Risky Bulletin Newsletter
December 17, 2025
Risky Bulletin: Most smart devices run outdated web browsers
Written by

News Editor
This newsletter is brought to you by Push Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
An academic study by a team of Belgian researchers has found that most of today's smart devices come with an embedded web browser that runs extremely out of date versions, sometimes as much as three years.
The study, from the Catholic University in Leuven, Belgium (KU Leuven), looked at browsers that ship with smart TVs, e-readers, gaming consoles, and other modern hardware.
All five e-readers that were tested, and 24 of 35 smart TV models, used embedded browsers that were at least three years behind current versions.
Some devices were released with vulnerable browsers from day one. For example, researchers found eight products that shipped with browsers over three years old at launch, exposing their buyers to attacks as soon as they turned on their products.
While some manufacturers advertised free firmware updates, most failed to update the embedded browsers.
The study found that device makers consistently failed to incorporate the free automatic updates that most current browser makers provide.
Researchers didn't discuss theoretical risks, but also reproduced known exploits to attack and compromise the embedded browsers.
In many cases, the browsers are embedded in the smart device user interface without their normal browser UI, so most device owners wouldn't be able to install updates even if they wanted. These types of deployments require the vendor to take the browser update, add it to its firmware, and then ship a firmware update, something that many vendors won't do due to development costs.
The team reported its finding to Belgian and US authorities, but only the Belgian Centre for Cybersecurity tried to facilitate engagement with vendors. The FTC did not respond.
The findings paint a grim picture for hardware vendors in the EU, which will have to ship regular and timely security updates starting with 2027, under the new EU Cyber Resilience Act. These updates will have to cover browser updates if the devices are commonly used to navigate the web.
"Our research shows that many vendors do not yet comply, even when examining just the embedded browsers of products. We aim to provide ongoing insights into how vendors improve (or fail to improve) their cybersecurity practices in relation to embedded browsers ahead of the Act's full implementation."
The research was presented in August at the Usenix SOUPS conference, but the team is still collecting data via a dedicated web page that users can access with their smart device.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Ribbon Finance crypto-heist: Hackers have stolen $2.7 million worth of crypto assets from Ribbon Finance last week. [Cryptopolitan]
Prosper data breach: Peer-to-peer lending platform Prosper has disclosed a security breach. The breach took place between June and August and impacted 17.6 million customers. The hackers stole personal information such as names, home addresses, and driver's license and Social Security numbers.
SoundCloud security breach: Hackers have breached music streaming service SoundCloud and stolen some user data. The breach impacted an ancillary service dashboard. SoundCloud says hackers have stolen data on almost 20% of its users, but all the data was part of public profiles.
PornHub is being extorted: Hackers are threatening to release search and watch history for PornHub premium users. ShinyHunters claims to have stolen more than 94GB of data from one of PornHub's analytics providers. The group is now demanding a ransom or it will release the data. PornHub says the information was taken from analytics company Mixpanel. OpenAI was also affected by the same Mixpanel breach. [BleepingComputer]
PdV cyberattack: A cyberattack has crippled the activity of Venezuelan state-owned oil and gas company Petroleos de Venezuela. The attack shut down operating and control systems for docks, production, and refineries in the country's northern region. The intrusion was allegedly a ransomware attack. [Argus Media//Reuters]
Iranian hackers put out bounties: An Iranian hacktivist group is offering $30,000 bounties for information on Israeli engineers working in the defense sector. The Handala hacker group is seeking information on Israeli engineers who work on Israel's Patriot, Arrow, and David's Sling air defense systems. The group doxxed multiple Israeli engineers last week in an attempt to intimidate them. Handala previously also offered bounties for information on Israel's intelligence agency and military personnel. [The Jerusalem Post]
Ukraine hacks ASCON: Ukrainian hacktivists have breached and sabotaged a major Russian defense contractor. The KibOrg group claims it wiped systems at ASCON, a software developer for the Russian defense industry. Hackers claim to have stolen more than 10TB of internal data and wiped backups and CCTV systems. ASCON develops software for Russian missiles, tanks, nuclear, and radar systems. [KibOrg//Archived]
Russian hackers breach Dutch public fountain: Russian hacktivists hacked and tried to sabotage a public fountain in the Netherlands. Hackers breached the system last year and tried to modify water levels. The incident took place last year and officials did not release the city's name. Dutch military security service MIVD described the hack as "the first Russian sabotage attack in the Netherlands." [Volkskrant]
General tech and privacy
Data centers are getting hot: More than 600 data centers, typically situated around the equator, are above their max operating threshold of 27 °C. [Rest of World]
Mozilla CEO goes full on AI: Mozilla's newly appointed CEO Anthony Enzor-DeMeo said the browser will shift to incorporating more AI technology in the coming year. Enzor-DeMeo told The Verge the browser now has around 200 million monthly active users, just 5% of Chrome's total user base.
