Risky Bulletin Newsletter
September 01, 2025
Risky Bulletin: Noem fires FEMA IT team over alleged cybersecurity failures
Written by

News Editor
This newsletter is brought to you by Push Security . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
DHS head Kristi Noem has fired 24 employees of the FEMA IT department, citing an alleged data breach and a string of cybersecurity failures.
The firings included FEMA CIO Charles Armstrong and FEMA CISO Gregory Edwards.
Noem claims the DHS discovered a breach of FEMA systems and stopped it before any data was stolen.
The DHS says the alleged breach was discovered after Noem ordered a review of FEMA IT operations.
The audit also found that FEMA did not deploy multi-factor authentication, used prohibited legacy protocols, failed to patch known and critical vulnerabilities, and did not have adequate operational visibility into its networks.
In a somewhat unhinged press release , the DHS and Noem claim the fired employees were " entrenched bureaucrats " and " deep-state individuals " who " resisted any efforts to fix the problem ," downplayed the issues, and " were more interested in covering up their failures ."
FEMA insiders who spoke to CNN shortly after the firings last Friday painted a totally different picture and described the ousted IT team and its leaders as " extremely competent " and " highly respected ."
At this point in time, and taking into account the declining credibility of any statements coming out of the Trump administration, it is unclear if a breach even took place or if Noem and the DHS are trying to make up reasons to fire FEMA staff to bring in their loyal lackeys into the agency instead.
The White House has been grasping at straws for months to find reasons to fire FEMA staff and leadership.
It previously administered lie detector tests to FEMA top officials and fired the FEMA CFO after she made payments authorized by DOGE a day before.
According to multiple reports , the Trump administration is intent on disbanding the agency altogether, or at least downsizing it to minuscule levels and leaving US states to handle their own natural disasters .
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Salesloft hack larger than initially thought: A security breach at sales automation platform Salesloft is larger than initially thought. The hackers who pivoted from Salesloft's network to Salesforce accounts also pivoted to Google Workspace , Slack, and Pardot integrations. The breach took place last month when hackers stole OAuth tokens that integrated its Drift AI agent with other platforms.
Major Update: We now believe this incident impacts other Salesloft Drift integrations, not just Salesforce. We’re advising Salesloft Drift customers to treat any and all authentication tokens stored in or connected to the Drift platform as potentially compromised.
— John Hultquist (@hultquist.bsky.social) 2025-08-29T14:43:25.973Z
Dutch cancer testing program doubles breach: A Dutch cancer-testing program has doubled the number of impacted patients from an initial 485,000 to over 941,000.
North Korea blamed for WOO X hack: North Korean state-sponsored hackers are behind the recent hack of cryptocurrency exchange WOO X. The company has blamed the recent hack of $14 million of crypto assets on the TraderTraitor group. The hackers allegedly social-engineered an employee to help debug an open-source project that later infected their work computer with a backdoor.
