Risky Bulletin Newsletter
May 19, 2025
Risky Bulletin: Japan passes active cyber defense law
Written by

News Editor
This newsletter is brought to you by SpecterOps , the experts in Attack Path Management. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
The Japanese government passed a new law last week that allows local agencies to carry out preemptive offensive cyber operations to prevent or suppress future attacks on the country's IT infrastructure.
Although named the Active Cyberdefense Law , its scope goes beyond what the name suggests and also includes several other provisions that modernize and upgrade the country's cybersecurity practices as a whole.
The most important section of the new law is not the part about "active cyber defense" but the part that overhauls some of Japan's data collection practices.
The new law grants the government the legal authority to intercept foreign internet traffic passing its infrastructure, which is similar to what many other countries are already doing.
The government can't sniff on internal data, but information gleaned from these interceptions can be used to detect possible threats.
In addition, the new law also requires companies from Japan's critical sector to disclose security breaches to the Japanese government as soon as possible.
These two data entry points can then be used to determine ongoing cyberattacks or future threats and allow Japan to respond.
The response will come either from Japan's national police or its military, the Self-Defense Forces.
Under the new law's provisions, Japan's national police will be allowed to employ so-called " cyber harm prevention officers " who will be allowed to take down servers and disrupt a threat actor's infrastructure before or during a cyberattack targeting Japanese organizations.
Police officers will handle mundane attacks, while cyber specialists from Japan's army will be called upon for more sophisticated threat actors and situations.
To simplify collaboration, individuals involved in active cyber defense will be allowed to work from joint centers .
The new law also urges authorities to set up public-private partnerships similar to those used in the US by CISA, NSA, and all the other cyber agencies.
Also, like in the US and other Western powers, a new oversight body will be created and operate as part of the Japanese Cabinet Office to ensure that police or the military don't abuse their new powers.
The oversight will be needed because, on early analysis of the law, it appears police and the military may need to act without a judge's approval for some missions due to time constraints. Individuals who use or leak data collected through this new process can face fines or even up to four years in prison.
A lot of the law mimics what the US has done over the past decade because the US was the one that threw the bucket of cold water on Japan three years ago.
According to the Asian Military Review , the event is known in Japan as the Blair Shock . It refers to a series of public statements made by US Director of National Intelligence Dennis C. Blair, who, in April 2022, revealed the breadth of China's penetration of Japanese government structures and criticized the country's cybersecurity posture as antiquated compared to the US and its allies.
Blair urged Japan to overhaul its approach to cyber operations, which the government did a few months later, in December, when it updated its national security strategy [ PDF ] and formally asked Parliament for a new cybersecurity law.
The new Active Cyberdefense Law is set to go into effect in 2027.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Rhode Island hack update: Rhode Island Governor Dan McKee said the BrainCipher ransomware, which hacked state systems last November, had actually breached the state five months earlier in July, silently rummaging around and stealing its data for months.
Procolored printers shipped malware: Procolored printers shipped with software that contained a remote access trojan and a cryptocurrency clipboard stealer. The vendor removed the malicious software from its website after being notified by YouTube review channel Serial Hobbyism and security firm G DATA . It is unclear how many years the malware was included in the official software or if it was added on purpose or following a hack. G DATA says activity from both malware strains appears to have stopped in March last year.
