Risky Bulletin Newsletter
September 12, 2025
Risky Bulletin: Most UK school hacks are caused by their own students
Written by

News Editor
This newsletter is brought to you by Trail of Bits . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
In the podcast version of this newsletter, we reported that that the personal data of almost 6000 Australian doctors and staff had leaked online. We meant to say 600!
The written newsletter has the correct number.
The UK's privacy watchdog highlighted a strange trend in the country where students are increasingly behind the hacks of their own schools.
The UK Information Commissioner's Office says it studied 215 insider-caused breaches in the UK educational sector between 2022 and mid-2024 and found that students were behind 57% of the intrusions.
Where a stolen password was used to breach a school system, students were involved in almost all cases (97%).
"Dares, notoriety, financial gain, revenge, and rivalries" were cited as main reasons for the hacks, which sounds about right if I channel my inner child.
Breaches were blamed on staff leaving devices unattended, students being allowed to use staff devices, incorrect permissions on school resources, and, in the rare 5% cases, on insiders using sophisticated techniques to bypass security and network controls.
The ICO study has two main conclusions. The first is that this type of early familiarization with hacking might lead kids on the wrong path and become a gateway to a life of cybercrime. I don't particularly agree with this. Getting into cybercrime is typically motivated by financial or social pressures.
The second is that this is also the schools' fault for failing to properly secure their networks. I do, somewhat, agree with this one.
The ICO urges schools to "remove temptation from students" and take steps to improve their cybersecurity and data protection practices.
That may not be as simple as the ICO hopes, though. According to British non-profit the National Education Union , the vast majority of UK schools face budget cuts and will not be able to afford most basic costs, let alone cybersecurity investments.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Dior fined in China: Chinese authorities have fined French fashion house Dior over a May data breach. Officials said Dior violated China's Personal Information Protection Law by sending the data of Chinese users overseas. Foreign companies must pass a security review with local authorities before collecting Chinese citizens' data. Dior was hacked in May in a series of hacks that targeted multiple subsidiaries of French fashion group LVMH. [ Additional coverage in Global Times ]
New Salesloft victims: New companies have added their names to the list of organizations impacted by the Salesloft Drift supply chain attack. They include HackerOne and Pantheon .
NSW Health doctors leak: The personal data of almost 600 NSW Health doctors and staff leaked online. Leaked data includes passports, licences, and medical credentials. NSW Health says the files leaked after a misconfiguration on its website. [ Additional coverage in Sky News Australia ]
Hello Gym leak: American gym chain Hello Gym leaked over 1.6 million voice recordings from gym members. The files leaked from a misconfigured AWS server managed by a contractor. Some of the calls contained members' personal information.
Washing machine hacks: A university campus in Amsterdam has shut down its laundry room after its five smart washing machines were hacked in July. Students were able to wash clothes for free for months, but the campus is now declining to cover the washing costs. Five "dumb" washing machines with a coin-based payment system are expected this month. [ Additional coverage in Folia ]
Panama ransomware attack: Panama's Ministry of Economy and Finance has fallen victim to a ransomware attack . The attack did not reach critical systems, and the Ministry has continued to operate normally. The INC ransomware group has taken credit for the intrusion and claimed to have stolen more than 1.5TB of data. [ h/t chum1ng0 ]
FastNetMon DDoS attack: A DDoS attack that clocked at more than 1.5 billion packets per second (Bpps) targeted the network of a DDoS mitigation service in Western Europe. The attack originated from a botnet made up of home routers and IoT devices.
Kenyan filmmakers hacked: Two Kenyan filmmakers had spyware installed on their devices by Kenyan police. The two were arrested in May for allegedly publishing false information related to a documentary on a recent youth uprising. They had devices seized that were returned two months later, containing the FlexiSPY spyware. The filmmakers appeared in court multiple times but have yet to be charged. [ Additional coverage in the CPJ ]
No money for Irish cops: The Police Service of Northern Ireland (PSNI) has told a judge it does not have the money to compensate cops impacted by a 2023 security breach. According to the BBC , affected staff are allegedly looking for around £100 million in damages, or around £10k per individual. More than 9,400 cops and police staff had their data leaked online due to a website misconfiguration.
