Risky Bulletin Newsletter
August 13, 2025
Risky Bulletin: Crypto-thieves turn their sights to Open VSX
Written by

News Editor
This newsletter is brought to you by Yubico . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
Crypto-thieves have found a new package repository to terrorize, and it's Open VSX , an independent database of Visual Studio Code extensions managed by the Eclipse Foundation.
While the VS Code editor has its official marketplace , Microsoft changed its licensing terms this year to block third-party code editors based on the original VS Code from using its marketplace to pull their extensions.
The change in policy, understandably, came after several AI-powered IDEs started cutting into VS Code's market share, all while Microsoft was paying to run and keep the VS Code marketplace online.
AI IDEs such as Cursor and Windsurf have since moved their plugin system to Open VSX, and have been encouraging developers to also upload their extensions to the portal.
But along with the move, the malware devs also came along. SecureAnnex founder John Tuckner has been tracking a campaign targeting Open VSX users for over a month.
The attackers upload malicious VS Code extensions on the portal that use hidden PowerShell scripts to install a hidden ScreenConnect client, a type of software used for remote management and monitoring.
Tuckner spotted the first signs of this campaign back in July, and Kaspersky also investigated an incident related to this campaign a week later.
The campaign targets blockchain and crypto developers and attackers use the SecureConnect client to sift through a developer's infected PC and then empty out their wallet.
The campaign is still ongoing, and blatantly malicious extensions are still being uploaded to Open VSX.
Looking at the code, the ENTIRE extension is malicious code. It runs a remote powershell script which installs ScreenConnect RMM giving access to your system the moment the extension is installed.
— tuckner (@johntuckner.me) 2025-08-12T17:07:42.458Z
Tuckner says major security upgrades will need to be made to Open VSX in the coming months to deal with the unwanted attention it's dealing with right now.
Install counts can be manipulated, the verification badge for developers is hard to spot, and the platform does no scanning even for the most basic malicious code.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
McDonald's Poland gets record GDPR fine: Poland's data protection agency has fined McDonald's Poland almost €4 million for leaking employee personal data. The leak occurred at a partner company that managed employee work schedules. Personal data such as names, passport numbers, positions, and work schedules leaked on the internet through an open directory. This is the second-largest GDPR fine handed out by Polish authorities. The agency fined the country's postal service €6.3 million earlier this year .
Yes24 ransomed again: A ransomware attack has disrupted the operations of South Korean online bookstore and ticketing platform Yes24 for the second time this year. The company's apps and websites went down on Monday morning but were restored by the afternoon. Yes24 suffered a similar ransomware attack in early June. [ Additional coverage in the Korea Herald ]
UWA incident: Staff and students at the University of Western Australia were locked out of their accounts after a security breach. UWA reset passwords for all accounts on Monday. The University said no other information appears to have been accessed. [ Additional coverage in 9News ]
Manpower breach: Staffing company Manpower has notified almost 145,000 users of a hack that exposed their personal data.
Data leak at Dutch cancer testing program: The personal data of almost 500,000 women was stolen from a Dutch cancer-testing program. The data was stolen from a third-party testing laboratory. It impacted women who tested for cervical cancer. The Dutch government hasn't identified the threat actor who stole the data.
Marks & Spencer restores service: British retailer Marks & Spencer has finally fully restored its online ordering system after a ransomware attack in April. [ Additional coverage in the BBC ]
Skibidi Farms hacked: A suspected child predator website named Skibidi Farms was allegedly hacked . Sorry, I'm not googling for that to confirm. I'm on enough FBI watchlists already.
Ransomware groups claim US defense contractors: Two ransomware gangs have claimed breaches of two major US military contractors. The World Leaks group claimed L3Harris , while the Play gang claimed an intrusion at Jamco Aerospace .
