Risky Bulletin Newsletter
February 04, 2026
Risky Bulletin: Plone CMS stops supply-chain attack
Written by

News Editor
This newsletter is brought to you by Dropzone. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Plone, a Python-based content management system, has avoided a supply chain attack at the start of this year.
A threat actor inserted malicious code in five of the organization's repositories but the modifications were spotted before they made it to any official release.
The incident was traced back to a single developer's account.
The attacker managed to get their hands on the developer's GitHub personal access token and force-pushed the malicious code hidden after a lot of whitespace.
"Locally the diff seemed only whitespace, but the malicious code is hidden after a lot of spaces, disappearing to the right of my terminal (this might be a git setting I have). On GitHub you can see it after clicking an extra button. I have committed a fix on master, removing the code."
"For clarity, why was this attack done by force pushes? Because they are harder to notice. The user could have done a normal push, but that would have been easier to look for. Anyway, for most repos we already had protection in place, so that the main or master branch could not be force pushed to."
According to Plone Release Manager Maurits van Rees, the attacker modified JavaScript code in the Plone CMS, which has since been removed.
According to GitHub's security team, which investigated the incident on behalf of the compromised user, the code targeted other developers working with Plone, and not visitors of Plone-based websites.
The code sets shell startup scripts for persistence, uses an RCE to take control over the developer's machine, and then starts exfiltrating sensitive data such as credentials, API keys, browser profiles, and crypto wallet files.
It is unclear how the attacker gained access to the compromised dev's personal access token, but the user said the attacker had access to the token for two months before the force-push operations.
This is just me theorizing about a possible source, but this would put the initial compromise of the developer's account at around the date of the Sha1-Hulud and GlassWorm self-replicating worms that hit the npm and VSCode ecosystems back in October. These worms targeted developers and stole their credentials, which is possible how they gained access to the GitHub personal access token.
For its part, the Plone project says it has now revisited some of the project's security settings and disabled a lot of risky Git operations and permissions, including force pushes.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Hackers extort school kids' parents: Hackers who breached a high school in Belgium are trying to extort the students' parents after the high school refused to pay a ransom demand. They are demanding €50 from each parent not to publish their child's data online. The attackers hacked the Our Lady Institute Pulhof in Antwerp last month and demanded €15,000 from the school's management. [VRT NWS // The Record]
Step Finance hacked for $30m: Hackers have stolen almost $30 million worth of tokens from the Step Finance DeFi platform. Step says the hackers used a "well known attack vector" to gain access to its treasury wallets. The platform's token, the STEP, plummeted more than 80% after the hack. [Blockonomi]
CrossCurve threatens hacker: The CrossCurve cryptocurrency bridge was hacked for $3 million after hackers exploited a bug in its smart contracts. CrossCurve CEO Boris Povar has threatened to take legal action against the attacker if they don't return the funds in three days. This will include a criminal complaint and a separate civil litigation. The company was previously known as EYWA. [Decrypt]
NationStates game reports breach: The NationStates browser game has reported a security breach caused by a player and bug hunter. The individual gained access to a production server and downloaded the game's source code and user data. NationStates says the player apologised but said data such as emails, passwords, and IP addresses were exposed nonetheless.
