Risky Bulletin Newsletter
June 13, 2025
Risky Bulletin: Predator spyware alive despite US sanctions
Written by

News Editor
This newsletter is brought to you by Push Security . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
Despite being sanctioned twice by the US Treasury Department last year, surveillance and spyware maker Intellexa has continued to operate and has even set up new server infrastructure for its customers.
In a report published on Thursday, security firm Recorded Future says it identified new customer- and victim-facing infrastructure, along with new systems to avoid detection.
The new infrastructure includes servers and domains for hosting and delivering the Predator mobile spyware, as well as VPS servers for anonymizing traffic and hosting management panels for Intellexa customers.
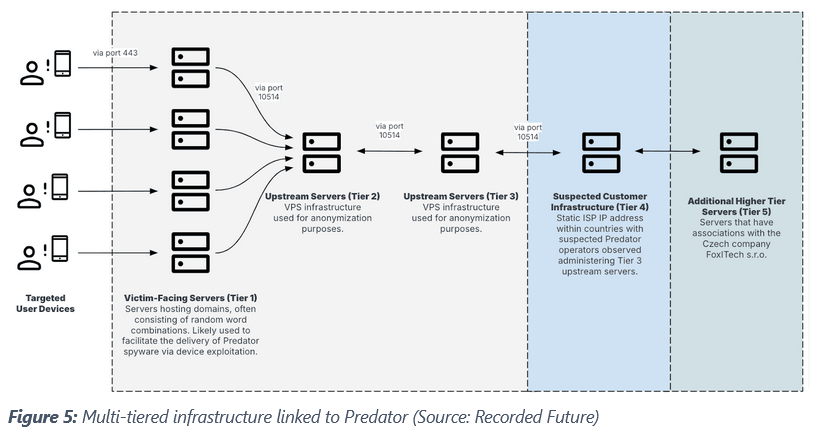
Predator infrastructure is now live in almost all previous countries where it's been active over the past two years, but also Mozambique, which appears to be a new customer after using the NSO's Pegasus spyware in previous years.
Half of the Intellexa customers are now based on the African continent, where spyware abuse has become rampant, especially against political rivals.
There is also a new active Predator cluster in an unnamed Eastern European country, but researchers aren't sure if it's a live system or just basic "testing and development operations."
Predator infrastructure goes up and down on a regular basis, similar to cybercrime operations. Servers and domains get exposed, Intellexa takes them down , and new infrastructure pops up online a few months later.
The Recorded Future report also confirmed that parts of the new Predator infrastructure are connected to a Czech company named FoxITech, which Czech news outlet VSquare first connected to Intellexa in an article last October.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Yes24 ransomware attack: A ransomware attack is disrupting the operations of South Korean online bookstore Yes24 . The company's online store and e-book platform have been down since Monday . Yes24's event ticketing system was also affected, which forced companies and the music industry to cancel events and concerts this week. No ransomware group has taken credit for the attack. [ Additional coverage in the Korea Herald ]
Ransomware hits Maine hospitals: A ransomware attack is disrupting services at at least five hospitals across the US state of Maine. The attack took place two weeks ago, at the end of May, and hospitals have yet to fully recover. Several patients have had tests and surgeries rescheduled due to IT issues. The incident is linked to Covenant Health and has also impacted some hospitals in New Hampshire. [ Additional coverage in WGME ]
RCMP breach: The Royal Canadian Mounted Police lost a sensitive USB key that contained information on informants, victims, witnesses, and its own employees. The device was unencrypted and was later copied and sold by criminal groups. The incident took place in March 2022 and impacted more than 1,700 individuals, according to Canada's privacy watchdog . [ Additional coverage in the CBC ]
New Paragon victims: Two European journalists had their iPhones hacked with Paragon Solutions' Graphite spyware. Victims include Italian journalist Ciro Pellegrino and an unnamed prominent European journalist. CitizenLab traced the infections to the same Paragon operator—which is very likely the Italian government. The attacks also involved a zero-click iOS iMessage zero-day ( CVE-2025-43200 ) that Apple patched in February.