Texas sues 5 smart TV manufacturers: The Texas Attorney General has sued five smart TV makers for illegal data collection practices. Lawsuits have been filed against Sony, Samsung, LG, Hisense, and TCL. The lawsuits claim smart TVs from the five companies use Automated Content Recognition (ACR) technology to spy on what users are watching. ACR technology takes screenshots of a TV's screen and uploads it to the TV maker's servers for analysis.
Google shuts down Dark Web Report: Google will shut down its Dark Web Report security feature next year. The feature notified users when their Google account data appeared on the dark web and prompted users to reset passwords. The feature will stop scanning the dark web on January 15 and shut down for good a month later.
Microsoft deprecates RC4: Microsoft is deprecating the old RC4 encryption cipher from Kerberos authentication. The cipher is vulnerable to Kerberoasting, an attack that allows threat actors to retrieve account credentials from Active Directory servers. Microsoft's decision to deprecate the protocol comes after US Senator Ron Wyden called on the FTC to investigate the company over its use of the antiquated cipher. The cipher played a crucial role in the Ascension Healthcare ransomware attack last year. [ArsTechnica]
Last week I announced that we're finally killing off RC4 in the Windows Kerberos stack. This has been a long time coming, so much so that we've been working on it for more than a decade, albeit off and on as we sometimes had to target other more pressing issues. What does this mean?
— Steve Syfuhs (@syfuhs.net) 2025-12-10T18:48:57.304Z
Government, politics, and policy
UK government ramps up war against porn: The UK government has asked tech companies to block nude images at the hardware level. The Home Office wants phone and laptop makers to deploy nudity-detection algorithms on their devices. Device owners will be blocked from taking or sharing explicit photos or videos unless they prove their age to the device maker. The new requirement is meant to protect children from pornography and move the age verification process from websites to user devices. [The Financial Times]
New NSA, CyberCom favorite: The White House is preparing to nominate Army Lt. Gen. Joshua Rudd, as the next head of Cyber Command and the US National Security Agency. Gen. Rudd is currently serving as deputy chief of US Indo-Pacific Command. Both CyberCom and the NSA have been without a leader since Trump dismissed Air Force General Timothy Haugh in April. The nomination of Army Lt. Gen. William Hartman for the same position fell through in October. [The Record]
US cybersecurity strategy: GovNext has more details on the upcoming US cybersecurity strategy that is supposed to free up US cyber agencies into responding to cyberattacks with offensive cyber operations, including the use of private contractors. The document is expected to be published next month. It's a long read and hard to summarize here.
US Tech Force: After dismantling the 18F department that provided the US government with cheap custom technology, the Trump administration announced the US Tech Force. The new agency will recruit around 1,000 tech workers from large US corps to "modernize" the government's network (most likely to peddle their stupid AI and proprietary walled garden ecosystems). Private sector partners include the usual list: AWS, Apple, Google, Dell, Microsoft, Nvidia, OpenAI, Oracle, Palantir, and Salesforce. [CNBC//FedScoop]
So the federal government deleted 18F, which was doing great work modernizing the government, and then replaced it with a clone? What is the point of all this. techforce.gov
— Eugene Vinitsky 🍒 (@eugenevinitsky.bsky.social) 2025-12-15T21:29:38.928Z
Sponsor section
In this Risky Business sponsor interview, Casey Ellis is joined by Push Security’s Field CTO, Mark Orlando. They chat about the ways that browser-based attacks are evolving and how Push Security is finding and cataloging them.
