Risky Bulletin Newsletter
May 09, 2025
Risky Bulletin: France says Russian influence operations are getting better, achieving results
Written by

News Editor
This newsletter is brought to you by Stairwell . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
VIGINUM, the French government's agency that hunts down and exposes foreign disinformation networks, says that Russian influence operations have now reached a mature level and are often achieving notable results.
The agency published a report this week on Storm-1516 —what appears to be one of the Russian government's most sprawling and active disinformation clusters.
Unlike many previous disinformation reports that tend to play down the effectiveness of such operations, VIGINUM doesn't mince words and describes Storm-1516's efforts as successful and " a significant threat to French and European public debate ."
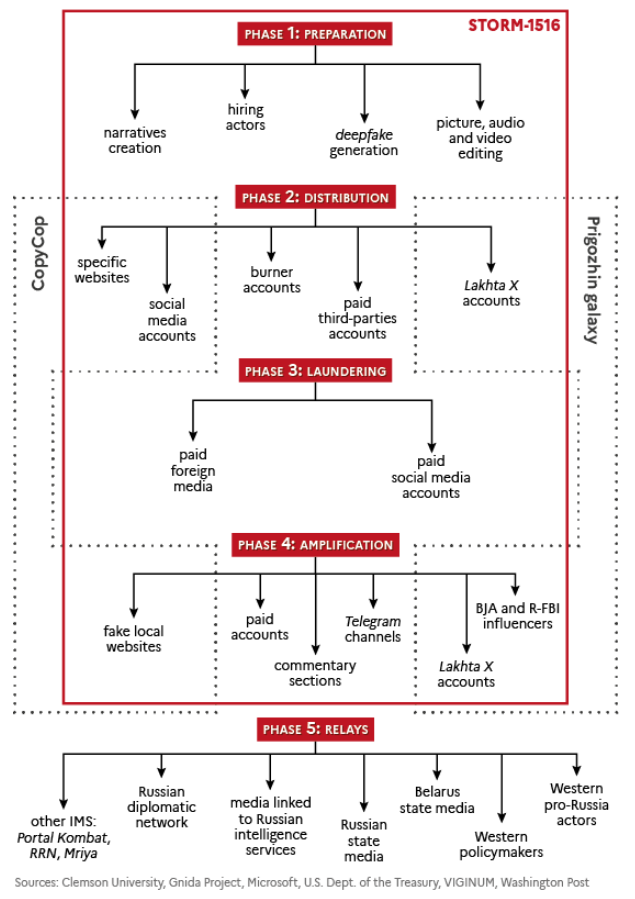
The report is the most comprehensive one put together on the group and any other Russian influence operation I've seen so far. It covers 77 different info-ops that Storm-1516 has conducted since its inception in March 2023.
It covers the group's supposed operators, its small sub-clusters, its modus operandi, the main themes and messages, and its cooperation with other entities in Russia's larger disinformation effort.
According to VIGINUM, the central figure at the heart of Storm-1516 activity is Yury Khoroshenky, a suspected military officer in Russia's military intelligence service GRU, possibly assigned to GRU Unit 29155.
Khoroshenky allegedly finances and coordinates the group's activities. This includes generating content on specific themes, distributing it through an assortment of channels, laundering it through independent and unrelated accounts, and amplifying it for visibility.
Some parts of this activity are handled by Storm-1516, but other parts are also handled by other entities and organizations. These sub-clusters include individuals who previously worked in Yevgeny Prigozhin's for-hire troll farms, organizations linked to Russian far-right political philosopher Aleksandr Dugin, and fake news websites run by American exiled cop John Mark Dougan. See the two charts below.
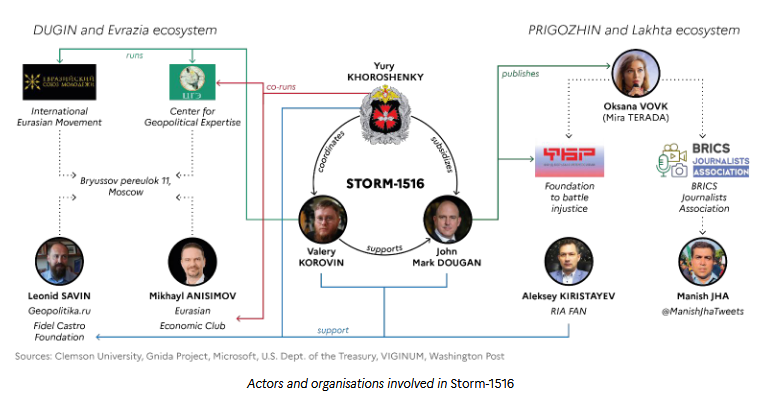
VIGINUM describes the interactions between Storm-1516, these sub-clusters, and other Russian influence operations as self-beneficial and opportunistic, and sometimes even coordinated. These groups may not be aware of each other's precise goals and operations, but they know who and where they are and help each other out in order to blur lines, hide in the noise, and create a general sense of mass and support for sometimes made-up topics.
