Risky Bulletin Newsletter
July 21, 2025
Risky Bulletin: SMS blasting incidents are rising
Written by

News Editor
This newsletter is brought to you by Thinkst , the makers of the much-loved Thinkst Canary . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
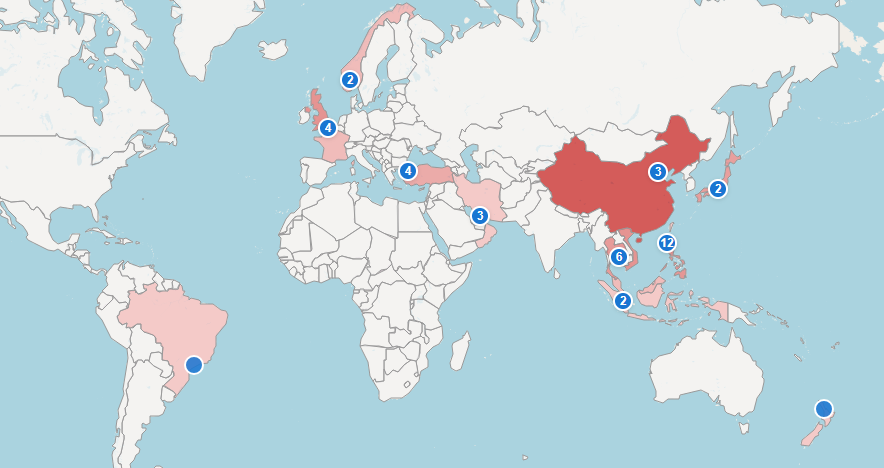
The number of public SMS blasting incidents has slowly increased over the past year, in a clear sign of a rising problem.
SMS blasters are devices that mimic a mobile base station to trick nearby phones into connecting to them. They are a variation of IMSI catchers ( aka cell-site simulators, fake base stations, or stingrays ), but instead of intercepting mobile traffic to snoop on a target and track their location, SMS blasters are designed to automatically send SMS messages to all users trapped in the fake base station's coverage.
The devices have been used to mass-spam mobile devices over the past decade, typically at organized events, such as concerts, political rallies, or other mass gatherings, and for silly marketing purposes.
They are portable. They can be put in a backpack or even inside a car, and then driven around for increased coverage of a specific zone, which makes them attractive for guerrilla marketing campaigns.
But with the rise of malicious SMS phishing (also known as smishing ), these devices have now become useful to a new category of users—namely, the cybercrime gangs and organized criminal cartels.
If you're the author of an infosec newsletter like me, or you swim and drown in cybersecurity news for other reasons, you've probably noticed that over the past year, maybe a year and a half, that news reports about incidents involving SMS blasters and adjacent arrests have slowly increased.
Just last week, a Chinese tourist was arrested in Oman for driving around the country's capital, Muscat, with an SMS blaster and sending messages that lured Omani citizens to a phishing page for a local bank.
In June, a Chinese student was sentenced to a year in prison for driving around London with an SMS blaster in the back of a Honda.

Also in June, Indonesian authorities arrested a man blasting SMS phishing texts across the country's capital, Jakarta.
In May, Japan's Ministry of Internal Affairs and Communications issued a public alert about the rise in smishing via fake base stations. The statement came three weeks after an internet sleuth discovered SMS blasters being driven around Tokyo and Osaka.
Also in May, Brazilian authorities dismantled an SMS blaster gang in Sao Paulo after a local telco reported interferences with the signal in the south of the city.
In April, Qatari authorities arrested 12 individuals for " SMS scams ." Photos released by authorities showed a device similar to the picture above, the SMS blaster used in London, suggesting this was another SMS blasting case.
The same month, Thai officials arrested two Chinese men for strolling through malls with an SMS blaster in a backpack .
Also in April, police in the Philippines detained a man selling SMS blasters to local criminal groups after an entrapment.
A month earlier, in March, Indonesian police said they were tracking the leader of a gang involved in SMS blasting across multiple cities.
Also in March, Philippine authorities arrested over 180 individuals in a case related to SMS blasting and cyber scam hubs, including one suspect who sold the blasters.
As Eric Priezkalns writes for CommRisk , in this particular case, the connection leads back to China's criminal underworld. Chinese criminal groups established POGOs ( gambling firms registered in the Philippines that cater to foreign markets ), but the same individuals also started importing and selling SMS blasters, feeding and helping the local cybercrime ecosystem evolve with new capabilities.
