Risky Bulletin Newsletter
November 07, 2025
Risky Bulletin: Europol arrests payment service executives for role in credit card fraud ring
Written by

News Editor
This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Law enforcement agencies from Europe, Asia, and North America have dismantled a massive credit card fraud network that stole money from users using unwanted online subscriptions.
Eighteen suspects were arrested for defrauding users of more than €300 million since 2016.
According to Europol and Eurojust, the group stole credit card data, created accounts on online websites with the stolen information, and subscribed users to premium services.
The scheme used subscriptions to fake dating, pornography, and streaming services to collect money from the stolen credit cards. They charged small fees of up to €50/month, hoping that victims wouldn't spot the transactions, and used complicated chargeback processes to avoid returning the funds when that happened.
Authorities say the group stole €300 million from users, but they actually tried to get their grubby hands on more than €750 million.
The fraud ring used shell companies in Cyprus and the UK to manage the fake sites, hid their websites from search engines, and also worked hand in hand with payment providers.
Five of the arrested suspects are individuals who served as executives and compliance officers at four payment service providers in Germany. According to authorities, the corrupt executives allowed the fraud ring to use their payment platforms in exchange for fees.
The operation is one of the oldest and largest ever discovered and dismantled by authorities. More than 4.3 million cardholders from a whopping 193 countries had been victimized in the operation.
More than 30 countries were involved in the investigation in some role or another.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Pakistani senators got scammed: Four Pakistani senators have fallen victim to online scammers. The senators lost between $1,700 and $3,000 to schemes requesting money for various projects. The lawmakers blamed the country's cybercrime investigations agency for failing to act and investigate the cases. [The Express Tribune]
Nikkei Slack hack: Hackers have stolen the data of more than 17,000 Nikkei employees. The data was taken from the company's Slack channel and included names, emails, and chat histories. The incident took place last month.
Dutch TV station hacked: A cyberattack has disrupted the TV and radio broadcasts of Dutch broadcaster RTV Noord. Hackers defaced the broadcaster's website, and employees couldn't log into work accounts. Radio DJs played music by changing CDs by hand until normal programming was restored. The hack took place on Thursday morning, and the downtime lasted for several hours. [NOS]
South Korean activist hacked: A South Korean activist specialized in North Korean human rights affairs has been hacked. Hackers infected their PC with malware and then sent malicious links to the target's KakaoTalk contacts. South Korean police suspect a North Korean APT group. [Korea JoongAng Daily]
M&S takes profit hit: British retailer Marks & Spencer reported a hit to its annual profits due to its April security breach. The company lost £136 million in profits in the first half of the year. Executives expect the retailer to be back to full operations by March next year. [Reuters/The Irish Times]
DDoS attacks target Belgium: Russian hacktivist group NoName057 targeted Belgium telecoms and hospitals with DDoS attacks on Wednesday. The attacks were described as "brief." [Belgian News Agency]
Another Italian targeted with Paragon comes forward: Francesco Nicodemo, a consultant who works with Italian left-wing politicians, says his smartphone was targeted with Paragon spyware. [TechCrunch]
KT tried to hide a second breach: South Korean telecom operator KT hid details of a second security breach this year. The telco found the BPFDoor malware on 43 servers and tried to silently remove the infections without notifying authorities. Customer data was exposed in the breach, and the telco now faces a major fine. The second breach was found by a government-led investigation into another KT security incident—where a threat actor used rogue base stations to collect user data, crack payment authentication, and steal money from KT's micro-payments platform users. [Yonhap News]
Nevada didn't pay ransom: The state of Nevada did not pay a ransom demand and rebuilt its IT network following a ransomware attack this August. The restoration process took four weeks. Officials traced back the attack to May, when an employee clicked on a search engine ad and installed a malicious sysadmin tool from a spoofed website. State officials spent $1.5 million to recover from the attack. [Nevada Governor's Technology Office]
SonicWall blames APT for cloud breach: SonicWall has blamed a foreign state-backed threat actor for a recent breach of its cloud service. Hackers breached the MySonicWall cloud service in September. They stole the firewall configuration backups for all SonicWall customers who chose to sync the data to their cloud accounts.
Balancer IR: Check Point has published an incident report on the $128 million hack of the Balancer DeFi platform this week.