Hack costs Victoria's Secret $10mil: Victoria's Secret expects to lose $10 million from its Q2 operating income due to a security breach that took down systems during Memorial Day. [ Additional coverage in RetailDive ]
China spies on Airbus: An Intelligence Online report claims that a small Chinese telecommunications company deployed an unauthorized antenna near Airbus sites in an apparent attempt to spy on Airbus and French satellites.
DDoS attack hit Sweden: Swedish Prime Minister Ulf Kristersson says the country's institutions have been under DDoS attacks for the past three days. [ Additional coverage in Euractiv ]
New Russian Railways DDoS attack: Ukrainian hackers have launched another DDoS attack against the websites of Russian Railways. They launched a similar attack last week .
Ukrainian hackers apparently launched another DDoS attack today at Russian Railways' website and mobile app. Ticket sales and terminals are reportedly still online, but customers are warned to anticipate possible service disruptions. t.me/telerzd/6615
— Kevin Rothrock (@kevinrothrock.me) 2025-06-12T13:08:15.346Z
General tech and privacy
Govts should launch period tracking apps: Public health bodies should launch their own period tracking apps as an alternative to commercial products. Academics from Cambridge University say that women are providing a "gold mine" of private information to private companies. Researchers warn that their data can be resold and weaponized against them for job discrimination and workplace monitoring. The same data can also be used to limit access to abortion, health insurance discrimination, and even cyberstalking.
Privacy groups protest against STOP CSAM Act: Multiple privacy groups wrote an open letter to US government officials about the STOP CSAM Act, the latest effort from US government officials to backdoor online encrypted services.
Meta sues nudify app maker: Meta has filed a lawsuit against the developer of the CrushAI nudify app. The company says CrushAI used Facebook and Instagram ads to drive traffic to the app—against its advertising terms of service. The app is developed by Hong Kong company Joy Timeline HK and allows users to create nude images out of regular photos.
Massive internet outage: A Google Cloud Platform outage managed to bring down a large part of internet services across North America on Thursday. [ Additional coverage in The Verge ]
One billion GitHub repos: GitHub celebrated this week the creation of its one billionth repository. It is named " shit ."
The 1 billionth GitHub repository has been created and it’s absolutely perfect.
— Christina Warren (@filmgirl.bsky.social) 2025-06-11T21:26:36.328Z
Government, politics, and policy
OAGs sue 23andMe: Twenty - seven states and the District of Columbia have sued genetic testing company 23andMe. The company filed for bankruptcy in March after a devastating hack in late 2023 and is preparing to sell its assets. The lawsuit seeks to block the sale of customer genetic data and prevent it from being misused by unknown parties. Fifteen percent of 23andMe users have already requested the company delete their data.
Dems ask GAO to look at NVD and CVE: Two Democrat Senators have asked the US GAO to look at the effectiveness of the CVE and NVD programs. [ Additional coverage in CyberScoop ]
Another CISA leadership departure: CISA Executive Director Bridget Bean has retired from the agency after three years. She is one of the tens of CISA leadership figures to depart the agency in the turmoil of DOGE cuts and White House pressure. [ Additional coverage in NextGov ]
Europol complains about E2EE again: The use of end-to-end encrypted apps has become an increasingly important obstacle to Europol investigations. The agency says that short metadata retention periods for E2EE apps are also impacting its ability to map out criminal networks. This is the third year in a row that Europol has highlighted the broad adoption of encrypted apps as a major barrier to its investigations, the agency said in its yearly organized crime report .
CNIL draft targets email tracking pixels: France's privacy watchdog is exploring the possibility of adding a consent mechanism to email tracking pixel technologies.
Danish ministry to adopt LibreOffice: The Danish Ministry of Digitalization will phase out Microsoft Office in favor of LibreOffice. The ministry plans to move all staff to open-source software by the end of the year. Denmark's largest cities, Copenhagen and Aarhus, have also announced plans to phase out Microsoft software and cloud services earlier this year. The move comes after the Trump administration ordered US intelligence agencies to step up spying on Greenland and Danish citizens. [ Additional coverage in The Local DK ]
Many more EU countries should be doing this. 👌
— Martin Ségur-Cabanac (@martinsegur.com) 2025-06-12T12:09:39.296Z
Sponsor section
In this sponsored interview, Casey Ellis interviews Push Security co-founder and Chief Product Officer Jacques Louw about how good phishing crews have gotten at evading detection. Attackers are hiding their payloads behind legitimate bot-detection tools to stop things like email security gateways from seeing them, as well as locking up phishing pages behind OAuth challenges. Push sees all this because it's installed as a browser plugin and sees what users see.
