Risky Bulletin Newsletter
June 04, 2025
Risky Bulletin: Security firms will attempt to clean up their own mess—APT name taxonomies
Written by

News Editor
This newsletter is brought to you by asset inventory and network visibility company runZero . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
Four of today's biggest cybersecurity firms— Microsoft , CrowdStrike , Google, and Palo Alto Networks —have announced an initiative to deconflict and harmonize APT naming schemes.
The companies will publish documents on how each of their own APT names maps out to the other.
So far, CrowdStrike and Microsoft have released images, JSON, and Excel files on how their own APT names overlap with their competitors.
The companies don't plan on developing and enforcing a universal APT nomenclature since that will be virtually impossible due to the infosec ecosystem's fragmentation.
The general idea behind this initiative is to make it easier for cybersecurity companies, independent security researchers, and other third parties to track APT activity.
Personally, I don't understand how that's gonna happen in a real-world scenario. Infosec companies tend to hoard IOCs and keep such information private as much as possible, which they then use to advertise and boast about their products' ability to spot activity that rivals don't see.
Tracking APT activity and assigning names to threat actors is a process heavily intertwined with IOC analysis.
Unless companies are willing to share more information prior to releasing reports or marketing material, we're still gonna have security firms giving the same group 293836472364863483264736 names and dealing with the deconfliction later.
As Yarden Shafir eloquently put it on Twitter earlier this week, this initiative is basically a chart drawing lines between different names.
Something like this has existed for over a decade but in an unofficial manner. A notorious Google spreadsheet that has been in the bookmarks of every infosec researcher and reporter I know.
It's nice that we now have something akin to that, but vetted by the security vendors themselves. What I would like is for more vendors to join in and publish similar charts/maps and then have all of it aggregated in one place so it's easier to check.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
NorthFace credential stuffing attack: Sports apparel maker NorthFace says its website was the victim of a credential stuffing attack on April 23.
Cartier data breach: A hacker has stolen customer data from luxury fashion house Cartier. The company has notified users about the breach this week. Stolen data includes names, emails, and the user's country. Cartier is the fifth major fashion brand to disclose a breach over the past month after Christian Dior, Tiffany's, Victoria's Secret, and Adidas. [ Additional coverage in BleepingComputer ]
Jabaroot hacks Morocco cadastre service: Algerian hacking group Jabaroot has hacked Morocco's land and property service and stolen its database. The group released over 10,000 files on Telegram claiming to contain real estate transactions by Moroccan public figures. The same group also hacked Morocco's social security database in April. At the time, Moroccan officials accused the group of releasing tampered and misleading documents. [ Additional coverage in Morocco World News ] [ h/t Adil Matrix ]
Hacker wipes KiranaPro servers: A hacker has wiped the servers of Indian grocery delivery startup KiranaPro. The hacker deleted the company's customer data along with the source code of its mobile app. The app is still online but can't process any new payments. According to TechCrunch , the hack originated from a former employee's account.
M&S breach aftermath woes: UK retail chain Marks & Spencer is holding walk-in recruitment days to hire new staff after a ransomware attack brought down its HR platform in April. The company posted Facebook ads telling anyone who wants a job to visit one of its stores. Marks & Spencer expects the disruption to its online platforms to last at least until July. [ Additional coverage in The Grocer ] [ h/t Kevin Beaumont ]
Vanta data breach: Business compliance company Vanta said that a bug in its platform exposed the data of around 4% of its customers to other customers. [ Additional coverage in TechCrunch ]
Hackers breach Malay Minister's WhatsApp account: An unidentified hacker has broken into the WhatsApp account of Malaysia's home minister and sent malicious links to his contacts. The incident took place at the end of May, and none of his contacts clicked the links. The incident is still under investigation by authorities. [ Additional coverage in NasionalDaily /English coverage in The Record ]
BitoPro crypto-heist: A hacker has stolen $11.5 million worth of cryptocurrency from Taiwanese crypto exchange BitoPro. The hack took place last month, on May 8, and was only now disclosed. The funds have already been laundered through services such as Tornado Cash and Thorchain. [ Additional coverage in CCN ]
Force Bridge crypto-heist: Hackers have stolen $3.7 million worth of crypto-assets from crosschain platform Force Bridge. According to blockchain security firm HashEx , the attackers exploited weak access control mechanisms to bypass bridge protections. They then spoofed transactions to manipulate the bridge and drain assets.