The group was created after Russia's invasion of Ukraine, and as expected, most of its content revolves around discrediting Ukraine, its people, and its government. VIGINUM says that 35 of the 77 Storm-1516 operations they analyzed focused on Ukraine, with most of it being—to put it mildly—made up bull***t.

The group also ran influence operations ahead of last year's election cycles, with a focus on the US, French, and German elections.
This typically involves deepfakes designed to peddle conspiracy theories and lies about political figures that support pro-Ukrainian and anti-Russian views.
At this point in your typical disinfo report, you'd have a representative from a social media platform that carried the said disinfo ( no conflict of interest here, move along ) tell you that the campaign was a failure because, from the tiny fraction of accounts and posts they detected and analyzed, the content had very few impressions and view counts.
The reality is that view counts don't matter. Disinformation works like Chinese water drop torture. The same message just needs to be there in the background and it will eventually enter the public consciousness at one point or another.
VIGINUM says that Storm-1516— and Russian influence operations as a whole since this is not the only group doing this —appears to have achieved that purpose. According to the agency, the group's campaigns often achieve notoriety and are covered by bigger news outlets and " they are sometimes adopted, unconsciously or opportunistically, by leading political figures and representatives ."
You don't measure the success of an influence operation by the number of tweet engagements. You measure it by the number of politicians taking your made-up claims as fact, spreading them further to the masses, and the percentages these groups now have in Western parliaments and government structures.
Western intel and cybersecurity experts may ridicule some of the childish and sometimes ludicrous topics coming out of Storm-1516, but the Kremlin continues to put billions of euros in online disinformation efforts 10 years after it started exploring the space, suggesting they're pretty happy with the results.
These influence operations are generally dumb and hilarious for anyone who studied for years to become an expert in cybersecurity, intelligence, or political topics, but these campaigns are not meant for the brainiacs analyzing them.
Recent election and voting results show these campaigns work at swaying public opinion in favor of Kremlin-friendly candidates, and VIGINUM says groups like Storm-1516 are now more sophisticated and have an " operational pace ."
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Delta Airlines hack class-action lawsuit to go forward: A US judge has allowed a class-action lawsuit filed by passengers against Delta Airlines to go forward. The lawsuit is seeking penalties for canceled and delayed Delta flights caused by the CrowdStrike IT outage last year. Delta refused to refund passengers by blaming the breach on CrowdStrike. A crucial claim from the plaintiffs was that Delta refused both CrowdStrike and Microsoft's help following the outage, which they say should make Delta liable and not CrowdStrike. [ Additional coverage in CyberDaily ]
NoName057 DDoS attacks switch to the UK: Russian hacking group NoName057 has launched DDoS attacks against tens of UK local government websites. The attacks have been going on for three days. The group switched to attacking UK sites after previous campaigns disrupted sites in the Netherlands and Romania. [ Additional coverage in The Guardian ]
SAA cyberattack: A cyberattack that took place over the weekend has crippled the IT networks of the South African Airways. The incident impacted the airline's website, mobile app, and several internal systems. The attack didn't impact the airline's flights. The South African Airways is one of South Africa's top 3 airlines, with a fleet of 20 airplanes. [ Additional coverage in The Record ]
Nova Scotia Power cyberattack: Ransomware is believed to be behind a cyberattack that hit Canadian energy provider Nova Scotia Power at the end of April. [ Additional coverage in CBC ]
PowerSchool extortions go brrr: Education software maker PowerSchool says hackers are extorting its customers using data they stole in a cyberattack last year. The company says school districts in Canada and the US have received ransom demands with data samples stolen from its platform. These second-hand extortions are taking place even if PowerSchool paid the initial attackers to delete its stolen data.
