Risky Bulletin Newsletter
November 03, 2025
Risky Bulletin: Norway skittish of its Chinese electric buses
Written by

News Editor
This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Oslo's public transportation agency conducted a security audit of its electric buses and, to nobody's surprise, found that its Chinese models could be remotely disabled by their manufacturer.
According to a report from local newspaper Aftenposten, the agency, Ruter, tested and took two electric bus models inside a Faraday cage room.
Ruter found that electric buses from Chinese company Yutong could be remotely disabled via remote control capabilities found in the bus software, diagnostics module, and battery and power control systems.
Similar features were not found in electric buses bought from Dutch company VDL.
The issue has prompted Ruter to take action and disable internet connectivity by removing SIM cards from the onboard modems.
The agency runs over 300 Yutong electric buses in Oslo, and 550 other Yutong buses are deployed across other cities in Norway.
In an interview with publish broadcaster NRK, Ståle Ulriksen, a national security expert from the Norwegian Naval Academy, showed his dismay at the naivety of Norwegian politicians.
"I cannot comprehend and understand why politicians refuse to listen to the security authorities' repeated, annual warnings," he said.
The exact same issue is not isolated to just electric buses. Similar remote control features have been found in port cranes deployed in the US, Chinese smart cars, solar panels, and about anything else that has a Chinese chip in it.
There is also the valid point that many of those remote control/surveillance systems are inside those products for legitimate purposes, such as debugging and remote support.
Why send a support team across the world and pay for expensive travel when you can just SSH your way into a device, restart some processes, and move on with your day?

Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
ACL fined for breach: Australia's privacy watchdog has fined the Australian Clinical Labs AUD$5.8 million (USD$3.8 million) for a 2022 security breach of its Medlab Pathology business that exposed the personal details of 223,000 individuals. [h/t Brett Sanders]
Garden crypto-heist: Hackers have stolen $10.8 million worth of crypto assets from the Garden DeFi platform. The hack took place last Friday. The company has offered the attacker a 10% bug bounty to return the stolen assets. According to a known blockchain investigator, more than a quarter of Garden's activity has been linked to criminal activity, such as laundering funds hacked from other platforms. [Additional coverage in Yahoo Finance]
UK Legal Aid hack: UK's Legal Aid agency says a hack it disclosed back in May was traced back to an intrusion into its IT network on April 23. The investigation is still ongoing. The breach was initially linked to a group tracked as ShinyHunters. [Additional coverage in Public Technology] [h/t DataBreaches.net]
Veradigm breach blast radius: According to an analysis from PogoWasRight at DataBreaches.net, more than a dozen companies may be indirectly affected by a breach at Veradigm, a provider of IT solutions for the healthcare sector.
CEC DDoS attacks: Cloudflare has published an IR report on the DDoS attacks that hit Moldova's Central Election Commission during the country's Parliament election on September 28.
"These attack patterns mirrored those against the election authority, suggesting a coordinated effort to disrupt both official election processes and the public information channels voters rely on."
Iranian hackers leak Israeli defense contractor data: Iranian hackers have leaked the employee names of a major Israeli defense contractor. The Cyber Toufan group claims it breached Maya Defense in early 2024. It released employee names, photos, internal documents, and CCTV footage from Maya factories. Maya Defense makes drones, missiles, and launcher systems for the Israeli government. [Additional coverage in the Tasnim News Agency]
General tech and privacy
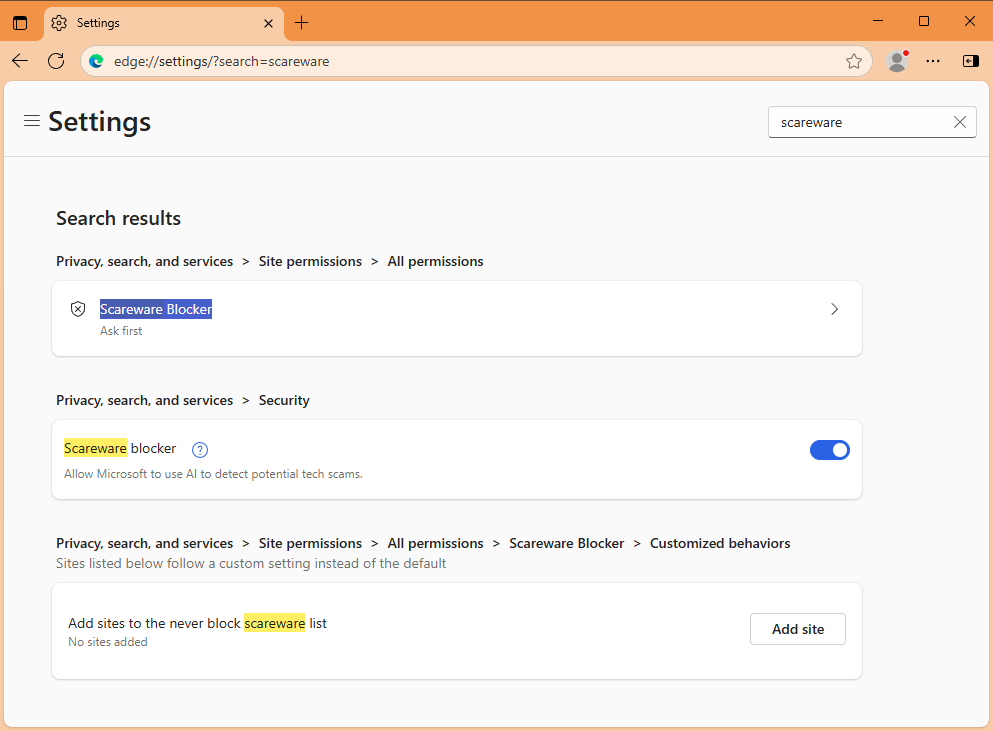