Coinbase breach linked to TaskUs: A Reuters report linked a recently disclosed Coinbase breach to an Indian woman working for US outsourcing company TaskUs. The suspect allegedly took photos of their work computer and shared them with hackers for bribes.
General tech and privacy
Firefox adds crypto-drainer detection: Mozilla has added a new security system to the Firefox add-on portal that detects extensions with malicious code designed to empty crypto wallets.
IPv4 exodus from Ukraine: Kentik looks at how a large part of Ukraine's IPv4 address space is now announced via Western ISPs and cloud providers.
FTC wild goose hunt: Under a Trump and Musk-controlled government, the FTC is now " investigating " if online advertisers "coordinated" a boycott of Twitter at a time when Musk unbanned all old accounts and the site was starting to get flooded with death threats, scam bots, and info-op troll networks. Because advertisers needed "coordination" to run away from a dumpster fire, apparently.
Old enough to remember when MAGAville was furious that the government was trying to pressure private companies. This is pure jawboning/chilling effects trying to create a "cost" for advertisers choosing not to advertise on X.
— Mike Masnick (@mmasnick.bsky.social) 2025-06-02T23:19:02.088Z
Vodafone gets historic fine: Germany's data protection agency has fined Vodafone a whopping €45 million due to malicious modifications of customer contracts. Per Bloomberg , the company cooperated with authorities and has already paid the fine.
PornHub pulls out of France: PornHub and all affiliated companies will stop serving adult content in France after the government has introduced a mandatory age verification requirement. [ Additional coverage in Politico ]
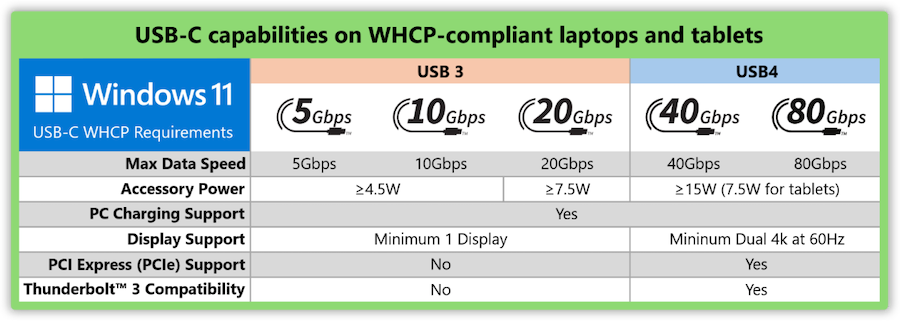
New Microsoft USB-C standards: Microsoft has published a set of minimum "quality" standards for USB-C ports that will ship with Windows 11 laptops. Companies who want to obtain a WHCP seal/label for their devices will have to ship USB-C ports that follow Microsoft's minimum standards. The company says it is imposing these new requirements after many vendors sell laptops with USB-C ports that don't support the full spectrum of USB-C features, with low transfer speeds, no charging support, no Thunderbolt compatibility, and other issues.
