Risky Bulletin Newsletter
October 10, 2025
Risky Bulletin: EU scraps Chat Control vote
Written by

News Editor
This newsletter is brought to you by Corelight . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
The European Union has scrapped next week's vote on Chat Control, proposed legislation that would have mandated tech companies to break their encryption to scan content for child abuse materials.
The project was supposed to be put to a vote on Tuesday, October 14, during a meeting of interior ministers of EU member states.
Denmark, which currently holds the EU presidency and was backing the legislation, scrapped the vote, according to reports on Austrian and German media.
Danish officials scrapped the vote after failing to gather the necessary votes to pass the legislation and advance it to the EU Parliament.
Only twelve of the bloc's 27 members publicly backed the proposal, with nine against, and the rest undecided.
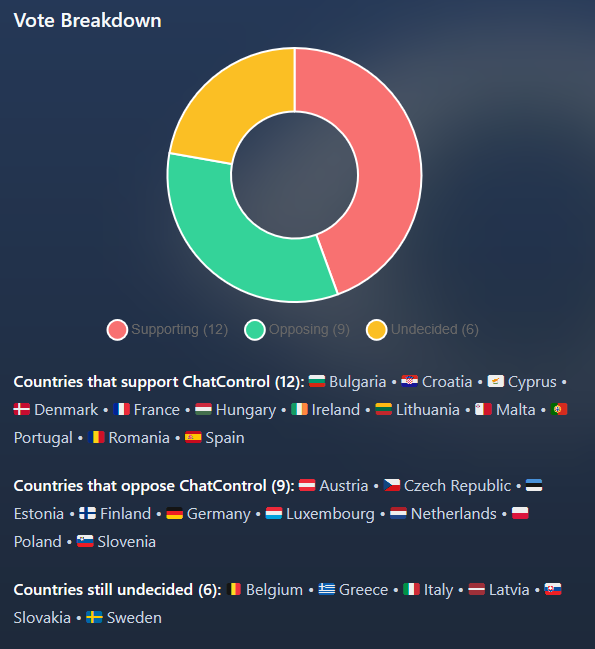
The final blow to Chat Control came over the past two weeks when both the Netherlands and Germany publicly opposed it.
Germany's Justice Minister, Dr. Stefanie Hubig, went out of her way to describe Chat Control as a " taboo for the rule of law ," arguing that the fight against child pornography does not justify removing everyone's right to privacy.
The law has seen the usual mass opposition from privacy groups, such as the EFF , but also from the tech sector, too, with over 40 major EU tech companies signing an open letter to EU officials.
Signatories described Chat Control as a "blessing for US and Chinese companies," since EU users will migrate to products that respect their privacy and ignore Chat Control.
The Chat Control opposition also received major help from a Danish programmer, whose Fight Chat Control website allowed Europeans to mass-mail their representatives and urge them to vote against.
According to a Politico Europe report, the website had driven so much traffic that it "broke" the inboxes of EU members of Parliament over the past weeks.
Risky Business Podcasts
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about the Clop ransomware gang. It is interesting because the group has arrived at a strategy that rinses a whole lot of enterprises at once and comes with a decent payday. But it's actually the least damaging kind of ransomware. Tom wonders why more gangs can't be like Clop?
Breaches, hacks, and security incidents
Salesforce will not pay the ransom: Salesforce will not pay a ransom demand to the hackers who launched an extortion website last week. The Scattered Lapsus$ Hunters group demanded a large payment from Salesforce, or they would publish customer records. The group claimed to have stolen almost one billion records from 40 Salesforce customers. The data was hacked earlier this year from SalesLoft, a Salesforce subsidiary that runs a sales-focused AI chat agent. [Addition coverage in Bloomberg ]
Qantas impacted by Salesforce breach: According to the Australian Broadcast Corporation , local airline Qantas was one of the tens of companies that had its data stolen from its Salesforce account. The hackers are threatening to release this data on Friday.
Also, Telstra: According to CyberDaily , Australian telco Telstra was also one of the affected companies, but the company is denying it.