OPM breach identity protections: Two US lawmakers have expressed concerns that DOGE staff might cut identity protections for current and former US government employees impacted by the 2015 OPM breach. [ Additional coverage in FedScoop ]
Russian hospital goes down after cyberattack: The IT network of a Russian private hospital has been offline for days after getting hacked by pro-Ukrainian hacktivists. The attack has been claimed by a new group named 4B1D . In a Telegram post, the group says it wiped five servers and encrypted over 100 workstations and databases at the Lecardo Clinic in the Russian Republic of Chuvashia. Local Russian officials said they would investigate the hospital for failing to disclose the hack and failing to secure its IT systems. [ Additional coverage in The Record ]
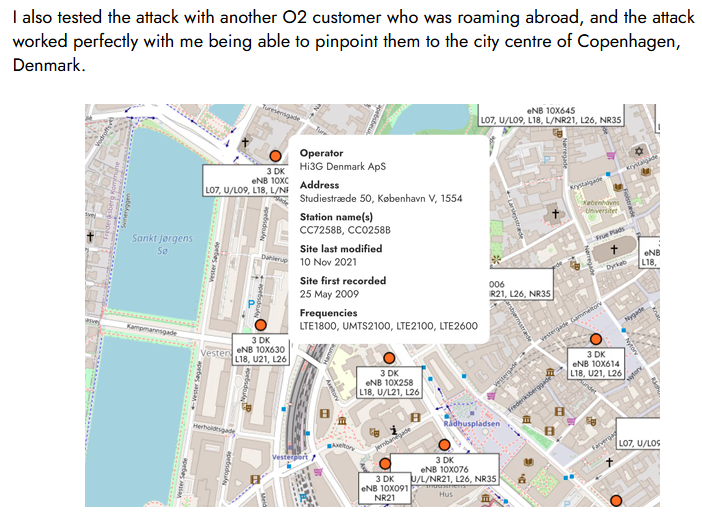
O2 telco network leaks user data, geolocation: British telco O2 has misconfigured its 4G network and is leaking sensitive customer data. VoLTE network traffic exposes raw data such as IMEI and IMSI codes and cell tower details for every call. According to mobile app developer David Wheatley , the data can be used to fingerprint devices and geolocate O2 users by calling their phone numbers. Wheatley contacted Virgin Media but has yet to receive a reply.
General tech and privacy
OpenAI releases Codex: OpenAI has released Codex , an AI assistant for software engineers and tuned for writing code and managing programming-related tasks.
Windows BitLocker bug: Microsoft has confirmed that a recent update is erroneously forcing some Intel-based Windows systems into the BitLocker recovery screen.
Twitter sanctions problems: A report from the Tech Transparency Project has found that Twitter took payments from sanctioned terrorist groups for premium accounts and features, which the groups used to spread its propaganda.
Epic Games accuses Apple of malicious compliance again: Fortnite maker Epic Games says Apple is breaking its own app review rules and is now blatantly refusing to publish app updates in violation of a court injunction in an antitrust lawsuit Epic filed against the OS maker a few years back.
Linux adds swap tables: The Linux kernel now supports memory swap tables .
Government, politics, and policy
The Netherlands criminalizes cyber-espionage: A new law entered into effect last week in the Netherlands that criminalizes more forms of espionage, including cyber espionage. Under the new law, persons who carry out espionage for foreign governments can face up to 12 years in a Dutch prison. The law applies to Dutch citizens, but also to foreign diasporas present in the country. Offenders can face up to eight years in prison or up to twelve if espionage activities lead to someone's death.
DOD DevSecOps report: The US Department of Defense CIO has released a report [ PDF ] on the progress of using DevSecOps to achieve faster delivery of software capabilities.
DOD cyber ops pause lasted one day: The Pentagon's pause of offensive cyber operations against Russia lasted only one day. Defense Secretary Pete Hegseth ordered US Cyber Command to cease operations against Russia in February, shortly after taking office. Republican Congressman Don Bacon, the chair of the House Armed Services cyber subcommittee, said the pause only lasted for a day but declined to provide other details. Bacon's statement also directly contradicts the Pentagon, which denied such a pause order was given in the first place. [ Additional coverage in The Record ]
NHS asks suppliers to boost cybersecurity: The UK NHS has asked suppliers in an open letter to boost their cybersecurity practices and help protect UK hospitals against ransomware attacks. Contractors were asked to keep systems updated, deploy backups and MFA, and implement cyber monitoring and logging capabilities. Several UK hospitals suffered ransomware attacks over the past few years after hackers breached systems from supplier networks.
