Risky Bulletin Newsletter
July 18, 2025
Risky Bulletin: New phishing technique bypasses FIDO keys
Written by

News Editor
This newsletter is brought to you by Zero Networks . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
At least one cybercrime group is using a new phishing technique that bypasses FIDO keys and grants attackers access to user accounts.
The new technique has been used in the wild by a threat actor known as PoisonSeed .
Earlier this year , the group was involved in phishing campaigns targeting the cryptocurrency community and designed to steal assets from their crypto-wallets.
Security firm Expel says it believes the group has now developed a new technique that allows it to bypass FIDO keys and access accounts that were previously unreachable.
The technique doesn't exploit any vulnerability in the FIDO protocol, but targets gaps in how online user authentication services are designed.
The technique is hard to explain, but once you understand it, you appreciate its simplicity. I'll just try to simplify it as much as possible in the steps below. Expel also has an infographic that takes you through all the steps.
- Attackers use an email to lure users to a website hosting their phishing kit.
- The phishing kit collects their usernames and passwords.
- Behind the hood, the phishing kit connects to the user's accounts and authenticates with the phished credentials.
- The phishing kit tells the remote website they don't have access to their FIDO security key and that it would like to use a process called " Cross-Device Sign-In ." This process was created to allow users to log into their accounts from a device where they don't have a passkey or security key registered (laptop, desktop, smart TV, etc.) using a device that does (typically a mobile).
- The real login generates a Cross-Device Sign-In QR code that the user needs to scan with their mobile.
- The phishing kit takes this QR code and shows it on the phishing page to the real (phished) user.
- If the victim scans the QR code, they unknowingly allow the attacker access to their account as a "cross-device" user.
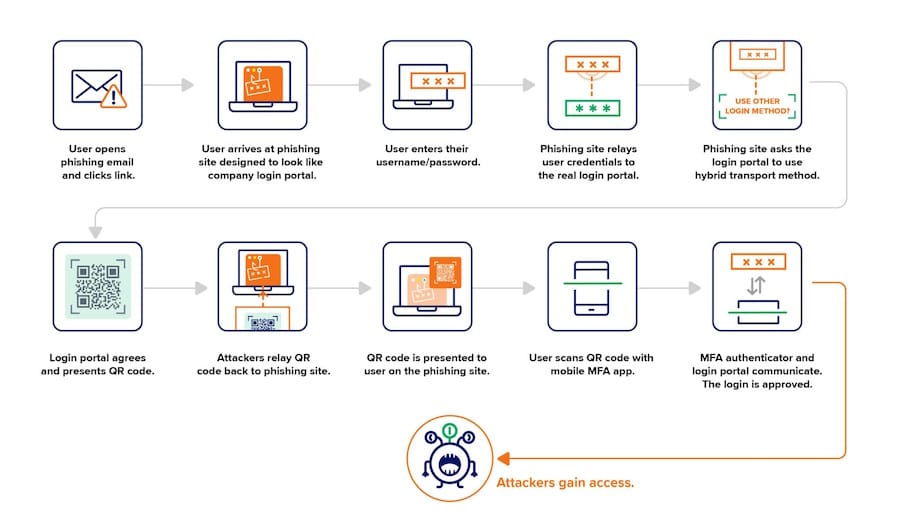
This new phishing technique resembles the structure of Attacker-in-the-Middle phishing kits that have been using reverse proxies to intercept SMS MFA challenges for the past decade.
It also vaguely resembles, or at least is inspired by, a similar technique described by Tobia Righi back in February.
Expel says that while the PoisonSeed is known for crypto thefts, this technique can be easily repurposed for any type of target that was previously thought to be unphishable because of active FIDO keys.
Risky Business Podcasts
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about Huawei's contract to manage storage for Spain's lawful intercept system. News broke this week that Spain had signed a €12 million contract, but it turns out Huawei has been involved in the system since 2004!
Breaches, hacks, and security incidents
South Korea's largest insurer ransomed: South Korea's largest insurance company got hit by ransomware on Monday. The incident has severely disrupted the activity of Seoul Guarantee Insurance. The company has been issuing handwritten loan guarantees to customers all week as it works to restore affected systems. This is the third major South Korean company to experience severe business disruptions this year due to a cyberattack. The country's largest telecom and its largest online bookstore suffered similar disruptions. [ Additional coverage in the Korea Herald ]
UAP ransomware attack: The United Australia Party has fallen victim to a ransomware attack. The incident took place on June 23. The AUP says hackers exfiltrated data from their servers. The data includes personal data, banking records, and employee details. The stolen files also included data from the Trumpets of Patriots party. Both parties were founded by Australian mining magnate Clive Palmer.