Williams & Connolly hack: One of the most prominent US law firms has notified customers of a security breach. Williams & Connolly says Chinese government hackers have breached some of its attorneys' email accounts. The law firm represents several high-ranking US politicians. Google's security team warned at the end of September about a Chinese hacking campaign targeted US law firms this year using zero-days in network appliances. [ Additional coverage in CNN ]
Discord breach update: Discord says a breach of its Zendesk environment only impacted 70,000 users . On the other hand, the hackers claim to have stolen the data of 5.5 million users .
MySonicWall security breach update: All SonicWall customers who used the company's cloud backup service are affected by last month's data breach. SonicWall initially said that only 5% of customers had device configurations stolen in the attack. The company has updated its breach notification page after finishing its investigation. Customers were told to reset firewall credentials following the incident.
Another Paragon victim identified: Italian businessman Francesco Gaetano Caltagirone is one of the 90+ Italians who were notified by Apple in January that they had their phones infected with Paragon's Graphite spyware. [ Additional coverage in TechCrunch ]
General tech and privacy
Thunderbird donations: The Mozilla Thunderbird email client received a whopping $10.3 million in donations last year.
Docker makes hardened images affordable: Docker says that an "add-on subscription" will now get developers and small companies unlimited access to security-hardened images. These are server images managed by Docker that are constantly being updated and patched for the most recent security flaws.
Microsoft will move GitHub to Azure: After removing independence from its GitHub division and placing it under its cloud operations, Microsoft is now prioritizing moving all of GitHub's servers to Azure infrastructure. The move is so important that all new feature development has effectively stopped until the migration is complete. [ Additional coverage in The New Stack ]
Telenor sued in privacy lawsuit: Norwegian telecommunications company Telenor has been sued for human rights abuses. Plaintiffs claim the company's subsidiary, CelcomDigi, unlawfully shared customer data with the Myanmar military junta. The data was allegedly used to hunt and imprison dissidents. A military junta overthrew Myanmar's democratically elected government in a 2021 coup. [ Additional coverage in Malaysiakini ]
Apple removes Eyes Up app: Apple has removed an app that allowed users to archive videos of Immigration Customs and Enforcement arrests and abuses. The app allowed users to download and save videos uploaded to multiple social media networks. A few days earlier, both Apple and Google also removed ICEBlock, an app that tracked sightings of ICE officers. [ Additional coverage in Engadget ]
A good reminder that Big Tech is a handmaiden to fascism. www.404media.co/apple-banned...
— Jonathan Cohn (@jonathancohn.bsky.social) 2025-10-08T19:38:35.125Z
Government, politics, and policy
CISA workers reassigned to immigration enforcement: The DHS has reassigned CISA cyber specialists to jobs supporting President Donald Trump's deportation agenda. CISA employees were moved to ICE, CBP, and the Federal Protective Service. According to Bloomberg , workers were given a week to accept the role or resign. Some of the reassignments included relocations to new geographic areas.
A bunch of folks have told me about this over the past few days. Patrick has good details here. "It seems like it’s in an effort to get them to quit instead of firing them," a US official told me. I'm off for the rest of the week (timing!) but I'll have a story on this shortly after I get back.
— Eric Geller (@ericjgeller.com) 2025-10-08T23:45:29.158Z
California enacts opt-out law: California Governor Gavin Newsom signed a bill into law that will require browser makers to allow Californians to opt out of having their personal data sold. Browser vendors will have to add a new setting that will notify web companies that their data is not for sale. The law specifically dictates that this mechanism be implemented in the browser instead of popups, having learned from the EU cookie banner disaster. [ Additional coverage in The Record ]
US Appeals Court halts FCC data breach rules: A US Appeals Court has halted the FCC's data breach reporting rules for telecom providers. The court suspended the case after the FCC's new leadership asked to reevaluate the rules itself. The rules were passed during the previous Biden administration and required telecom providers to notify victims of security breaches within 30 days. US telco industry groups sued the FCC last year arguing that the agency overstepped its authority. The Appeals Court initially sided with the FCC in August before the agency sabotaged its own case. [ Additional coverage in Cablefax ]
China cleanses its internet: China's cybersecurity agency has launched a campaign to remove posts from the Chinese internet that express negative or pessimistic emotions. Chinese social media platforms will have to scan and remove all negative content within the next two months. The campaign targets social networks, short videos, and live broadcast content. The move comes after Chinese youth have complained online of their bleak future and the lack of jobs. [ Additional coverage in The Independent Singapore ]
UK fund for Balkan cybersecurity: The UK government has announced a £4 million project to help countries in the Western Balkans improve their cyber defenses.