Edge gets a scareware blocker: Microsoft has added a new security feature in its Edge web browser. The new Scareware Blocker uses a local computer vision model to spot and block fullscreen popups and phony warnings. The feature was added in Edge version 142, released last week. It will only run on systems with more than 2 GB of RAM and four CPU cores.
Chrome 142: Google has released version 142 of its Chrome browser. See here for security patches and webdev-related changes. The biggest change in this release is a new security feature to block local network attacks. This version also runs a second test (origin trial) for the new Device Bound Session Credentials security feature. Chrome will also disable all force-installed extensions that violate Chrome Web Store terms of service, even if they don't have a malware categorization. Chrome 142 also uses an LLM to detect scareware and scams, similar to what Edge also added.
arXiv updates moderation after wave of AI slop: The arXiv portal has updated its moderation for the computer science category and will stop accepting papers that have not gone through a peer review first. The portal blamed the huge influx of AI slop.
BlueSky will test a dislike button: Social media network BlueSky will test a dislike button. Dislikes will be private and used to rank replies in threads. Information gathered from dislikes will not be used to downrank accounts.
OpenAI Aardvark: OpenAI has released Aardvark, an AI agent for analyzing code repos to find and fix security flaws. Currently in private beta.
Aardvark is a labor of love and mission for the whole team. We are super excited to bring it to you. Sign up for the beta immediately!!! openai.com/index/introd...
— Dave Aitel (@daveaitel.bsky.social) 2025-10-30T18:14:37.213Z
Government, politics, and policy
CyberCorps program freeze: A US government program that trains cybersecurity experts will likely saddle participants with giant loans. The US CyberCorps program provides free cybersecurity training as long as students find federal jobs and internships. Participants say the government has rescinded job offers and frozen new hires. Students will likely have to pay from their own pocket or be saddled with a giant six-figure loan unless the US government steps in and honors its part of the deal. [Additional coverage in CyberScoop]
CFPB ends Meta investigation: Under the new Trump leadership, the US Consumer Financial Protection Bureau has ended its investigation of Meta's use of user financial data for ad targeting. Expect more tech and monopoly-friendly decisions from the CFPB going forward. After all, this is the same agency that gave the go-ahead to data brokers to sell the data of Americans just a few months ago. [Additional coverage in The Record]
Italy gets age checks: Adult sites will have to implement age checks for Italian users starting on November 12. [Additional coverage in LaPresse]
Germany to pay for its stupidity (again): The German government is considering using public funds to pay its largest telecom operator, Deutsche Telekom, to replace Huawei gear. The costs would exceed €2 billion. Unlike other NATO countries, Germany ignored US warnings and allowed local telcos to deploy Huawei equipment. Most NATO allies have blocked Huawei from their telecommunications networks. [Additional coverage in Bloomberg]
France wants to raise tech tax: The French Parliament wants to raise its digital services tax to 6% from 3%. The government is opposing the plan, fearing another Trump tantrum and possible tariffs. [Additional coverage in Politico]
Cambodia and Thailand to collaborate on scam crimes: Cambodian and Thai officials have signed a partnership to collaborate on scam compound operators. [h/t CyberScamMonitor]
Russia may force companies to replace foreign software: Russian lawmakers are considering a law to force all local commercial companies to replace foreign-made software. The Duma previously passed a law requiring state-run organizations to use Russian-made software by 2028. According to RBC, foreign-made software still dominates most Russian industry sectors.
