Risky Bulletin Newsletter
September 19, 2025
Risky Bulletin: Pentagon has +70K cyber staff, and a lot of overlap
Written by

News Editor
This newsletter is brought to you by application allow-listing software maker Airlock Digital . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
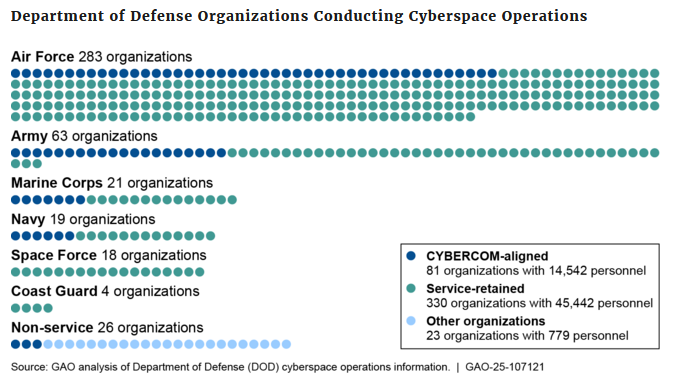
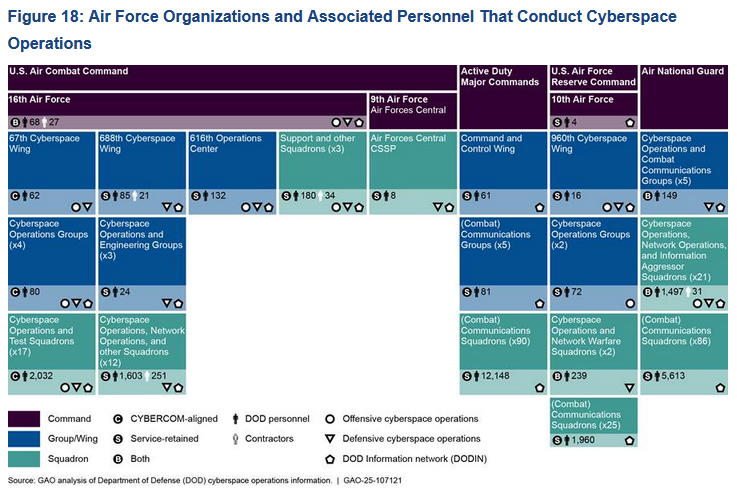
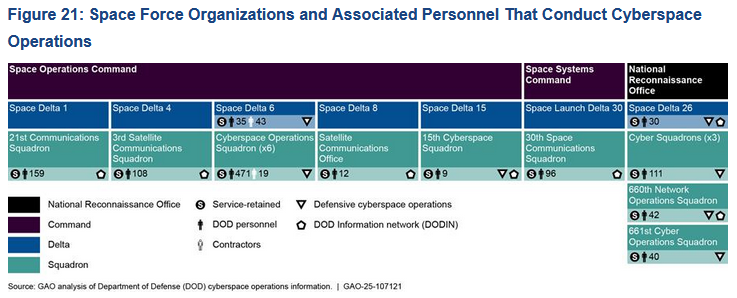
The US Department of Defense has more than 70,000 individuals working on cybersecurity and cyberspace operations, according to a report published this week that provided the first accurate number for such a task force.
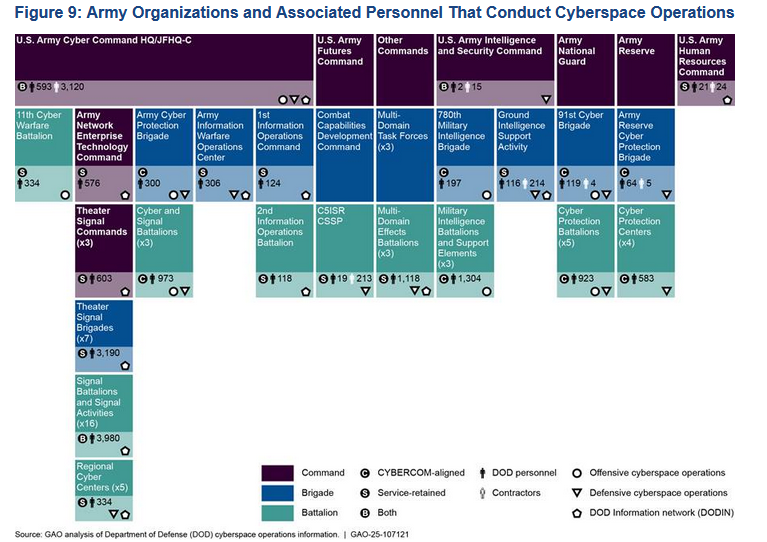
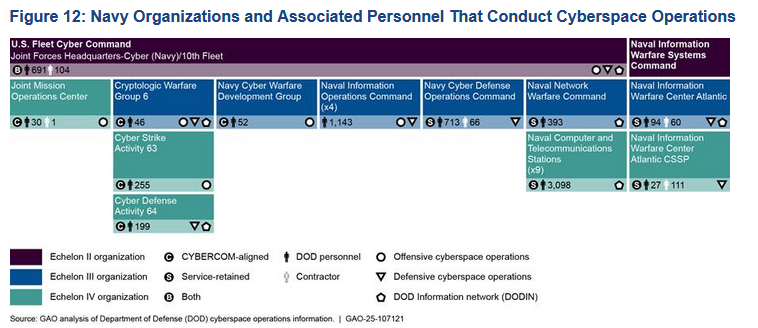
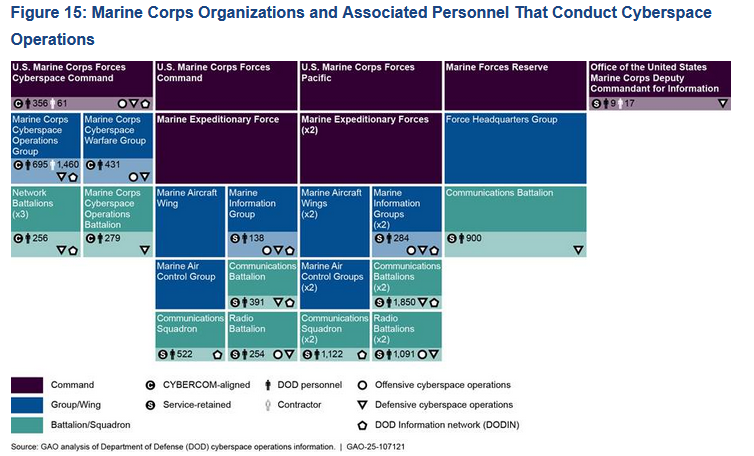
The figure includes 61,000 military and civilian personnel and 9,500 temporary contractors, spread across 504 organizations. They work for Cyber Command, the Army, Navy, Marine Corps, Air Force, and Space Force.
The report , from the US Government Accountability Office, was commissioned by Congress in 2023, after Russia's invasion of Ukraine, to help lawmakers identify all the Pentagon's cyber capabilities and help review and optimize its operations, in light of Russia's invasion of Ukraine and after several hacks of US government networks.
Its main finding is that many organizations and groups across the Pentagon's branches provide overlapping services and that there is room for cost-cutting and reorganization.
The most overlap was found in personnel training and the administration of cybersecurity service providers.
While you might need to run multiple EDRs or parallel vulnerability scanners on the same networks, you don't want every branch setting up its own cyber training structures and basically duplicating and overpaying for the same thing, something that even GAO agreed with.