Austrian ministry hacked: Hackers have gained access to the email server of the Austrian Interior Ministry. The hackers allegedly stole emails from around 100 employee accounts. Officials described the intrusion as "targeted and professional." [ Additional coverage in Der Standard ]
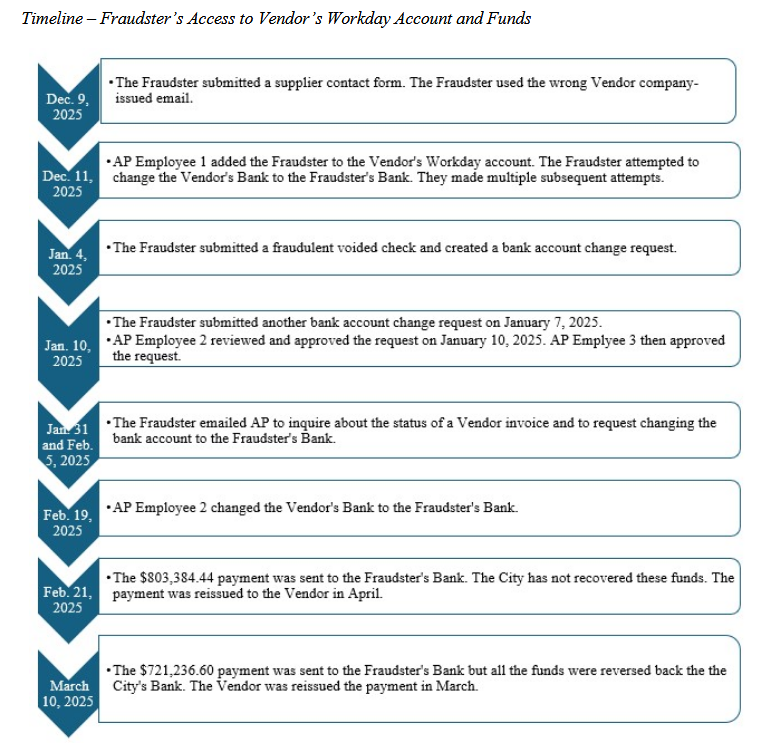
Baltimore loses $1.5mil to scammer: The city of Baltimore has lost $1.5 million to a scammer at the start of the year. The attacker spoofed a vendor and tricked the city into making two payments into the wrong bank account. The city managed to recover the second payment, worth $700,000, after catching on to the scheme. [ Additional coverage in CBS News /City of Baltimore Office of the Inspector General report/ PDF ]
General tech and privacy
Meta embraces AI pr0n: Meta's AI chatbots impersonated celebrities and engaged in flirty chats with users. The bots impersonated the likes of Taylor Swift, Scarlett Johansson, and Selena Gomez, all without their permission. According to Reuters , the bots also generated inappropriate nude images, including of underage child stars. A previous report found that Meta's AI chatbots engaged in romantic conversations with children. Attorneys General from 44 US states sent letters to 11 AI chatbot and social media companies last week, warning of investigations if this type of behavior continued.
"Reuters also found that Meta had allowed users to create publicly available chatbots of child celebrities, including Walker Scobell, a 16-year-old film star. Asked for a picture of the teen actor at the beach, the bot produced a lifelike shirtless image. 'Pretty cute, huh?' the avatar wrote beneath the picture."
KylinOS 11 released: Kylin Software has released KylinOS 11 , the latest version of China's so-called "national OS." Security and AI features are the main highlights of this release.
Vivaldi disavows AI: The Vivaldi browser team has promised not to deploy AI and LLMs all over its codebase and keep the browsing experience as private as possible.
Big tech problem: Amnesty International has called on world governments to check the " uncontrolled power " of big tech firms. Might be too late, if you ask me.
Hacker finds Tesla's lost data: A white-hat hacker played a crucial role in finding data from a Tesla crash that the carmaker claimed was lost. According to the Washington Post , the researcher's work helped plaintiffs secure a $243 million verdict against the company. Plaintiffs sued the company after a Tesla car on autopilot plowed into a couple in Florida in 2019, killing a young woman.
This story is batshit and makes it pretty clear without outright saying it that Tesla deliberately lied to hide data showing its autopilot drove a car into a couple of people www.washingtonpost.com/technology/2...
— River_Tam (@rivertam.bsky.social) 2025-08-29T11:22:06.407Z
Government, politics, and policy
CFAA limits ruling: A US Court of Appeals has ruled that the Computer Fraud Abuse Act (CFAA) cannot be used to prosecute employees for work-related infractions. US debt collection firm National Recovery Agency Group claimed that two employees broke the CFAA when one shared a password with another employee while she was sick. The US Court of Appeals for the Third Circuit ruled that the CFAA can only be used when hacking and the theft of trade secrets are involved. [ Additional coverage in Law.com ]
Live facial recognition in Germany: Hesse will become the first German state to deploy AI-based live facial recognition to help with policing activities.
Israel hacked bodyguards of Iranian officials: The Israeli military launched missile strikes against Iranian officials by hacking and tracking the phones of their bodyguards. The strike hit and failed to destroy a bunker where Iranian officials met during a military conflict between the two countries in June. According to the New York Times , Israel had been tracking the "careless use of mobile phones" by Iranian bodyguards for years prior to the attack.