Earlier than that, in February, a 23-year-old was arrested in Hong Kong for using an SMS blaster to impersonate government services and collect credit card data.
In January, Thai officials arrested two Chinese men who were posing as tour guides but were actually driving around Bangkok with an SMS blaster in their car.
Back in November last year, Malaysian authorities detained four individuals for driving two cars around the Klang Valley and Kuala Lumpur with SMS blasters.
Also in November, Thai police arrested a Chinese man for driving around Bangkok and posing as a local ISP to scam users.
In October, New Zealand reported its first case of SMS blasting, a 19-year-old in Auckland. The teenager was arrested in August, which explains why NZ-CERT issued an advisory about SMS blasting that month.
In July last year, Brazilian authorities arrested a 22-year-old who was getting paid $180/week to drive a car with SMS blasters around Sao Paulo.
In June 2024, UK authorities also arrested two Chinese nationals for using a homemade SMS blaster to send smishing across London.
CommRisk, a trade publication for the telco sector, is keeping track of all these incidents via an interactive map , which we expect to get real busy in the coming months.
Using an SMS blaster has its benefits, compared to using Twilio and other platforms that can let criminal groups send mass SMS spam.
SMS blasters let you get closer to users and effectively bypass any security defenses put in place at the telco or other software provider's level.
This is important, since even if spam is everywhere, a lot of it is also getting blocked these days. It's not cheap sending one million spam messages only to get a 10% delivery or open rate. On the other hand, an SMS blaster can put your smishing message in a phone's inbox 100% of the time, as long as users have 2G enabled on their phone—and most people do. SMS blasters also allow attackers to make their messages look authentic, since they control all the details of the SMS and aren't limited to the text.
The downside to using an SMS blaster is that you need people on the ground in a bunch of places. SMS blasters are also not cheap, with prices going for a few thousand USD, with some devices costing up to $35,000 .
When it comes to protecting against SMS blasters, the easiest way is to disable 2G on your phone. SMS blasters exploit the lack of proper authentication systems in the 2G protocol to work.
The best protection against SMS blasters is in Android, which, since v12, has had a dedicated setting to let users disable 2G traffic. On iOS, it's a little bit complicated. There's no separate option to disable 2G, but putting your iPhone in Lockdown Mode also disables 2G, although Lockdown Mode also disables a lot of other features users might want to keep enabled.
The problem is that many people won't be smart enough to know to, or know how to, disable 2G on their phone.
In the end, most people will remain vulnerable to SMS blasters unless more centralized defenses are deployed at a telco level.
Google has taken a step towards this direction by adding a new notification to Android 16, released this year, that warns users when they connect to fake cell towers.
Risky Business Podcasts
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about Huawei's contract to manage storage for Spain's lawful intercept system. News broke this week that Spain had signed a €12 million contract, but it turns out Huawei has been involved in the system since 2004!
Breaches, hacks, and security incidents
GUR claims Gazprom hack: Ukraine's military intelligence service claims to have hacked Gazprom, Russia's largest gas producer. Officials claim to have wiped servers, disabled over 20,000 workstations, and deleted backups. The hack allegedly impacted almost 390 Gazprom subsidiaries and branches. Gazprom has not confirmed the attack, but its website has been down for days. [ Additional coverage in the Kyiv Independent ]
Russian alcohol retailer closes stores: One of Russia's largest alcohol producers has closed more than 2,000 stores across the country following a ransomware attack last week. Novabev Group says the attack impacted its online store and ability to process orders at WineLab stores. The company has refused to pay the ransom and has since restored operations. [ Additional coverage in The Record ]
Iranian bank hack impacted a second bank: A suspected Israeli operation that hacked and brought down the Sepah Bank in Iran also impacted a second bank named Pasargad, per a new Iran International report .
Secret Service swatting incident: Per an Axios report , a top US Secret Service official was swatted over the 4th of July weekend.
CoinDCX crypto-heist: Hackers have stolen $44 million worth of crypto assets from Indian crypto exchange CoinDCX . The company's CEO described the incident as a "sophisticated server breach." CoinDCX says user funds are safe. [ Additional coverage in CoinTelegraph ]
Chinese hackers breach Singapore: Singapore's cybersecurity agency has detected Chinese hackers in parts of its critical infrastructure. The agency has attributed the hacks to a group tracked as UNC3886. The group has a long history of using exploits to target unpatched networking and enterprise gear.