Canada Computers breach exposes card data: Canadian IT retailer Canada Computers has suffered a security breach that compromised customer card data. Customers who used the guest checkout option on its website had their personal and card data collected. The malicious code was live between December 29 to January 22. [CBC]
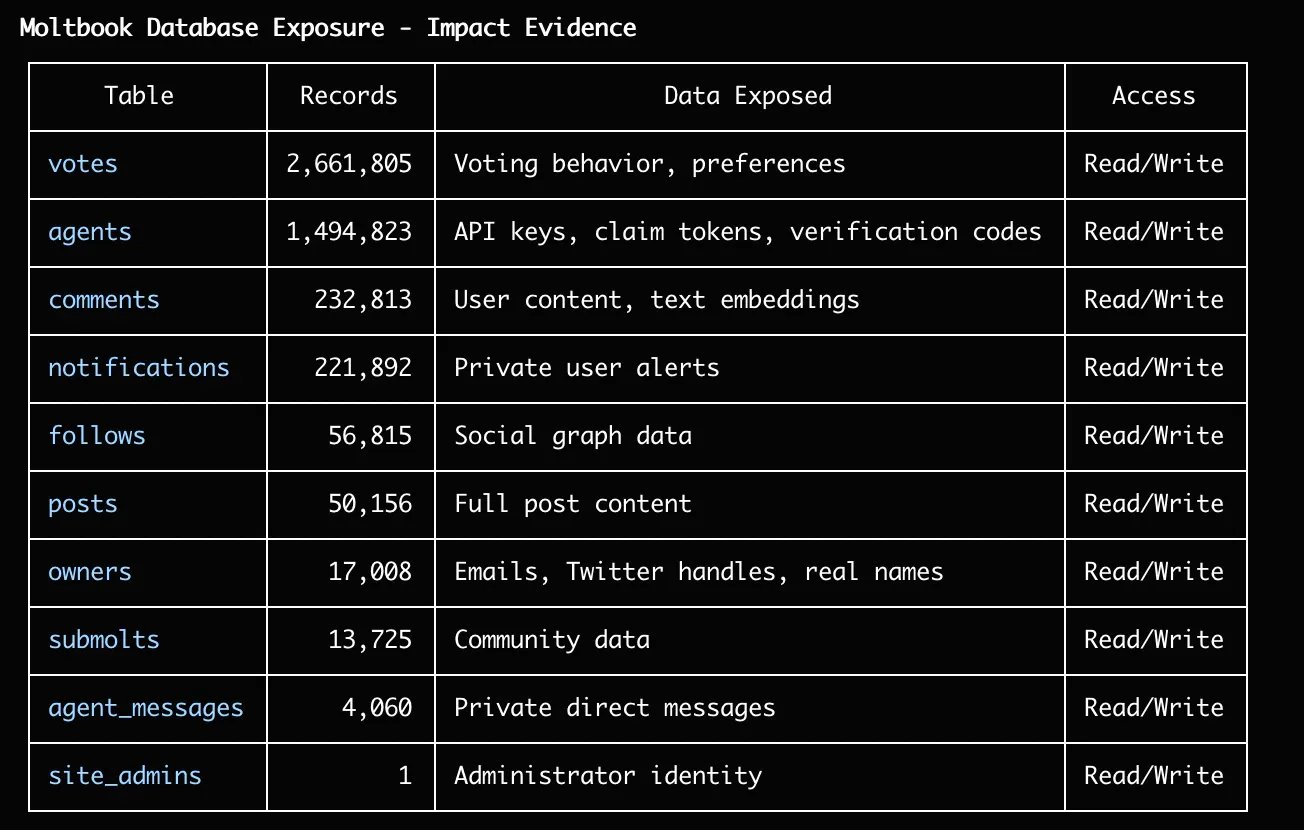
Moltbook mega-leak: A backend database belonging to the Moltbook AI platform has exposed more than 1.5 million API tokens, according to reports from cloud security firms Permiso and Wiz. The platform is a social network for OpenClaw personal AI assistants. The leak exposed the API tokens of the connected OpenClaw agents, messages exchanged between them, and information on the agents' owners. The source of the leak was a misconfigured Supabase production database that was left exposed on the internet with full read and write permissions.
General tech and privacy
France raids Twitter's Paris offices: French authorities [PDF] and Europol have raided the French offices of social media network X. The raids are part of a criminal investigation over spreading child sexual abuse images and pornographic deepfakes. The investigation is related to a Grok AI feature that lets Twitter users generate nude images, including of small children. French authorities have also summoned Elon Musk and former CEO Linda Yaccarino to appear at hearings in April. Both Ofcom and the ICO also announced official investigations into the platform on the same day in the UK. [The Independent]
A defining feature of life in the US today is watching other countries address serious issues in ways this country can not, or will not, do.
— Philip Eil (@phileil.bsky.social) 2026-02-03T14:54:14.860Z
Mountain View disables all Flock ALPRs: The city of Mountain View in California, the home of most of the US tech sector, will disable all Flock automated license plate readers. The city is disabling the cameras after "out of state agencies" accessed the city's data without its awareness or consent. Mountain View officials say Flock also failed to notify them of the unauthorized access to its data.