"Although some overlap can be intentional and appropriate, unnecessary overlap can lead to organizations paying for the same service or product twice or more."
The report doesn't provide a figure of what the DOD could save from deduping, but it comes at the right time to help Defense... uhmmmm... Secretary of War Pete Hegseth make a decision when it comes to Pentagon cost cuts. The DOD hinted back in May that it was looking to release some of its civilian personnel from its cyber workforce.
But aside from US government optimization efforts, the GAO report has its own special importance, being the first full review and inventory of US cyber personnel, something that many in the cybersecurity and national security space will appreciate reading.

Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
DHS I&A leak: A DHS office has leaked unclassified data for two months, between March to May 2023. The leak occurred due to a misconfiguration in a platform managed by the DHS Office of Intelligence and Analysis (I&A). The Office collects surveillance data to share with other US law enforcement agencies. The misconfiguration exposed investigative leads to tens of thousands of users who did not have authorization to view them. [ Additional coverage in the Brennan Center for Justice ]
MySonicWall security breach: Hackers accessed backups of firewall configuration files stored on the MySonicWall cloud service. SonicWall is notifying customers and asking them to reset firewall credentials. Less than 5% of SonicWall's firewalls are affected. The attacker allegedly used a brute-force attack to break into the accounts and steal the backup config files.
Grupo Zeta ransomware attack: The Mydata ransomware has leaked data from Grupo Zeta , one of LATAM's largest distributors of liquefied petroleum gas (LPG).