Arrests, cybercrime, and threat intel
Dutch police identify Cracked.io users: Dutch police have identified and contacted 126 individuals who had accounts on the Cracked.io hacking forum. Authorities filed criminal cases against eight suspects and warned the rest about engaging in further criminal activity. The youngest person contacted by authorities was 11 years old. Law enforcement agencies from the US and Europe seized Cracked and Nulled in January. The forum had over 4.7 million users and was known for selling hacking services, stolen data, and malware.
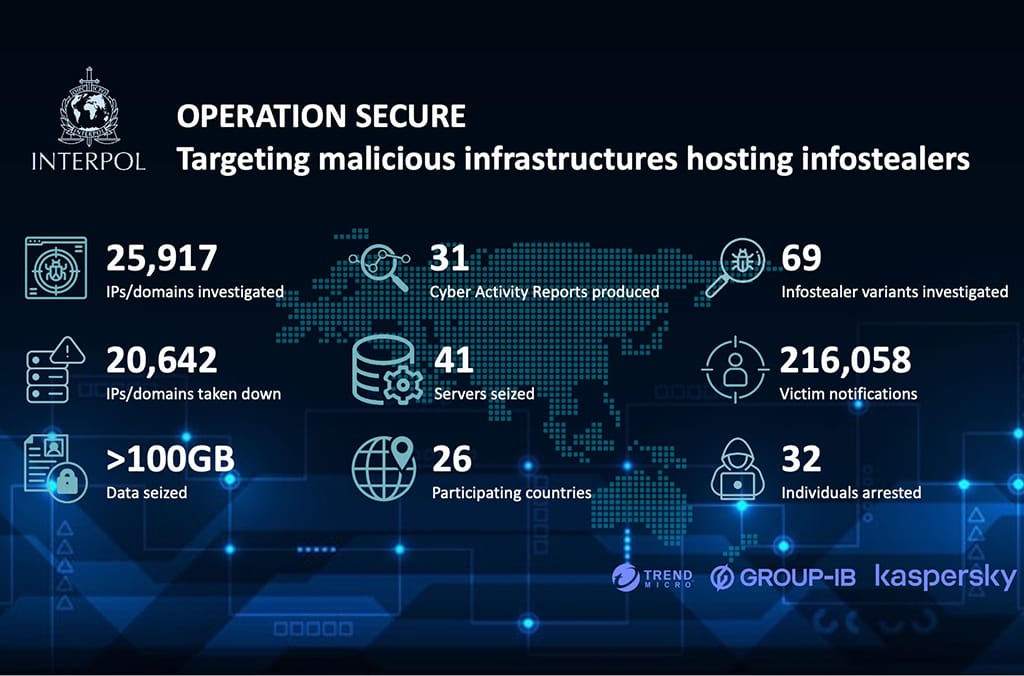
Interpol Operation Secure: Interpol and law enforcement agencies from 26 countries have seized infrastructure linked to infostealer operations. Authorities seized over 40 servers, more than 20,000 domains and IP addresses, and arrested 32 individuals. More than half of the suspects were detained in Vietnam. According to Group-IB , the seized servers were linked to Lumma, RisePro, and META Stealer infrastructure.
Scammers detained across SE Asia: Law enforcement agencies across Southeast Asia have arrested 1,800 suspects linked to cyber scam operations. The group was linked to different online scams that stole over $225 million from victims. Nine countries took part in an operation that spanned over a month.
Turkiye detains 400+ on cybercrime charges: Turkish law enforcement detained 423 suspects on cybercrime charges following raids across 29 provinces. The suspects ran phishing operations that accessed bank accounts to steal money or place online bets. Some suspects were also linked to crypto and investment scams. 145 are still under arrest, while another 128 were released on judicial review. Authorities also confiscated assets worth over $125 million from the suspects.