Oettinger ransomware attack: German beer and soft drinks maker Oettinger Getranke is investigating a ransomware attack after its name was listed on the RansomHouse portal. [ Additional coverage in Yahoo Finance ]
Ransomware delays Masimo orders: A ransomware attack that took place at the end of April is disrupting the manufacturing facilities of medical device maker Masimo. The company says factories are operating at "less than normal levels" and that its ability to fulfill orders has been affected. Masimo is one of the Top 15 biggest medical device makers in the world.
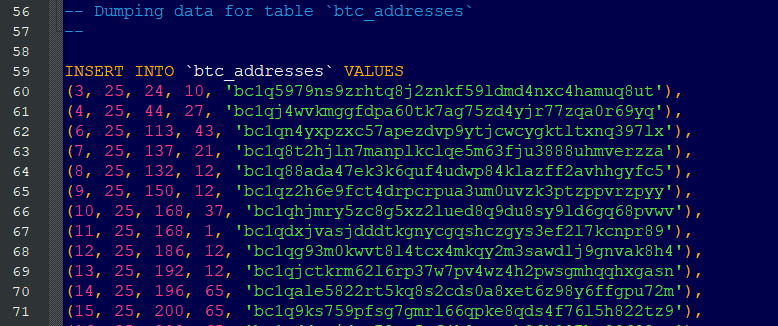
LockBit v4 hacked: An unknown individual has hacked the dark web portal of the LockBit ransomware gang and leaked its backend database. The leaked data contains Bitcoin addresses used by the group, backend users, and victim chats. The hack targeted version 4 of the LockBit ransomware portal, which launched at the end of last year after law enforcement seized the previous version. Based on the message they left on the defaced LockBit site, the attacker appears to be the same individual who hacked the Everest ransomware gang last month . [ h/t @club31337 ]
General tech and privacy
Apple to revamp Safari: According to Bloomberg , Apple is looking at revamping its Safari web browser around AI features. Can this stupid AI bubble burst faster before companies enshitify all products?!?!?!?
Gmail to stop supporting 3DES: Google says that the Gmail email service will stop supporting the 3DES cipher on May 30. After that date, Gmail will drop all emails sent using this encryption method.
Microsoft's deputy CISOs: I've been looking for this list for a while, but here are the names and roles of the 13 deputy CISOs that Microsoft named as part of its Secure Future Initiative (SFI) security program last year.
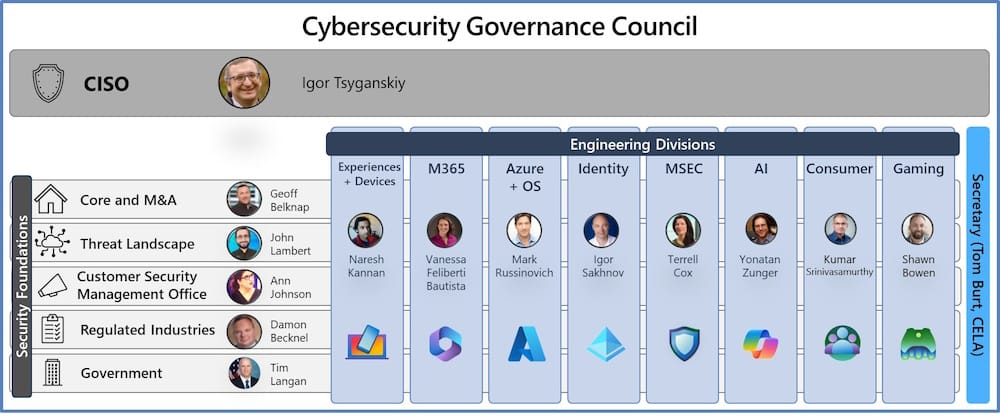
Government, politics, and policy
EU wants a KYC for the online advertising sector: EU officials are working on regulation that will force online advertising companies to check the legitimacy of advertisers before posting the ads. According to the Financial Times , the initiative is led by Ireland and seeks to fight a rising trend in scam ads posted online and specifically via social media. EU lawmakers are also seeking to introduce a system for the automatic reimbursement of scammed funds via banks and payment services such as Mastercard, Visa, or PayPal.
Hungary breaks AI Act: According to EDRi , Hungary has passed new law amendments that break the EU AI Act and allow local authorities to use real-time facial recognition software for minor infractions such as peaceful protests.