WhatsApp now uses Rust for media processing: Meta is now using a Rust component to safely process media files shared on WhatsApp. Meta is moving to Rust after it realized that the vast majority of major WhatsApp security flaws were caused by memory safety bugs in its C and C++ code. The company plans to use memory-safe languages like Rust for all new code going forward.
Open VSX to boost security: The Eclipse Foundation will roll out a series of security features to the Open VSX marketplace for VS Code extensions. The platform will scan extensions for malicious code, typosquatted names, and extensions that accidentally contain credentials. It will start monitoring extensions in February and start the enforcement phase the next month. Over the past months, Open VSX has hosted hundreds of malicious extensions, including a self-replicating worm named GlassWorm.
YouTube blocks third-party playback on mobile: Google has confirmed that it is now blocking YouTube videos from playing in the background via third-party browsers like Vivaldi, Firefox, and Samsung Internet. [Android Authority]
"Background playback is a feature intended to be exclusive for YouTube Premium members. While some non-Premium users may have previously been able to access this through mobile web browsers in certain scenarios, we have updated the experience to ensure consistency across all our platforms."
Firefox adds AI killswitch: Mozilla will add controls in the Firefox settings that will let users disable its new AI features. The controls are coming in Firefox 148, to be released this month.
AI Controls (formally 'kill switch') are landing in today's Firefox Nightly, and will land with Firefox 148 later this month.
— Firefox for Web Developers (@webdevs.firefox.com) 2026-02-02T17:07:57.561Z
Government, politics, and policy
Russia goes after cash deposits at ATMs: The Russian government is working on a law that will require banks to refuse cash deposits at ATMs of more than 1 million rubles ($13,000) per month. The measure is designed to block some methods of money laundering. Currently, there are no limits on ATM cash deposits. [Interfax]
Russia reconsiders IM bans: Some Russian lawmakers have introduced a bill that would block the Roskomnadzor from full-blocking instant messaging services such as Telegram and WhatsApp, claiming it violates citizens constitutional rights. [RBC]
FCC warns of ransomware attacks: The FCC has urged American telecommunications companies to secure their networks against ransomware attacks. The agency has asked telcos to patch their software, enable MFA, and segment and regularly scan their networks. The FCC said it was aware of multiple incidents that have already hit some of the smaller providers. [CybersecurityDive]
ICE uses Mobile Fortify: ICE agents are using an app named Mobile Fortify to scan someone's faces and match them against a huge biometrics database of more than 1.2 billion images. The database aggregates photos from multiple US government systems. Its two primary sources are two DHS databases—the Homeland Advanced Recognition Technology, or HART, and Automated Biometric Identification System, or IDENT. [Bloomberg]
Liberty Eclipse cyber exercise: The US Department of Energy held its annual cyber-exercise that mimics a cyberattack on US critical infrastructure.
EU to share data with US border agency: Even if White House officials are mocking and attacking the EU on an almost daily basis and its border agency is randomly picking people off the streets, EU officials are apparently going ahead with a plan to share the personal and biometrics data of EU citizens with the US for border enforcement. Bruxelles really needs to start reading the room. [Politico Europe]
Spain goes on the kids social media ban train: Spain is the latest country to flaunt a social media ban for kids under the age of 16. It joins the likes of Australia, Russia, France, the UK, and the Netherlands. [CNBC]
NSO is meddling in the Pall Mall process: Multiple human rights groups warn that sanctioned spyware maker NSO Group is trying to attach itself to political initiatives tied to the Pall Mall process in an attempt to have the sanctions lifted and come back into the market. [The Record]
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats to Edward Wu, founder of Dropzone AI about a recent Vanderbilt University report that reveals that foreign adversaries’ resources are growing. Edward says AI capabilities are critical to the future of cyber defence, because the west can’t hire itself out of the shortfall.
Arrests, cybercrime, and threat intel
Meta's ad problem is bigger than thought: Nearly one in three Meta ads shown in the EU and the UK over a 23-day period pointed to online scams. A small cluster of just ten advertisers were responsible for over 56% of the malicious ads. The ads and the scam sites shared payment and infrastructure linked to China and Hong Kong. Gen Digital believes this is an indicator of an organized, industrial-scale operation.