EU countries look at social media bans for kids: At least four EU states are looking at implementing a social media ban for children under the age of 15. Greece, France, Ireland, and Spain are said to be looking for allies for a larger EU agreement. Australia implemented a social media ban for children under 16 last year, and New Zealand is also looking to pass a similar restriction. [ Additional coverage in FranceInfo ]
Sponsor section
In this Risky Bulletin sponsor interview Justin Kohler, Chief Product Officer at SpecterOps talks to Tom Uren about the impossible challenge of managing identity directory services securely. Organisations try to implement the principle of least privilege but have no idea if they have done a good job. Justin talks about approaches SpecterOps is developing to address this problem.
Arrests, cybercrime, and threat intel
SEC Twitter hacker sentenced: A US judge has sentenced an Alabama man to 14 months in prison for hacking the Twitter account of the US Securities and Exchange Commission. Eric Council Jr. used SIM swapping to take control of the SEC account in January of last year and posted a fake announcement. The announcement caused the Bitcoin price to spike and then fall when the tweet turned out to be fake. He was arrested a few months later after showing almost no OpSec.
Hacker DR32/Abdilo sentenced to time served: A US judge has sentenced Australian hacker DR32 to time served. David Kee Crees pleaded guilty earlier this year to hacking seven US companies between June 2020 and July 2021. He was arrested in 2022 after selling data to an undercover agent. The judge considered that the two years Crees spent in prison while waiting for extradition was punishment enough for his crime. Unconfirmed reports claim Crees, who also went online as Abdilo, also hacked a ransomware gang. [ Additional coverage in DataBreaches.net ]
US arrests crypto-thieves: The US has charged and arrested 12 suspects for their role in the theft of more than $263 million worth of cryptocurrency. Ten suspects were detained in California, while two are still at large and believed to be in Dubai. The twelve are allegedly part of the gang that helped Malone Lam steal the funds last year. Lam was arrested last year for pulling what is considered one of the largest crypto thefts from a single person in US history.
Aels profile: Intel471 has published a profile on Russian hacker Andrei Vladimirovich Tarasov, also known as Aels. He was arrested in July 2023 in Germany for a hacking spree linked to the Angler exploit kit but was later released after a judge found the US had not provided enough concrete evidence for extradition. He then went back to Russia, a country he appears to hate, and continues to be active on hacker forums.
New npm malware: Two hundred forty-eight malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details .
Yeshen-Asia campaign: Safety Cybersecurity has published a report on Yeshen-Asia , a collection of 60 malicious npm packages uploaded to npm by a suspected Chinese threat actor. The packages were removed after the company published a blog post about it, after initially claiming npm was ignoring the issue.
New Breached copycats: Threat intel DarkOwl looks at the new round of copycats for the Breached hacking forum after the site went down at the start of April.
Australia Post warns of rising RCS scams: Australia Post says it is seeing an increase in parcel scams sent to its users via iMessage and Google RCS.
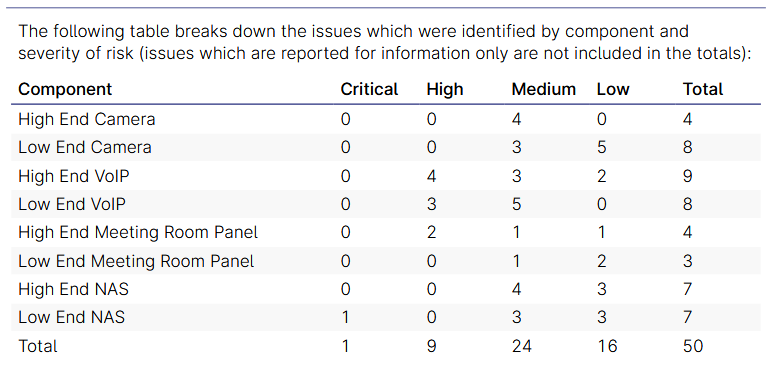
UK enterprise market study: An NCC study commissioned by the UK government has found that some types of enterprise devices used across the UK are riddled with vulnerabilities. Some of the findings are below.