NZ plans <16 social media ban: New Zealand lawmakers have proposed a bill that would ban kids under 16 from social media. [ Additional coverage in RNZ ]
US ACCESS Act: Three US senators have reintroduced legislation that would require major social media platforms to become interoperable and allow users to port their data. The Augmenting Compatibility and Competition by Enabling Service Switching Act, or the ACCESS Act, will apply to any social media company with over 100 million monthly active users in the US. This is the third time the three senators introduce the ACCESS Act after similar efforts in 2019 and 2023 .
Three US departments ban TeleMessage: Three US government departments have told employees to stop using the TeleMessage service, according to Bloomberg . The service allows companies to log and archive conversations taking place in secure messengers such as Signal, WhatsApp, and others. Two separate hackers have breached TeleMessage's backend last week after it was revealed that White House officials use the service.
Top FBI cyber official leaves: Bryan Vorndran, the assistant director of the FBI Cyber Division, is leaving the agency later this year. According to The Record , he was the main figure behind the FBI's efforts to disrupt and seize cybercrime infrastructure. He is also the co-chair of the Joint Ransomware Task Force.
Vorndran is one of the longest-serving cyber officials at his level in the government. In addition to increasing multilateral takedowns of cybercrime infrastructure, he's been instrumental in deepening the FBI's partnerships with other agencies, especially CISA.
— Eric Geller (@ericjgeller.com) 2025-05-08T19:25:10.092Z
Sponsor section
In this Risky Bulletin sponsor interview, Mike Wiaceck, CEO and founder of Stairwell, explains why he believes security is really a data storage and retrieval problem. He demonstrates how that pays off in the analysis of new malware.
Arrests, cybercrime, and threat intel
Six DDoS booters taken down: EU and US law enforcement have seized six DDoS-for-hire services that were used to launch DDoS attacks for as little as €10. Four suspects involved in running the sites were also arrested in Poland. The four ran services known as CfxAPI, CfxSecurity, NeoStress, JetStress, QuickDown, and ZapCut. The sites used a simple GUI to allow anyone to launch DDoS attacks just by entering an IP address.
Mr. DeepFakes admin exposed: Four major news organizations have identified the administration of a notorious deep-fake service as a Canadian pharmacist from Toronto. David Do is allegedly the administrator of MrDeepFakes, one of the largest services for creating deep-fake celebrity adult content. The MrDeepFakes service shut down at the start of the month after reporters reached out.
Scam account takedowns: Meta took down over 23,000 Facebook Pages and accounts that targeted users in Brazil and India with investment scams.
Recruitment scams: Netcraft has spotted an explosion in recruitment scams designed to infect job seekers with malware.
BAV2ROPC campaign targets Entra environments: Between March and April this year, a threat actor attacked Microsoft Entra environments that did not disable legacy authentication protocols. The brute-force attacks targeted Entra customers still running BAV2ROPC (Basic Authentication Version 2 Resource Owner Password Credential), an authentication method used by older email apps and devices. Security firm Guardz says the attacks were very coordinated and spread geographically to avoid detection.
Malicious PyPI package goes undetected three years: Socket Security has discovered a malicious Python library that contained a remote access trojan and went undetected for over three years.
Malicious npm packages: The same Socket team has also discovered three malicious npm packages that hijack the Cursor IDO on macOS to steal credentials and plant backdoors.
New npm supply chain attack: A threat actor has compromised the rand-user-agent JavaScript library and released a malicious version containing a remote access trojan. The incident took place on Monday and impacted rand-user-agent, an npm package with over 45,000 weekly downloads. Security firm Aikido says the project was still widely used even if its developer considered it semi-abandoned.
Facebook malvertising campaign: Bitdefender has spotted a new Facebook malvertising campaign mimicking major crypto exchanges. That's what Facebook is these days, malicious ads and political info-ops.
Brazilian phishing campaign: Cisco Talos has spotted a phishing campaign that targets Brazilian companies. The campaign uses the Brazilian electronic invoice system NF-e as a lure to get victims to install the remote access tool on their systems. The attackers abuse the "free trials" periods of legitimate RMM software such as ScreenConnect, N-able, and PDQ Connect.
"Talos assesses with high confidence that the threat actor is an initial access broker (IAB) abusing the free trial periods of these RMM tools."