Sextortionist pleads guilty: A Nigerian national has pleaded guilty in the US to charges related to a sextortion scheme that led to the death of a Pennsylvania 20-year-old. Samuel Olasunkanmi Abiodun is one of three Nigerians charged with the harassment and death of Jack Sullivan in January 2023. Sullivan paid the group $3,000 but took his own life after they demanded more money.
Proxy provider linked to DDoS attacks: Qurium researchers have linked recent DDoS attacks against Peruvian and Venezuelan independent news outlets to the network of a proxy provider. Attacks were linked to a shadowy service named Packet Express that operates tens of thousands of IP addresses. Server provider Peg Tech shut down Packet Express' infrastructure but refused to provide details about its operators.
VexTrio and HelpTDS: Infoblox has linked the new HelpTDS traffic redirection service to the VexTrio threat actor.
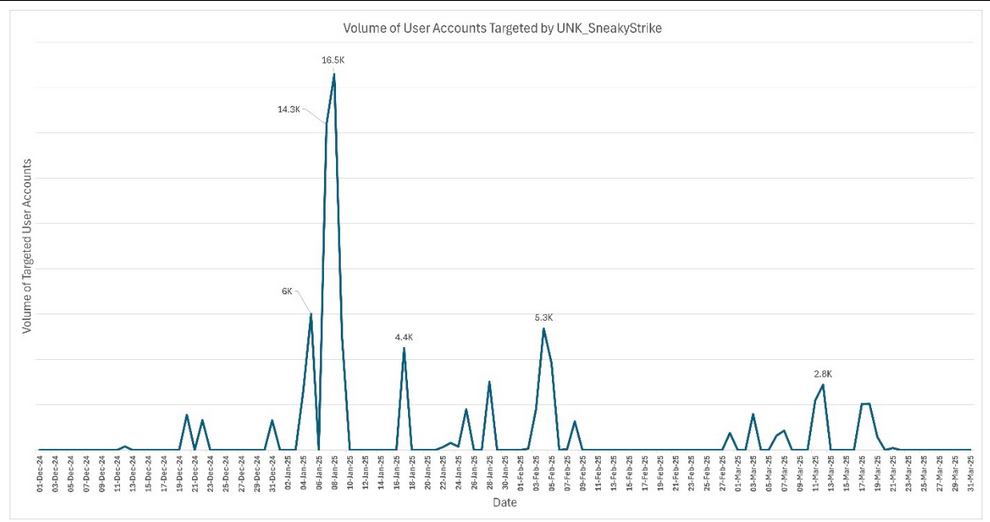
UNK_SneakyStrike targets Entra accounts: A new hacking group has abused an open-source tool to take over Microsoft Entra ID accounts. The attacks started in December of last year and targeted over 80,000 accounts at hundreds of organizations. Attackers used TeamFiltration , a tool to enumerate Entra ID accounts and launch password-spraying attacks. Proofpoint tracks the attackers as UNK_SneakyStrike .
ConnectWise rotates certs over security: Remote management platform ConnectWise will rotate its code-signing certificates due to security concerns after an APT breached its network earlier this year. The company says these two events are not related but just a precaution.
Discord invite link abuse: Check Point has spotted a threat actor re-registering expired or deleted Discord invite links as custom vanity invite URLs in order to hijack users and redirect them to malware.
JSFuck abuse: PAN's Unit42 looks at how threat actors are abusing the JSFuck obfuscation algorithm to hide malicious code.
AitM phishing kits landscape: Sekoia has published a report looking at the AitM phishing kit landscape, its evolution, and today's largest providers.
DPRK-linked malicious npm package: Aikido Security has spotted a new malicious npm package targeting the Web3 crypto community that appears to be linked to North Korean hacking operations.
New ransomware gangs: Three new ransomware operations, named Teamxxx, Warlock, and Walocker, have been spotted leaking data on the dark web.
Malware technical reports
CyberEye (TelegramRAT) builder: CyFirma looks at the builder for a remote access trojan known as CyberEye, or TelegramRAT.