IT employee sues over breach fallout: A former IT employee is suing the Fulton County government for being unfairly blamed for a security breach. Omotade Adeniyi says a 2024 ransomware attack was blamed on him even though the breach originated from other employees' systems. He also claims he suffered racial abuse from his supervisor due to his Nigerian origins. Adeniyi was placed on leave after the hack and then fired a few months later, together with another Nigerian colleague. He previously worked for Fulton County for 14 years. [ Additional coverage in Atlanta News First ]
Apple sends spyware notifications to French users: Apple has notified users in France of a spyware campaign that targeted their devices. The notifications went out on September 3. According to France's cybersecurity agency , it is the fourth time this year that Apple has notified French citizens of spyware attacks. Previous notifications went out in March, May, and June.
General tech and privacy
Android C2PA Content Credentials: Google has published an explanation of how its new C2PA Content Credentials system works. The system uses cryptography to authenticate photos as coming from an official Pixel smartphone. It is designed to help identify when photos are edited or modified by AI tools.
BlueSky age checks: BlueSky says it will implement age checks for South Dakota and Wyoming after previously declining to do so for Mississippi.
More pr0n investigation in the UK: The UK's telecommunications watchdog has launched investigations against 22 adult and pornography sites. The sites are being investigated for failing to comply with the UK Online Safety Act and implement age checks for UK visitors. Ofcom launched a similar investigation against 34 porn sites at the end of July.
Apple secretly tweaks AI: According to a leaked memo obtained by Politico Europe , Apple started to secretly tweak its AI algorithm to be more conservative following pressure from the White House. fReE sPeEcH cOuNtRy!!!!
California's Project Sherlock: Billionaire Tom Siebel's C3 AI and Amazon are building Project Sherlock, a sprawling surveillance and policing system for the state of California. [ Additional coverage in Forbes ]
Microsoft makes Store publishing free: Individual developers can now publish their apps on the Windows Store for free , without paying onboarding fees. Developers will no longer need a credit card to set up their account. Microsoft announced the new rules as it's struggling to populate the Store with apps from its sprawling developer landscape. Most developers still publish apps via their own websites or via GitHub.
Durov gloating: Telegram CEO Pavel Durov is gloating that his app was used to plan the "Block Everything" protests by France's far-right parties this week. According to Reuters , French intelligence is investigating foreign interference in the protests.
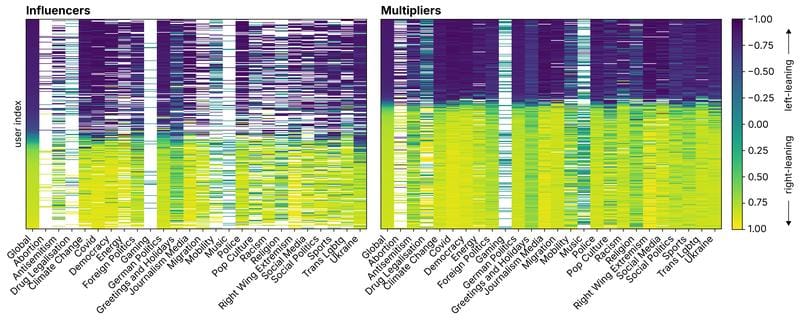
Social media division: An academic study has found that "influencers" are responsible for a lot of the societal and political polarization on Twitter. "Multiplier" accounts then help promote those messages.
Government, politics, and policy
GPC investigation: State attorneys general from California, Colorado, and Connecticut have announced a joint investigation into companies refusing to comply with Global Privacy Control. The GPC is a protocol that notifies websites and advertisers that users don't want their data collected and sold. Data trackers that refuse to honor the GPC are in violation of recently passed state privacy laws. Seven other US states also require companies to honor GPC, but have not joined the enforcement action.
ICE stingray use: According to Forbes , the US ICE used a stingray (fake cell tower) device to track down individuals for deportation.