Dutch Public Prosecutor goes offline: The Dutch Public Prosecution Office disconnected its internal network from the internet on Friday. The Dutch cybersecurity agency believes the Office was likely hacked via a vulnerability in its Citrix NetScaler appliances. A vulnerability known as CitrixBleed2 has been actively exploited in the wild for almost two weeks. The Office allegedly patched servers, but systems remained vulnerable. [ Additional coverage in NOS ] [ h/t Bert Hubert ]
General tech and privacy
Getting off US tech: Paris Marx has published a guide on how users can move away from US-based tech products.
DuckDuckGo no AI version: The DuckDuckGo search engine has launched a version of its search that does not include any AI-generated content.
Proposal to freeze old cryptocurrency: An upcoming Bitcoin technical specification will block users from transferring funds secured with outdated encryption algorithms. Bitcoin wallets and exchanges will have to use secure quantum-resistant cryptography or have assets frozen on the blockchain. The Bitcoin team says quantum computers are an existential threat to the entire ecosystem. It estimates the migration will take at least five years. [ Additional coverage in CoinSpeaker ]
CrowdStrike outage impacted US hospitals: At least 750 US hospitals experienced IT outages last year due to a faulty CrowdStrike update. At least 200 hospitals lost access to healthcare records, possibly impacting patient care, according to a new study by a team of medical cybersecurity researchers. CrowdStrike called the paper "junk science." [ Additional coverage in WIRED ]
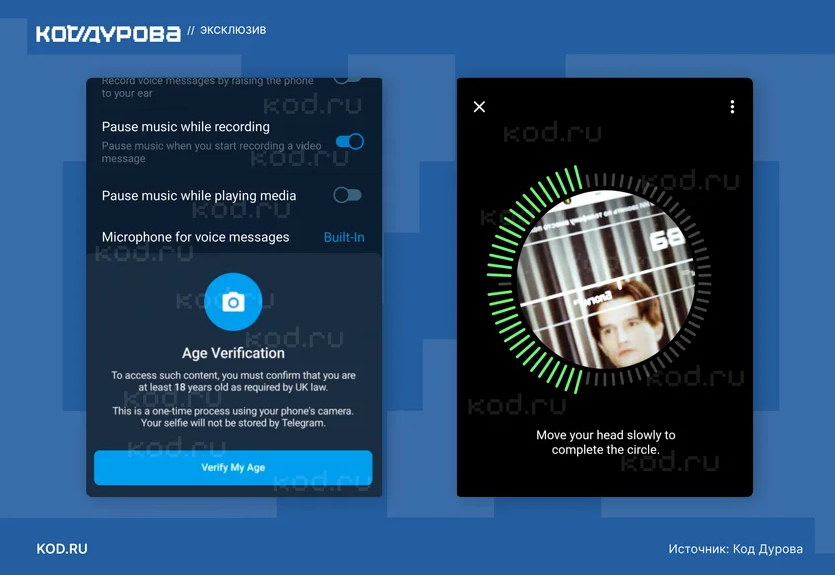
Telegram is working on an age verification system: Russian instant messaging service Telegram is working on its own implementation of an age verification system. The system will allegedly be used to grant users access to channels and groups that host 18+ materials. [ Additional coverage in Durov Code ]
Government, politics, and policy
Microsoft removes escorts program from DOD cloud: After a ProPublica report exposed the fact that Microsoft was allowing Chinese software engineers to interact with DOD cloud systems through an "escorts" program, Microsoft says it has now made changes to this program to exclude Chinese engineering teams from interacting with DOD environments. Great, I guess! Maybe don't roll out these kinds of schemes to sensitive government customers in the first place! Just my two cents!
Russia threatens WhatsApp: State Duma deputy Alexander Gorelkin has hinted that it may be time for WhatsApp to withdraw from the Russian market. Gorelkin has been one of the major legislative forces behind many laws taking aim at Western tech firms operating in Russia since the country's invasion of Ukraine. Rumors are that the Kremlin is already secretly preparing new laws to ban Western IT in the country starting this September.