BrowserVenom malware: Kaspersky has published a report on BrowserVenom , a new malware strain that reconfigures all browsing instances to force traffic through a proxy controlled by the threat actors. The malware is currently distributed via malicious websites posing as the DeepSeek homepage.
Pickai backdoor: Chinese security firm QiAnXin has sinkholed a domain linked to the new Pickai backdoor and found over 700 victims. The malware was deployed on Linux systems using zero-days in ComfyUI, an app for managing genAI models. No CVEs in the report, though.
Myth Stealer: Trellix looks at Myth Stealer , a Rust-based infostealer that launched in December of last year and is offered through a MaaS model.
Fog ransomware: Broadcom's Symantec security team has published a report on the intrusion toolsets used by the Fog ransomware .
Sponsor section
In this on-demand webinar , Push Security VP of R&D Luke Jennings walks you through the common TTPs used by the Scattered Spider group this year and how you can defend against them.
APTs, cyber-espionage, and info-ops
China's Defense-Through-Offense approach: Eugenio Benincasa, writing for Natto Thoughts , looks at how Chinese authorities have adopted a Defense-Through-Offense approach, also known as Defend Forward, to cyber operations.
To defend, one must first know how to attack” (未知攻,焉知防). This mindset, popularized by a Taiwanese hacker Lin in the 1990s, spread from China's red hackers to CTF teams. Today, it powers China's cyber industry. New piece for @nattothoughts.bsky.social nattothoughts.substack.com/p/defense-th...
— Eugenio Benincasa (@euben.bsky.social) 2025-06-11T16:17:19.072Z
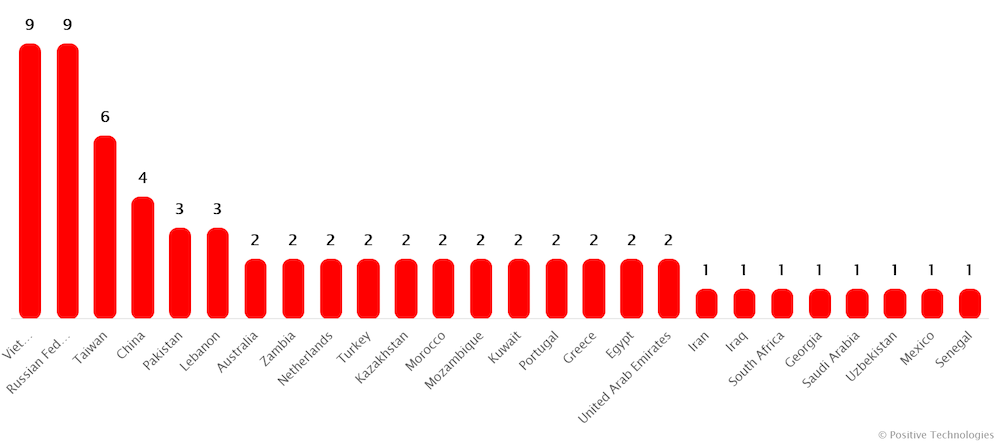
Exchange espionage campaign: A mysterious hacking group has deployed keyloggers on the login pages of Exchange servers. Security firm Positive Technologies has identified 65 victims across 26 countries, with a third being government systems. The hackers are using the ProxyShell vulnerability to take over systems and deploy a keylogger that collects user logins. The attacks are believed to be espionage related.
Vulnerabilities, security research, and bug bounty
EchoLeak Copilot vulnerability: Researchers have discovered a vulnerability in the Microsoft 365 Copilot AI assistant that can leak data from user inboxes. The attack, named EchoLeak ( CVE-2025-32711 ), requires no user interaction. Attackers only have to send an email to a targeted account with hidden prompts. The exploit runs when users ask Copilot to perform a task on their inbox.
Prompt injection means email viruses are back. A researcher found a security vulnerability where you send an email with hidden instructions which when CoPilot scans the email, executes and then hides the source of the instructions. It took Microsoft 5 months to fix the issue.
— Dare Obasanjo (@carnage4life.bsky.social) 2025-06-11T19:03:00.258Z
TokenBreak attack: AI security firm HiddenLayer presents TokenBreak , a new attack to bypass security protections in some LLMs.