Wyden calls for Microsoft FTC investigation: Sen. Ron Wyden (D-Ore.) has called on the FTC to investigate Microsoft for its shoddy products and " culture of negligent cybersecurity " that enabled the Ascension Health hack of last year.
CISA to look for more CVE funding: CISA will explore alternative funding mechanisms for the CVE program. The program assigns identifiers and tracks security flaws for the US government. The database is run by the MITRE Corporation, and the program almost collapsed in April after CISA funding lapsed. [ Additional coverage in NextGov ]
China to increase fines for data breaches: The Chinese government is working on an amendment to its cybersecurity law that would increase fines for data breaches. Critical infrastructure operators could face fines of up to $1.4 million (¥10 million). Individuals responsible for a breach could also face personal fines of up to $14,000 (¥100,000). The amendment again threatens punishments for companies storing "important" data overseas. [ Additional coverage in China Daily ]
France social media ban: The French government is working on a law that would ban kids under the age of 15 from social media. The law would also introduce a nighttime curfew for children aged 15 to 18. Australia has already enacted a similar law that bans social media apps for kids under 16. [ Additional coverage in RFI ]
UK delays cybersecurity law: The UK government has delayed the Cyber Security and Resilience Bill (CSRB) again after failing to pass it for the past three years. [ Additional coverage in The Record ]
Sponsor section
In this Risky Business sponsor interview , Casey Ellis chats with Keith Hoodlet from Trail of Bits. Keith is Trail of Bits' director of engineering for AI, machine learning, and application security, and he joined Casey to talk about why prompt injection attack techniques that target AI are an unsolvable problem.
Arrests, cybercrime, and threat intel
Vastaamo hacker released from prison: Finnish hacker Aleksanteri Kivimäki has been released from prison following an appeal. Kivimäki hacked Finnish psychotherapy centre Vastaamo in 2020 and released highly sensitive patient files. He was arrested in 2023 following an international manhunt. He was sentenced last year to six years in prison. The court released him because he is a first-time offender and had already served almost half of his sentence. [ Additional coverage in YLE /English version here ] [ h/t Brian Krebs ]
Fake QR codes: The Hague in the Netherlands has warned citizens about fake QR codes being placed on top of legitimate ones in parking lots across the city. The QR codes redirect users to phishing sites where hackers intercept parking payments and steal banking details. Similar schemes have also been spotted in the UK and the US last year.

PoisonSeed infrastructure: The DomainTools security team has spotted new domains linked to PoisonSeed, a financially motivated threat actor known for its phishing operations.
AdaptixC2 abuse: PAN's Unit42 has spotted threat actors abusing a new open-source C2 framework named AdaptixC2 in the wild.
Ransomware costs surge, despite fewer attacks: The costs associated with ransomware attacks have risen this year, despite a smaller number of attacks and cyber-insurance claims. Cyber insurance provider Resilience says ransomware costs rose by 17% even if claims were down by 53%. Ransomware was the dominant claims category, accounting for 91% of all losses this year. [ Additional coverage in CFODive ]
Rise in UK scam waves: UK mobile operator Virgin Media O2 says there is a "significant rise" in SMS scam texts. The most common themes are gambling, recruitment, and car finance-related scams.
"More than 600 million scam text messages have been blocked from reaching O2 customers phones so far in 2025 – more than double the number in 2023 and 2024 combined."