Putin has ordered new restrictions on software “made in unfriendly foreign countries”, a list that includes about 40 nations, such as the US, UK and EU. The order specifically mentions “communication services.” The government must present proposals by September 1
— Mediazona English (@en.zona.media) 2025-07-17T19:26:43.993Z
Sponsor section
In this Risky Business sponsor interview, Thinkst Canary CEO Haroon Meer chats to Casey Ellis about the company's impressive growth over the past decade, and how it approached that path a little differently to other firms. Haroon's advice for young startup founders: Is your problem worth solving? And can you actually solve it? And… Love your customers.
Arrests, cybercrime, and threat intel
ATM jackpotters arrested in Michigan: US authorities have arrested two Venezuelan nationals for stealing more than $100,000 via ATM jackpotting. The two allegedly used electric scooters to drive to the ATMs and cover sensors with glue. They came back hours later, removed coverings, connected to the ATM, and installed malware that emptied cash reserves. Authorities used facial recognition to identify one of the suspects, and then confirmed his identity using Facebook photos. [ Additional coverage in mLive ] [ h/t DataBreaches.net ]
Russia arrests seven leakers: Russian authorities have charged seven suspects with leaking data from government systems. Two individuals have been detained while the rest are under house arrest. The suspects are employees at IT providers and the Ministry of Internal Affairs' analytical and data department. If found guilty, the suspects can face up to ten years in prison. [ Additional coverage in Mediazona ] [ h/t DG ]
IR/IL Cyber War Tracker: Security researcher Hamid Kashfi has put together a Google spreadsheet with cyber-related activity related to the recent skirmish between Iran and Israel.
New npm malware: Two hundred two malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details .
npm supply chain attack: Hackers gained access to five popular npm packages last week and released new versions containing malware. The malicious code specifically targeted Windows systems. The attackers gained access to the libraries after phishing their maintainer. The five affected packages are some of the most popular npm toolkits around and have over 95 million weekly downloads. They also impacted thousands of other downstream packages. [ Additional coverage in Socket Security ]
Heads up that v3.3.1 of npmjs.com/is has malware in it, due to another maintainer’s account being hijacked. They’re removed for now, v3.3.0 is set at latest, v3.3.1 is deprecated, and a v3.3.2 will be published once I’m not on my phone (thx @github.com codespaces)
— Jordan Harband (@jordan.har.band) 2025-07-19T18:21:21.546Z
Malicious AUR packages: The Arch Linux team has removed three malicious packages from the AUR package repository. The packages posed as browser modifications but downloaded and installed a RAT from GitHub. The packages were live for two days before they were removed.
Greedy Sponge targets Mexico: Arctic Wolf has spotted a financially motivated group named Greedy Sponge target organizations in Mexico with malspam that delivers versions of AllaKore RAT and SystemBC.
Hangro: A security researcher named Nick has looked at the infrastructure of Hangro , a VPN app that North Korean authorities use to hide their communications. It's a two - part series.
Malware technical reports
Ghost Crypt: In May, eSentire has spotted a new malware crypter being used in the wild and named Ghost Crypt .
BlackByte-Crux ransomware: Huntress looks at BlackByte-Crux , a new version of the BlackByte ransomware that launched this month.
NailaoLocker ransomware: Fortinet's security team analyzes a new ransomware strain named NailaoLocker .
Phobos and 8base free decrypters: Japanese authorities have released free decrypters for the Phobos and 8base ransomware strains. Authorities developed the decrypter after the arrest of the Phobos and 8base admins. The Phobos ransomware has operated as a RaaS since 2018. The 8base group launched in 2023 on a leaked version of the Phobos code.
DeedRAT: Lab52 has published a technical analysis of DeedRAT , a remote access trojan used by an unnamed Chinese espionage group.
SquidLoader: Trellix has spotted a new wave of SquidLoader malware samples deployed in attacks against Hong Kong financial institutions.