Twitter crypto scam campaign: Silent Push has spotted a new scam campaign that abuses a URL spoofing bug on Twitter to redirect users to scam sites.
Inferno Drainer never shut down: The Inferno Drainer cryptocurrency phishing operation has continued to operate even after announcing publicly that it was shutting down in 2023. Security firm Check Point has found evidence that smart contracts and wallet-draining scripts are still in use today. The company has identified over 30,000 crypto wallets that have been drained of over $9 million crypto assets over the past six months alone.
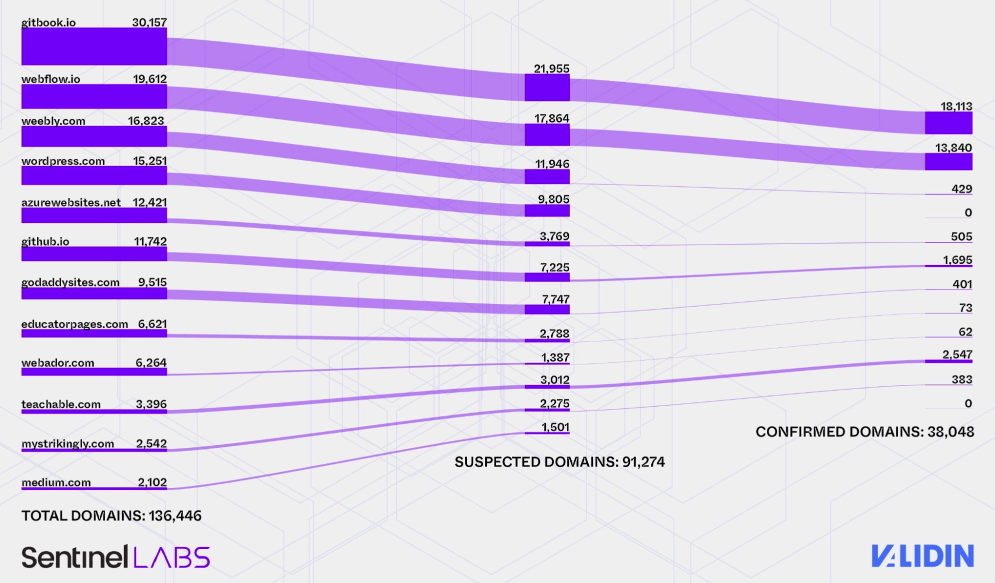
FreeDrain crypto theft network: SentinelOne and Validin have published reports on FreeDrain, a huge scam network that uses SEO manipulation to lure cryptocurrency enthusiasts to crypto-wallet phishing pages.
EOL router attacks: The FBI IC3 has published a new PSA warning companies and home consumers that threat actors are exploiting old and outdated end-of-life routers to create massive botnets and that they should probably buy a new device.
UK warns of AI effects on cybercrime: The UK's cybersecurity agency warns in a gloomy report that AI will have a pretty negative effect on the cybercrime landscape in the coming years by boosting threat actor automation and capabilities.
"There will almost certainly be a digital divide between systems keeping pace with AI-enabled threats and a large proportion that are more vulnerable, making cyber security at scale increasingly important to 2027 and beyond."
DPRK IT worker schemes expand to Asia: After expanding to Europe earlier this year, North Korean remote IT worker schemes are now also targeting Asian organizations, per a new Sophos report .