UNF loses $400mil from ransomware attack: Grocery distributor United Natural Foods expects to lose up to $400 million in sales this year due to a cyberattack. The company fell victim to a ransomware attack last month and took multiple systems offline for days. The downtime affected its ability to fulfill and distribute customer orders. [ Additional coverage in SecurityWeek ]
Qantas gets an injunction for its hacked data: Australian airline Qantas has obtained an injunction to prevent individuals and organizations from using or publishing data stolen in a recent ransomware attack. The court injunction suggests the company is not willing to pay the ransom and is expecting the hackers to leak the data. No ransomware group has taken credit for the incident so far. [ Additional coverage in CyberDaily ]
UK MoD leak exposed spies and special forces: A data breach that exposed the names of Afghans who helped the UK military during the Afghan war was far larger than previously thought. The leak also exposed the personal data of UK spies and special forces. A small number of senior military officials, MPs, and other government officials were also affected. According to the BBC , the leak originated at the UK Special Forces headquarters. The incident took place in 2023 and was kept secret until this week through a special super-injunction.
Seychelles Commercial Bank confirms hack: Hackers have stolen customer data from the Seychelles Commercial Bank. The organization confirmed the breach in a notification sent to customers last Friday. The bank said no money was stolen in the incident. A hacker is allegedly trying to extort the bank, which has refused to engage in negotiations so far. [ Additional coverage in BankInfoSecurity ]
Air Serbia hacked: Hackers have breached Serbia's national airline, Air Serbia. IT staff have been allegedly working for days to recover systems, although no flights were delayed. [ Additional coverage in Insajder ]
BigONE crypto-heist: Hackers have breached and stolen $27 million worth of crypto-assets from the BigONE cryptocurrency exchange. The funds were stolen from one of the company's hot wallets on Wednesday. BigONE promised to reimburse any affected user.
General tech and privacy
Cloudflare starts blocking piracy sites: Cloudflare has given in to pressure and is now helping the UK government block access to piracy sites within the UK. [ Additional coverage in TorrentFreak ]
EU stalls Twitter investigation: The EU has effectively stopped its investigation into Twitter for breaking the EU DSA, following pressure from the White House. [ Additional coverage in Reuters ]
Roblox to test face age estimation tech: The Roblox video game will test a new technology that can estimate a user's age based on a facial scan.
Steam bans thousands of games: Valve has banned thousands of games from Steam following pressure from payment providers. Most of the games contain adult content. [ Additional coverage in Eurogamer ]
Exchange gets 6 months of ESUs: Microsoft will provide extended security updates for Microsoft Exchange 2016 and 2019 servers for six months past their EOL date of October 14, this year. Security updates will be available until April 14, 2026. The news comes after Microsoft said two weeks ago it was not planning on offering ESUs for these two products.
Government, politics, and policy
EU imposes new sanctions on Russia's propaganda machine: The European Union has imposed new sanctions on Russia's propaganda machine. New sanctions were imposed on the Russian Television and Radio Broadcasting Network and the MD24 TV station in Moldova. Sanctions were also levied against Simeon Boikov, an Australian blogger known as Aussie Cossack. The EU also sanctioned TigerWeb, a Crimea-based company behind an influence operation known as Portal Kombat.
US House hearing on Stuxnet: It's the year of the lord 2025, and the US House Homeland Committee is holding a hearing on the old Stuxnet attacks. Lawmakers hope the operation's lessons might guide new legislation in the field of critical infrastructure. Well, if a Stuxnet meeting is gonna get ICS operators to patch, then have all the Stuxnet meetings you want! [ Additional coverage in CyberScoop ]
FCC to ban Chinese gear in submarine cables: The US FCC wants to ban companies from using Chinese equipment when laying out new submarine cables. [ Additional coverage in The Record ]
Australia will establish a cyber reserves force: The Australian government will establish a cyber reserves branch as part of its defense forces. The new branch will be made up of civilian cybersecurity experts and will focus on defending Australia's critical networks. The new force is expected to launch early next year. [ Additional coverage in DefenceConnect ]
Russia to fine improper web searches: The Russian Duma passed a new law this week that criminalizes searching the internet for what the government considers "extremist content." Russians can be fined up to $65 for searching for prohibited content. This includes search terms related to the LGBTQ movement, terrorist groups, and fascist ideology. Fines will also be imposed for users searching for VPNs and other censorship evasion technologies. [ Additional coverage in Forbes Russia /English coverage in the Washington Post ]
New advances in internet censorship: Punishment not for *saying* the wrong things online, but just for searching for them.