Russia may ban cybersecurity information: A proposed bill by Russia's Ministry of Finance wants to ban the dissemination of information that can be used to carry out cyberattacks. This is basically any type of cybersecurity research and educational material. This has all of Russia's infosec space panicked. [ Additional coverage in Kommersant ]
Spain cancels Huawei contract: The Spanish government has canceled a controversial contract that would have deployed Huawei equipment on various government internet networks. [ Additional coverage in El Pais ]
Sponsor section
In this sponsored interview Casey Ellis chats with Push Security co-founder Jacques Louw. Push’s browser plugin gives a unique level of visibility into how users interact with the web and the attacks they face. Jacques talks through what they’re seeing, and their recently published taxonomy of phishing attacks. It’s on Github for everyone to contribute to!
Arrests, cybercrime, and threat intel
Another SMS blaster detained in Vietnam: Vietnamese authorities arrested a foreign national for sending fraudulent SMS messages. The suspect drove around Ho Chi Minh City with two SMS blasters in the back of their car. The devices sent SMS messages impersonating Vietcombank and Vietnam Post. This was the third SMS blaster incident recorded in the same city this past month. [ Additional coverage in CommsRisk ]

Safetrac WFH investigation: Australian authorities are investigating compliance company Safetrac for breaching the state of Victoria's surveillance laws. According to the Australian Financial Review , Safetrac used company laptops to record their screens and audio conversations without their consent. The surveillance targeted employees working from home this year. Safetrac CEO Deborah Coram admitted to the practice in recent legal documents.
Ukrainian cluster behind cyber attacks: Three Ukrainian and one Seychelles network are behind a wave of password spraying attacks against SSL VPN and RDP devices.
BABYLONGROUP: The Chollima Group published a report on BABYLONGROUP , a cluster of North Korean remote IT workers that has ties to a cyber-espionage division tracked as Moonstone Sleet.
Gambler Panel: KrebsOnSecurity has a profile on Gambler Panel , a service to redirect legitimate traffic to scam gambling sites that lure users with free credits but steal their crypto.
C-suite phishing campaign: The Stripe OLT team has spotted a large-scale malvertising campaign targeting C-suite execs with malicious ads that take them to phishing pages.
Mastodon phishing campaign: There's a new phishing campaign targeting Fediverse users, asking them to verify Mastodon profiles on sites that capture their credentials.
Cisco ASA reconnaissance campaign: A coordinated reconnaissance campaign is targeting Cisco ASA firewalls. The scanning wave peaked last Thursday, August 28, when more than 200,000 probes hit honeypots. The scans looked for an assortment of new and old ASA bugs, looking for an initial foothold. Most of the activity originated from three ASNs.
Cisco ASA honeypot blew up Aug 28: – 200k probes in 20h – 3 ASNs only: NYBULA / CHEAPY-HOST / GCS – Each IP ~10,102 reqs (scripted) likely prepping for CVE-2025-20182/20134 (DoS), disclosure bugs, or legacy RCEs. Report: medium.com/@Nadsec/hone... OTX Pulses: otx.alienvault.com/user/conrat
— Nad (@nadsec.online) 2025-08-29T17:01:27.783Z
Malware technical reports
MetaStealer: Huntress looks at a campaign using a fake AnyDesk installer that spreads and deploys the MetaStealer malware .
PolarEdge botnet: Censys has published a report on PolarEdge , a recent IoT botnet that has slowly grown in size and is likely used as an ORB.
"Following a specific pivot, we uncovered a connect-back proxy management system that was detected running on a host associated with the PolarEdge compromises back in 2024, and is currently running on over 2,400 hosts. This system appears to be a well-designed server that may be one of the many tools used for managing the PolarEdge botnet."
NightSpire ransomware: AhnLab has published a report on the NightSpire ransomware , a double-extortion group that launched in March.
Interlock ransomware: The same AhnLab team looked at the Interlock ransomware .
AI Waifu RAT: Security researcher Ryingo has published an analysis of the AI Waifu RAT , a RAT disguised in malicious LLMs distributed in underground role-playing communities.
TinkyWinkey Keylogger: CyFirma has published a technical analysis of the new TinkyWinkey Keylogger , first spotted in the wild in June.