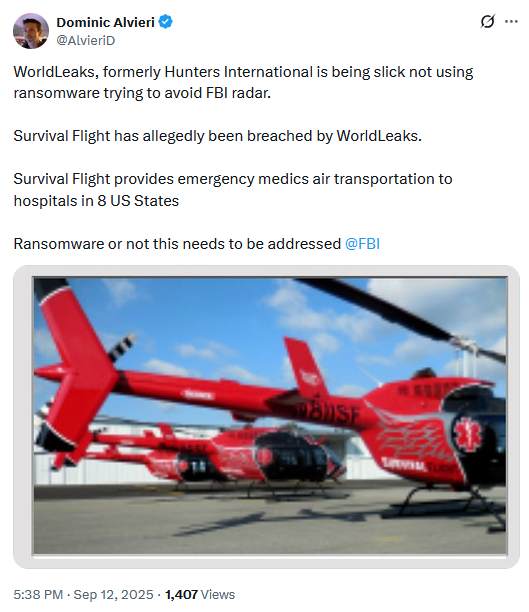
Survival Flight extortion: The World Leaks data extortion crew has leaked patient data from Survival Flight, a provider of medical air evacuation services. The hack took place in July and impacted almost 11,000 patients. According to DataBreaches.net , this is the company's second hack over the past year.
General tech and privacy
DeepSeek returns flawed code to certain groups: The DeepSeek AI engine returns code with security flaws if it determines that the coder is associated with a specific minority group. According to the Washington Post , programmers from Tibet and Taiwan received code of lower quality. DeepSeek also refused requests if queries hinted that the code would be used by the Islamic State or the Falun Gong movement.
Mastodon rolls out post quotes: The Mastodon quote posts feature is now live and rolling out.
Wasm 3 is out: Version 3 of the WebAssembly specification is now live. Most of its new features are already supported in all major browsers, except Safari, which has been lagging behind in almost all new standards for years now.
Tails 7 is out: The Tor Project has released v7.0 of the Tails privacy-centric operating system. The biggest change is a huge speed boost for boot-ups.
Windows 10 EOL: Consumer Reports has joined the increasing list of consumer groups that asked Microsoft to continue supporting Windows 10 past its current EOL of October 14, next month.
Server on a vape: Embedded engineer Bogdan Ionescu has managed to host a web server on a disposable vape .
Fiverr layoffs: Fiverr will fire 250 employees , or about a third of its staff, as the company adopts AI to replace them.
Firefox 143: Mozilla has released Firefox 143. New features and security fixes are included. The biggest feature in this release is support for web apps, pinned websites directly to the taskbar, and running them. You can now also preview the webcam before granting a website permission to use it. DNS-over-HTTP has also arrived in the Firefox for Android version, five years after the desktop version.
Government, politics, and policy
Brazil passes age verification law: Brazil passed a new data protection law. The new Digital ECA is similar to the UK Online Safety Act. It will require companies to introduce age verification checks to limit children's access to sexual and violent content. It also requires tech companies to introduce parental control systems to let parents limit a child's use of their platform. All platforms are banned from using a child's data for targeted advertising. [ Additional coverage in The Record ]
Afghanistan bans fiber optic in a region: The Taliban government in Afghanistan has banned the installation of new fiber optic cables in the Balkh province "to prevent immorality." [ Additional coverage in the AP ]
Moldova establishes disinfo agency: The Moldovan government will establish an agency to counter disinformation. The new STRATCOM agency will have 29 employees and will start operating within a month. First steps to establish the center began in 2023, but it will launch days after Moldova holds its parliamentary elections. [ Additional coverage in Moldpres ]
ICE signs new phone-hacking contract: US Immigration and Customs Enforcement has signed a new $3 million contract with Magnet Forensics. The company merged with Grayshift in 2023 and is the maker of Graykey, a tool to force-unlock phones and extract user data. ICE also signed a $10 million contract with facial recognition company Clearview AI and reactivated a contract with Israeli spyware and surveillance maker Paragon Solutions. [ Additional coverage in TechCrunch ]
Congress hearing on online radicalization: The US House Oversight and Government Reform Committee will hold a meeting with the CEOs of Discord, Steam, Twitch, and Reddit on the radicalization of online users. While you'd think this is because of all the right-wing activity on those platforms that has taken place for years and years, it's not. It's because of the recent Charlie Kirk assassination.
Extremist murders by ideology, 2013 to 2022. www.pbump.net/o/reassessin...
— Philip Bump (@pbump.com) 2025-09-13T02:38:40.803Z
Sponsor section
In this Risky Business sponsor interview , Casey Ellis chats with David Cottingham and Daniel Schell from Airlock Digital. They discuss the challenge of browser extension management for enterprises, why it's a priority, and how Airlock can help.
Arrests, cybercrime, and threat intel
UK arrests two Scattered Spider members: UK police have arrested two teen members of the Scattered Spider hacking group. Thalha Jubair and Owen Flowers were arrested at their home addresses on Tuesday. They are 19 and 18, respectively. They stand accused of hacking London's public transportation agency, Transport for London, last August. Jubair was also charged in the US for the hacks of 47 US companies and extorting ransoms of at least $115 million.