Epstein sought to hire Sabu: Late sex offender Jeffrey Epstein, at one point, sought to hire a hacker and was recommended to reach out to Hector "Sabu" Monsegur of LulzSec fame. Monsegur says he was never contacted, despite his name being in recently released Epstein documents. [Straight Arrow News]
Recon campaign targets Citrix devices: A massive reconnaissance campaign targeted Citrix devices last week. The attack used more than 60,000 residential IPs to search for the login pages of Citrix ADC and Netscaler gateway devices. According to GreyNoise, reconnaissance activity to map infrastructure typically predates new exploitation attempts.
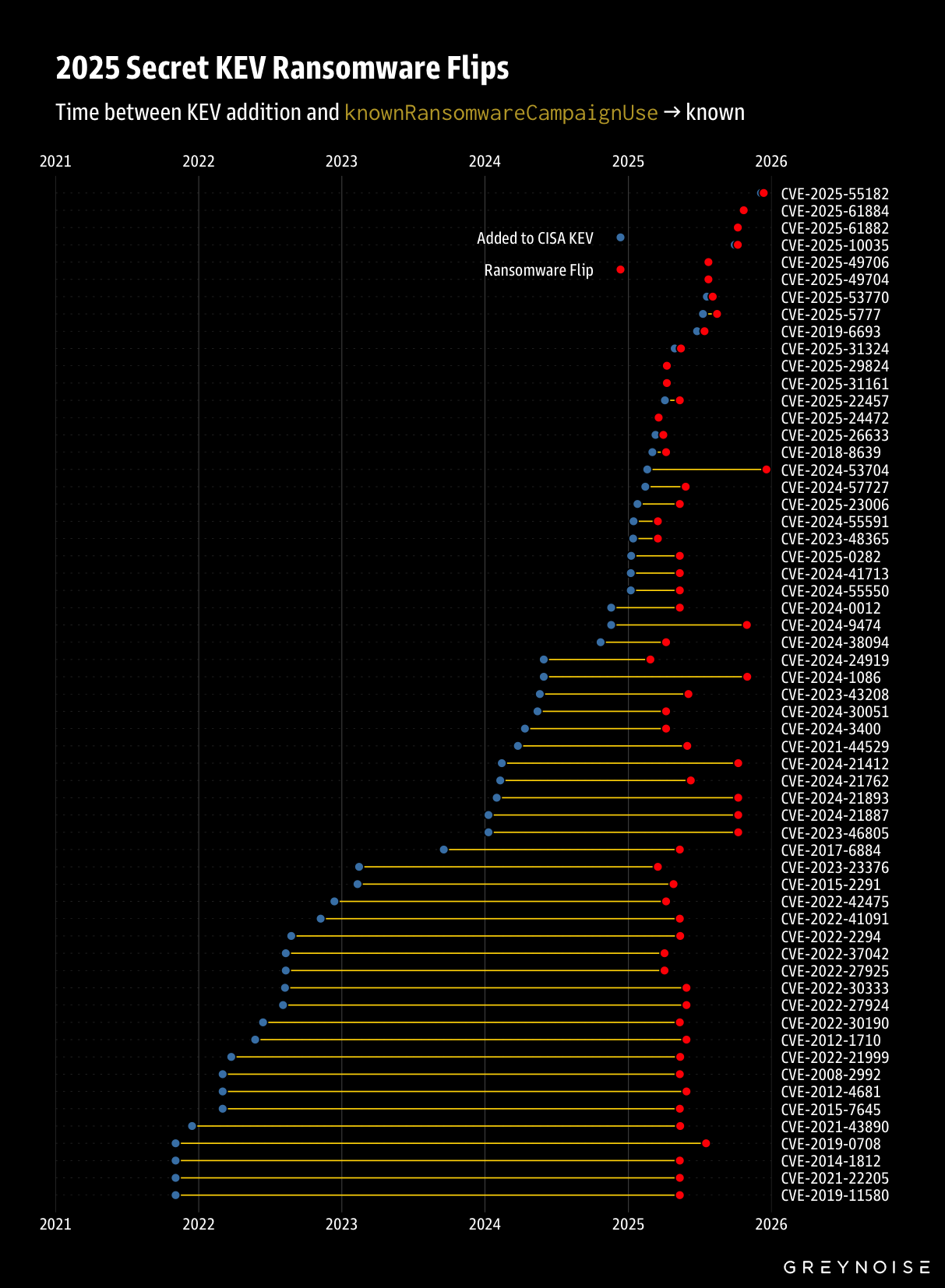
Ransomware arsenal expanded last year: CISA silently updated entries for 59 vulnerabilities last year. The silent updates flipped a tag meaning the bugs were used in ransomware attacks. A third of the updated vulnerabilities impacted networking devices. Security firm GreyNoise says the updates are welcome but says most security teams would have not been aware of them since the agency doesn't advertise them.