"Its ability to capture all keystrokes, including special keys and multi-language input, alongside detailed system metrics such as CPU, memory, OS version, and network identifiers, underscores the sophistication of modern malware targeting endpoint systems."
TamperedChef infostealer: Truesec looks at TamperedChef , the infostealer dropped on systems that installed a backdoored version of the AppSuite PDF Editor, first spotted by G DATA last week.
Sponsor section
In this wholly sponsored Soap Box edition of the show, Patrick Gray chats with Adam Bateman and Luke Jennings from Push Security. Push has built an identity security platform that collects identity information and events from your users' browsers. It can detect phish kits and shut down phishing attempts, protect SSO credentials, and find shadow/personal accounts that a user has spun up.
APTs, cyber-espionage, and info-ops
Homeland Justice campaign: An Iranian espionage group known as Homeland Justice is behind a spear-phishing campaign that impersonates the Omani Ministry of Foreign Affairs.
Amazon disrupts APT29: The Amazon security team has disrupted a cyber-espionage operation linked to Russia's SVR intelligence service. The campaign hijacked traffic from hacked websites, a tactic known as watering hole attacks. Users were redirected to Microsoft device-code phishing pages. Amazon took down servers and domains, and also worked with Cloudflare to prevent the APT29 group from moving to new servers. This is the second time AWS has disrupted APT29 since last October .
APT-C-53 (Gamaredon): Qihoo 360 has spotted new tooling and TTPs from Russian cyber-espionage group APT-C-53 (Gamaredon).
Lazarus (APT-Q-1): Chinese security firm QiAnXin looks at the Lazarus Group's recent use of ClickFix themes to trick targets into infecting themselves with malware, including a variation that targeted macOS users.
Operation HanKook Phantom: Seqrite researchers have spotted a new APT37 campaign targeting South Korea's intelligence and government sectors.
AI fuels new propaganda era: New research looks at how small-scale LLMs that can run on commodity hardware are fueling a new rise in AI propaganda factories. Although these new AI-driven personas can be detected, the study also asks if online platforms can adapt fast enough, as the political will to fight online dis/misinformation is waning.
Chinese info-op: Graphika has found a network of fake news sites and social media accounts laundering news from Chinese state media on Facebook, Instagram, Mastodon, Threads, and X.
"The assets almost certainly used AI tools to translate and summarize articles from CGTN, likely in an attempt to disguise the content's origin. The network assets disseminated primarily pro-China, anti-West content in English, French, Spanish, and Vietnamese."
New Matryoshka campaign: There's a new Matryoshka info-op campaign targeting Moldova's pro-EU President Maia Sandu with AI-manipulated videos.
Vulnerabilities, security research, and bug bounty
Netskope LPE: AmberWolf researchers have found an LPE in the Windows client for Netskope.
Sitecore CMS RCE: WatchTowr Labs has found three new vulnerabilities in the Sitecore CMS, including a cache poisoning one and an RCE.
Passwordstate auth bypass: Enterprise password management platform Passwordstate fixed an authentication bypass in its platform's Emergency Access feature.
Apple declines to patch Safari bug: Apple has declined to patch an address bar spoofing bug in Safari. The bug exploits custom mouse cursors to overlay a fake URL in the address bar.
WhatsApp patches zero-day: Meta has patched a zero-day vulnerability in the WhatsApp instant messenger. The zero-day (CVE-2025-55177) was part of an exploit chain used in the wild to hack Apple devices. Apple patched its side of the exploit (CVE-2025-43300) in a security update released on August 20. According to Amnesty International , the two zero-days have been used in "an advanced spyware campaign" over the past 90 days.
Infosec industry
Threat/trend reports: Incogni , Positive Technologies , and Yandex Cloud have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about proposed legislation that would allow the President to license private sector hackers to go after cybercrime groups. The bill won't pass, but letting hackers loose on industrial-scale scam farms actually makes sense.
In this edition of Between Two Nerds , Tom Uren and The Grugq talk about how the teenage hacking groups Scattered Spider, Lapsus$, and ShinyHunters are collaborating.