Suspect charged in UK political honeytrap scandal: A former UK Labour councillor has been charged with blackmail and communications offences related to a UK Parliament honeytrap scandal. Oliver Steadman allegedly posed as a woman and sent flirtatious WhatsApp messages and indecent images to 12 individuals, including five UK politicians. The incident took place in late 2023 and was initially believed to be the work of foreign hackers. Steadman was arrested in April 2024 and charged this week. He resigned from his position shortly after the arrest. [ Additional coverage in Politico Europe ]
AI chatbots abused for scams: A Reuters study found that threat actors can easily trick AI chatbots to write phishing emails, even if they should normally refuse these types of tasks. Tested chatbots included Claude, ChatGPT, DeepSeek, Gemini, Grok, and Meta AI.
M365 hack spike: Finland's cybersecurity agency has noted a sudden rise in hacked Microsoft 365 accounts in August. The agency received 70 reports last month of hacks that originated from compromised Microsoft 365 accounts. August alone accounted for a fifth of all breaches that originated from Microsoft 365 accounts this year (330).
GOLD SALEM profile: Sophos has published a profile on GOLD SALEM , a suspected Chinese threat actor that is behind the Warlock ransomware.
ShinyHunters profile: EclecticIQ has published a profile on ShinyHunters and the group's recent shenanigans. It's a good summary of all its recent TTPs, from vishing to phishing infrastructure. According to a different report from ReliaQuest , the group is now primarily focused on financial institutions.
"EclecticIQ analysts assess with high confidence that ShinyHunters team collaborated with other eCrime actors, such as Scattered Spider and RaaS members in DragonForce, to increase the success rate of their attacks."
ComicForm group: F6 researchers have spotted a new threat actor ( ComicForm ) using mass email campaigns to target companies in Russia, Belarus, and Kazakhstan.
GhostAction supply chain incident: PyPI says it invalidated all PyPI tokens stolen from GitHub repos by a malicious action on September 5 in a supply chain attack known as GhostAction. The PyPI team says none of the tokens were abused to upload malware to their registry.
Shai-Hulud worm reaches 500 packages: A supply-chain attack that deployed a worm on the npm repository has now reached more than 500 packages . The worm has been linked to the same group that carried out a previous npm supply-chain attack known as S1ngularity . Just like in the previous attack, attackers steal access tokens and upload them to public GitHub repositories. The worm skips Windows and only runs on macOS and Linux systems. Security firm UpGuard has also identified at least 17 major companies impacted the the token thefts.