Ukraine passes Cyber Forces law: The Ukrainian Parliament passed a law to establish a national cyber force. The new Cyber Forces Command will answer directly to Ukraine's commander-in-chief. It will be composed of regular recruits and a reserve force. Civilians will be able to join the cyber reserve force on a temporary basis to carry out tasks without formally joining the military. [ Additional coverage in the Kyiv Independent ]
Cyber irregulars, baby! [Service] “does not require formally becoming a military service member and can be carried out on a temporary or periodic basis….” Sounds like it’s formalizing the freelancers, pretty much the current state of online conflict?
— Sig. Ug. (@sigug.bsky.social) 2025-10-09T12:07:25.775Z
Sponsor section
In this Risky Business sponsor interview , Catalin Cimpanu talks with Ashish Malpani, Head of Product Marketing at Corelight. The discussion looks at how NDRs might evolve, such as expanding to protect inter-cloud networks and complementing EDRs.
Arrests, cybercrime, and threat intel
Kido hackers arrested: UK police have arrested two teenagers for hacking and extorting a London nursery. Both teens are aged 17 and are based in Bishop's Stortford, in Hertfordshire. The duo hacked the Kido nursery chain last month and published the data of young children on the dark web, seeking to obtain a ransom. They went online under the name of the Radiant Group.
Kasatkin case in France: A Russian basketball player accused of being a ransom negotiator for the Conti group has contested the evidence of French authorities. Daniil Kasatkin's legal team claims there is no hard evidence to link him to any criminal activity. Lawyers claimed Kasatkin didn't own the Gmail address listed in court documents and that the IP address was also a VPN node. According to French cybersecurity report Gabriel Thierry , the defense also claimed that some of the dates also coincide with championship tournaments. Kasatkin was arrested in June, and US authorities are also seeking his extradition.
TwoNet targets OT/ICS networks: A Russian hacktivist group named TwoNet claimed the hack of a water treatment facility that ended up being just a Forescout honeypot. The hack was part of a larger campaign targeting internet-exposed OT and ICS networks.
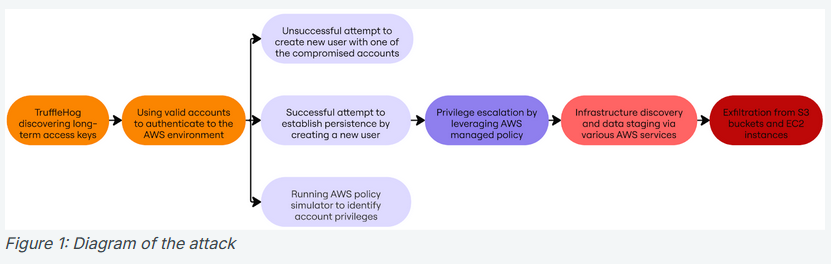
Crimson Collective goes after AWS environments: The hack against software giant Red Hat is part of a larger campaign that is targeting AWS cloud accounts. A group named the Crimson Collective is using compromised IAM accounts to access and pilfer corporate AWS environments. According to Rapid7 , the group is currently focused on data theft for future extortion campaigns.
New ClickFix variation: Expel looks at a new and more stealthy ClickFix variation that leverages cache smuggling to avoid downloading malicious files in an attempt to reduce detection.
Oracle E-Business Suite exposure: Censys has identified more than 2,000 Oracle E-Business Suite platforms connected to the internet. These platforms have been targeted with a zero-day in a hack-and-extort campaign linked to the Clop gang.