- A number of serious remote code execution vulnerabilities were discovered that could give an unauthenticated attacker full control of a device over the network.
- Outdated software was prevalent across devices, with one device's bootloader being over 15 years old.
- In most cases an attacker with physical access to a device would be able to fully compromise a device and install a persistent backdoor.
- Most tested devices run all processes as the highly privileged "root" user, potentially giving an attacker unrestricted access or control of a device.
- Many of the discovered issues were related to generally insecure configuration of services, applications, or features.
Malware technical reports
HTTPBot: NSFOCUS says a DDoS botnet named HTTPBot that appeared in August of last year saw a significant spike in size last month.
VanHelsing ransomware: Fortinet researchers have published a report on the VanHelsing ransomware , a strain typically used in targeted attacks. So far, the group has targeted companies across only four countries—the US, Australia, Italy, and France.
Interlock ransomware: Resecurity has published a look at the evolution in tactics of the Interlock ransomware group .
NullPoint Stealer: ThreatMon has published a report on NullPoint Stealer , a .NET stealer whose source code got leaked online last month.
Sponsor section
Justin Kohler, VP of Product at SpecterOps, shows how BloodHound Enterprise can be used to find and fix Active Directory (mis)configurations that could let attackers easily own your entire enterprise.
APTs, cyber-espionage, and info-ops
Matryoshka campaign: Disinformation experts have spotted Russian info-op group Matryoshka launching a massive disinfo operation ahead of Russian-Ukrainian peace in Istanbul. The operation tried to portray Zelensky and Ukraine as desperate for negotiations and begging for peace. The most interesting part of the report is that Russian bot networks are so large right now on Twitter that they can generate "significant interaction" for their own posts. <s> Congratulations to Elon Musk for fixing Twitter's bot problem. </s> [ Additional coverage in The Kyiv Insider ]
"The bot posts on X have received significant interaction—though almost entirely from other accounts within the same network—while the campaign has failed to gain traction on platforms like BlueSky."
Doppelganger report: Have you ever wanted to read a 215-page report on Doppelganger, the Russian disinformation group? Now's your chance!
Doppelganger targets Romania's second election round: Romania's Interior Ministry says Russian disinformation group Doppelganger spun up a new campaign to target the second round of the country's presidential election. The group also targeted Romanians with disinformation ahead of the first round two weeks ago and a now-canceled presidential election round last year. The campaign was successful and kept Romanian authorities busy and on their toes all day on Sunday ( thread ).
Vulnerabilities, security research, and bug bounty
Volkswagen app security flaws: Volkswagen has fixed multiple vulnerabilities in its mobile app that could have allowed attackers to hijack user accounts and retrieve car and driver personal data. The app lacked brute-force protection, stored internal credentials in plaintext, and exposed any car owner's details just by supplying a vehicle ID (VIN). Security researcher Vishal Bhaskar discovered the issues last year and worked with the company to have them fixed.
Commit Stomping: ZephrSec's Andy Gill looks at Commit Stomping , a technique that abuses the ability to alter commit timestamps to hide malicious behavior.
New Windows kernel streaming bugs: DEVCORE researchers have published part three of their kernel streaming vulnerabilities, a new way to attack the Windows kernel. This third part focuses on MDL-related issues (where MDL is the Memory Descriptor List). Previous parts focused on the Microsoft Kernel Streaming Service ( MSKSSRV ) and the KS Event .
New process injection technique: Friends Security has developed a new process injection technique that relies on thread context only.
ICS honeypots: An academic research project estimates that up to 25% of industrial control systems (ICS) exposed on the internet are honeypots.