— Sarah McLaughlin (@sarahemclaugh.bsky.social) 2025-07-17T15:29:17.550Z
Sponsor section
In this Risky Bulletin sponsor interview, Zero Networks Field CTO, Chris Boehm, discusses the everyone-gets-an-AI future with Casey Ellis. Zero Networks makes network microsegmentation achievable without simply handing an AI control of the network. Will generative artificial intelligence ever be trusted to make hard access control decisions?
Arrests, cybercrime, and threat intel
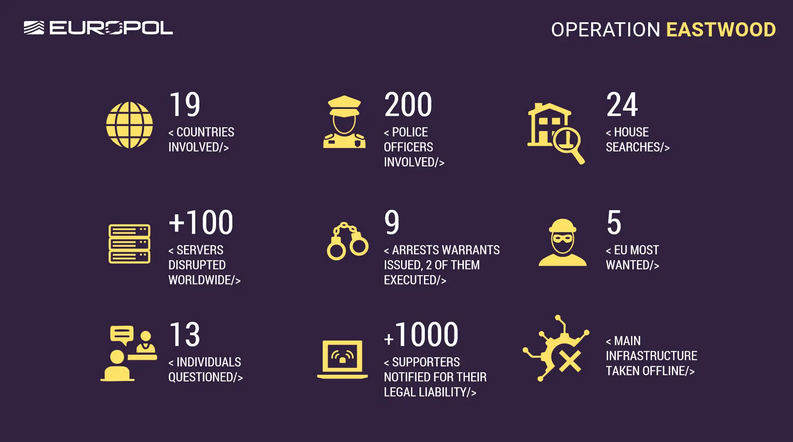
Europol disrupts NoName057(16): An international law enforcement operation has disrupted the activity of pro-Kremlin hacktivist group NoName057(16). Authorities seized over 100 servers, detained two members, and issued arrests for seven other individuals. The NoName057 launched after Russia's invasion of Ukraine and carried out thousands of DDoS attacks against Western countries. It used Telegram channels and a gamified experience to recruit new individuals to its cause. Authorities say they've identified more than 1,000 supporters and notified them of possible legal repercussions. [ Press releases from Europol , Dutch police , Swedish police , Swiss police , German police ]
whoa r u telling me criminals had an association with the state [shocked pikachu]
— Selena Larson (@selenalarson.bsky.social) 2025-07-17T13:56:40.371Z
Ryuk member extradited to US: The US has extradited an Armenian national from Ukraine for his role in Ryuk ransomware attacks. Karen Serobovich Vardanyan was part of a group that extorted over $15 million from victims. The group also included another Armenian and two Ukrainians. The Armenian was arrested in France and is still subject to extradition proceedings.
Scattered Spider members released on bail: A British court has released four members of the Scattered Spider group on bail. The four were arrested last week. They've been charged with hacking UK retailers Marks & Spencer, Co-op, and Harrods. [ Additional coverage in Nation Cymru ] [ h/t Kevin Beaumont ]
Cambodia detains 1k scammers: Cambodian authorities have arrested more than 1,000 suspects linked to online scams and cybercrime operations. Police raids took place across six provinces between Monday and Wednesday. Prime Minister Hun Manet ordered government bodies to crack down on cybercrime operations following pressure from international partners. According to the Camboja News , major scam compounds connected to political elites remain untouched.
CAMBODIA: English translation of PM order that was 'leaked' before the wave of scam compound raids that have taken place in recent days. 1/2 www.khmertimeskh.com/501718152/ro...
— Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2025-07-17T12:19:38.342Z
Thai scam center raids: Thai officials have raided properties connected to a Cambodian senator and business tycoon in connection with a local network of cyber scam call centers. [ Additional coverage in the Bangkok Post ]
Belgium uses bread bags to warn about cybercrime: Belgian authorities are using messages printed on bread bags to warn the elderly about cybercrime threats. Police have distributed more than 10,000 bags to bakers across the Pajottenland region as part of a recent experiment. The bags contain tips on dealing with scammers who request PINs and passwords. [ Additional coverage in VRT ]
Google sues BADBOX botnet: Google has filed a lawsuit against the operators of the BADBOX botnet. The group is known for infecting Android-based smart TVs with malware that engages in ad fraud. The botnet is believed to have infected over 10 million devices.
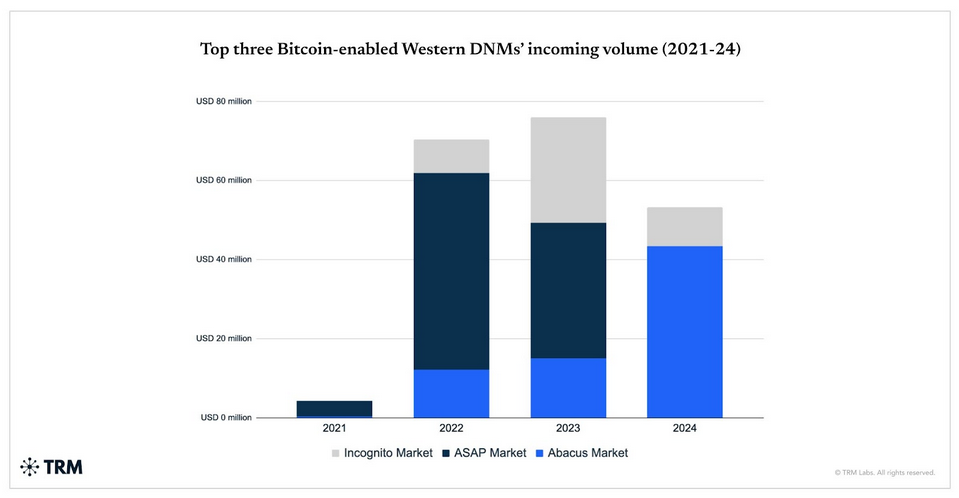
Abacus Market exit scam: According to TRM Labs , the Abacus dark web market appears to have exit-scammed. Abacus was one of the largest marketplaces on the dark web before its disappearance.
Surveillance vendor deploys new SS7 exploit: A mobile surveillance vendor is exploiting a vulnerability in the SS7 telecommunications protocol. The exploit allows the attacker to bypass SS7 security defenses and trick mobile operators into disclosing a subscriber's location. ENEA has seen attacks dating back to the last quarter of 2024. [ h/t Cathal McDaid ]
New Massistant phone forensics tool: Chinese authorities are using a new forensics toolkit to extract data from seized Android phones. The new Massistant tool is allegedly used at border checkpoints and by local police forces. It can extract geolocation data, images, SMS messages, contacts, and data from third-party messaging apps. According to mobile security firm Lookout , Massistant appears to be the successor of a previous tool used by authorities named MFSocket.
Fortinet shells in the wild: Security researchers have found webshells on almost 80 Fortinet FortiWeb firewalls. The Shadowserver Foundation believes the webshells were installed after hackers exploited a recently patched vulnerability ( CVE-2025-25257 ). The bug is a pre-auth SQL injection in the firewall's web panel. Fortinet has not yet confirmed in-the-wild exploitation.
UNC6148 targets SonicWall SMAs: A hacking group linked to ransomware attacks is targeting SonicWall SMA appliances again. Google says the group is using credentials and one-time password seeds stolen during previous intrusions to gain access even to fully-patched devices. The group deploys a new backdoor and user-mode rootkit named OVERSTEP to modify the boot process and hide its components. Google tracks the attackers as UNC6148 . They were previously linked to attacks with the Abyss ransomware.
cloud.google.com/blog/topics/... An interesting ongoing deployment of a backdoor for older SonicWall appliances documented by Mandiant. According to the report it is assumed to be linked to criminal activities, not spying, which kind of rare for network device backdooring.
— Goupil (@furaxfox.bsky.social) 2025-07-18T00:07:40.087Z
SilverFox ops: The DomainTools analyzes infrastructure used by the SilverFox threat actor to target users in China with Windows malware. This is part three of a deeper analysis of Chinese malware ops.