Arrests, cybercrime, and threat intel
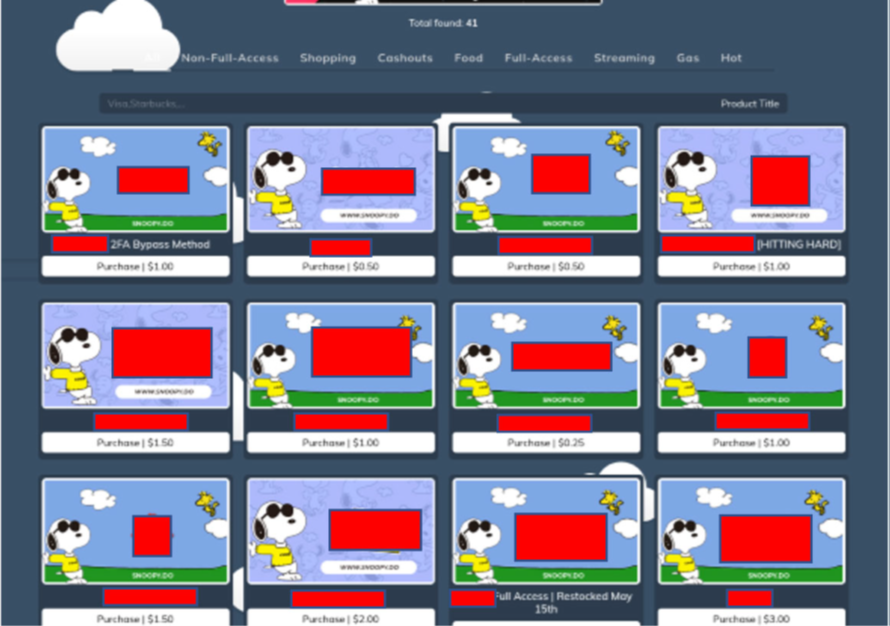
DraftKings hacker pleads guilty: A 20-year-old from Minnesota has pleaded guilty to hacking sports betting website DraftKings. Nathan Austad admitted to launching a credential-stuffing attack against the platform in November of 2022. Austad used the hacker pseudonym of Snoopy and worked with two other co-conspirators. The trio hacked and then sold access to more than 60,000 DraftKings accounts. All three were arrested last year and have now pleaded guilty. One of his co-conspirators has been sentenced to 18 months in prison.
SMS blasters detained in Serbia: Serbian police have detained two Chinese nationals for driving around with an SMS blaster device in their car. The duo allegedly sent SMS phishing messages that lured locals to phishing sites. The sites posed as mobile operators and government portals to collect payment card details. Collected card data was later abused overseas. [CommsRisk]

Ukraine dismantles fraud call centers: Ukrainian authorities have dismantled fraud call centers across three cities. The call centers collected more than €10 million from victims across Europe. The operators posed as local governments and law enforcement to trick victims into wiring them money. Authorities have identified 45 suspects and arrested 12.
DDoSia ephemeral infrastructure: Censys looked at DDoSia, an open-participation DDoS botnet managed by the NoName057 group. The botnet was taken down earlier this year and has now made a comeback. Censys says the botnet is typically managed through new command and control servers that only live for a few hours, or a few days, at max.
Browser hijacking techniques: G DATA researcher Karsten Hahn looks at three popular techniques modern malware is using to hijack web browsers.
Malware hits RuTube: Malicious videos leading users to malware-laced files have made their way on Russia's RuTube, its in-house YouTube clone.