Velociraptor abuse: Cisco Talos and Rapid7 have spotted a ransomware group (Storm-2603) abusing the Velociraptor open-source DFIR tool in its attacks. They installed an older version of the tool and then used a vulnerability to elevate privileges. They then used the tool to download and run Visual Studio Code, abusing that app's tunneling feature for stealthy comms.
"Talos assesses with moderate confidence that this activity can be attributed to the group Storm-2603 , based on overlapping tools and TTPs. Storm-2603 is a suspected China-based threat actor first identified in July 2025, when they began exploiting the on-premises SharePoint vulnerabilities known as ToolShell."
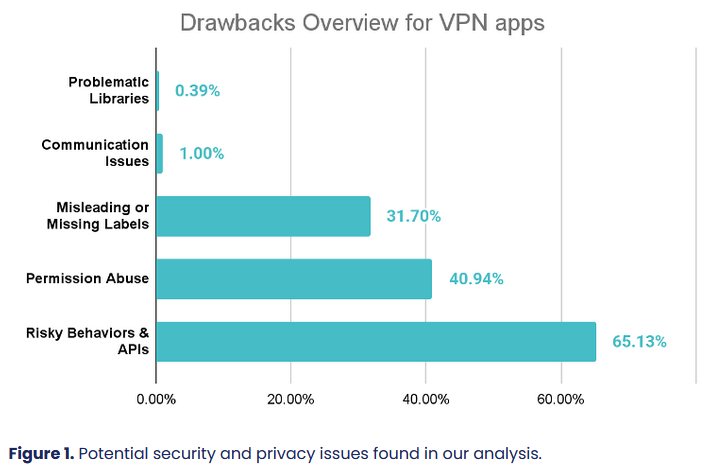
Free VPNs are useless: A study of 800 free mobile VPN apps has found that most are plagued by security flaws, abusive permissions, and the use of sensitive and risky APIs.
Russian Market profile: Rapid7 has published a profile of the Russian Market , today's top online shop for selling hacked credentials. More than 30,000 stolen credentials are being added to the portal each month, with over 180,000 put up this year.
PBaaS ecosystem: Infoblox looks at the emergence of a Pig-Butchering-as-a-Service ecosystem, driven by the explosion of scam compounds across Southeast Asia. The company says many of these services can be tracked using DNS data trails.
Storm-2657 profile: Microsoft has published a profile on Storm-2657 , a financially motivated threat actor that breaches US universities to hijack employee payroll payments.
New CipherWolf RaaS: A new ransomware-as-a-service named CipherWolf is being advertised on underground hacking forums, per SOCRadar .
New Kryptos ransomware group: A new ransomware gang launched its dark web leak site this week, the Kryptos gang. The site currently lists three victims.
Malware technical reports
RondoDox botnet grows massive: Trend Micro says that a botnet named RondoDox that launched earlier this year has grown to a massive size and is now exploiting more than 50 vulnerabilities across 30+ different vendors.
macOS infostealers: Red Canary looks at the main differences between Atomic, Odyssey, and Poseidon, the top three biggest infostealers targeting macOS devices.