"The Balancer exploit demonstrates how mathematical vulnerabilities in DeFi protocols can be weaponized through automation and careful parameter tuning. The attacker's success stemmed from recognizing that negligible rounding errors become exploitable when amplified through dozens of operations in atomic transactions."
General tech and privacy
Meta makes a fortune from scam ads: Roughly 10% of Meta's annual revenue comes from ads for scams and banned products. The company made more than $16 billion from shady ads last year. According to internal documents, Meta preferred to charge known scammers a higher ad rate rather than block their accounts. A Reuters investigation found that Meta executives agreed to only act on scams in the case of "impending regulatory action."
Meta annually earns $16 billion (with a "b") on ads built to defraud people. It's so bad that Meta itself admits that its advertising tools and platforms have made it a pillar of the global scam economy. Reporting by Reuters. www.reuters.com/investigatio...
— Tim Karr (@timkarr.bsky.social) 2025-11-06T12:34:33.702Z
Twitter algorithm modified to support far-right: A Sky News nine-month investigation has found that the Twitter algorithm intentionally amplifies right-wing and extremist content in the UK. The research is similar to what many other research groups and newspapers have also found out over the past two years.
- Left-wing users saw almost the same amount of left-wing and right-wing content, even though they only followed left-wing accounts.
- But only 14% of the political content sent to our right-leaning users was left-wing.
- The neutral users saw twice as much right-wing content as left-wing content.
- Barely any of the political content shown to our X users was non-partisan.
- So right-wing content was shown most prominently, regardless of users' political leaning.
Vital piece of investigative reporting from Sky. They've uncovered the X algorithm which feeds users extremist right wing material from the moment they join the site. It is a far-right radicalisation engine, by design. news.sky.com/story/the-x-...
— Ian Dunt (@iandunt.bsky.social) 2025-11-06T07:22:46.760Z
Rust Maintainers Fund: The Rust Foundation has announced the Maintainers Fund, a way to finance some of its key developers and ensure the programming language is actively maintained at all times.
Google Maps rolls out extortion reporting feature: Google is rolling out a dedicated form to allow businesses listed on Google Maps to report threat actors who post bad reviews and demand ransoms to remove the negative comments.
Epic settles with Google: Video game maker Epic Games has settled with Google in a 5-year-old lawsuit over Play Store practices. Google has agreed to lower fees for Android app developers. Fees will be capped at 9% or 20%, depending on multiple factors. Google will also allow Android apps to use alternative payment systems, which was Epic's main point of contention. The settlement will require a judge's approval. [TechCrunch/Settlement PDF]
Chrome autofill to support govt IDs: Google has updated the Chrome Autofill feature to support government-issued IDs. Google Chrome will be able to remember, sync, and automatically fill in passport data and driver's license numbers. The company plans to support more data types over the coming months.
Government, politics, and policy
UK to block spoofed numbers: UK mobile carriers will block spoofed phone numbers starting next year. Six of the country's largest telcos will upgrade their networks over the coming year. The companies will mark when calls come from abroad to prevent scammers from impersonating UK phone numbers. The telcos will also roll out "advanced call tracing technology" to allow law enforcement the tools to track down scammers.
Dutch schools cybersecurity deadline: Dutch schools must meet several cybersecurity standards by 2030. [112 Amsterdam]
Russia charges first "extremist search" suspect: Russian authorities have filed charges against a 20-year-old man for deliberately searching the internet for extremist content. This is Russia's first case for such a crime under a law that entered into effect in September. The suspect allegedly searched for content about Ukraine's Azov battalion. The suspect, an employee of a medical institution in central Russia, denied the charges and claimed he accidentally stumbled upon the content. [Ura]
OAIC breach statistics: The Office of the Australian Information Commissioner has received 532 data breach notifications in the first half of the year, a 10% decrease compared with the previous 6 months. Almost 60% of breaches were linked to malicious and criminal acts. Cybersecurity incidents were the predominant source of breaches of this kind.
Tanzania returns online: The Tanzanian government has restored internet connectivity for the country after going offline for five days on its Election Day. Social media networks remain disrupted, per NetBlocks.