LARVA-208 switches to Web3 devs: A known ransomware IAB and affiliate, specialized in phishing operations and known as LARVA-208 and EncryptHub , is now targeting Web3 crypto devs.
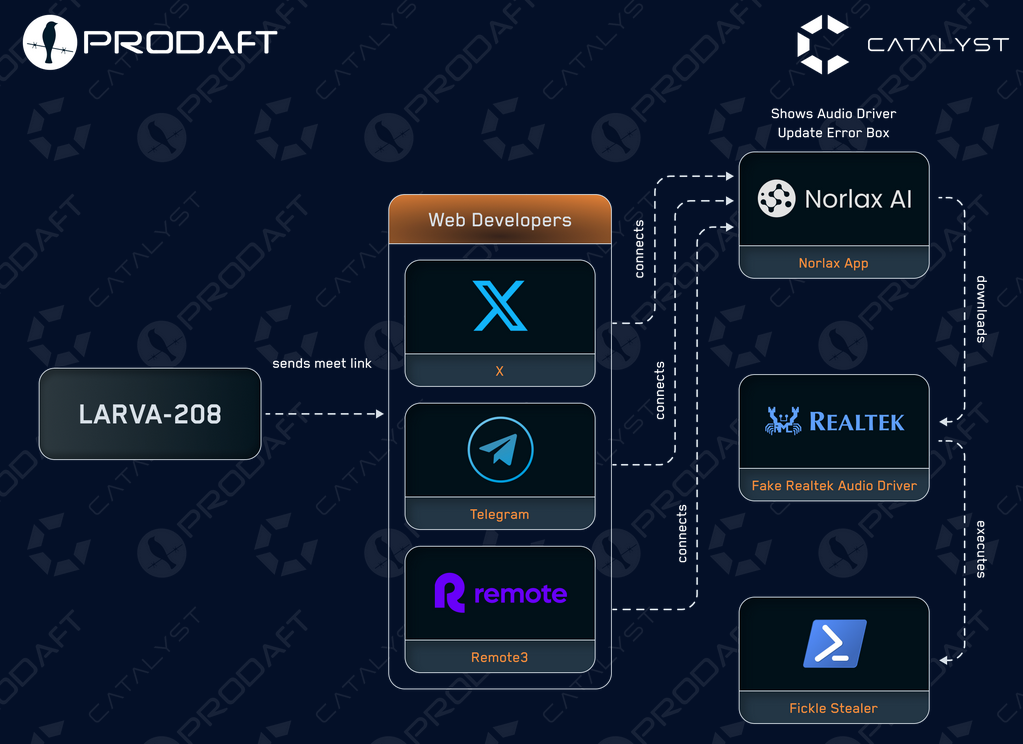
Octo Tempest: Microsoft has published a blog post with new TTPs from Octo Tempest (Scattered Spider) attacks.
Baqiyatlock313 ransomware: A pro-Palestine hacktivist group named Liwaa Mohammad has launched its own ransomware strain named Baqiyatlock313 .
Maison Receipts service: Group-IB profiles Maison Receipts , a service for generating fake receipts for major retail brands. The service is used by groups that sell counterfeit products or online scammers who run fake shopping portals.
New protestware spreads on npm: Anti-Russian protestware has been spotted in 28 npm packages. The libraries contain hidden functionality that activates for Russian-language users visiting Russian domains in a browser. The code breaks the websites or prevents them from loading. According to Socket Security , some libraries disclose their behavior while others do not.
Cryptojacking is still alive: Security firm c/side has spotted new websites engaged in cryptojacking—in-browser cryptomining. Since cryptojacking is banned in web browsers, this one tried a stealthier approach via WebAssembly.
PQC support in SSH servers: According to a new Forescout report , only 6% of over 186 million SSH servers today use post-quantum cryptographic algorithms.
More MaaS platforms used to target Ukraine: Cisco Talos warns that more MaaS platforms are now being used to target Ukrainian organizations. Initial abuse included SmokeLoader and RomCom, but this has now expanded to Amadey and Emmenhtal.