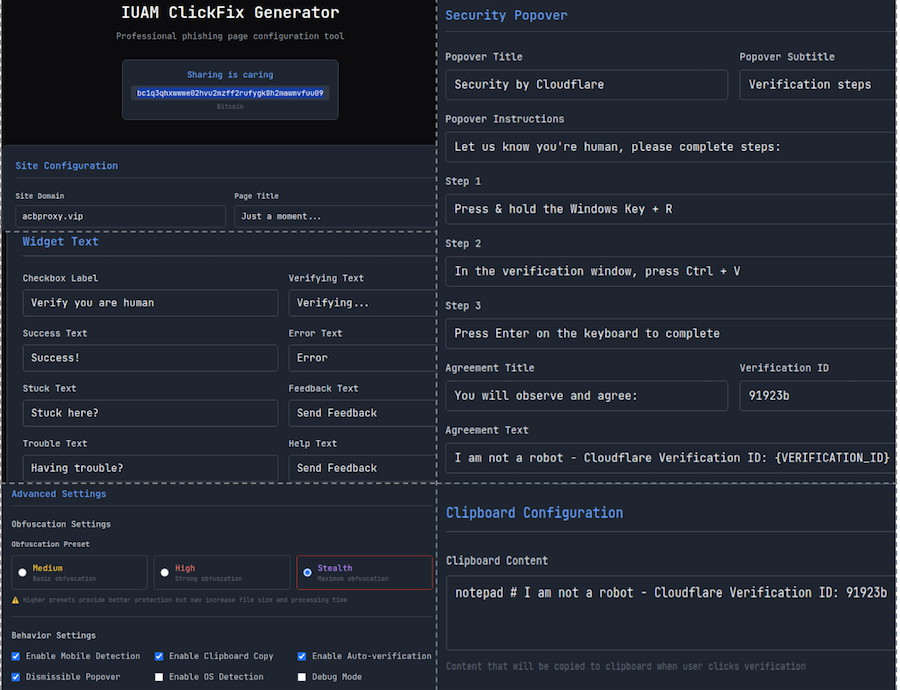
IUAM ClickFix Generator: PAN's Unit42 looks at IUAM ClickFix Generator , a new phishing kit designed to produce phishing pages with a built-in ClickFix challenge.
Sponsor section
James Pope, Corelight's Director of Technical Marketing Engineering, demonstrates the company's Open NDR Platform and how it combines network detections with a whole host of other data sources.
APTs, cyber-espionage, and info-ops
OpenAI disrupts PRC espionage operations: OpenAI's security team banned ChatGPT accounts used by Chinese state-sponsored hackers to write spear-phishing emails. The accounts were allegedly used by groups tracked by the infosec industry as UNK_DROPPITCH and UTA0388 . The emails targeted Taiwan's semiconductor industry, US academia, US think tanks, and organizations representing Chinese minorities. OpenAI says threat actors primarily abuse its service to improve phishing messages, rather than write malware, which is also what threat intel company Intel471 has observed.
UTA0388: Volexity has a more detailed report on the UTA0388 APT operations and its (ab)use of AI services for its phishing operations, although not that much info on targeting and general ops.
Chinese APT Nezha abuse: Huntress has spotted threat actors abusing the open-source Nezha remote management and monitoring agent in recent intrusions. Based on the victims, the attacker appears to be a Chinese cyber-espionage operation, but Huntress has not formally attributed it.
"What began with a creative way to drop a web shell onto the system quickly escalated into a multi-stage attack that demonstrated a clear focus on stealth and persistence. Tools, malware, IP addresses, domains, and victim demographics all appear to point towards a capable China-nexus threat actor who has been underreported on."
Vulnerabilities, security research, and bug bounty
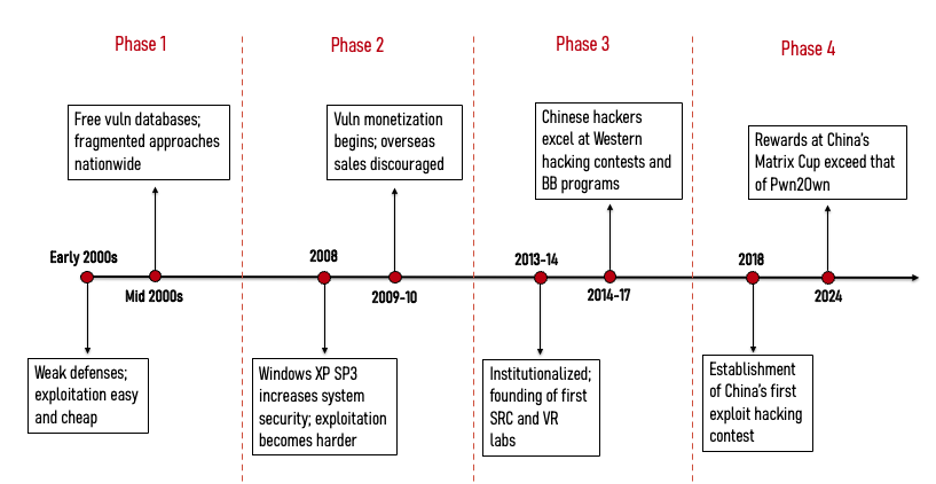
China's vulnerability research ecosystem: The Natto Thoughts team looks at how the Chinese vulnerability ecosystem has evolved over the past two decades.