Pennsylvania AG cyber incident: A "cyber incident" is allegedly to blame for the downtime of the Pennsylvania AG website and its backend network. Officials say the incident targeted the network that hosts the AG's resources, but didn't say who it was exactly. [ Additional coverage in StateScoop ]
Russia suspected of US Courts hack: US investigators believe Russian hackers are behind a recent breach of the US Courts case management system. The hackers allegedly search for criminal cases involving people with Russian and Eastern European surnames. It is unclear if the hack is the work of Russian cyber units or cybercrime groups. The hack took place around the July 4th holiday, and hackers accessed the PACER and CM/ECF systems. [ Additional coverage in the NYT ]
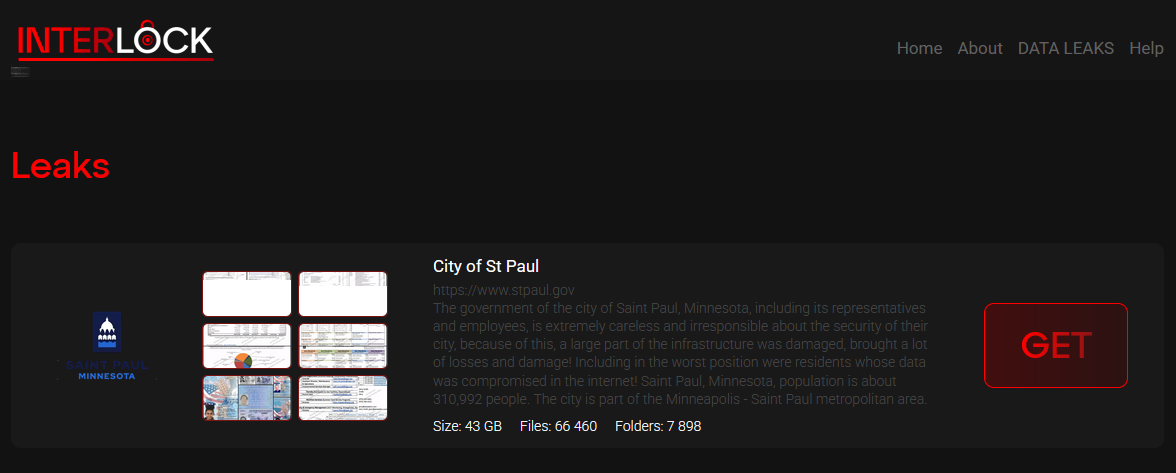
Interlock leaks St. Paul data: The Interlock ransomware gang has published over 43GB of files from the city of St. Paul, Minnesota. The group published the data after officials refused to pay the ransom. The city chose to recover and secure its network instead. It converted the Roy Wilkins Auditorium into a security center and asked employees to visit and secure accounts. More than half of the city's employees reset passwords and updated devices on Monday alone.
General tech and privacy
Reddit blocks the Wayback Machine: Reddit claims AI bots scraped its content off the Wayback Machine, so instead of suing AI companies, it is now blocking the Wayback Machine. [ Additional coverage in The Verge ]
Firefox AI issues: Firefox users are mad at Mozilla because of an AI component that drains their battery and hogs the CPU. [ Additional coverage in Neowin ]
GitHub funding helped 71 projects with security: Seventy-one open-source projects received funding from GitHub over the past nine months to improve their security. The funding was provided through the GitHub Secure Open Source Fund the company established last November. The projects received $10,000 to allocate to fixing security flaws over the next 12 months. According to GitHub , projects fixed more than 1,100 vulnerabilities and prevented the leak of over 90 secrets and tokens. Some of the largest projects that received funding include Node.js, Next.js, Bootstrap, Log4j, and Jupyter.
GitHub loses independence: Microsoft has moved GitHub under its CoreAI team after GitHub CEO Thomas Dohmke resigned this week. [ Additional coverage in The Verge ]
Wikipedia loses UK OSA lawsuit: A UK judge has dismissed the Wikimedia Foundation's challenge against the Online Safety Act. The court has ruled the Foundation has to start verifying visitors' age when accessing adult content on Wikipedia.
Data brokers are hiding opt-out pages: The Markup found that data brokers are hiding their opt-out pages from search engines, making it difficult for users to find and remove themselves from databases.
Government, politics, and policy
US Coast Guard cyber teams: Politico's John Sakellariadis has published a profile on the US Coast Guard cyber teams, which discovered unauthorized communications equipment in Chinese-made cranes deployed across US ports.
Russian software prices explode: A Kommersant report looks at how the Russian government might remove intellectual property rights from companies with a dominant and monopoly-like position on the market. The move appears to be caused by Russian software companies that raised prices by up to nine times after Western companies left the Russian market.