No CISA election monitoring room: For the first time in years, CISA didn't run its usual election day situation room. The group typically shares information on physical and cyber threats with local and state authorities ahead of and during elections. The lapse comes as CISA has fired thousands of workers this year. According to Bloomberg, remaining CISA election security staff have been "prohibited" from contacting state election officials.
NSA imploding: Similar to other agencies, the Trump administration has gutted the NSA with program cuts, staff layoffs, and deferred resignations. [NextGov]
DOJ's FCA settlements: The US DOJ has secured over $50 million via cybersecurity-related False Claims Act (FCA) settlements this year. I don't particularly agree with this National Law Review piece on the subject, attributing these to the Trump administration, since most of these cases started under Biden. Everything else the Trump administration has done has destroyed the country's cybersecurity posture and defenses. I very much doubt it's an "enforcement priority." [h/t DataBreaches.net]
"Collectively, these settlements reflect a clear message: Cybersecurity is an enforcement priority for the second Trump administration, and any organization that contracts with the federal government is a potential target."
AI-Related Job Impacts Clarity Act: Two US senators have introduced a bill that would instruct the US Department of Labor to track the number of jobs lost to AI. The AI-Related Job Impacts Clarity Act would require US companies and federal agencies to report the number of workers they fired and replaced with AI technology. The data would be compiled and made available via a public report.
CISA firings: CISA says the firings of 54 employees from its Stakeholder Engagement Division do not violate a recent court injunction. The agency says the firings were planned before the court order and do not affect unionized employees. The SED was a CISA division that collaborated with the private sector and local governments to secure critical infrastructure. [NextGov]
CISA's filing in the shutdown layoffs lawsuit provides the first confirmed count of laid-off employees in the Stakeholder Engagement Division: storage.courtlistener.com/recap/gov.us... (h/t www.nextgov.com/people/2025/...) CISA says employees are exempt from injunction b/c they're not in a union.
— Eric Geller (@ericjgeller.com) 2025-11-05T20:12:46.545Z
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats with Sublime Security CEO and founder, Josh Kamdjou, about how Sublime is seeing a massive surge in ICS or calendar invite phishing and how the email security platform can help.
Arrests, cybercrime, and threat intel
Bai crime family members sentenced to death: Chinese authorities have sentenced five people to death for running cyber scam compounds in Myanmar. Five others were handed life sentences, while nine of the accused were handed prison sentences of up to 20 years. All were members of the Bai crime family. In September, China also sentenced to death 11 members of the Ming crime family for similar crimes.
Members of two other crime families are also in custody (Wei and Liu), also on scam compound-related charges garwarner.blogspot.com/2025/10/scam...
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-11-06T15:32:19.049Z
German scammer arrested in Georgia: Georgian authorities have arrested a German national for their involvement in online scams. The suspect was allegedly a member of an operation known as the Scam Empire. The group was exposed in March following a joint investigation between 32 media outlets. The group made more than $275 million by running scams using call centers in Eastern Europe, Israel, and Georgia. [OCCRP]
Teen arrested over Roblox suicides: Iraqi police have arrested a 14-year-old boy for an extortion campaign that led to the suicide of 30 children across several Arab countries. The suspect recruited victims via the Roblox online game. He lured them to 16 online communities he was running, where the victims were later pressured into acts of self-harm, animal abuse, and eventually suicide. [Gulf News][h/t Andy Jabbour]
CapitalOne hacker original sentence reinstated: A US judge has resentenced CapitalOne hacker Paige Thompson. The judge reimposed Thompson's original 2022 sentence of time served and a five-year probation period. A US appeals court vacated Thompson's original sentence in March for being too lenient. Prosecutors requested an 84-month prison term. The judge chose to go with the original sentence because Thompson would not receive the appropriate gender transition medical care while incarcerated. [CyberScoop]
Five love scammers arrested in Vietnam: Five Cambodian nationals were arrested in Vietnam at the end of last month. The suspects were part of a romance scam ring that operated out of the Cambodian city of Bavet. They fled to Vietnam after a recent government crackdown on scam compounds. The five were arrested at the request of South Korean authorities for stealing $3.2 million from South Korean residents. [Korea JoongAng Daily]
GFW analysis: The DomainTools security team has published part two of its analysis of more than 500GB of data that was leaked from Chinese companies managing China's national firewall system, aka the Great Firewall.