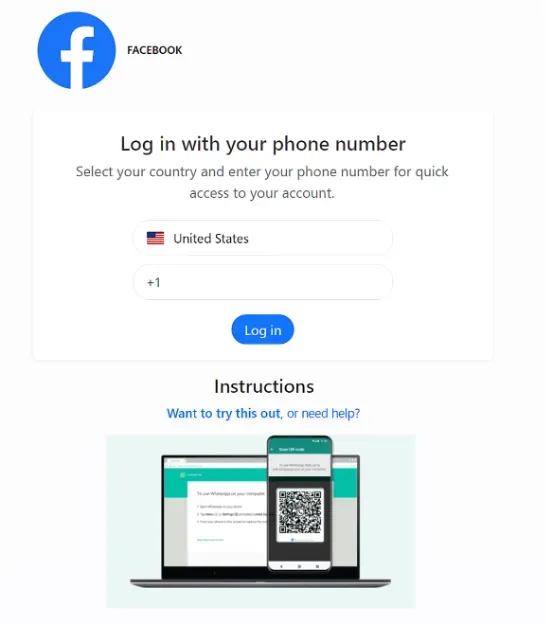
GhostPairing technique: Threat actors are using a new social engineering technique to hijack WhatsApp accounts. The new GhostPairing attack lures victims on pages with malicious QR codes. Scanning the codes will link an attacker's device to the victim's WhatsApp account. The attack is a variation of a technique used by Russian state-sponsored hackers to intercept Signal messages earlier this year.
NuGet malware: Socket Security has spotted a new malicious NuGet package that steals Stratis wallet passwords and uploads them to a Russian IP address.
Chrome extension steals AI prompts: A Chrome extension has been caught collecting prompts that users entered into AI chatbots. The Urban VPN Proxy extension collected prompts from ten AI platforms, such as ChatGPT, Copilot, Gemini, and Deepseek. The extension developers claimed they collected the prompts to check for malicious links returned by the chatbots. The same developer has been linked to shady data collection practices this year by two other researchers.
Parked domains for malvertising: Infoblox says some parked domains inventories are being used to deliver malvertising.
BPH ecosystem overview: Security firm Silent Push has published a report on today's most notorious bulletproof hosting providers, internet companies that provide hosting to criminal threat actors and which do not honor abuse reports from authorities or security firms.
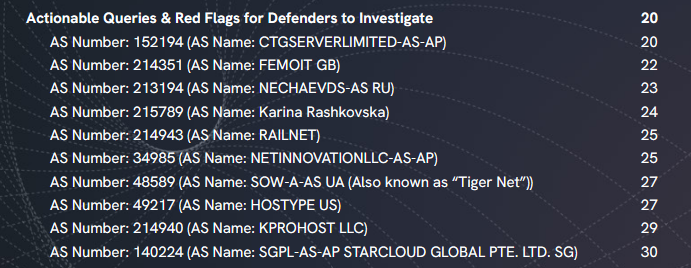
Big day for Silent Push, which released today a "magnum opus" on bulletproof hosting providers and announced its purchase of Canadian preemptive cyber defense vendor Hyas. www.silentpush.com/white-papers... www.govinfosecurity.com/silent-push-...
— Cynthia Brumfield (@metacurity.com) 2025-12-15T19:29:10.957Z
Malware technical reports
The Gentlemen ransomware: AhnLab has published a technical report on The Gentlemen, a new ransomware group that popped up online in August. See similar reports from Cybereason and Trend Micro.
Makop ransomware: Acronis has published a write-up on the Makop ransomware. The ransomware is typically delivered via RDP exploitation and most of its victims are based in India. In recent intrusions, the group has also started deploying the GuLoader malware along the ransomware.
Frogblight: Kaspersky has discovered a new Android banking trojan named Frogblight. The malware is currently being used to target Turkish banks.
Cellik has a "Play Store integration" feature: A new Android RAT named Cellik is being sold on underground forums with a special feature that lets threat actors bundle it into legitimate apps hosted on the Play Store.
NexusRoute campaign: CyFirma looks at NexusRoute, an e-crime campaign that targets Indian Android users. The campaign impersonates the Indian Government Ministry and the official mParivahan and e-Challan apps.
DarkGate adopts ClickFix: The DarkGate malware loader is now using ClickFix for initial distribution campaigns, according to new Point Wild research.