"The root cause lies in the tokenizer. Models using BPE (Byte Pair Encoding) or WordPiece tokenization strategies were found to be vulnerable, while those using Unigram were not."
Heroes V exploit: Synacktiv has published a write-up on an exploit in Ubisoft's Heroes of Might and Magic V 2006 game.
Mitel PoCs: InfoGuard Labs has released PoCs for two Mitel unauth vulnerabilities.
Thunderbird patches bug that leaked Windows credentials: Mozilla has patched a security flaw in the Thunderbird email client that could have been abused to leak Windows credentials. The vulnerability was in the way Thunderbird managed mailbox:/// links. Mozilla says attackers could have used emails with malicious mailbox:/// links that would leak NTLM hashes to an attacker's SMB server. The bug could also save malicious files to disk or fill a user's hard drive with garbage content even if the auto-download setting was disabled.
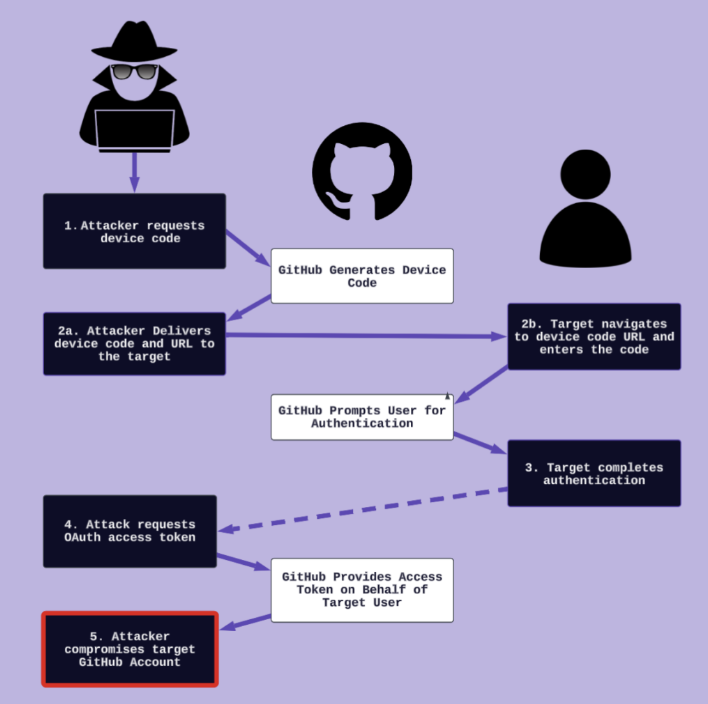
GitHub Device Code Phishing: Praetorian researchers warned against device code phishing attacks that can target and hijack GitHub accounts, complete with some real-life case studies from their own work.
GitLab security update: GitLab has released security updates for ten vulnerabilities.
PAN and Trend Micro security updates: Security firms Palo Alto Networks and Trend Micro have released security updates.
Salesforce write-up: AppOmni Chieef of SaaS Security Aaron Costello has published a technical write-up on five bugs he discovered in Salesforce products that the company patched this week.
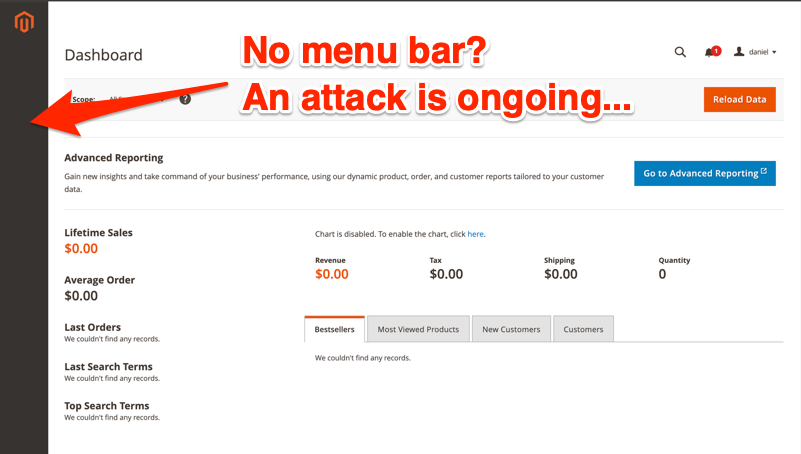
Major Magento bug warning: Adobe has urged customers to install a critical Magento security update by the end of the week. The company expects the bug (CVE-2025-47110) to come under active exploitation. According to security firm Sansec , the bug is a cache poisoning and XSS exploit that lets attackers replace the admin menu with malicious code.