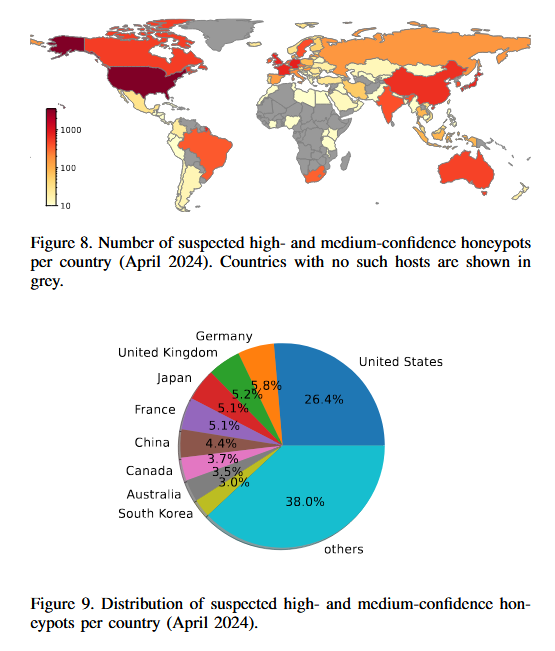
Infosec industry
Threat/trend reports: NCSC NZ , NewsGuard , ReasonLabs , and the US DOD [ PDF ] have recently published reports and summaries covering various infosec trends and industry threats.
New tool—UNIDIR Intrusion Path: The United Nations Institute for Disarmament Research has introduced Intrusion Path , a new framework for analyzing cyberattacks.
New tool—NetImpostor: A security researcher known only as Pepperoni has released NetImpostor , a tool for establishing a full stateful TCP connection with a spoofed source IP address from the same subnet using ARP poisoning.
"NetImpostor runs on Linux and can be used for defense evasion purposes, as well as for bypassing a firewall's restrictions, by using the allowed source IP from the same subnet and impersonating another computer."
New tool—TriageMCP: r-tec Cyber Security Sven "eversinc33" has released TriageMCP , an MCP server for triage and static PE analysis.
Tool update—Volatility: The Volatility Foundation has announced full feature parity between Volatility 2.x and Volatility 3.x. Volatility 2 is now deprecated.
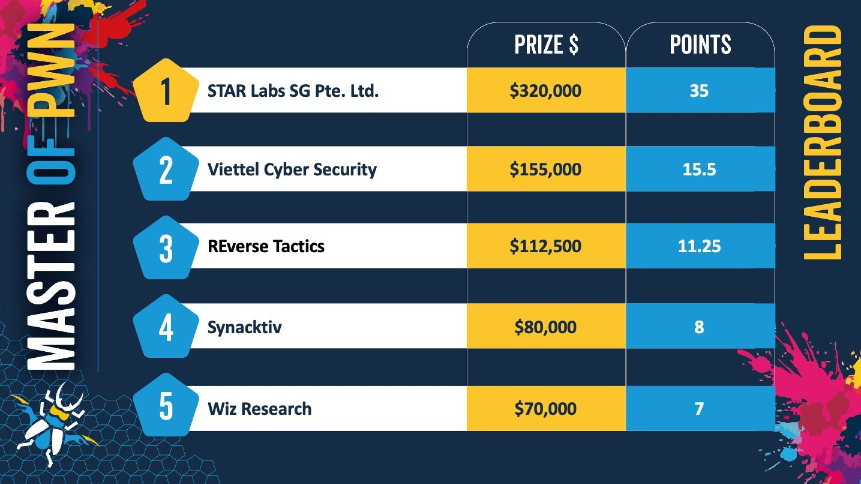
Pwn2Own 2025 Berlin: STAR Labs has won the 2025 spring edition of the Pwn2Own hacking contest, which took place this year at the OffensiveCon conference in Berlin. Day one , two , and three results are here.
Risky Business podcasts
In this special edition of the Seriously Risky Business podcast, Patrick Gray speaks with former NSA Cybersecurity Director Rob Joyce and former director of the CIA's Center for Cyber Intelligence Andy Boyd.
In this edition of Between Two Nerds, Tom Uren and The Grugq examine whether the US should steal intellectual property from Chinese companies.