Scattered LAPSUS$ Hunters: Picus Security has published a profile on cybercrime group Scattered LAPSUS$ Hunters and its most common TTPs.
Russian state involvement in hacktivist groups: Analyst1 has published a report on how the Russian state has gotten its hands dirty and set up several hacktivist groups to support its war in Ukraine.
"First things first. Do we think the Russian state is involved in hacktivist activity? Yes. Based on the evidence we've laid out, our level of confidence is high. Let's start with the state's general stance toward everyday life: it has its hands in everything: domestic policy, legislation, social control, and the constant pressure on dissent. So, to imagine that the Kremlin would simply ignore one of the most strategic domains of power, cyberspace, would be, to put it simply, illogical."
RMM abuse: ZenSec looks at the crucial role legitimate remote monitoring and management (RMM) tools are having on the ransomware and broader cybercrime ecosystem, slowly replacing the use of RATs.
Booking phishing campaign: Sekoia looks at a massive Booking.com phishing campaign that uses a "I paid twice" theme to lure hotel managers on ClickFix pages and then collect their credentials. Compromised hotel accounts are then used to target their customers with banking trojans.
Aisuru botnet growth: Nothing says "giant botnet" more than showing up in the top domain rankings at today's top cloud providers—Cloudflare, Microsoft, AWS, and Google. Congratulations to Aisuru for being so big that it now makes traffic rankings. [KrebsOnSecurity]
Aurologic profile: Recorded Future has published a profile on aurologic GMBH, a German company established in 2023 that provides cloud infrastructure and upstream transit to a bunch of bulletproof hosting providers, including sanctioned entities.
macOS ClickFix: Push Security is seeing an evolution in ClickFix techniques, including an increasing number of campaigns targeting macOS users.
Play Store malware: Almost 240 malicious Android apps snuck on the official Play Store this past year. The apps were downloaded more than 42 million times. According to security firm Zscaler, Android malware detections grew by 67% year-over-year.
New npm malware: Datadog has discovered 17 npm packages containing malware hidden in their postinstall scripts, targeting Windows systems.
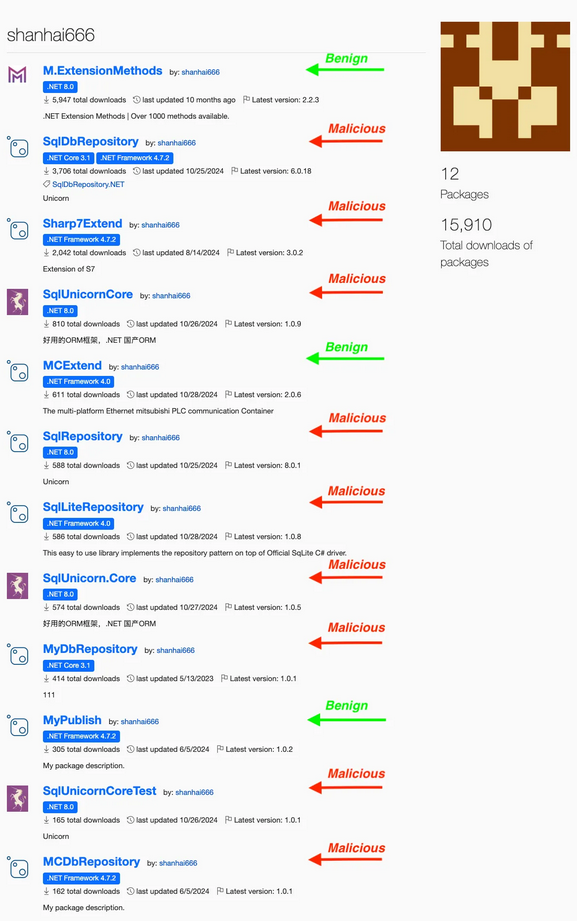
NuGet malware delivers delayed destructive payloads: Socket Security has discovered malicious NuGet packages designed to sabotage databases and industrial control systems. The packages were published in 2023 and 2024 and are designed to run malicious code after specific trigger dates in 2027 and 2028. Eight packages target database systems and will terminate the database process with a 20% probability after a trigger date. The ninth package targets industrial PLCs and runs the same malicious code right away. After June 6, 2028, this package will prevent the PLC from writing new data, effectively destroying the device.