Oracle EBS exploitation: A recent zero-day in the Oracle E-Business Suite has been exploited in the wild since July. It was one of multiple Oracle EBS vulnerabilities exploited by the Clop extortion group. According to Google's Mandiant division, the group has successfully breached dozens of Oracle customers and is now in the extortion phase of its operation.
KEV update: CISA has updated its KEV database ( twice ) with two vulnerabilities that are currently exploited in the wild. This includes a recent Zimbra zero-day and a Grafana 2021 bug.
RediShell PoC: Project Discovery researcher Dwi Siswanto has released a PoC for the recent RediShell Redis vulnerability .
WP plugin exploitation: Threat actors are exploiting a vulnerability in the Service Finder Bookings Plugin, a plugin included with the Service Finder commercial theme.
"This theme has been sold to approximately 6,000 customers. This vulnerability makes it possible for an unauthenticated attacker to gain access to any account on a site including accounts with the 'administrator' role."
CamoLeak vulnerability: Legit Security has found a vulnerability in the GitHub Copilot Chat that allowed silent exfiltration of secrets and source code from private repositories. The attacker could have also modified Copilot responses to return malicious code.
Framelink Figma RCE: Imperva has discovered a remote code execution bug in the Framelink Figma MCP server, now tracked as CVE-2025-53967.
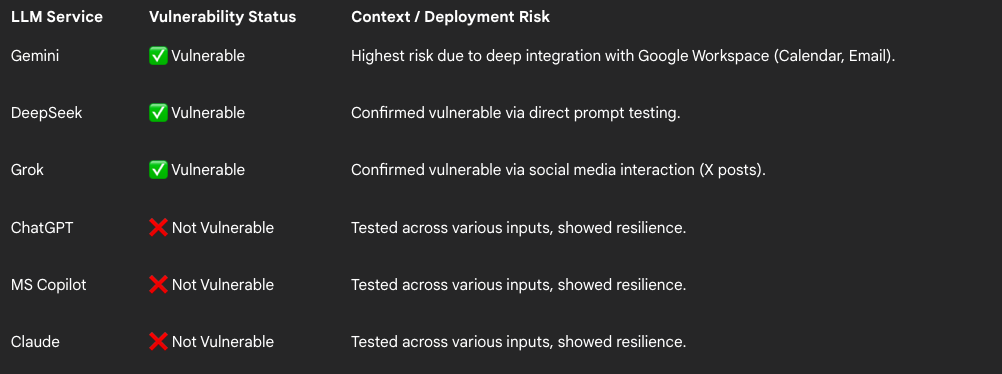
ASCII smuggling attack on LLMs: The Grok, Gemini, and DeepSeek AI agents are vulnerable to ASCII smuggling attacks. These attacks use invisible ASCII control characters to introduce malicious prompts in seemingly benign text. Per AI security firm FireTail , Google declined to address the attack vector.
Infosec industry
Threat/trend reports: Akamai , Forcepoint , Intel471 , the NCC Group , OneTrust , Positive Technologies , ReliaQuest , and Zimperium have recently published reports and summaries covering various threats and infosec industry trends.
Acquisition news: C2A Security has acquired VigilantOps, a security firm specializing in SBOM automation.
Cloudflare IR team: Cloudflare has an incident response team now, going by the name of Cloudflare One REACT .
New tool—Tokenex: Security firm Riptides has released Tokenex , a Go library for getting and refreshing credentials from various cloud providers and authentication systems.
Risky Business podcasts
In this edition of Between Two Nerds , Tom Uren and The Grugq talk about the zero-day mass exploitation of SharePoint and Exchange. This type of widespread hacking appears to be increasingly common... but is it?