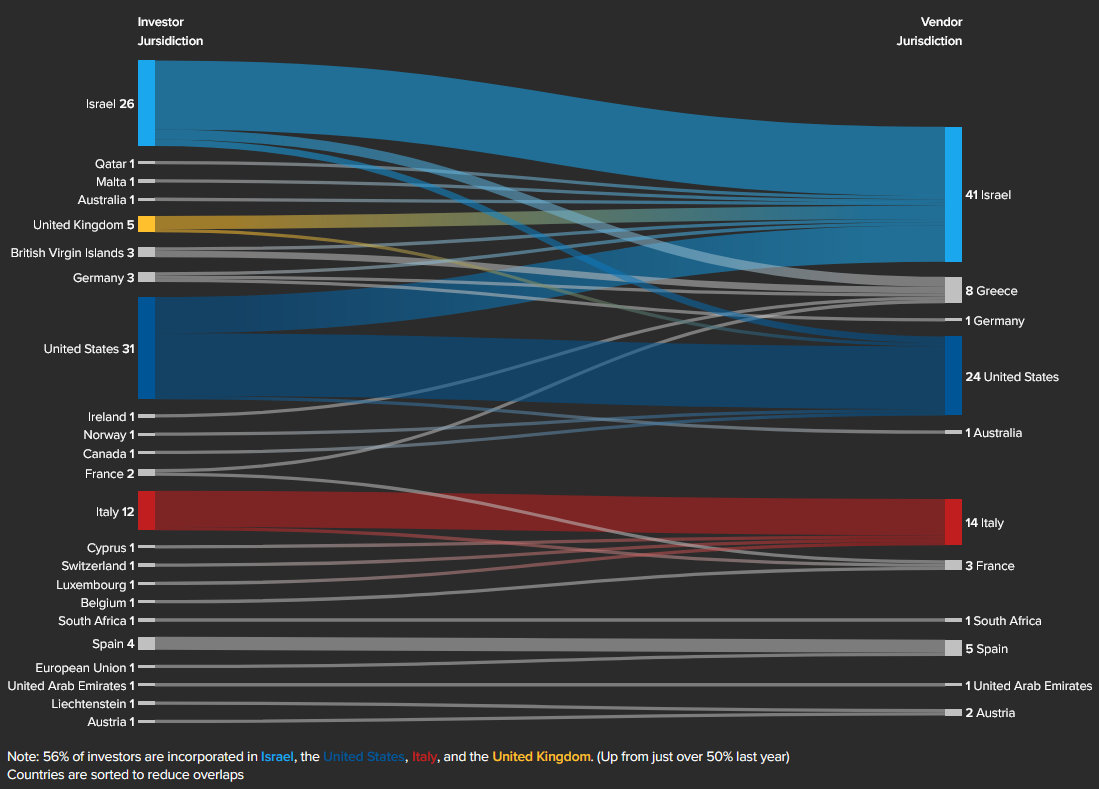
US investment in spyware triples: The number of US investors in spyware and surveillance technologies has tripled in 2024 compared to the previous year. The US is now the largest investor in spyware technologies, with 31 entities compared to just 11 in 2023. According to the Atlantic Council , most of the US investor money has flowed to entities in the US and Israel.
Akira's SonicWall campaign: Australia's cybersecurity agency has detected a spike in attacks against SonicWall devices. The attacks have been linked to the Akira ransomware group. The group is allegedly using a 2024 vulnerability and compromised credentials as an initial entry point into corporate networks.
Nulled plugins campaign: Wordfence has spotted a campaign using "nulled" (cracked, pirated) WordPress plugins to backdoor websites with rogue admin accounts.