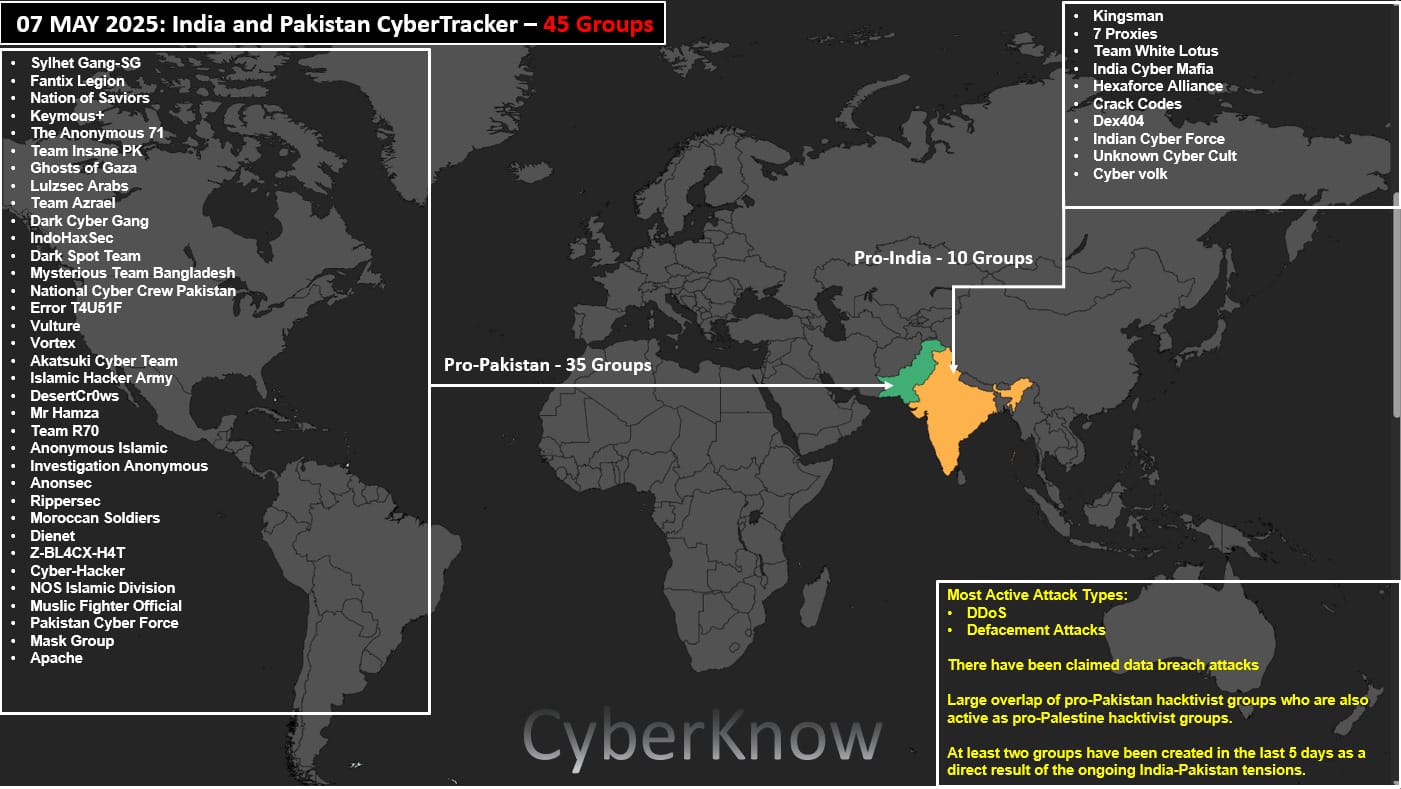
India-Pakistan cyber war: CyberKnow has set up a tracker for all the hacktivist groups involved in the recent Indian-Pakistan armed conflict. Currently, there are 45 groups involved, 35 on the side of Pakistan and the other 10 for India.
Malware technical reports
DOGE Big Balls ransomware: Netskope has published a report on the DOGE Big Balls ransomware strain that popped up online last month.
Nitrogen ransomware: ANY.RUN has published a technical report on the Nitrogen ransomware , a double-extortion group that was first spotted last September and likes to target financial entities.
Agenda ransomware: A new Trend Micro report looks at how the Agenda ransomware has adopted SmokeLoader and NETXLOADER for their arsenal and recent intrusions.
Hunters International ransomware: Synacktiv has a report out on how the Hunters International ransomware group targets networks heavily relying on VMware ESXi hypervisors.
CoGUI phishing kit: Proofpoint has spotted a new phishing kit named CoGUI that is currently used in phishing campaigns against Japanese targets. The company says CoGUI is similar to the Darcula phishing kit, and both kits are used by Chinese-speaking threat actors.
Panda Shop phishing kit: Resecurity has identified a new phishing kit named Panda Shop that is currently being used by Chinese criminal groups for international SMS phishing operations. Resecurity believes former members of the Smishing Triad group are involved in running the kit.
"Like the Smishing Triad, Panda Shop offers a customized smishing kit that can be deployed on any server. Our investigators suspect the group includes Smishing Triad members who transitioned their operations under the new brand after being publicly shamed. The kit's structure and scripting scenarios analyzed by Resecurity mimic the same product but include specific improvements and new supported templates."