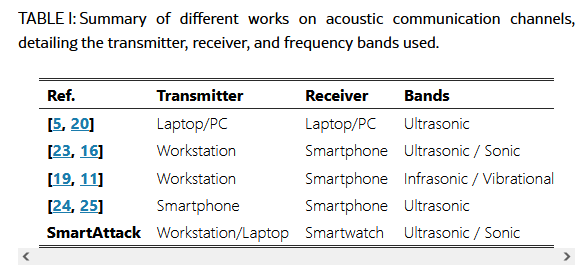
SmartAttack technique abuses smartwatches: For the past decade, academics have explored ways of exfiltrating data from air-gapped systems using laptops, desktops, and smartphones as the receivers in those attacks. New research looks at the possibility of using smartwatches instead.
"We present and evaluate SmartAttack, an attack method that exploits the built-in microphones of smartwatches to receive and decode ultrasonic signals in the 18–22 kHz frequency range. Through extensive experimentation, we demonstrate that this attack can successfully transmit data over distances exceeding 6 meters, achieving data rates of up to 50 bits per second."
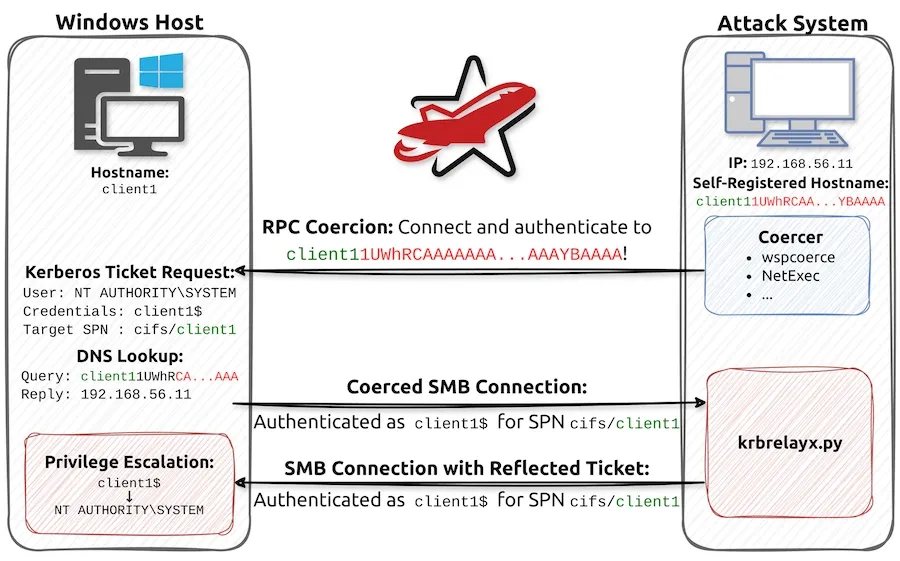
New NTLM reflection attack: RedTeam Pentesting , Synacktiv , and SySS have published technical analyses of CVE-2025-33073 , a new way to execute NTLM reflection attacks. This was fixed in this month's Patch Tuesday and also works against Kerberos.
Infosec industry
Acquisition news: Security firm and SIEM provider Securonix has acquired threat intel platform ThreatQuotient.
New NIST guidance: US NIST has published new guidance with 19 new examples on how to build zero trust architectures using off-the-shelf commercial technologies.
Stryker goes free: The Stryker mobile pen-testing app is now free . Learn how to use it from Lukas Stefanko , an expert in Android malware and reverse engineering.
New tool—Apple Container: Apple has released the source code of its new Container feature that lets macOS users run Linux container images on their OS.