Interesting. I’ve seen publicly leaked exfil’d data that are from windows hosts. See end of this thread. bsky.app/profile/evil...
— Adam Baldwin (@evilpacket.net) 2025-09-18T00:21:48.049Z
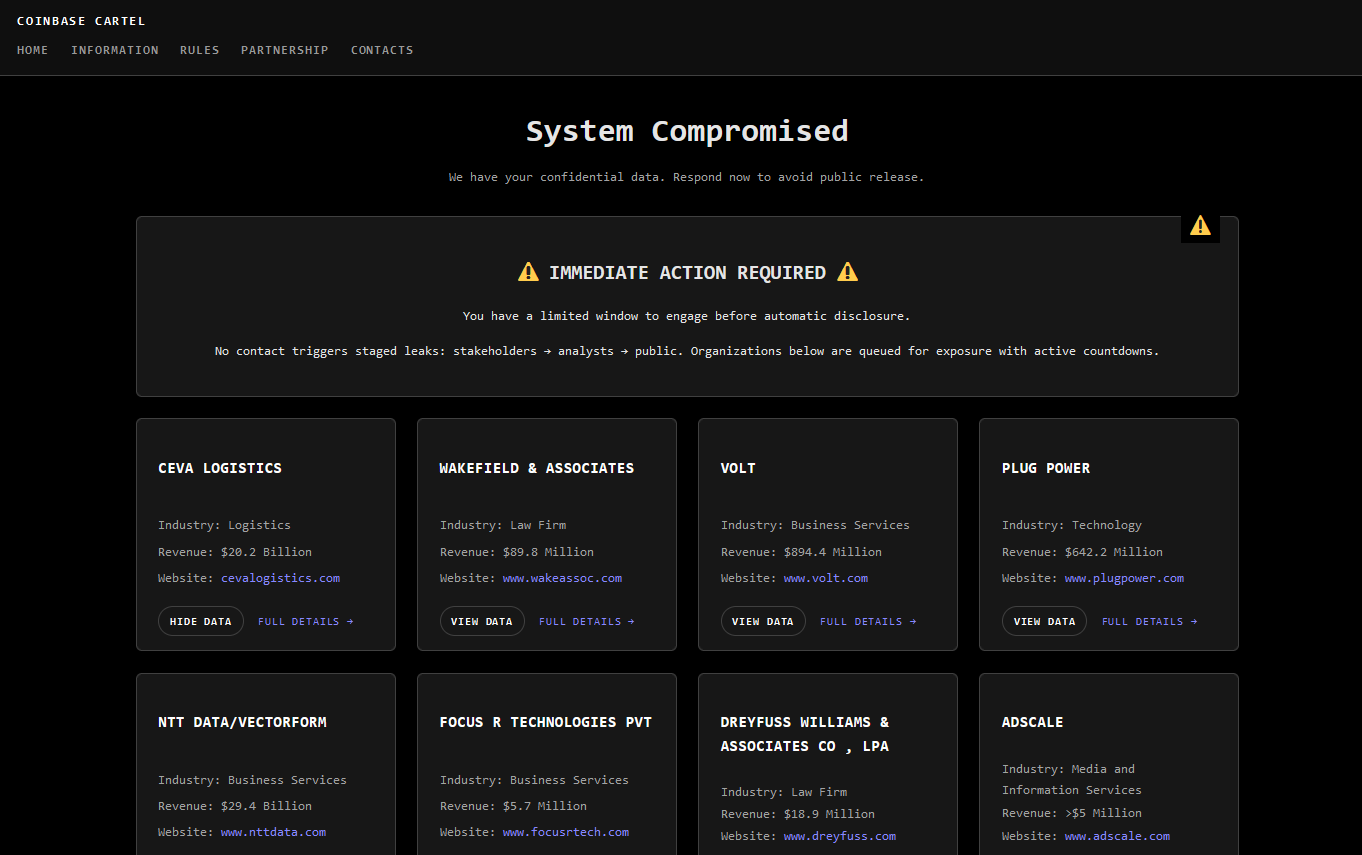
New CoinbaseCartel extortion group: A new data extortion group named the CoinbaseCartel has been spotted extorting victims this month. Its dark web leak site currently lists ten victims, including some big names like SK Telecom, Desjardins, and NTT Data.
Malware technical reports
CountLoader: Silent Push has discovered a new malware loader named CountLoader that is currently being used by Russian-based initial access brokers in attacks that later deploy ransomware such as LockBit, BlackBasta, and Qilin.
Formbook: Security researcher Cormac Conlon has published a technical write-up on Formbook .
SilentSync RAT: Zscaler has discovered two malicious PyPI packages deploying the new SilentSync RAT . The malware can only run on Windows, can execute remote commands, and has all the info-stealing features you want.
SystemBC botnet returns: The SystemBC malware botnet has returned to life and is infecting new devices. The botnet had servers seized by Europol in May last year. According to Lumen , the botnet is now targeting virtual private servers instead of home consumers. They are renting access to the hacked servers to multiple proxy network operators.
New Ivanti device malware: CISA has published details about a new backdoor found deployed on hacked Ivanti devices this year.
BlackLock ransomware: AhnLab has published a report on the BlackLock ransomware , a group that launched in June last year, after rebranding from the El Dorado name.
Raven Stealer: Point Wild has spotted a new C++ and Delphi-based infostealer advertised under the name of Raven Stealer .
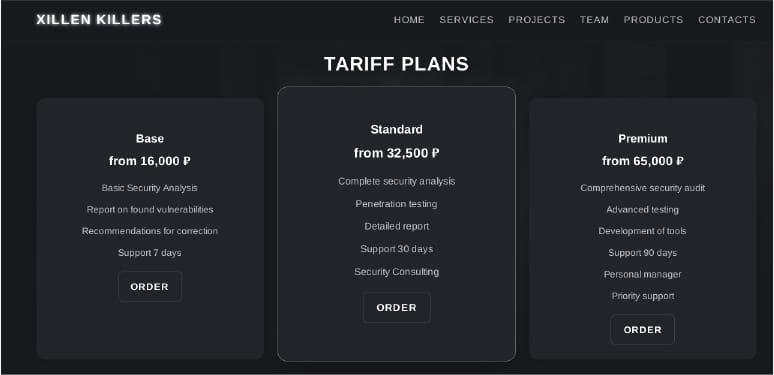
XillenStealer: CyFirma looks at XillenStealer , an open-source Python-based infostealer available on GitHub. A commercial version is also being sold online through a dedicated website. Evidence suggests that the malware's creator is a Russian speaker.
Sponsor section
In this product demo of the Airlock Digital application control and allowlisting solution, Patrick Gray speaks with Airlock Digital co-founders David Cottingham and Daniel Schell.
APTs, cyber-espionage, and info-ops
CopyCop infrastructure: Recorded Future looks at new infrastructure linked to a Russian influence operation known as CopyCop, or Storm-1516. This includes " 200 new fictional media websites targeting the United States (US), France, and Canada, in addition to websites impersonating media brands and political parties and movements in France, Canada, and Armenia ."
