea's hacker ecosystem, this is the report for you. [ Report PDF ]
Vulnerabilities, security research, and bug bounty
VSC RCE in Restricted Mode: Starlabs researcher Devesh Logendran has published a write-up on a clever XSS bug in Visual Studio Code that could be elevated into an RCE inside the app's Restricted Mode. This wasn't patched—for reasons—but the bug isn't trivial to exploit either.
"An XSS vulnerability in the newly-introduced minimal error rendering mode for Jupyter notebooks enables arbitrary JavaScript code to be executed within the vscode-app WebView for the notebook renderer. The vulnerability can be triggered by opening a crafted .ipynb file if the user has the setting enabled, or by opening a folder containing a crafted settings.json file in VS Code and opening a malicious ipynb file within the folder. This vulnerability can be triggered even when Restricted Mode is enabled (which is the default for workspaces that have not been explicitly trusted by the user)."
Chrome zero-day: Google has released a security update to patch a Chrome zero-day exploited in the wild. Tracked as CVE-2025-4664, the zero-day can allow attackers to leak cross-origin data via malicious HTML pages. Solidlab security researcher Vsevolod Kokorin discovered the vulnerability and posted a public proof-of-concept online last month. Kokorin says the vulnerability could have been used for OAuth account takeovers. [ Additional coverage in Bleeping Computer ]
Invanti zero-day analysis: WatchTowr Labs has published a technical analysis of the two zero-days Ivanti patched in its EPMM product this week.
Hidden SAP zero-day patch: SAP apparently patched a zero-day in its May 2025 Patch Tuesday updates this week. The zero-day is tracked as CVE-2025-42999 and was allegedly used in an exploit chain with a previous zero-day that SAP patched at the end of April—CVE-2025-31324. If you wonder why you're only finding out about the exploitation only now, it's because SAP hid the exploitation details behind a login screen—again! [ Additional coverage in Bleeping Computer ]
Jenkins security updates: The Jenkins project has published five security updates for five of its plugins.
Infosec industry
Threat/trend reports: Action1 , Google TAG , Kaspersky , and Malwarebytes have recently published reports and summaries covering various infosec trends and industry threats.
Acquisition news: Email security giant Proofpoint has agreed to acquire Hornetsecurity, a German firm specializing in M365 security.
Pwnie Awards nominations: Are now open !
Pwn2Own adds AI category: Trend Micro has added AI as a category for its upcoming Pwn2Own Berlin hacking contest, set to be held during the OffensiveCon security conference this week.
Stratoshark donated to Wireshark: Cloud security firm Sysdig has donated the Stratoshark app to the Wireshark Foundation. Sysdig engineers designed Stratoshark as a Wireshark-like traffic inspection tool for cloud environments.
DEFCON wins defamation lawsuit: A judge has ruled in favor of security conference DEFCON in a defamation lawsuit filed by Christopher Hadnagy, a former host of one of its security villages. DEFCON banned Hadnagy in 2022 after it received several abuse reports from conference participants. Hadnagy sued, claiming the conference and its main organizer, Jeff Moss, had defamed him.
DEF CON legal update: Truth is a complete defense against defamation. The Hadnagy lawsuit against us is over. Summary judgement. Dismissed, with prejudice. You can read the judgment here storage.courtlistener.com/recap/gov.us... . Stay tuned for a more detailed report. #defcon #legalupdate
— DEF CON (@defcon.bsky.social) 2025-05-13T21:36:12.067Z
New tool—WizOS: Wiz, now part of Google Cloud, has released WizOS , a hardened Linux distribution based on Alpine Linux.
New tool—oniux: The Tor Project has released oniux , a command-line utility providing Tor network isolation for third-party applications using Linux namespaces. In normal words, it can hide any Linux app's traffic in the Tor network.
Black Hat Europe 2024 videos: Talks from the Black Hat Europe 2024 security conference, which took place last December, are available on YouTube .
Risky Business podcasts
In this special edition of the Seriously Risky Business podcast, Patrick Gray speaks with former NSA Cybersecurity Director Rob Joyce and former director of the CIA's Center for Cyber Intelligence Andy Boyd.
In this edition of Between Two Nerds, Tom Uren and The Grugq examine whether the US should steal intellectual property from Chinese companies.