Malware technical reports
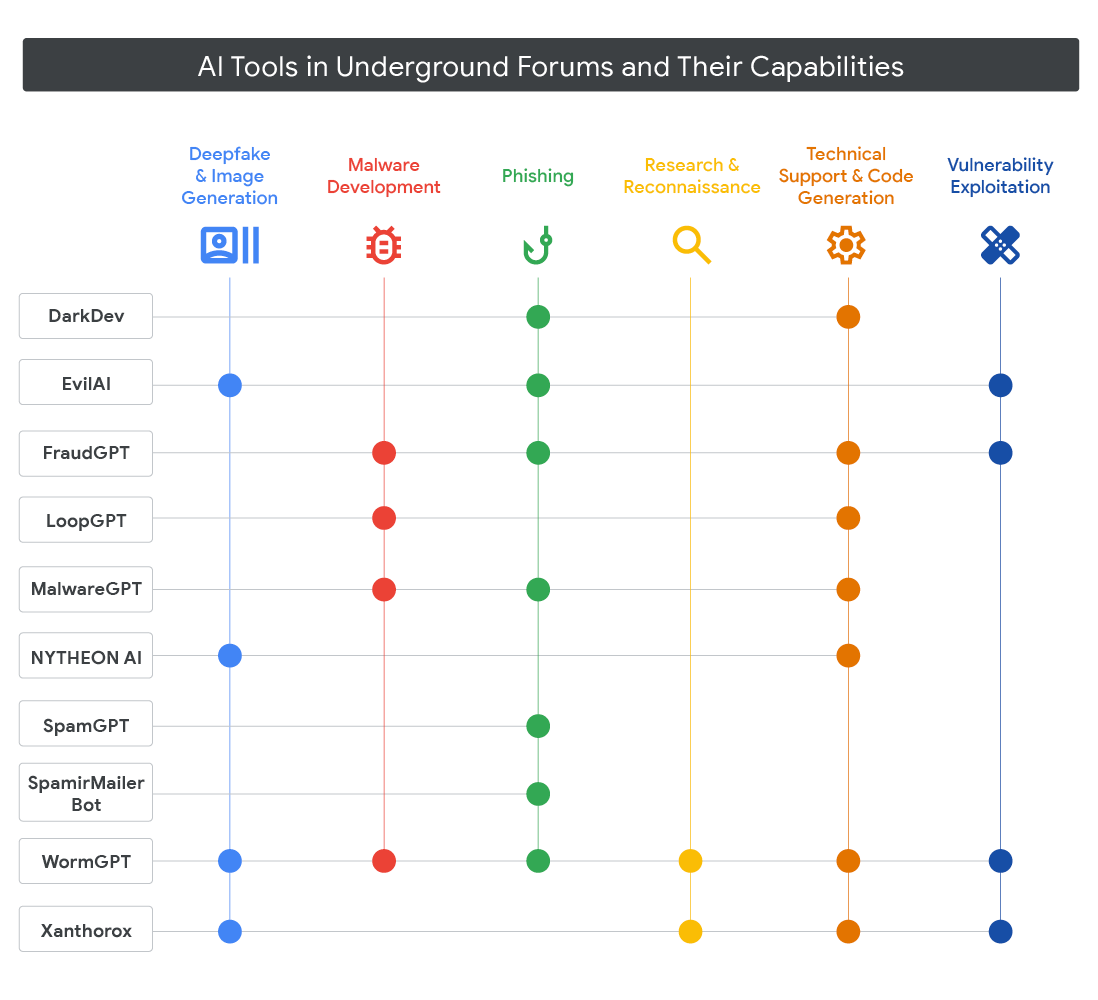
AI-powered malware: Google's threat intel team has published a report on malware strains that have adopted AI. It's just five malware strains, and they're all garbage. One of the five eventually turned out to be an academic project. The age of full AI malware will still have to wait, but malware devs are also creating their own LLM tools for very specific purposes.
LeakyInjector and LeakyStealer: The Hybrid Analysis team has published a report on LeakyInjector and LeakyStealer, two malware families used in attacks against cryptocurrency owners.