Kirk disinfo campaigns: NewsGuard looks at how China, Russia, and Iran used the Charlie Kirk assassination to try and divide the US or for their own silly political aims, such as trying to link Ukraine or Israel to the gunman.
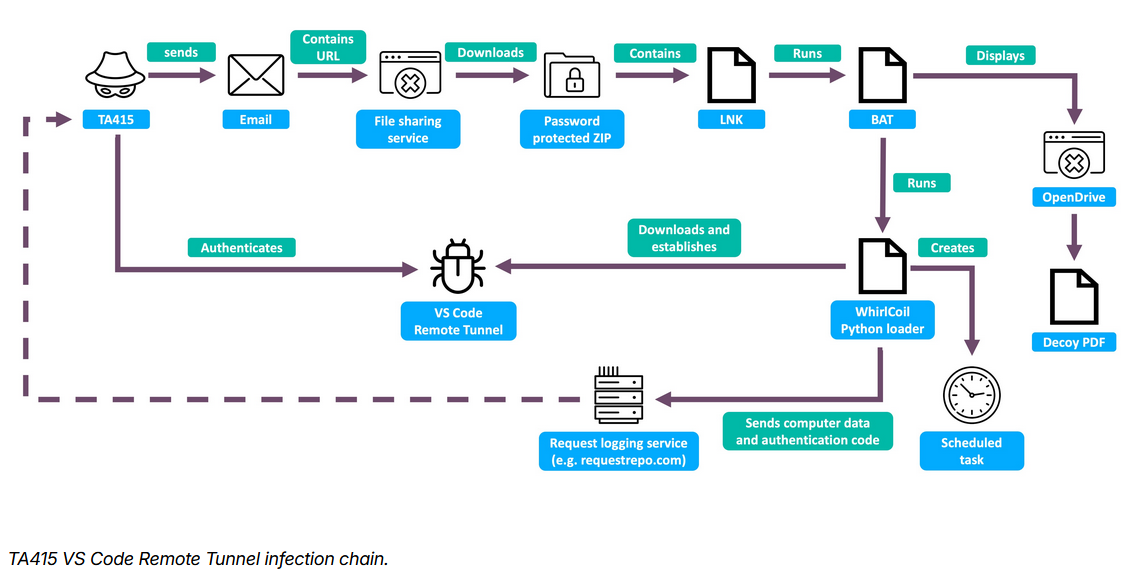
TA415 abuses VSCode tunnels: A Chinese cyberespionage group is abusing the VSCode Remote Tunnel feature to control malware in compromised environments. The technique has been used in recent attacks against US think tanks, government, and academic organizations. Proofpoint linked the attacks to a group known as TA415 and APT41.
New MuddyWater tooling and infrastructure: Group-IB has uncovered new infrastructure and malware variants used by the MuddyWater Iranian cyber-espionage group.
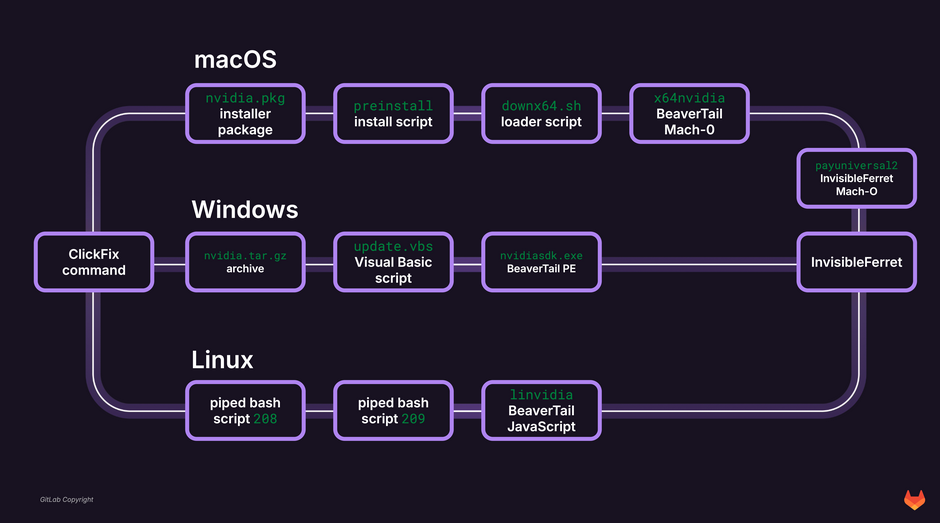
Contagious Interview infrastructure: The GitLab security team has identified new infrastructure used to deploy BeaverTail and InvisibleFerret, malware linked to North Korean hackers.