ZnDoor: NTT Security looks at ZnDoor, a backdoor deployed via the recent React2Shell exploits.
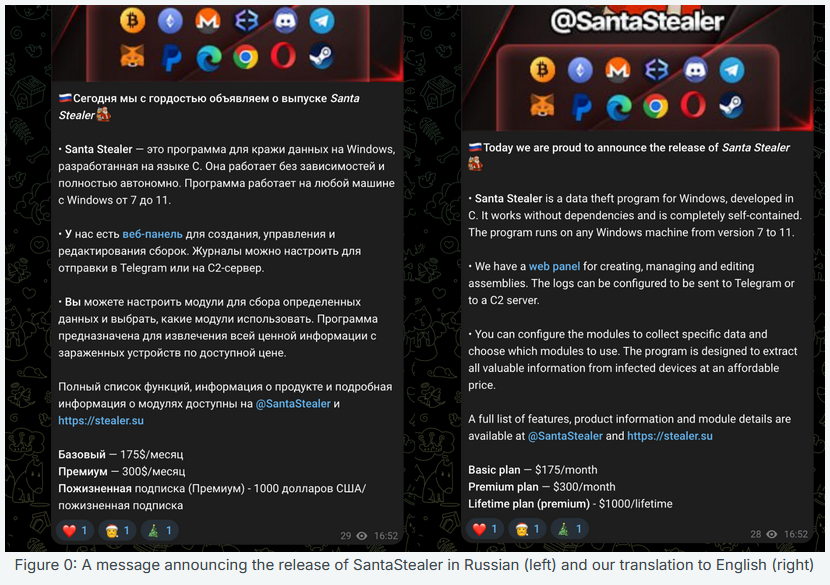
SantaStealer: There's a new infostealer in town named SantaStealer, launched just in time for the winter holidays! According to Rapid7, the infostealer is a rebrand of the older BluelineStealer.
Sponsor section
In this wholly sponsored Soap Box edition of the show, Patrick Gray chats with Adam Bateman and Luke Jennings from Push Security.
APTs, cyber-espionage, and info-ops
GRU critical infrastructure hacks: Russian military hackers have increased their attacks against critical infrastructure in NATO and Western countries. Attacks have shifted this year from vulnerability exploitation to targeting misconfigured edge devices. The AWS security team has linked the attacks to units inside Russia's military intelligence agency GRU.
Ink Dragon: Check Point looks at new campaigns from the Ink Dragon APT, also known as Earth Alux, Jewelbug, REF7707, CL-STA-0049. The group deploys a ShadowPad IIS implant on misconfigured ASP.NET apps.
DRBControl's Type 1 backdoor: IIJ researchers look at Type 1, a new backdoor used by DRBControl, an APT group with a history of targeting casino and gambling operations.
UNC5174's SNOWLIGHT: Seokia has published a report on the Linux version of SNOWLIGHT, a malware downloader used by UNC5184. The group is a suspected MSS cyber contractor.
Kimsuky's Android ops: South Korean security firm ENKI has spotted North Korean hacking group Kimsuky using Android malware to go after their targets.
"While we could not confirm the initial vector, we assess that the threat actor distributed the malicious APK link via smishing and used QR codes to lure victims into downloading and executing the app on their smartphones."
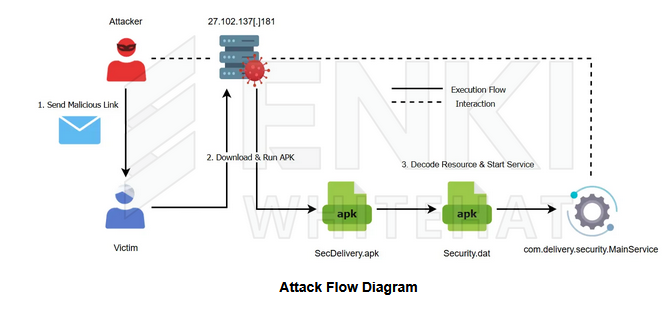
Vulnerabilities, security research, and bug bounty
Gladinet exploitation: Threat actors are exploiting a new vulnerability in Gladinet CentreStack and Triofox file-sharing servers. Attackers use the vulnerability (CVE-2025-14611) to retrieve a hardcoded cryptographic key, which they then use to run malicious code. The vulnerability has been abused in the wild as a zero-day since last month. According to security firm Huntress, at least nine companies have been hacked so far.