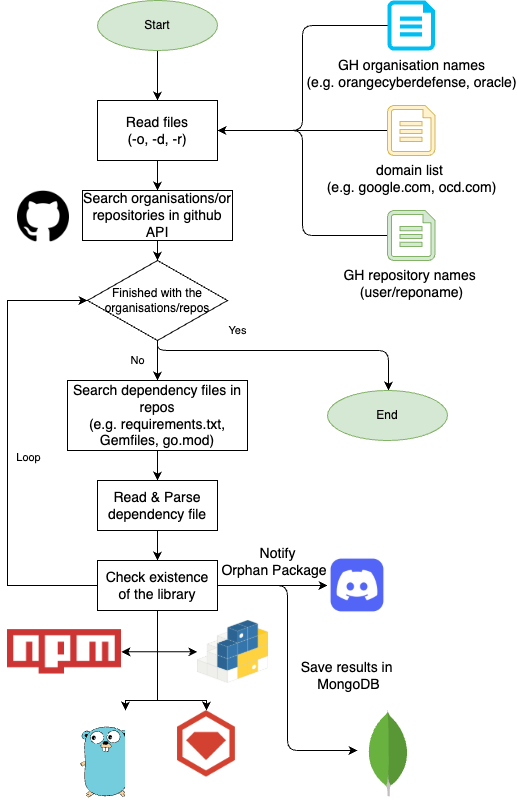
New tool—Depscanner: Orange's security team has released Depscanner , a tool to detect dependency confusion attacks by scanning public repository dependencies in an org's GitHub projects that have orphan libraries in their dependencies.
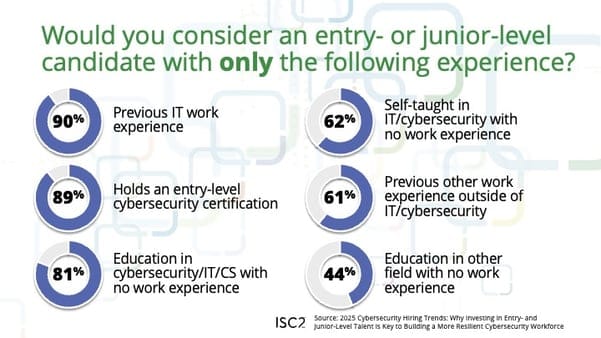
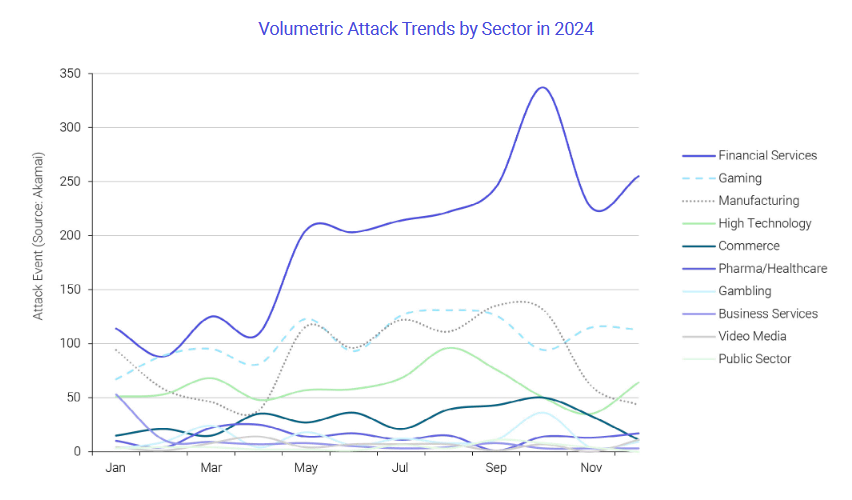
Threat/trend reports: Abnormal AI , Europol , FS-ISAC , ISC2 , the OPCC , Radware [ PDF ], and Veracode have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Seriously Risky Business , Tom Uren and Patrick Gray talk about how a Trump executive order has scaled back the government's cyber security ambitions. They also discuss North Korea's use of AI in its IT worker scam and the emergence of espionage-as-a-service... perhaps.
In this edition of Between Two Nerds , Tom Uren and The Grugq take a deep dive into the hackers of Unit 29155, Russian military intelligence's sabotage and assassination group.