"If CISA updates a vulnerability's status in the Known Exploited Vulnerabilities (KEV) catalog and nobody notices, did it even matter?"
AppLocker abuse: Threat actors are abusing AppLocker rules to prevent EDR solutions from starting. The Purple Team looks at how this can be abused in the wild.
ClawHub malicious skills explode: The number of malicious skills on the ClawHub portal has exploded from 28 last week to almost 400 on Tuesday, according to reports from Gen Digital, Koi Security, and OpenSourceMalware. OpenClaw is an open-source AI assistant that users can host locally and connect to their apps and personal accounts. Skills work like plugins and allow the assistant to perform certain automated tasks. Since its meteoric rise to fame this month, security researchers have now spotted an influx of malicious OpenClaw skills that steal user credentials or deploy malware on their computers. The assistant was previously known also as ClawdBot and MoltBot.
NyashTeam still alive: A cybercrime operation known as the NyashTeam has survived a takedown from Russian authorities and is still active. Russian security firm F6 says it found new server infrastructure and malware developed by the group, including a new Windows screen locker. Russia's national domain registrar seized 110 domains operated by the group last July. The NyashTeam has been active since 2022 and has primarily developed remote access trojans.
Global Man exit scams: An underground cybercrime service that sold code-signing certificates has exit-scammed. The certificates were used by multiple malware operations to sign their payloads. The Global Man team claims the service's source code was compromised. Funds deposited by customers in the service have also disappeared.
Malware technical reports
The Nitrogen ransomware has a bug: The Nitrogen ransomware contains a bug that permanently corrupts encrypted files. The bug overwrites a part of the ransomware's public key. It only impacts Nitrogen's ESXi variant. Security firm Emsisoft has urged victims to avoid paying the attackers since they will not be able to decrypt their files.
LockBit 5.0 ransomware: LevelBlue's SpiderLabs has published a report on the ESXi version of the LockBit 5.0 ransomware strain. This is just part one of a LockBit series, with two more parts to come.
DragonForce ransomware: LevelBlue's Cybereason team has published a report on the inner-workings of the DragonForce ransomware crew and their tumultuous 2025.
ValleyRAT: The same Cybereason team also looks at a campaign delivering ValleyRAT.
njRAT: Netresec researchers have published a report looking at njRAT campaigns dropping the MassLogger infostealer.
Arsink RAT: Zimperium has spotted a spike in detections of Arsink, a remote access trojan targeting Android devices.
"Distribution is broad and social-engineered. The malware is pushed via Telegram, Discord, and MediaFire links, as well as similar channels, while impersonating dozens of popular brands."
Sponsor section
In this sponsored product demo, Dropzone founder and CEO Edward Wu walks Risky Business podcast host Patrick Gray through the company's AI SOC analyst.
APTs, cyber-espionage, and info-ops
Notepad++ incident linked to Chinese APT: A Chinese state-hacking group compromised the server infrastructure of the Notepad++ app for six months last year. Cybersecurity firm Rapid7 has linked the attack to a group known as Billbug and Lotus Blossom. The attackers used access to Notepad++ servers to ship malicious updates to a small number of carefully selected targets. The final payload was a never-before-seen backdoor named Chrysalis. According to Kaspersky, targeted individuals included:
- Individuals located in Vietnam, El Salvador and Australia;
- A government organization located in the Philippines;
- A financial organization located in El Salvador;
- An IT service provider organization located in Vietnam.