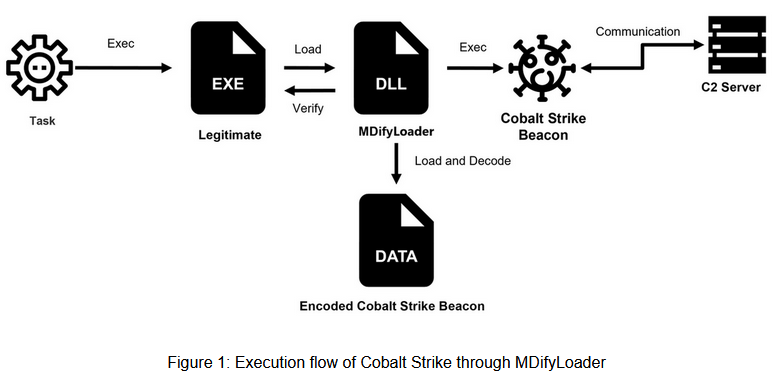
MDifyLoader: JPCERT/CC has released a report on MDifyLoader , a new malware they spotted installed on hacked Ivanti Connect Secure devices, via two recent vulnerabilities tracked as CVE-2025-0282 and CVE-2025-22457.
Sponsor section
In this Soap Box edition of the podcast, Patrick Gray chats with Thinkst Canary founder Haroon Meer about his "decade of deception."
APTs, cyber-espionage, and info-ops
UK sanctions Russian (cyber)spies: The UK government has sanctioned three units of the Russian military intelligence service, GRU, and 18 of their officers. The group used cyber campaigns and influence operations to destabilize the UK, Ukraine, and NATO allies. The units conducted online reconnaissance to help target missile strikes, including a strike that killed hundreds of civilians at the Mariupol Theatre in 2022. They also used malware to help plan the Skripal poisonings. The sanctions also hit three GRU officers who run the African Initiative, a social media content mill operating out of West Africa.
AUTHENTIC ANTICS linked to APT28: The UK's cybersecurity agency published in May a report on a new malware strain named AUTHENTIC ANTICS. The malware runs in the Outlook process to show fake login screens and steal account credentials. On Friday , the UK NCSC linked the malware to Russian cyber-espionage group APT28.
Matryoshka goes after Moldova: A Russian disinfo group named Matryoshka is apparently going hard after Moldova , pushing 39 false claims over the past three months.
Iranian security firm behind airline hacking spree: An Iranian security firm is behind a years-long hacking campaign that targeted airlines all over the world. Security firm Amnban is allegedly one of the contractors behind an Iranian hacking group known as APT39. Besides airlines, the company also targeted freight and logistics companies. Its operations came to light after a leak of internal documents obtained by Iranian security researcher Nariman Gharib.
Iranian 'security firm' #Amnban targeted 17+ global airlines in state-sponsored espionage. CEO hired US/FBI-sanctioned hacker, built shadow infrastructure with dozens of fake emails worldwide. Full story with leaked internal documents: blog.narimangharib.com/posts/2025%2... #APT39
— Nariman Gharib (@nariman.bsky.social) 2025-07-19T11:45:58.057Z
Vulnerabilities, security research, and bug bounty
New Microsoft SharePoint zero-day: Threat actors are exploiting a new zero-day vulnerability in on-premise Microsoft SharePoint servers. Tracked as CVE-2025-53770 , the vulnerability is a variant of an older bug and allows for remote code execution attacks. The zero-day is named ToolShell and is based on an exploit used at the Pwn2Own hacking contest this February. An exploit is already available online. Microsoft says it's working on patches but has not provided a deadline. The zero-day attacks were first spotted by Vietnamese security firm Viettel Cyber Security.
New CrushFTP zero-day: Hackers are exploiting a CrushFTP zero-day to take over unpatched servers. CrushFTP says the hackers reverse-engineered a recent patch and discovered a bug they didn't initially foresee. Tracked as CVE-2025-54309 , the bug allows attackers to take over the CrushFTP admin panel. CrushFTP servers running versions released July 1 and later are safe. [ h/t cR0w ]
Intelbras router vulns: Brazilian security firm Tempest Security has found four vulnerabilities in Intelbras routers. All issues have now been fixed.
Upcoming Matrix security patch: The team behind the Matrix IM servers has announced an important security update that will be released on August 11.
curl considers ending bug bounty program: The curl project is considering shutting down its bug bounty program due to the increase in AI slop bug reports it has been receiving over the past months.
Infosec industry
Threat/trend reports: ANSSI , Firefox , Harmonic Security , HP Wolf Security , and PwC have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Between Two Nerds , Tom Uren and The Grugq examine whether US cyber operations are too stealthy. Could they get more bang for the buck if they adopted a devil-may-care attitude to getting busted?