GootLoader returns: The GootLoader botnet has returned with new campaigns after more than a year of inactivity. The botnet is up to its old tricks and using SEO poisoning to redirect traffic to malicious sites. The sites host malicious files that infect users with the malware. GootLoader is then used to deploy other malware, including multiple strains of ransomware. [Huntress/GootLoader blog]
Lockbit 5.0 ransomware: Flashpoint has published a report looking at the supposed new versions of the Lockbit ransomware, tracked as v5.0.
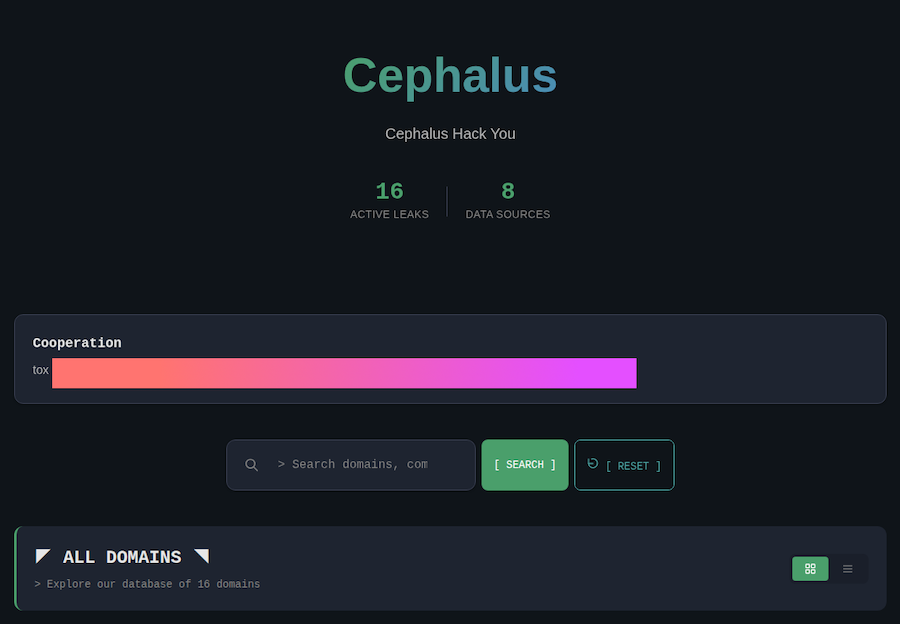
Cephalus ransomware: AhnLab looks at the new Cephalus ransomware, a strain first seen in August. The group leverages RDP accounts for initial access and operates a dark web leak site that hasn't been updated in more than two months, suggesting the group might have disbanded already.
Sponsor section
In this sponsored product demo, Sublime Security co-founder and CEO Josh Kamdjou joins Risky Business podcast host Patrick Gray to show off the company's email security platform, including its latest agentic AI bells and whistles.
APTs, cyber-espionage, and info-ops
VShell: Security researchers have linked a new mysterious Linux backdoor to a cyber contractor for the Chinese state. According to security firm NVISO, the VShell that was first spotted in August is the work of a group tracked as UNC5174. Google previously identified the group as a cyber contractor for China's Ministry of State Security.
Chinese APT campaign: Symantec has spotted a Chinese threat actor targeting a US non-profit organization that has influence over government policy on international issues. TTPs were too vague and overlapped multiple groups, such as Kelp, Space Pirates, and APT41.
UNK_SmudgedSerpent: Proofpoint has spotted a new Iranian APT group, which the company is now tracking as UNK_SmudgedSerpent. The group's targeting includes academics and foreign policy experts. The group's TTPs overlap with many other Iranian groups, showing some sort of collaboration, personnel movement, or similar training/contractors.
New Sandworm destructive attacks: Russian military hackers have deployed new data wipers in Ukraine. The Sandworm group targeted government agencies and companies in Ukraine's energy, logistics, and grain sectors. Payloads included Sting and ZEROLOT, two new data wipers. ESET researchers believe the attacks were meant to weaken Ukraine's economy.
Cavalry Werewolf: Russian security firm Dr.Web has published a report on suspected Kazakhstan APT Cavalry Werewolf and its attacks on Russian government institutions.