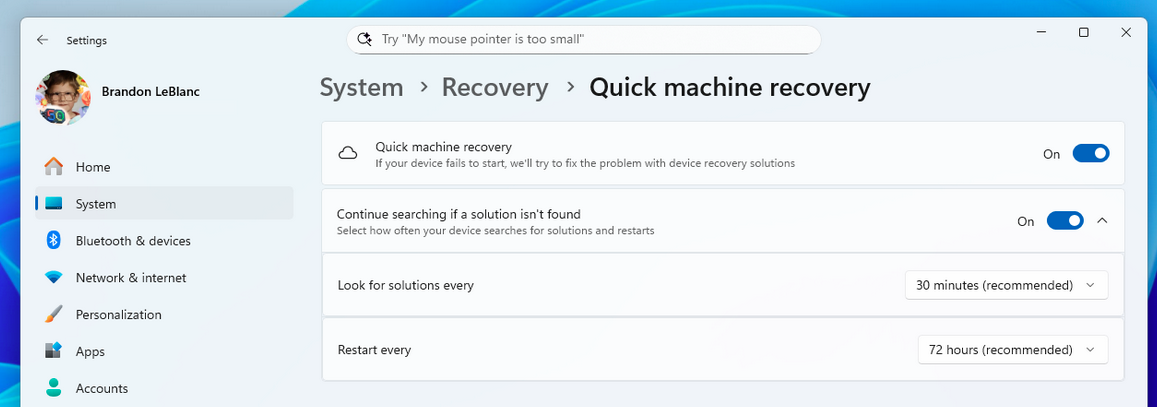
Microsoft tests Quick Machine Recovery: Microsoft has started testing a new feature named Quick Machine Recovery. The feature is a new setting that (once enabled) will allow the OS to look and retrieve solutions for boot issues directly from Microsoft servers. Microsoft developed the feature following the CrowdStrike outage last year. It is currently undergoing limited testing in Windows 11 beta and insider preview builds.
Government, politics, and policy
New US DCDC: The Pentagon has reorganized CyberCom's defensive joint force (JFHQ-DODIN) into a sub-command structure named the Department of Defense Cyber Defense Command (DCDC). [ Additional coverage in DefenseScoop ]
CISA cuts: According to a new version of the US spending bill proposal, CISA now stands to lose $420 million in funding for next year and another 1,000 staff. All of this is still subject to negotiations and changes. [ Additional coverage in NextGov ]
"According to a detailed budget supplement released Friday evening, CISA's projected workforce would drop from 3,292 employees to 2,324 for the 2026 fiscal year, which starts at the end of September. The agency's operational funding obligations would also fall by more than $420 million, from $2.38 billion to $1.96 billion, and a separate agency budget justification document shows its total funding would drop some $495 million."
Trump cyber nominees get industry support: Two cybersecurity coalitions have expressed public support for Sean Plankey and Sean Cairncross, Donald Trump's nominees for CISA Director and National Cyber Director, respectively. [ Additional coverage in CybersecurityDive ]
EMR-ISAC shuts down: An organization providing cybersecurity assistance to emergency services has shut down at the end of May. The Emergency Management and Response - Information Sharing and Analysis Center (EMR-ISAC) ceased operations after CISA cut funding earlier this year. The group provided cybersecurity assistance to fire departments, police stations, bomb squads, ambulance services, search and rescue teams, and other emergency service operators. EMR-ISAC is one of the several ISAC teams that have shut down following CISA funding cuts this year. [ Additional coverage in DarkReading ]
North Dakota has data breach notification requirements: The North Dakota government passed a new bill that introduces new cybersecurity and breach notification requirements. The law enters into effect on August 1 and applies to financial corporations but excludes banks and credit unions. Under the new law, companies must notify the state within 45 days if a security breach impacts more than 500 residents. Companies must also implement cybersecurity programs, run period risk assessments, and hire professionals to oversee these programs. [ Additional coverage in DataBreaches.net ]
Top FBI cyber official leaves: FBI Cyber Division Deputy Assistant Director Cynthia Kaiser is leaving the agency for the private sector, taking a job at security firm Halycon. She previously served with the agency for 20 years and was heavily involved in ransomware takedowns. [ Additional coverage in NextGov ]
Oppressive states rejoice: Twelve of the world's loveliest oppressive and authoritarian states have signed a joint statement praising the adoption of a recent UN cybercrime convention. Signatories include Russia, Belarus, Burkina Faso, Cuba, North Korea, Egypt, Iran, Iraq, Kyrgyzstan, Laos, Nicaragua, and Venezuela. [ Additional coverage in Granma /English coverage in CiberCuba ] [ h/t Andy Jabbour ]
Legion of Doom, unite! The anti-Five Eyes. Cuba signs cybersecurity agreement with Russia, Iran, Venezuela, Nicaragua, and North Korea en.cibercuba.com/noticias/202... #cybersecurity @gate15.bsky.social
— andy jabbour (@andyjabbour.bsky.social) 2025-06-03T12:46:03.705Z
Sponsor section
In this sponsored interview, Risky Business Media's brand new interviewer, Casey Ellis, chats with runZero founder and CEO HD Moore about why vuln scanning tech is awful and broken. He also talks about how they're trying to do something better by gluing their own discovery product to the nuclei open-source vulnerability scanner.