Russian telcos want to ban foreign IM calls: Four of Russia's largest telcos have petitioned the government to ban voice calls made via foreign instant messengers. The companies argued that a ban would return traffic to traditional voice calls and increase their revenue. Telcos said they need the revenue to support rising infrastructure maintenance costs. Returning voice calls to traditional systems would also improve the state's interception capabilities, with some IM calls being encrypted. [ Additional coverage in Forbes Russia ]
Russia expands SORM to 5G satellites: The Russian government is extending its SORM traffic interception system to 5G satellite communications. Operators will have to install SORM equipment at ground stations located in Russia. The new legislation is expected to go into effect in March next year. [ Additional coverage in RBC ]
Sponsor section
In this Risky Business sponsor interview , Tom Uren talks to Derek Hanson, Yubico's Field CTO, about making account recovery and onboarding for employees phishing-resistant. They also discuss the problems and opportunities of syncable passkeys.
Arrests, cybercrime, and threat intel
BEC lawsuit in the Netherlands: A judge in the Netherlands has ruled in favor of the victim in the country's first BEC-related lawsuit. A local car company was ordered to reimburse €27,000 to an Australian man who paid for a car in 2022. The company had its email account hacked, and scammers redirected the payment to their own bank accounts. The customer sued after the company refused to deliver the car or reimburse the payment. [ Additional coverage in Security.nl ] [ h/t Dirk ]
DOJ seizes BlackSuit funds: The US Department of Justice says it seized over $1 million from the wallets of the BlackSuit ransomware group. That's just a meager part of the $370 million that US officials estimate the group has made since 2022.
Wrench attacks increase: Physical attacks on cryptocurrency holders have increased sharply this year. At least one Bitcoin owner gets kidnapped every week and is often tortured for access to their wallet. According to SatoshiLabs, many of the attacks are driven by data leaks from cryptocurrency exchanges. [ Additional coverage in CoinTelegraph ]
VexTrio scams: Infoblox has published new data on the VexTrio group's scam empire, covering everything from websites to malicious desktop and mobile apps.