Vulnerabilities, security research, and bug bounty
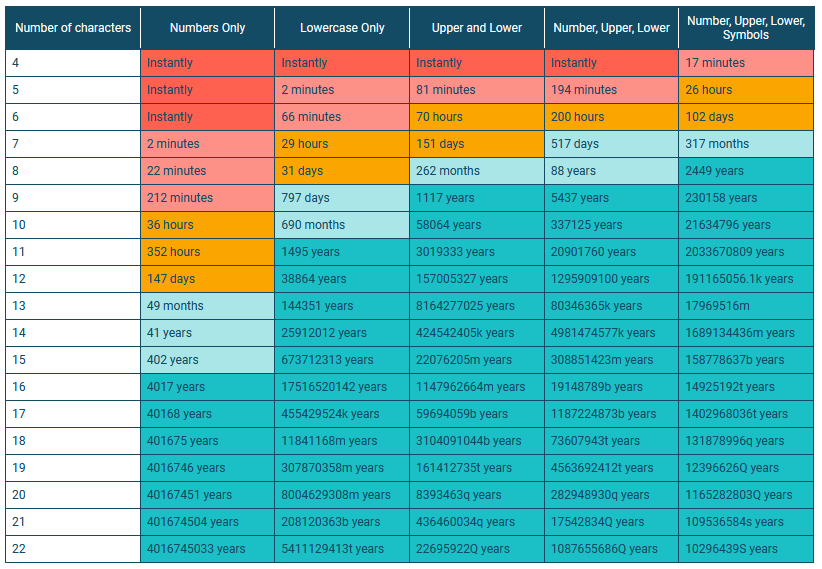
Bcrypt cracking table update: SpecOps has updated the bcrypt cracking table times if attackers were using modern GPU cards. Insert " correct horse battery staple " joke .
Azure Entra EoP: Dirk-jan Mollema has published a write-up on CVE-2025-55241 , a vulnerability that can let attackers gain global admin rights over any Azure Entra ID tenant. This was patched at the start of the month in an emergency Azure security update.
PureVPN IP leak: A software engineer known as Andreas has found two IP leaks in the PureVPN GUI and CLI clients for Linux.
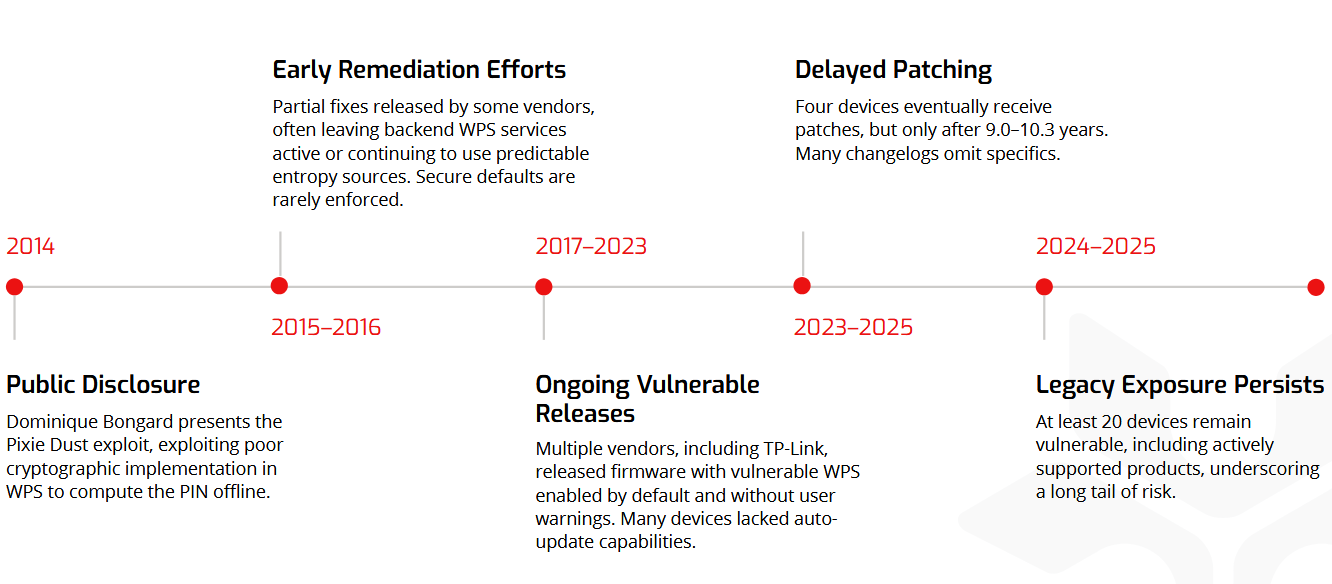
Pixie Dust is still exploitable: Many current router models are still vulnerable to a 10-year-old WiFi attack named Pixie Dust. The attack allows threat actors to recover a router's WPS PIN and access its WiFi network. A NetRise study of 24 current routers found that 20 were still vulnerable.