Kimsuky's EndClient RAT: Security researcher Ovi Liber has published a report on EndClient RAT, a new AutoIT-based RAT spotted in Kimsuky operations.
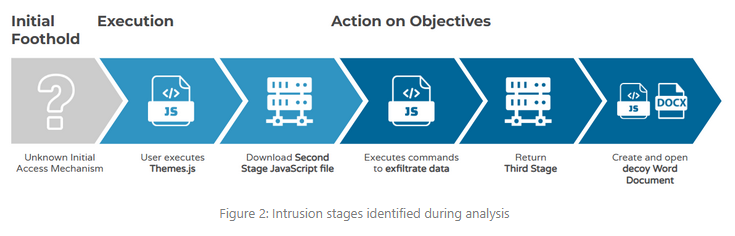
Kimsuky's JavaScript Dropper: Pulsedive analyzes a new JavaScript-based malware dropper used in recent Kimsuky operations.
"Analysis of the Kimsuky sample revealed two additional JavaScript files and a Word Document. Since the Word document is empty and does not run any macros in the background, it may be a lure. Moreover, as the initial access vector is unknown, we cannot say how the initial Theme.js file is delivered to the user."
Vulnerabilities, security research, and bug bounty
Keras vulnerability: Zscaler researchers have found an arbitrary file access and SSRF vulnerability (CVE-2025-12058) in the Keras AI platform.
PPPP protocol review: Security researcher Wladimir Palant has published a review of PPPP, a protocol mainly used by P2P security cameras.
Cisco security updates: Cisco has released four security advisories for multiple products.
HackedGPT vulnerabilities: Tenable researchers have discovered seven vulnerabilities and techniques to attack ChatGPT users. The bugs can allow attackers to exfiltrate private information from users' memories and chat history.
Advanced Installer vulnerability: Cyderes has identified a vulnerability in the Advanced Installer, a framework for building Windows installers. The bug can enable threat actors to hijack app update mechanisms and run malicious external code if update packages are not digitally signed. Cyderes says its testing did not find organizations that enabled the "sign only" update mode for their apps. Advanced Installers is used by some of the world's largest companies, such as Apple, Microsoft, Google, and IBM.
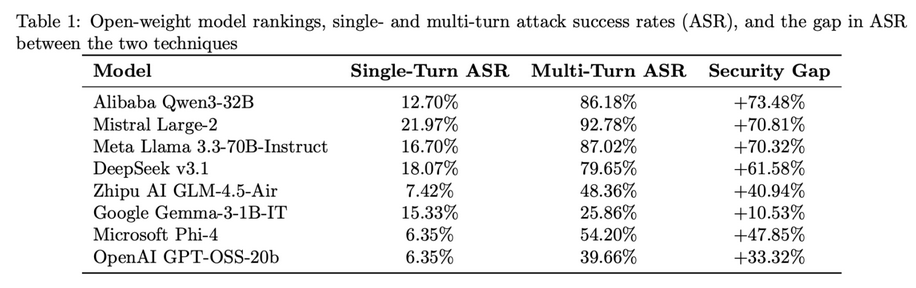
Open-weight LLMs are insecure: Cisco researchers have found "pervasive" vulnerabilities across eight open-weight LLMs currently available on the market from companies such as OpenAI, Alibaba, Mistral, Google, and others. It was kind of expected. Once open-sourced, these models are rarely kept up to date. [arXiv paper]
Infosec industry
Threat/trend reports: Akamai, Cycode, Google, ESET, Netskope, OAIC, Portnox, RSAC, and Zscaler have recently published reports and summaries covering various threats and infosec industry trends.
Google-Wiz acquisition approved: The US Justice Department has approved Google's acquisition of Israeli cloud security company Wiz. Google agreed to acquire Wiz in March for $32 billion and entered an antitrust review in June. The deal is expected to close in 2026. [Calcalist]
RIP David Harley: Former ESET research fellow David Harley has passed away, according to VirusBulletin.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about aggressive US cyber operations targeting the Venezuelan government in President Trump's first term. These were narrowly successful in that they achieved their immediate operational goals, but they didn't achieve Trump's broader policy goal of ousting Venezuelan leader Nicolás Maduro.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the futility of using aggressive cyber operations to send messages between states.