Russia blocks new Telegram and WhatsApp registrations: Russian telecom operators are blocking calls and SMS messages used by Telegram and WhatsApp's two-factor authentication service. The blocking is also affecting new user account registrations. Russia started blocking Telegram and WhatsApp voice calls in August and has been trying to block in-app messaging since last month. [Additional coverage in Kodurova]
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats to Sublime Security CEO and founder, Josh Kamdjou about how Sublime is seeing a massive surge in ICS or calendar invite phishing and how the email security platform can help.
Arrests, cybercrime, and threat intel
Conti member extradited to US: A Ukrainian man was extradited to the US to face hacking charges related to attacks with the Conti ransomware. Oleksii Oleksiyovych Lytvynenko was arrested in Ireland in July 2023. The 43-year-old was allegedly a member of the gang between 2020 and June 2022. He later moved on to other cybercrime activities until days before his arrest.
Thai police arrest fleeing scammers: Thai authorities have arrested 24 individuals working on online scams at a villa near Bangkok. 21 of the 24 were Filipino nationals. Officials say the scammers fled from Myanmar after the neighboring country began cracking down on scam compound operations last month. [Additional coverage in Khaosod] [h/t eerht]
Cambodia raids scam compound: Cambodian authorities have arrested 111 people following a raid at a scam compound in the country's capital. 106 of the suspects were Indonesian nationals. Officials said the raid is part of a larger crackdown on cyber scam operations across the country. [Additional coverage in the Khmer Times]
Singapore seizes scam tycoon's funds: Singaporean authorities have seized S$150 million ($115 million) in assets belonging to a major Cambodian scam compound operator. Both the Prince Holding Group and its founder, Chen Zhi, were sanctioned last month by the US Treasury. The group ran scam compounds in Cambodia, where it used kidnappings and threats of violence to force workers to carry out online scams. Seized assets included bank accounts, securities accounts, cash, a yacht, 11 cars, and six properties.
764 leader charged: The US government has charged an Arizona man with multiple crimes for leading the 764 online terror network. Baron Cain Martin stands accused of extorting children for sexual content, running a murder-for-hire operation, animal torture, and more. Martin was arrested in December of last year. The 764 community is an offshoot of The Com, another online group engaging in similar behavior.
AFP stands up two cybercrime task forces: Australia's Federal Police has stood up two new cyber task forces. The new Taskforce Pompilid will target online networks that exploit young children to produce violent or extremist materials. Taskforce Thunder will focus on cybercrime across the Pacific region.
Woman stuck in Mauritius for five years after cyber charge: A Canadian woman has been stuck in Mauritius for the past five years. Vanita Mirpuri was forced to hand over her passport to the Canadian consulate and is forbidden from leaving the country. She was accused of hacking her former husband's email account five years ago. Local authorities say that while the original charge has been withdrawn, a new hacking charge has been filed against her by her former husband. Canadian authorities are refusing to release her passport until all charges have been settled. [Additional coverage in the Globe and Mail]
Couple loses fortune to scammers: A Canadian couple has lost CAD$1 million (USD$710,000) to online scammers. The couple, in their 70s, fell victim to a tech support scam that showed error messages on their laptop. Over the course of five months, the scammers called the couple daily, posing as Canadian authorities. The scammers convinced the victims to purchase gold from a shady investment portal and transfer Bitcoin via ATM machines. [Additional coverage in CTV News]
TamperedChef variations: CyberProof researchers have spotted new versions of the TamperedChef campaign, spreading its infostealers using various app lures.