ShadowLeak ChatGPT zero-click attack: Radware researchers have discovered a zero-click attack that can leak inbox data from a Gmail account that is using ChatGPT's Deep Research email agent, just by sending one malicious email to a victim's account.
Chrome zero-day: Google has released a security update to patch an actively exploited Chrome zero-day. Tracked as CVE-2025-10585, the zero-day is a vulnerability in Chrome's V8 JavaScript engine and was discovered by one of Google's internal security teams. It is the sixth Chrome zero-day patched this year.
WatchGuard security update: WatchGuard has patched an unauth RCE in its Firebox firewalls.
Atlassian security updates: Atlassian released five security updates last week, part of the company's September Patch Tuesday. One of them is a Confluence RCE.
Jenkins security updates: The Jenkins project has published seven security updates for the project's core files.
GitLab security updates: GitLab has released security updates to patch six vulnerabilities in its main product.
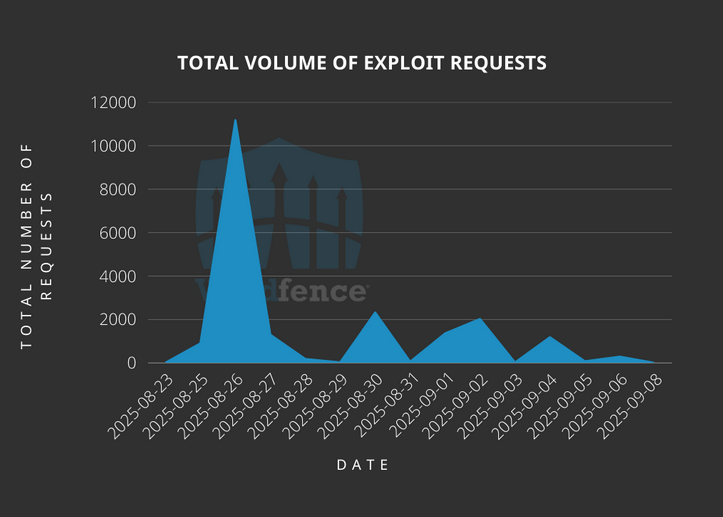
Case Theme User exploitation: Threat actors are exploiting a vulnerability in Case Theme User, a WordPress plugin bundled with various commercial WordPress themes. The vulnerability allows remote attackers to access any account on sites if they know a user's email address. According to Wordfence , the plugin is installed on more than 12,000 websites. Exploitation began at the end of August and is ongoing.
Infosec industry
Threat/trend reports: Akamai , Claroty , Emsisoft , Moonlock [ PDF ] , NCC Group , NordVPN , and TIOBE have recently published reports and summaries covering various threats and infosec industry trends.
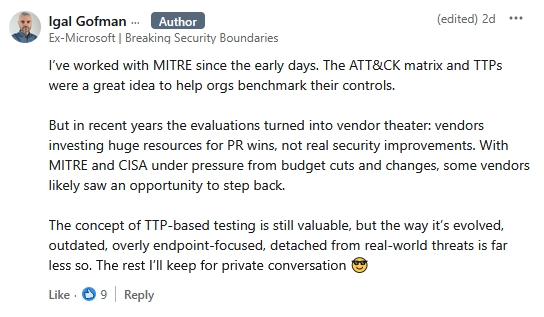
Companies pull out of ATT&CK evaluations: Three major EDR vendors have pulled out of evaluations for the MITRE ATT&CK framework. The evaluations check if the EDRs detect common TTPs used in the real world by known threat actors. SentinelOne and Palo Alto Networks pulled out last week, while Microsoft left in June. [ h/t Patrick Garrity ]
Netskope increases IPO: Security firm Netskope has raised the price of its IPO from the initial $15/share price to $17. [ Additional coverage in CNBC ]
New tool—Fickling: Security firm Trail of Bits has released Fickling , a tool to decompile, analyze, and rewrite Python pickle files, a format used by AI/ML tools.
KazHackStan 2025 streams: Live streams from the KazHackStan 2025 security conference, which took place this week, are available on YouTube . The recordings are in Russian.
Black Alps 2024 videos: Talks from the Black Alps 2024 security conference, which took place last November, are available on YouTube .
Risky Business podcasts
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about why it is good news that US investment in spyware vendors has skyrocketed. They also discuss the in-principle agreement for TikTok to remain in the US. It's a win-win: a win for China and a win for TikTok, but not so much a win for US national security.
In this edition of Between Two Nerds , Tom Uren and The Grugq talk about the limits of a state's cyber power.