Brute-force campaign targets Fortinets: A brute-force campaign is targeting Fortinet devices. The campaign started on August 3 and is still ongoing. It first targeted Fortinet VPNs and later shifted to FortiManager devices. Almost 800 unique IPs were involved in the attacks in a single day, representing the highest volume GreyNoise has seen in recent months.
XZ Utils backdoor still around: Binarly has found 12 Docker images that still contain the backdoored version of the XZ Utils library.
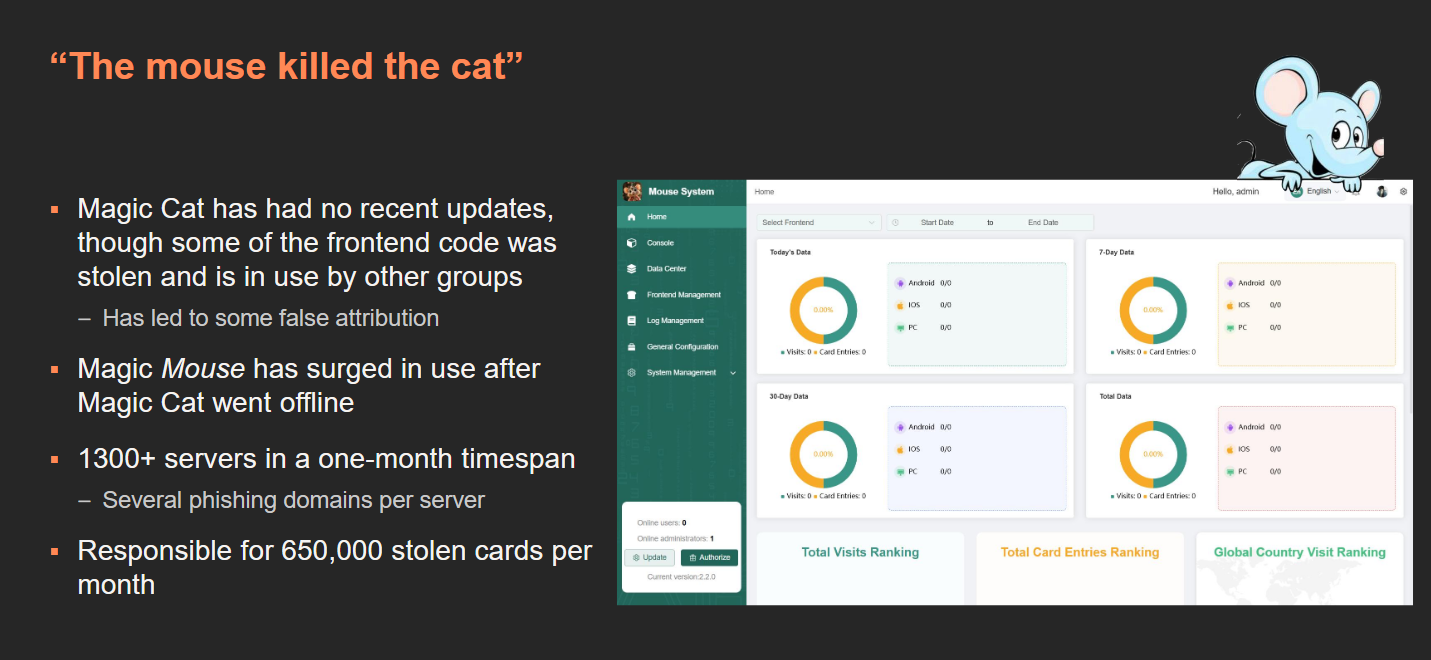
Magic Mouse PhaaS: After it was exposed earlier this year in a joint investigation , security firm Mnemonic believes the Magic Cat (Darcula) Phishing-as-a-Service platform is now back under a new name of Magic Mouse. [ Additional coverage in TechCrunch / DEF CON talk PDF ]
XSS forum is attempting a comeback: The mod team of the recently seized XSS (DamageLab) hacking forum is attempting a comeback under the name of DamageLib .
Cybercrime Super Friends: ReliaQuest looks at how members of the Scattered Spider and ShinyHunters groups joined forces to hack Salesforce customer accounts and then extort the companies for major paydays.
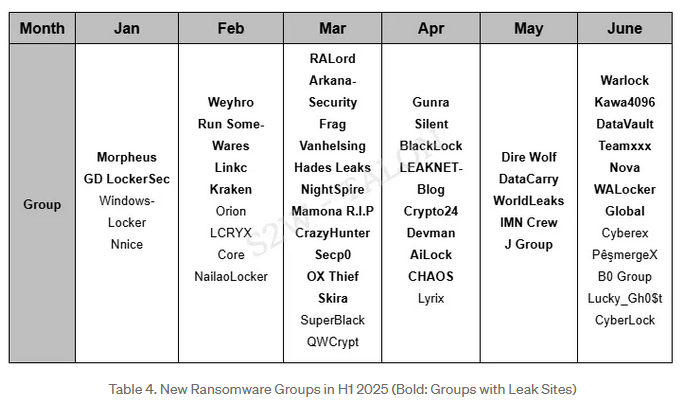
New ransomware groups: South Korean security firm S2W has spotted 51 new ransomware groups in the first half of the year, eight more than the same period last year.
Malware technical reports
Cmimai Stealer: K7 researchers look at a new infostealer that appeared in June, named Cmimai Stealer , and coded in VBS.
Raven Stealer: CyFirma has spotted a new C++ and Delphi-based infostealer advertised under the name of Raven Stealer . For now, it seems to target only Chromium-based browsers.
DarkBit free decryptor: Israeli security firm Profero has developed a decryptor for the DarkBit ransomware. The decrypter exploits a weak key generation algorithm used by the DarkBit group to brute-force the decryption key. The DarkBit group launched in 2023 and is believed to be associated with the MuddyWater Iranian espionage group. Profero has not released the decryptor but has offered to help any of the group's past victims.
Charon ransomware: Trend Micro researchers have spotted a new ransomware group called Charon . Researchers say the ransomware was spotted in targeted attacks against the Middle East's public sector and aviation industry. It also exhibits advanced APT-style techniques.
SmartLoader distributed through GitHub: AhnLab looks at a campaign that used IT software-related GitHub projects to distribute apps infected with the SmartLoader .