New Fortinet attacks: Threat actors are exploiting two Fortinet vulnerabilities (CVE-2025-59718 and CVE-2025-59719) that were patched last week. Attacks have been spotted by security firm Arctic Wolf. The vulnerabilities allow attackers to bypass the SSO authentication on Fortinet devices. Attacks aren't widespread because FortiCloud SSO login is disabled by default.
MGT Varnish backdoor mechanism: MGT Commerce has released a security update to remove a backdoor mechanism from one of its Magento extensions. The system could have allowed remote attackers to run malicious code on servers running the MGT Varnish caching component. Security firm Sansec believes the backdoor system was benign and was used for debugging and to enable remote upgrades.
Email client audit: Germany's cybersecurity agency BSI has conducted a security audit of 12 email clients.
JumpCloud vulnerability: XM Cyber researcher Hillel Pinto discovered a critical vulnerability in the JumpCloud Remote Assist for Windows agent. This is tracked as CVE-2025-34352.
Windows Admin Center EoP: Cymulate has published a write-up on CVE-2025-64669, an elevation of privilege vulnerability in the Windows Admin Center that was patched this month.
VStarcam vulnerabilities: Security researcher Wladimir Palant looked at multiple vulnerabilities in the firmware of VStarcam IP cameras. They are still unpatched.
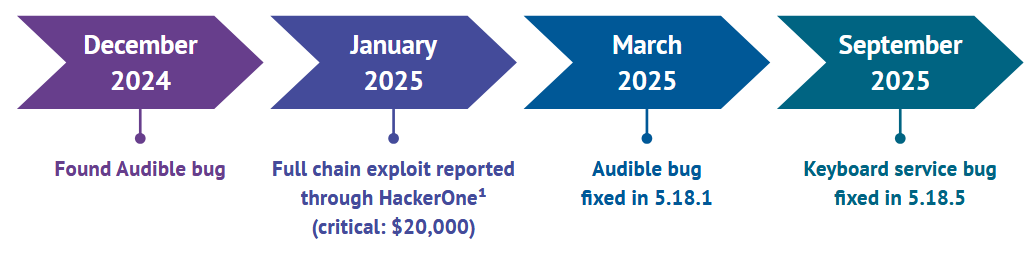
Kindle vulnerability: Amazon has patched a vulnerability in the Kindle e-book reader. The security flaw could have allowed threat actors to gain root access over the device and take over a user's Amazon account. The delivery method was a malicious Audible e-book file and the vulnerability exploited the media parsing process. The issue was discovered by Thales security researcher Valentino Ricotta, who received a $20,000 bug bounty for his finding. [The Times]
Infosec industry
Threat/trend reports: Cloudflare, Counterpoint, F6, LevelBlue, ThreatRecon, and Sedgwick have recently published reports and summaries covering various threats and infosec industry trends.
Acquisition news #1: Cybersecurity company Silent Push has acquired HYAS, an adversary infrastructure tracking platform.
Acquisition news #2: Cybersecurity firm Cyderes has acquired Lucidum, a provider of security data fabric and entity intelligence.
New tool—AZexec: Security firm Logisek has released AZexec, a PowerShell-based Azure/Entra ID enumeration tool.
New tool—UEFI Secure Boot guide: The NSA has released a guide on how to configure UEFI Secure Boot and harden setups against rootkits.
Usenix SOUPS videos: Talks from the Usenix Symposium on Usable Privacy and Security (SOUPS) 2025 security conference, which took place in August, are available on YouTube.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk to Hamid Kashfi, CEO and founder of DarkCell, about the Iranian cyber espionage scene.
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray discuss a new report proposing a framework for deciding when cyber operations raise red flags. It suggests seven red flags and could help clarify thinking about how to respond to different operations.