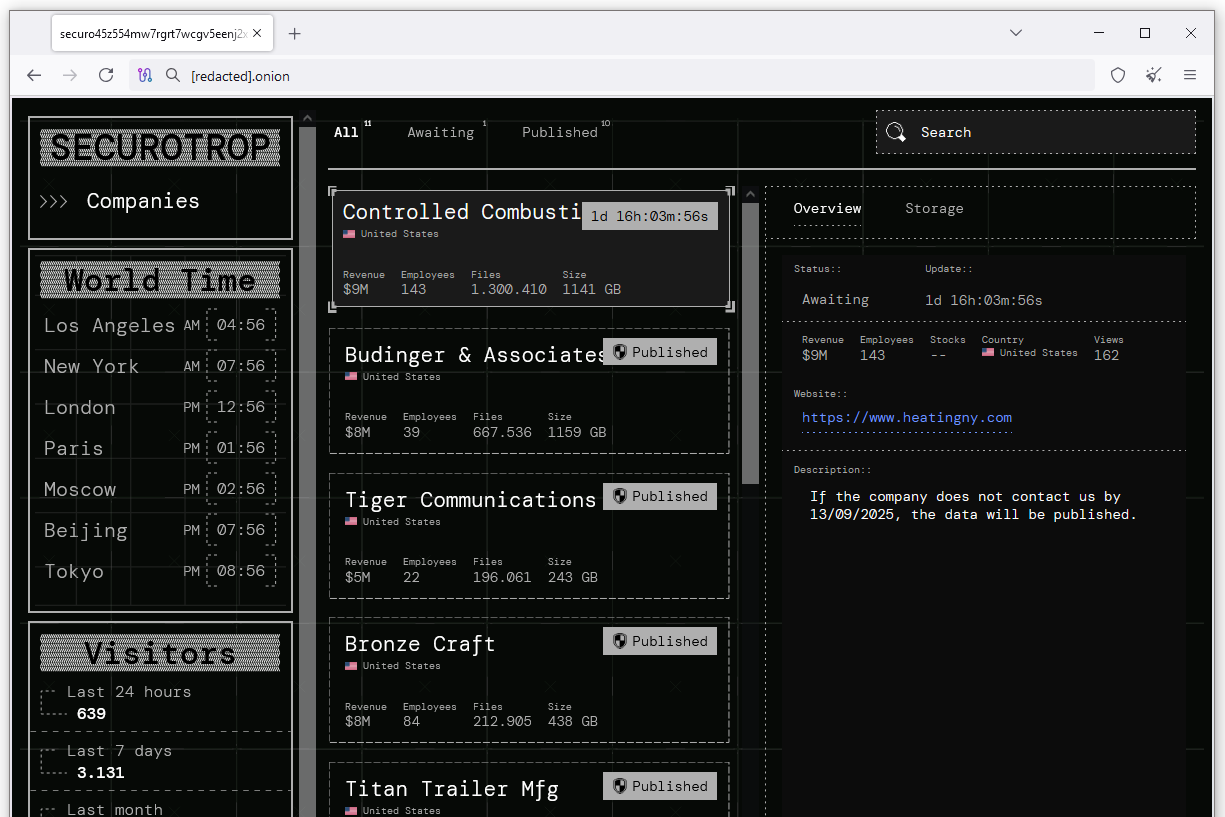
New Securotrop ransomware: A new ransomware group named Securotrop has been spotted extorting victims this month. Its dark web leak site currently lists 10 victims.
Malware technical reports
ChillyHell backdoor: Jamf researchers have published a technical analysis of ChillyHell , a macOS backdoor that's been silently distributed in the wild since 2021.
kkRAT: Zscaler has spotted kkRAT , a new remote access trojan making the rounds on the Chinese underground cybercrime scene.
BaoLoader: Expel has published a report on BaoLoader , a PUP signed with stolen certs and used to load malicious Chrome extensions.
CyberVolk ransomware: AhnLab has published a report on a new RaaS platform named CyberVolk . The service launched at the start of July and targets home users with small $1,000 ransoms. The group is a former pro-Kremlin DDoS group that shifted to ransomware attacks last year. It also claims to be based in India.
BlackNevas ransomware: The same AhnLab team also looked at the BlackNevas ransomware , which they believe is a rebrand of the older Trigona group.
Sponsor section
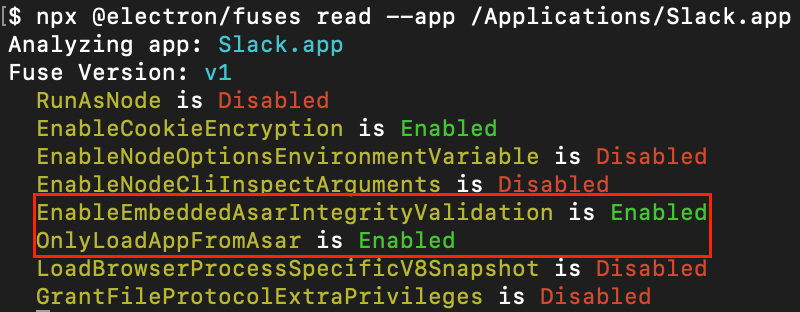
A vulnerability discovered by Trail of Bits in Electron applications allows attackers to bypass code integrity checks by tampering with V8 heap snapshot files, enabling local backdoors in applications like Signal, 1Password, and Slack.