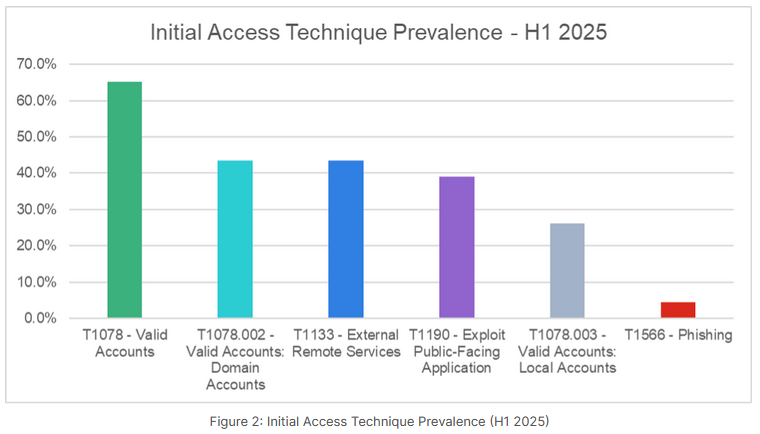
Valid accounts still rule the day: According to Fortinet's H1 IR report, valid/compromised accounts have remained the top entry vectors for most breaches this year.
Open VSX rotate creds: The Eclipse Foundation says it rotated tokens used by developers to publish VS Code extensions on its Open VSX store after the developers leaked the secrets in their code (see this Wiz blog post). The org says it also fully contained the GlassWorm malware that was spreading on Open VSX.
New npm malware: One hundred eighty-seven malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Reformed malware dev: The developer of the ZeroAccess botnet has abandoned the malware ecosystem and is now a legitimate software developer. The man has been identified as Maksim Samuistov, a 40-year-old Ukrainian living in Odessa. According to security researcher Dominik Reichel, the ZeroAccess kernel debugger has been found in multiple legitimate projects. FBI, Europol, and Microsoft disrupted ZeroAccess in December 2013, but Samuistov was never charged with any crimes.
BadCandy flourishes in Australia: More than 400 Cisco IOS XE routers have been infected with the BadCandy malware across Australia. The routers were hacked after owners failed to deploy a 2023 security update. The security update patched a zero-day that was abused by a Chinese cyber-espionage group known as Salt Typhoon. Australia's cybersecurity agency says exploitation was still ongoing as of late October.

New Katreus miner: A threat actor is renting a new cryptominer named Katreus on underground hacking forums.
🚨 New KATREUS Miner (Silent XMR Miner) Advertised on underground forums with: • Anti-kill, watchdog, persistence & injection modules • AV evasion claims (C + ASM) • Targets Windows 8.1 → Server 2025 • Seller offering only 5 “licenses” #ThreatIntel #Cryptomining #InfoSec
— marktsec (@marktsec.bsky.social) 2025-11-01T18:03:31.325Z
Malware technical reports
OysterLoader: An ongoing malvertising campaign is dropping OysterLoader, also known as Broomstick and CleanUpLoader. The malware is typically used as an initial entry point for attacks with the Rhysida ransomware.
SleepyDuck RAT: SecureAnnex has published a report on SleepyDuck, a remote access trojan deployed via boobytrapped VS Code extensions shared on the Open VSX portal. The malware stands out because of its use of the Ether blockchain as a C&C system.
SectopRAT: Prodaft researchers look at SectopRAT, a pretty advanced remote access trojan also known as ArechClient2.
Aura Stealer: Security researcher Xyris has published a two-part analysis of Aura Stealer, an infostealer that popped up this year and is being sold at dirt-cheap prices as low as $2.95 per month.
Sponsor section
In this sponsored product demo, Sublime Security co-founder and CEO Josh Kamdjou joins Risky Business podcast host Patrick Gray to show off the company's email security platform, including its latest agentic AI bells and whistles.
APTs, cyber-espionage, and info-ops
Operation SkyCloak: Indian security firm Seqrite has spotted a spear-phishing campaign targeting Russian and Belarusian military personnel. The campaign specifically targeted the Russian Airborne Forces and Belarusian Special Forces.
Kimsuky's HttpTroy backdoor: Gen Digital has discovered a new backdoor named HttpTroy, used by a North Korean APT group Kimsuky. It also spotted a new version of the BlindingCan RAT, used by the Lazarus APT.