RedisRaider crypto-miner: A new cryptocurrency mining operation is targeting Linux servers running Redis databases. Security firm DataDog says the new RedisRaider group is extremely aggressive and scans entire randomized portions of the IPv4 space. The group's malware is written in Go, but the final payload is the good old XMRig miner.
Sponsor section
Learn why traditional security falls short and how Stairwell gives you the edge to outpace tomorrow's threats and uplevel your security team .
APTs, cyber-espionage, and info-ops
Iranian APT impersonates model agency: Palo Alto Networks has spotted an Iranian APT impersonating a German model agency to lure victims on its website and gather intel on possible targets. The company says the activity overlaps with the techniques of a group known as Agent Serpens, also APT35 and Charming Kitten.
Chaya_004 behind NetWeaver attacks: A Chinese threat actor that Forescout tracks as Chaya_004 is behind a recent SAP NetWeaver zero-day (CVE-2025-31324).
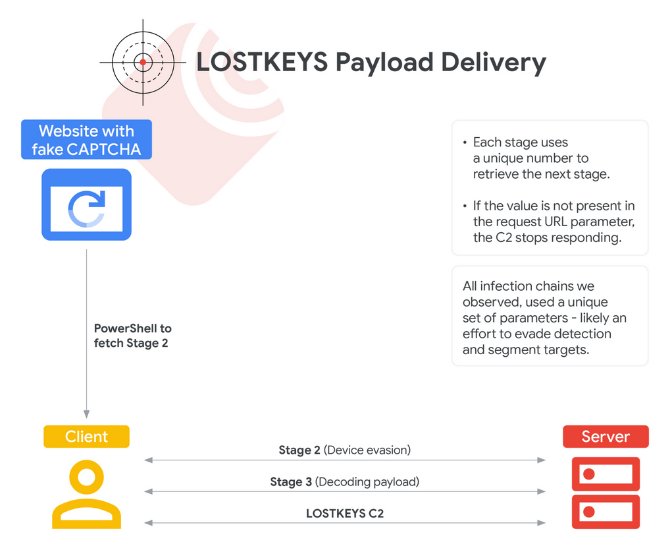
ColdRiver adopts ClickFix: Russian cyber-espionage group ColdRiver is using ClickFix tactics to infect targets with a new malware strain named LostKeys .
Vulnerabilities, security research, and bug bounty
New SonicWall zero-day: Security firm Rapid7 has discovered a new zero-day vulnerability exploited in the wild in SonicWall SMA SSL VPN servers. Tracked as CVE-2025-32819, attackers are using the zero-day to elevate privileges to admin level on already compromised systems. SonicWall released security updates , although the company has yet to confirm the attacks.
SysAid RCEs: WatchTowr Labs has discovered three remote code execution bugs in the on-premises version of IT service management software SysAid. The vulnerabilities don't require authentication to exploit and can allow attackers access to sensitive corporate systems, such as tickets, asset inventories, and help desk systems. All three issues were patched back in March. Patching is advised since SysAid vulnerabilities have been historically exploited by ransomware gangs.
Ubiquiti security updates: Ubiquiti has released a security update for UniFi Protect Cameras to fix an RCE vulnerability with a severity score of 10/10.
Windows CLFS zero-day: Symantec says the Play ransomware is now exploiting a Windows CLFS zero-day ( CVE-2025-29824 ) patched last month. The zero-day was initially exploited by the RansomExx ransomware gang.
7-Zip vulnerability: CrowdFense has published a technical breakdown of CVE-2024-11477, a memory vulnerability in the 7-Zip archiving tool.
Microsoft Bookings vulnerabilities: ERNW has published technical details on a series of vulnerabilities in the Microsoft Bookings platform. The reported issues are patched, but they could have been used to manipulate meeting calendars, leak meeting data, or exhaust employee calendars.
Radware firewall bypass: CMU's CERT/CC says the Radware Cloud Web Application Firewall is vulnerable to various filter bypass techniques.
macOS RCE: Seven months after it was patched, ZDI has published a technical write-up on a pretty rare RCE in Apple's macOS.
Cisco security updates: Cisco has released 29 security advisories for various products, including one to patch a CVSS 10 bug .
WhatsApp group messaging analysis: An academic paper analyzes the design and flaws of WhatsApp's E2EE group messaging feature. Let's say the researchers are not impressed and have found multiple issues that will need to be answered and clarified by Meta engineers.