APTs, cyber-espionage, and info-ops
Salt Typhoon companies: Natto Thoughts has published profiles on Beijing Huanyu Tianqiong and Sichuan Zhixin Ruijie, two of the three Salt Typhoon contractors that were recently sanctioned by US authorities. Natto published a profile on the third, Sichuan Juxinhe, here .
ToneShell in Myanmar: Intezer has spotted a new version of the ToneShell backdoor being deployed in attacks in Myanmar. The malware has been historically used by a Chinese espionage nexus known as Mustang Panda.
EggStreme in the Philippines: Bitdefender has discovered a fileless malware framework named EggStreme that appears to have been used in a suspected Chinese APT attack against the Philippines' military base.
APT1 backstory: Kim Zetter is looking into the backstory of Mandiant's 2013 APT 1 report, the first report on an APT of its kind.
Vulnerabilities, security research, and bug bounty
bugSWAT event: Google has awarded ~$1.6 million to security researchers during a recent hackathon event. The event focused on the Google Cloud platform and helped patch 91 valid vulnerabilities. The hackathon accounted for two-thirds of the bug bounties paid for Google Cloud this year.
Activision VRP: Activision said this week that the team behind its RICOCHET anti-cheat engine is also involved in its official bug bounty program, so bug reports will also be evaluated for their cheating potential.
FreePBX zero-day: WatchTowr Labs has published a write-up on CVE-2025-57819, the FreePBX zero-day that was disclosed and patched last week.
"The report demonstrates how the commercial Endpoint module is being exploited through an authentication bypass and SQL injection chain to achieve full remote code execution, allowing adversaries to create backdoor users, tamper with databases, and use scripts to wipe logs and hide their activity. While FreePBX has issued an out-of-band patch for the Endpoint module, parts of the attack chain remain unpatched."
Argo CD write-up: FutureSight has published a write-up on CVE-2025-55190, the Argo CD bug that can leak Git credentials.