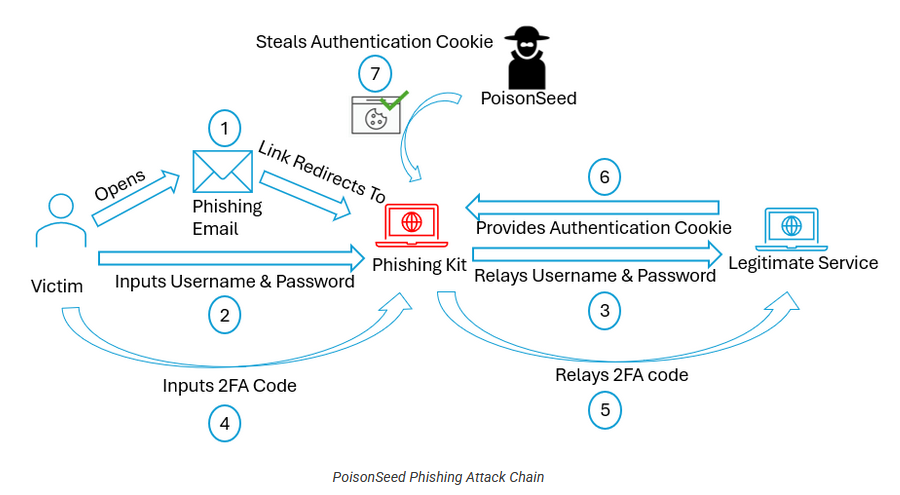
PoisonSeed's phishing kit: NVISO has published a technical analysis of a phishing kit used by the PoisonSeed group. NVISO says the group overlaps with what other companies call Scattered Spider and CryptoChameleon. The phishing kit has been used in phishing campaigns targeting crypto owners.
Sponsor section
In this sponsored interview, Patrick Gray talks to Yubico's COO and President, Jerrod Chong, about a new YubiKey feature: pre-registration. You can now ship pre-registered Yubikeys to your staff, so you don't need to rely on your staff to enrol them. They've achieved this with really slick Okta and Entra ID integrations.
APTs, cyber-espionage, and info-ops
Chinese firm linked to AI-driven info-ops: The Chinese government is using AI companies to monitor and manipulate public opinion on social media. A company named GoLaxy has run influence operations targeting Hong Kong and Taiwan with the help of AI tools. GoLaxy used a tool named GoPro to build psychological profiles and then deployed bot networks to sway public opinions. The company allegedly removed blog posts mentioning work with the Chinese government after being exposed. [ Additional coverage in NextGov ]
UNC3886 profile: Picus Security has published a profile and TTPs from UNC3886 , a suspected Chinese APT that recently hacked a critical infrastructure operator in Singapore.
New Curly COMrades APT: A new Russian cyber-espionage group has been spotted targeting Georgia and Moldova. Attacks from the Curly COMrades group coincided with Russian influence operations pushing pro-Kremlin geopolitical shifts in both countries. The attacks targeted judicial and government bodies in Georgia, and an energy distribution company in Moldova.
RomCom also abused WinRAR zero-day: Slovak security firm ESET says a recent WinRAR zero-day was also abused by the RomCom APT. Previously, BI.ZONE said the Paper Werewolf APT also launched attacks with the same vulnerability. ESET says RomCom was first.
Possible Kimsuky leak: Two hackers have leaked files from the backend of a state-sponsored hacking group. The files contain phishing kits, stolen data, and targeting information. The two leakers claim the server belongs to Kimsuky, a North Korean state-sponsored espionage group. The two say the stolen data suggests the group might also carry out operations for China and might also include Chinese-speaking members. A more complete analysis of the data will be published in the Phrack magazine this week. [ Additional coverage in DarkReading / Phrack files PDF ]
Hahahahaha
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-08-11T21:25:23.127Z
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the August 2025 Patch Tuesday. We had security updates from Adobe , Microsoft , SAP , Ivanti , Fortinet , Check Point , Supermicro , Intel , AMD , NVIDIA , AMI [ PDF ] , Dell , SolarWinds , Schneider Electric , Siemens , ABB , Zoom , Synology , Axis , and ServiceNow . The Android Project , Qualcomm , D-Link , Cisco , Splunk , QNAP , Arm , Chrome , Drupal , Autodesk , Trend Micro , Elastic , Facebook , 7-Zip , WinRAR , and Moxa released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 107 vulnerabilities . No zero-days this month.