Arrests, cybercrime, and threat intel
22 sextortionists detained in Nigeria: Nigerian authorities have arrested 22 suspects linked to a sextortion campaign across the globe. The suspects were detained following a joint investigation between Australian and Canadian police. The group has been linked to at least one suicide, a 16-year-old child in New South Wales in 2023.

US govt swatter pleads guilty: A Romanian man who swatted multiple US senior government officials has pleaded guilty in a DC court. Thomasz Szabo, 26, was the moderator of an online chatroom called Shenanigans. He worked with members of the community to harass individuals with fake bomb threats and police swattings. In late 2023, Szabo was involved in a large-scale campaign that targeted multiple US government officials. Victims included high-ranking figures such as a former US president, members of Congress, state governors, federal officials, and members of US law enforcement agencies. Szabo and a Serbian national were identified and arrested last September after using Google Voice to place the swatting calls.
Europol takes down online propaganda: Europol says it took down more than 2,000 links promoting jihadist and right-wing violent extremist and terrorist propaganda. Officials say the content targeted children for future radicalization.
NSO asks for new trial: Israeli spyware maker NSO Group has filed an appeal in its WhatsApp lawsuit and is demanding reduced damages or a new trial. The company called the damages outrageous, blatantly unlawful, and unconstitutionally excessive. A judge awarded Meta last month $167 million in damages after an NSO-developed exploit was used to hack 1,400 WhatsApp users. [ Additional coverage in TechCrunch ]
JINX-0132 targets DevOps servers: A new threat actor named JINX-0132 has launched a large-scale operation to breach DevOps infrastructure and deploy cryptocurrency miners. The attacks have targeted technologies such as Consul, Docker, Gitea, and Nomad. Wiz says this campaign marks the first publicly documented instance of Nomad servers being exploited in the wild.
Russian Market profile: ReliaQuest has published a profile on the Russian Market , an underground shop where threat actors sell stolen credentials obtained through infostealer infections. The site looks to become the go-to stealer shop after the takedown of the Genesis and LummaStealer markets.
Malicious Ruby libraries: Socket Security has discovered two malicious Ruby libraries designed to intercept traffic to the Telegram API. The two plugins are marketed as Telegram proxies built on the FastLane app automation service. Socket researchers believe the plugins were created to target developers in Vietnam, where authorities recently announced a nationwide block of the Telegram service.
Malicious npm packages: And because it's another day that ends in "day," security researchers have also found malicious npm packages , these ones targeting BSC and Ethereum developers.
Another ClickFix campaign: A malvertising campaign using the Booking.com brand is redirecting users to ClickFix sites that try to infect them with the AsyncRAT malware, per Malwarebytes .
Toll phishing scams evolve: Spamhaus says that recent toll road phishing spam campaigns have evolved from impersonating local toll site operators to impersonating the DMV itself.
Akira chats and negotiations are not private: Threat intelligence analyst Marco A. De Felice has published two reports of instances where the Akira ransomware failed to protect victims who paid the ransom, who didn't realize anyone could read those conversations if they knew where to look. [ h/t DataBreaches.net ]
Hedera NFT scam: The FBI says that scammers used free NFT rewards to scam Hedera users out of their funds.
Malware technical reports
HuluCaptcha framework: Security researcher Gi7w0rm looks at a toolkit named HuluCaptcha that helps threat actors deploy fake CAPTCHA screens for ClickFix attacks.
BPFDoor: Security researcher HaxRob has published a two - part technical analysis of BPFDoor, a malware strain that targets Linux and has been linked to some past APT activity. The report also covers recent versions of the malware spotted this year.
Lazarus OtterCookie: ANY.RUN has published a technical analysis of OtterCookie , an infostealer used by the Lazarus APT.