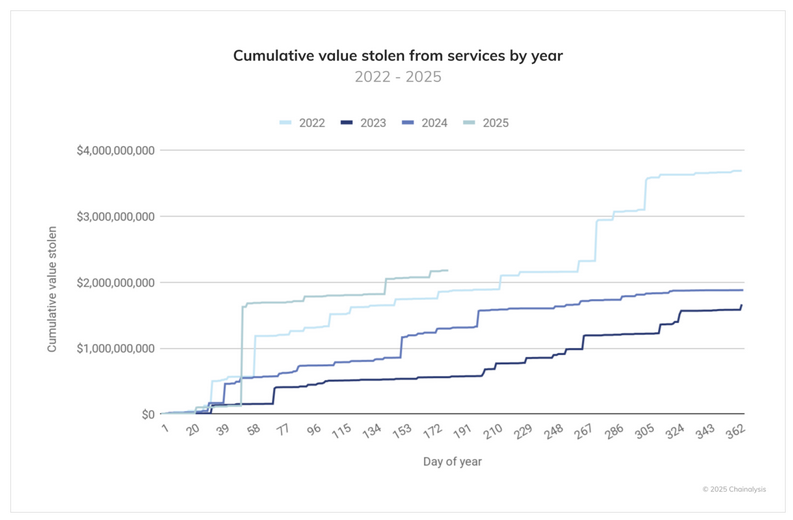
Crypto-thefts this year reach $2.17b: Hackers and scammers have stolen over $2.17 billion in crypto assets in the first half of this year. The sum is already larger than last year's total, but most of it is just one hack—the DPRK's $1.5 billion ByBit hack.
Malware technical reports
Katz Stealer: SentinelOne has published a profile and a technical breakdown of Katz Stealer , an infostealer offered through a MaaS model advertised on hacking forums, Discord, and Telegram for prices ranging from $50 to $360/month.
Linuxsys cryptominer: Cybercriminals are exploiting an old 2021 vulnerability to break into Apache HTTP servers and deploy a cryptominer known as Linuxsys .
New Matanbuchus 3.0: Threat actors are using unsolicited Microsoft Teams calls to trick corporate employees into infecting themselves with malware. The attackers pose as tech support staff and guide employees through the process. The final payload is version 3.0 of the Matanbuchus malware, which launched earlier this month.
Kawa ransomware: Trustwave has published a technical analysis of Kawa , a new ransomware operation that launched at the end of June. The ransomware uses a leak site similar to Akira and a ransom note similar to Qilin, but no other tangible connections have been spotted.
Sponsor section
Zero Networks is offering a comprehensive guide that highlights the growing importance of advanced microsegmentation in a security landscape.

APTs, cyber-espionage, and info-ops
Rainbow Hyena: An unidentified hacktivist group, which BI.ZONE calls Rainbow Hyena , is targeting Russian healthcare and IT organizations with phishing campaigns.
UAC-0001: CERT-UA has spotted new UAC-0001 (APT28) activity. This campaign uses spear-phishing to distribute a version of the LAMEHUG malware.
Russia's info-ops in the occupied territories: The Russian government has flooded social media communities in occupied Ukrainian territories. The Atlantic Council has spotted over 3,600 automated accounts that post pro-Russian comments on local Telegram channels. The messages are designed to encourage gratitude and loyalty to Russia and to blame Ukraine's government for the war. The same network was also spotted spamming local Telegram communities inside Russia.
"In the context of wide-ranging attempts to control the information environment, inauthentic comments, including those published by automated means, serve as a means to manipulate the perception of public opinion within the occupied territories, an aspect of computational propaganda referred to as ' manufacturing consensus ' by Samuel Woolley. A high volume of comments expressing a certain viewpoint can create the impression that it represents the majority opinion in a community, regardless of whether that is actually the case."
Operation Overload info-ops: ISD Global says social media networks such as BlueSky, TikTok, and Twitter have heavily cracked down on Operation Overload , a Russian influence operation also known as Matryoshka and Storm-1679 that currently targets Moldova.
"X removed 73 percent of sampled posts, compared to just 20 percent in the first quarter of 2025. On TikTok and Bluesky, removal rates were higher than 90 percent. This could reflect platforms' increasing awareness of the operation or that its use of bots and other manipulation tactics is brazen enough to trigger automated moderation systems."
GhostContainer backdoor: Kaspersky has discovered GhostContainer , a backdoor planted on Microsoft Exchange servers by a suspected APT operation.
"Based on all the analysis conducted, it is evident that attackers are highly skilled in exploiting Exchange systems and leveraging various open-source projects related to infiltrating IIS and Exchange systems. They possess an in-depth understanding of how Exchange web services operate and show remarkable expertise in assembling and extending publicly available code to create and enhance sophisticated espionage tools."