Vulnerable car maker portal: A security researcher has found severe vulnerabilities in the online dealership portal of a major carmaker. Eaton Zveare says the bugs could have allowed attackers to create their own admin accounts. The vulnerabilities resided in the portal's login system and were patched in February. Zveare told TechCrunch he won't name the carmaker. [ DEF CON talk PDF ]
On-board routers expose smart buses to hacks: An unpatched vulnerability can allow hackers to take over routers installed on smart buses and then hijack critical bus systems. The vulnerabilities impact routers from BEC Technologies, commonly installed on smart buses in Taiwan. Attackers can bypass authentication and access the router's management panel. According to Trend Micro, attackers can easily escalate access from the router to critical systems that manage collision detection, traffic sign recognition, and GPS tracking. Researchers say they notified the router maker, but the company failed to prepare a patch. [ Additional coverage in SecurityWeek /DEF CON talk PDF ]
Unpatched OpenHands AI bug: All Hands AI has failed to patch a prompt injection vulnerability in its OpenHands AI coding agent that can lead to remote code execution attacks.
Erlang/OTP SSH attacks: PAN's Unit42 looks at the recent attacks targeting CVE-2025-32433, an unauth RCE in the Erlang/OTP SSH client. Around 70% of the attacks targeted OT networks, but that's also where this thing is mostly deployed.
Heracles attack: Academics have developed a new attack that can leak sensitive data from cloud environments and confidential VMs that rely on AMD's SEV-SNP technology. The new Heracles attack exploits the process of moving confidential data to a new memory location. The attack was successfully used to leak kernel memory, cryptographic keys, user passwords, and web sessions. AMD released patches this week.
L1TF Reloaded attack: Academics have found new ways to exploit the L1 Terminal Fault (Foreshadow) CPU side-channel attack. The new attack, dubbed L1TF Reloaded , combined the original attack with other vulnerabilities and was used in experiments to leak sensitive data from VMs running on public clouds—except AWS , apparently.
"Moreover, with an average end-to-end duration of 15 hours to leak the TLS key of an Nginx server in a victim VM under noisy conditions, without detailed knowledge of either host or guest, the attack is realistic even in one of today's biggest and most important commercial clouds."
SleepWalk attack: Academics have developed a new hardware attack that exploits context switching and CPU power consumption to leak sensitive data like encryption keys. The attack is named SleepWalk .
There's just so much here than your usual side-channel analysis approaches. 1: A single power spike caused by an OS-level context switch, like the kernel sleep function, gives ya exploitable information. This means that only the amplitude of that one spike per sample is enough to recover secrets
— Daniel Cuthbert (@dcuthbert.bsky.social) 2025-08-12T13:48:20.222Z
Infosec industry
Threat/trend reports: Check Point , Dragos , Picus Security , Radware , S2W , and Thinkst have recently published reports and summaries covering various infosec trends and industry threats.
New tool—RoboDuck: South Korean security firm Theori has released RoboDuck , a Cyber Reasoning System (CRS) that ranked third in DARPA's AI Cyber Challenge (AIxCC).
"Our system is unique among the competitors in that it has a full pipeline to develop Proofs of Vulnerability (POVs) without fuzzing, symbolic execution, or related techniques."
New tool—Sanctum: Security researcher Fluxsec has released Sanctum , a proof-of-concept EDR written in Rust.
New tool—AI Agents Attack Matrix: Security researcher Michael Bargury has released the AI Agents Attack Matrix , a database of TTPs used to target GenAI-based systems, copilots, and agents.
Pwnie Awards 2025: The Pwnie Awards for the best hacks and security bugs were handed out on Saturday at the DEF CON security conference. Heise has a summary of who won what.
DEF CON 33: Slides and other materials from the DEF CON 2025 security conference, which took place last week in Las Vegas, are available on the conference's website .
WHY 2025 videos: Talks from the What Hackers Yearn 2025 security conference, which took place over the weekend in the Netherlands, are available on YouTube .
Risky Business podcasts
In this edition of Between Two Nerds , Tom Uren and The Grugq dissect the Belarusian Cyber Partisans hack of Russian airline Aeroflot. Despite the short-term impact, the airline will likely bounce back quite quickly. But it is still a big win for the Cyber Partisans.