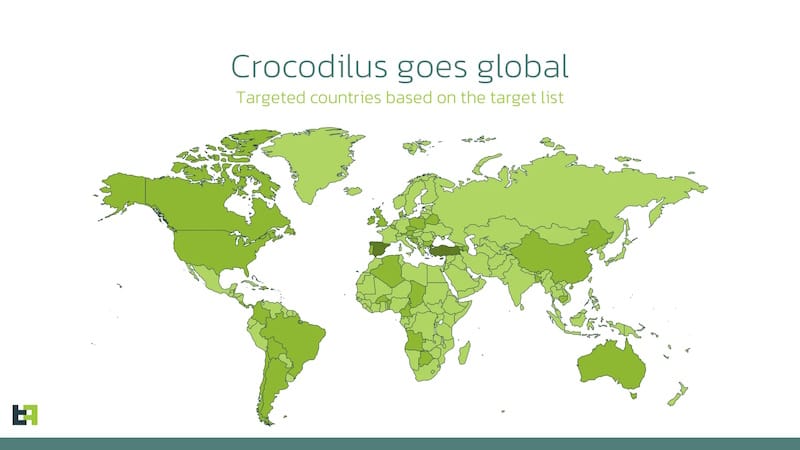
Crocodilus Android banking trojan expands globally: The Crocodilus Android malware is adding new contacts to a victim's address book to aid in social engineering attacks. The malware launched this year and is primarily distributed via malvertising campaigns. Its main role is to collect login credentials for mobile banking apps and extract seed phrases from crypto wallet apps. Initial attacks targeted banks in Spain and Turkey, but the malware has now expanded to target users all over the globe.
Sponsor section

APTs, cyber-espionage, and info-ops
STFD-686 spyware infects Syrian Army: Syrian Army officers and soldiers allegedly installed spyware on their Android devices. The spyware was hidden inside STFD-686, an app that promised financial aid for military members. The app claimed to be a project of the Syria Trust for Development, a humanitarian organization overseen by Bashar al-Assad's wife. It contained a version of the SpyMax remote access trojan that allowed attackers to track the movement of Syrian soldiers. The app was rolled out in June last year, five months before the Assad regime's collapse in December. [ Additional coverage in New Lines Magazine ]
UNC5792 targets Armenia: A Russian cyber-espionage group tracked as UNC5792 is using Signal to spear-phish individuals and organizations within Armenia's civil society and public sector.
PhantomCore: F6 researchers have discovered new campaigns linked to PhantomCore , an APT previously linked to Ukraine.
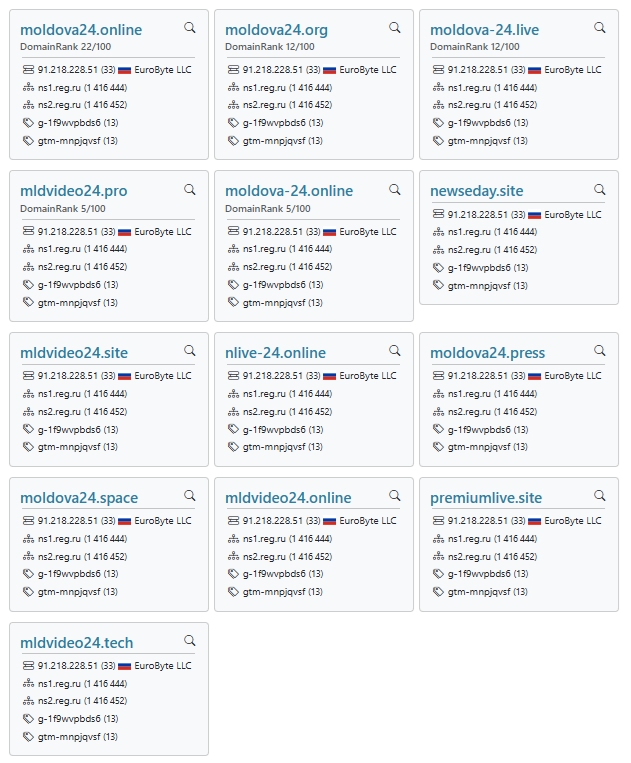
MD24 linked to Russia: DFRLab has linked a newly created Moldovan news site named Moldova24, or MD24 , to Russian server infrastructure and Russia's (sanctioned) state media RT and TV Novosti.