UNG0002 campaign across Asia: Seqrite has spotted a sprawling APT campaign targeting multiple Asian jurisdictions, including China, Hong Kong, and Pakistan.
Three Chinese groups target Taiwan: Multiple suspected Chinese espionage groups have been seen targeting Taiwan's semiconductor industry, according to a new Proofpoint report . The groups have been identified as UNK_DropPitch, UNK_SparkyCarp, and UNK_FistBump.
New from the one and only pun-king @mkyo.bsky.social on the increased and ongoing Chinese targeting of semiconductor-related organisations in Taiwan. Edge device exploitation may be the TTP of the moment, but Chinese groups still go phishing when the chips are down www.proofpoint.com/us/blog/thre...
— Saher (@saffronsec.bsky.social) 2025-07-17T08:43:59.173Z
Vulnerabilities, security research, and bug bounty
Chrome zero-day: Google has released a security update to patch an actively exploited Chrome zero-day. Tracked as CVE-2025-6558, the vulnerability is a sandbox escape via an exploit in Chrome's WebGL and GPU components. It was discovered by Google's own security team and appears to be part of an exploit chain, together with another zero-day patched earlier this month. It is the fifth Chrome zero-day patched this year.
CitrixBleed 2 exploitation: GreyNouse says it saw attacks exploiting the CitrixBleed 2 vulnerability two weeks before a public PoC was published on July 4.
TeleMessage exploitation: The same GreyNoise has also spotted mass reconnaissance and exploitation activity for CVE-2025-48927, a vulnerability in the Signal backup tool TeleMessage SGNL.
OCI Code Editor RCE: Tenable's research team has discovered a remote code execution vulnerability in the Oracle Cloud Infrastructure Code Editor that can be exploited to hijack a customer's Cloud Shell environment. This is now patched.
Golden dMSA attack: Semperis researchers have found a design flaw in the Windows Server 2025 delegated Managed Service Accounts (dMSAs). The flaw, codenamed Golden dMSA , simplifies the brute-force generation of passwords for all dMSA users.
"Semperis researchers rate this vulnerability as MODERATE because to exploit it, attackers must possess a KDS root key available only to only the most privileged accounts: root Domain Admins, Enterprise Admins, and SYSTEM. However, this attack can be high impact, enabling cross-domain lateral movement and persistent access to all managed service accounts and their resources indefinitely."
Vulnerable Bluebird preinstalled apps: Poland's CERT says three apps preinstalled on Bluebird smartphones contain vulnerabilities that enable local attacks
ATEN KVM switch vulnerabilities: Russian security firm Positive Technologies has found three vulnerabilities in ATEN KVM switches. The devices allow operators to control multiple networking devices from the ATEN device. The vulnerabilities allow attackers to take control of all connected devices.
NVIDIAScape vulnerability: Google's Wiz team has discovered a container escape vulnerability in the NVIDIA Container Toolkit (NCT). The toolkit is a sandboxing technology for NVIDIA GPUs on Linux and powers many AI services across cloud platforms. According to Wiz, the NVIDIAScape vulnerability allows a malicious container to bypass isolation and gain root access to the host machine.
Cisco security updates: Cisco has released four security advisories for various products.
BIND security updates: ISC has released two security advisories for the BIND DNS resolver. [ h/t cR0w ]
Oracle CPU: The quarterly Oracle security updates are out, with patches for 309 vulnerabilities. Qualys and Tenable have breakdowns of the fixes.
Infosec industry
Acquisition news: Asset management company Lansweeper has acquired asset discovery platform Redjack.
New tool—WAF Detector: Cloud security engineer Ammar Alim has released WAF Detector , a tool for detecting and testing Web Application Firewalls (WAFs) and Content Delivery Networks (CDNs).
Threat/trend reports: Chainalysis , Contrast Security , Elliptic , ENISA , Forescout , ISC2 , Knostic , Pew Research , and SpecOps have recently published reports and summaries covering various infosec trends and industry threats.

Risky Business podcasts
In this edition of Between Two Nerds , Tom Uren and The Grugq examine whether US cyber operations are too stealthy. Could they get more bang for the buck if they adopted a devil-may-care attitude to getting busted?