APT-Q-12's NAKSOO RAT: TahirSec has published a report on NAKSOO, a new remote access trojan used by APT-Q-12, a group also known as DarkHotel and APT-C-60. Qihoo 360 also published a report on the same APT, looking at how its operators changed tactics "almost immediately" after a Qihoo report in June. The same APT was also spotted attacking Japanese orgs by the country's CERT.
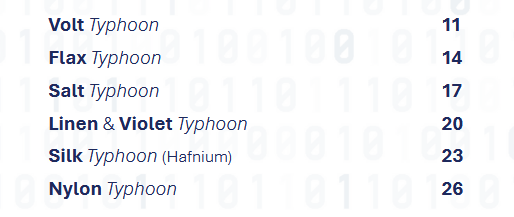
The Typhoons: The McCrary Institute at the University of Auburn has published a report on all the major Chinese APT groups, typically tracked under a [XXX] Typhoon code.
Vulnerabilities, security research, and bug bounty
Linux bug exploited by ransomware groups: Ransomware groups have started exploiting a recent Linux vulnerability in the wild. The attacks leverage a 2024 vulnerability in the Linux nf_tables kernel component to gain root access. Attacks in the wild have been confirmed by CISA, although it's unknown what group is using the bug (CVE-2024-1086).
Anthropic File API abuse: Embrace The Red goes over how the Anthropic File API, used by the Claude Code Interpreter feature, can be used for data exfiltration.
GameMaker IDE vulnerability: A vulnerability allows attackers to crash games compiled with the GameMaker IDE. Only games that use the network_create_server() function are affected. The vulnerability (CVE-2025-12501) allows attackers to crash a game's server using malformed or oversized packets.
GDI bugs: Check Point has published a technical write-up on three bugs in the Windows Graphics Device Interface (GDI). The bugs were patched in May, July, and August.
"Our extensive investigation into EMF+ files shows that staying ahead of potential threats requires continuous diligence and adaptation. By sharing these findings, we hope to raise awareness and provide valuable insights and recommendations to enhance security for all Windows users."
Agent session smuggling attack: PAN's Unit42 has discovered a new technique named agent session smuggling that exploits the A2A protocol to allow malicious AI agents to control other agents.
Elastic security updates: Elastic has released security updates for its ECE (Elastic Cloud Enterprise) platform.
Infosec industry
Threat/trend reports: DataDog, Fortinet, GitHub, Google [PDF], Trellix, and Wallarm have recently published reports and summaries covering various threats and infosec industry trends.
New tool—MCP Scanner: Cisco has open-sourced MCP Scanner, a Python tool for scanning MCP (Model Context Protocol) servers and tools.
New tool—ShareHound: SpecterOps' Remi Gascou has open-sourced ShareHound, a Python tool to map the access rights of network shares into a BloodHound graph.
New tool—Reverie: Facebook has open-sourced Reverie, a syscall interception framework for Linux.
New tool—EDR-Redir: Red teamer Two Seven One Three has published EDR-Redir, a tool to redirect an EDR's working folder to a folder of the attacker's choice.
New tool—Undelete: Head of Research for a supply chain security company Safety, Paul McCarty, has released Undelete, a tool that finds a package that has been recently deleted from the npm registry by searching it across secondary mirrors.
New tool—COM-Fuzzer: Security firm Warpnet has released COM-Fuzzer, a tool to analyze and visualize COM/DCOM interfaces.
New tool—NTLM Password Changer: Security researcher Kazem Fallahi has released NTLM Password Changer, a tool to change Windows account passwords through the Samlib.dll API and avoid triggering the usual password change events.
Infosec drama, episode 28,311: MIT has apparently deleted research about the rise of AI-powered ransomware after being called out by several cybersecurity experts. Unfortunately, the Wayback Machine never forgets. Stay tuned for episode 28,312!
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Peter Williams, the general manager of vulnerability research firm Trenchant, who has pleaded guilty to selling exploits to the Russian zero-day broker Operation Zero. It's a terrible look, but it doesn't mean the private sector can't be trusted to develop exploits.
In this edition of Between Two Nerds, Tom Uren and The Grugq dissect a recent Chinese CERT report that the NSA had hacked China's national time-keeping service.