Infosec industry
CrowdStrike layoffs: Security firm CrowdStrike will lay off around 500 workers , representing around 5% of its 10,000-strong global staff. CEO George Kurtz said AI productivity gains were a factor in the layoffs, but they will continue to hire new staff throughout the year. CrowdStrike stock fell 4% after the layoffs announcement but the stock was up 29% for the year. [ Additional coverage in Investor's Business Daily ]
Layoffs at CrowdStrike. I’m safe, but if you’re looking for IR consultants I know a bunch of fucking amazing ones that will be looking for jobs 🫠
— muteki (@muteki.bsky.social) 2025-05-07T14:54:18.859Z
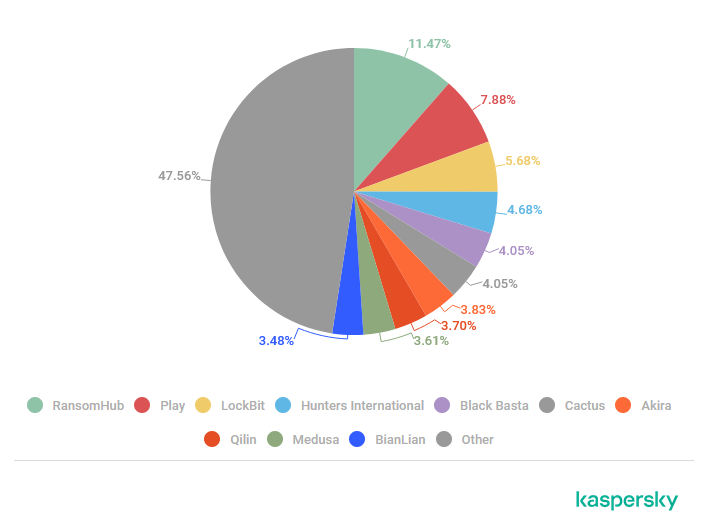
Threat/trend reports: Amazon , Bitsight , Coalition , CompTIA , Kaspersky , and the UK NCSC have recently published reports and summaries covering various infosec trends and industry threats.
New tool—Evilent: Thunter has released Evilent , an NTLM relay attack using the MS-EVEN RPC protocol and antivirus-assisted coercion.
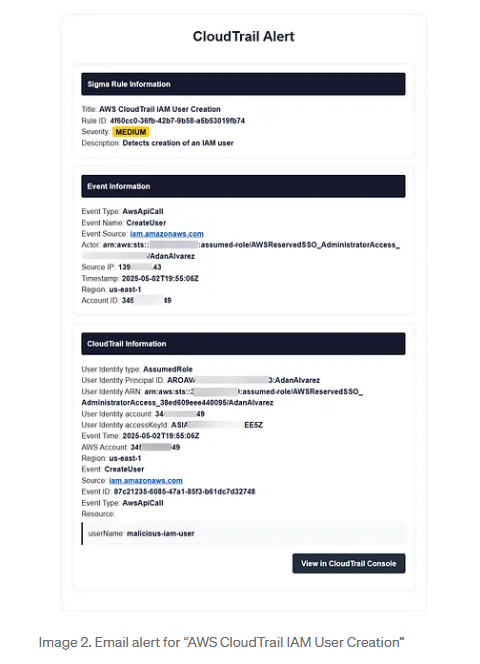
New tool—TrailAlerts: Security engineer Adan Alvarez has released TrailAlerts , an AWS-native, serverless cloud-detection tool that lets you define simple rules as code and get rich alerts about events in AWS.
NDSS 2025 videos: Talks from the Network and Distributed System Security (NDSS) Symposium 2025, which took place at the end of February, are available on YouTube .
Insomi'Hack 2025 videos: Talks from the Insomni'Hack 2025 security conference, which took place in March, are available on YouTube .
SO-CON 2025 videos: Talks from the SpecterOps 2025 security conference, which took place at the end of March, are available on YouTube .
Risky Business podcasts
Tom Uren and Patrick Gray talk about how the US is planning to take the gloves off in cyberspace and conduct much more aggressive offensive cyber operations. US responses to cyber espionage have not been very aggressive to date, but Tom is not convinced that cyber punches are required, so much as blows that really hurt.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about an in-depth report on a Ukrainian hacking control panel. The panel shows how the Ukrainian group thinks about hacking operations, and the pair discuss why the report exists and what it achieves.