Vulnerabilities, security research, and bug bounty
Android Security Bulletin: Google has released the Android security updates for June 2025 .
Qualcomm zero-days: Chipmaker Qualcomm has released security updates to patch three zero-day vulnerabilities exploited in its Adreno GPU driver. The zero-days were discovered by Google's security team in attacks against Android smartphones. The patches have been made available to smartphone makers, and updates will be delivered to users in the coming weeks.
Chrome zero-day: Google has released a security update to patch an actively exploited Chrome zero-day. Tracked as CVE-2025-5419, the vulnerability is a memory corruption issue in the browser's V8 JavaScript engine. It was discovered by Google's own security team and is the third Chrome zero-day patched this year.
KEV update: CISA has updated its KEV database with five vulnerabilities that are currently exploited in the wild. They include two ASUS bugs, two CraftCMS ones, and a ConnectWise ScreenConnect zero-day.
Vulns in Ulefone and Krüger&Matz preinstalled apps: Poland's CERT has found vulnerabilities in apps preinstalled on Ulefone and Krüger&Matz smartphones. The vulnerabilities allow a local attacker to steal PIN codes or factory reset the device. They can also allow attackers to inject and run malicious code with system-level privileges.
Windows vuln PoC: Security researcher Mohammed Idrees Banyamer released a PoC for CVE-2025-30397 , an RCE in the Microsoft JScript scripting engine patched last month.
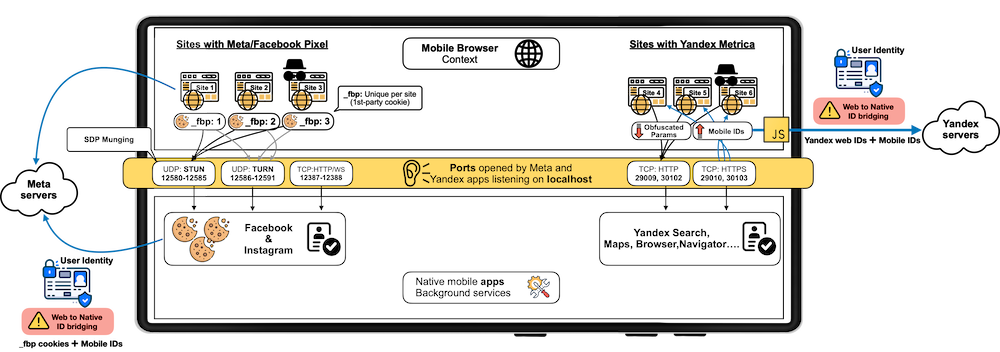
Meta and Yandex abuse localhost ports for tracking: Meta and Yandex have used a secret technique that abuses localhost ports to track mobile users as they navigate the web. Websites using the Meta Pixel and Yandex Metrica scripts open local ports on Android devices. Meta and Yandex apps running on the same device connect to these ports to receive information such as browsing metadata, cookies, and advertising IDs. Researchers have named the technique web-to-app ID sharing and say it bypasses privacy protections such as Incognito Mode, Android's permission controls, and clearing cookies. Meta stopped using the technique after it was disclosed by researchers. [ Additional coverage in ArsTechnica ]
Infosec industry
New tool—Delegations: The Manticore Project has released Delegations , a tool to work with all types of Kerberos delegations in AD.
New tool—Obfusk8: Security researcher x86byte has released Obfusk8 , an obfuscation library for C++17.
SentinelOne blames outage on software bug: SentinelOne said that a major outage of its infrastructure on May 29 was caused by a software bug in "an infrastructure control system that removed critical network routes."
Threat/trend reports: Abnormal AI , HUMAN Security , and PeckShield have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Between Two Nerds , Tom Uren and The Grugq look at the NSA's take on information warfare, all the way back from 1997.
In this edition of Seriously Risky Business , Tom Uren and Patrick Gray talk about Russian DanaBot malware developers making a tailored variant of their malware specifically for espionage. This fills in some of the blanks on the exact relationship between Russian criminals and the country's intelligence services.