VMScape attack: A team of academics has developed a new side-channel attack that breaks virtualized environments. The VMScape attack works against AMD Zen CPUs and Intel Coffee Lake processors. It is a Spectre-like attack that can allow malicious guests in a cloud environment to leak hypervisor data.
AirBorne attack also impacts CarPlay: Two Apple AirPlay vulnerabilities known as AirBorne also impact the Apple CarPlay service .
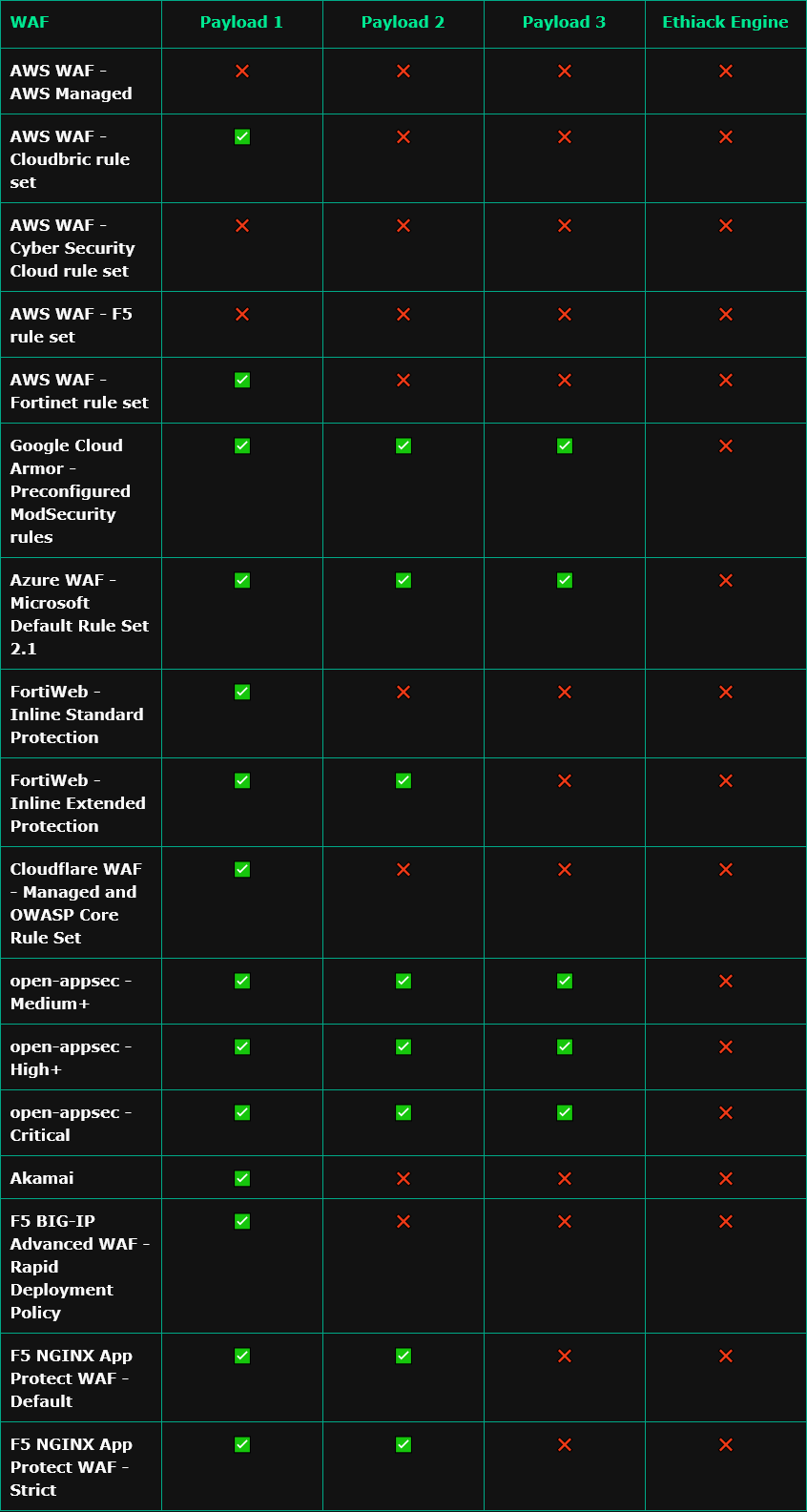
Bypasses in 9 WAFs: A new exploit allows threat actors to bypass the web application firewalls of nine vendors. The attack abuses parameter pollution techniques and was found by security firm ETHIACK. It was tested against 9 WAFs in 17 different configurations.
Infosec industry
Threat/trend reports: FB-ISAO , Prophet Security , Resilience , Schneider Electric [ PDF ] , Sophos , Tenable , and Zscaler have recently published reports and summaries covering various threats and infosec industry trends.
SEC-T 2025 streams: Live streams from the SEC-T 2025 security conference, which took place this week, are available on YouTube .
New tool—Inboxfuscation: Cloud security firm Permiso has released Inboxfuscation , a sophisticated Unicode-based obfuscation technique that is able to create malicious inbox rules that evade detection by traditional security monitoring systems.
New tool—Sh3ller: Red teamer Roberto La Piana has open-sourced Sh3ller , a lightweight C2 framework.
New tool—KittyLoader: One of Fortinet's security engineers has released KittyLoader , a highly evasive loader written in C/Assembly.
Acquisition news: F5 plans to acquire CalypsoAI , a company specializing in security AI infrastructure.
Risky Business podcasts
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about the Salesloft Drift incident. It is a great example of the sprawling impact that the breach of a single service provider can have. We expect these single-compromise-large-blast-radius attacks will become the new norm.
In this edition of Between Two Nerds , Two Nerds Tom Uren and The Grugq talk about the trend toward outrageously complicated exploits and what it means for hacking and cyber espionage.