APT28 jumps on new Office zero-day: Russian GRU-linked cyber-espionage group APT28 is now using an Office zero-day disclosed last week for spear-phishing campaigns targeting Ukrainian targets, per a new Ukraine CERT report. Zscaler also covered this campaign, which also targeted EU countries, in what it calls Operation Neusploit.
KGB internal memo on viruses: Russian cyber expert Oleg Shakirov has uncovered an internal KGB memo from the USSR era that detailed the first computer virus and its impact on the Russian IT landscape, and even some KGB systems. [Packets from Cyberia]
"While the authors of the memo correctly identified uncontrolled software sharing as the main reason for proliferation of malicious programs, they were also concerned about the possibility of viruses being weaponized by Soviet Union’s adversaries. This concern was informed by the KGB’s past experience of ensuring security of imported computers."
ATPs in Russia: Russian security firm F6, which splintered from Group-IB, has published its yearly threat report. The company says it tracks 27 APTs targeting Russia and the CIS space. A similar report from Positive Technologies found that APT attacks didn't only increase, but also grew in sophistication.
Lazarus series: Red Asgard has published parts III and IV of their series on tracking Lazarus APT operations. Parts I and II are linked. The reports specifically look at the group's "Contagious Interview" campaigns that target job seekers.
Vulnerabilities, security research, and bug bounty
Legal threats against researchers and infosec reporters: A joint survey conducted by infosec reporter Zack Whittaker and DataBreaches.net found that 90 of 112 respondents, which included security researchers and cybersecurity journalists, received legal and criminal threats over their work.
"Overall, half of the respondents reported receiving at least one legal threat. Researchers and journalists were equally likely to receive legal threats, but journalists were a lot more likely to be threatened by criminals. Despite receiving threats, the majority of respondents did not retract or change their research or reporting."
Metro4Shell attacks: Threat actors are exploiting a vulnerability in Metro, a development server that ships with the React Native app framework. Tracked as CVE-2025-11953, the vulnerability was disclosed in November and the first attacks started a month later. It is an OS command injection that allows remote unauthenticated attackers to run malicious commands via simple server POST requests. Security firm VulnCheck has spotted attacks targeting Windows systems with PowerShell-based loaders.
KEV update: CISA has updated its KEV database with four vulnerabilities that are currently exploited in the wild. They include two FreePBX bugs, and GitLab and SolarWinds vulnerabilities.
RRLP and LLP tracking: Software engineer Sudheer Singh looks at how telcos use the RRLP and LPP protocols to extract the exact GPS coordinates of their subscribers without a notification or prompt on the device. The two protocols were initially designed to help emergency services locate callers in distress, but has since been adopted for more shady ad tracking practices.
GatewayToHeaven vulnerability: Security researcher Omer Amiad has published a report on GatewayToHeaven, a vulnerability in the GCP's Apigee that allowed for attackers to read and write cross-tenant access logs and analytics data.
Quest RCE: NetSPI has found a remote code execution vulnerability in the Quest Desktop Authority, an enterprise platform for managing Windows endpoints at scale. Tracked as CVE-2025-67813, the bug allows attackers to tap into an SMB named pipe used by the Quest desktop agents and run malicious commands using SYSTEM privileges.
Unfixable Chrome URL leak bug: The Google Chrome team says it is "infeasible" to fix a side-channel attack that can allow malicious extensions to leak a user's current URL.
Infosec industry
Threat/trend reports: F6, Intezer, NightDragon, Patchstack, Positive Technologies, Prove, and ThreatDown have recently published reports and summaries covering various threats and infosec industry trends.
New tool—GhostKatz: Security researcher Julian Peña has released GhostKatz, a tool to extract LSASS credentials directly from physical memory by abusing signed vulnerable drivers.
New tool—LOLAPI: A security researcher going by Magic Claw has published LOLAPI, a catalog of legitimate system APIs weaponized for cyberattacks. The catalog also includes detection strategies and known malware and groups abusing the technique.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the recent Russian attack on Polish electricity infrastructure.
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about the Pall Mall Process, an international effort to reign in abusive spyware. The pair also discuss news that Chinese Salt Typhoon hackers compromised the calls of senior UK officials in Downing Street.
