Risky Bulletin Newsletter
February 02, 2026
Risky Bulletin: StopICE blames hack on "a CBP agent here in SoCal"
Written by

News Editor
This newsletter is brought to you by Dropzone. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
StopICE, an app that lets Americans track the location of US Immigration and Customs Enforcement (ICE) raids, has played down a recent security breach and claims to have linked the hack to "a personal server associated with a CBP agent here in SoCal."
Administrators said this wasn't the first time the same agent tried to hack or disrupt their systems.
The latest incident took place on Friday when users started receiving SMS alerts warning them to uninstall the app.
Individuals on Twitter claimed that hackers collected the app's user data and shared it with law enforcement agencies, including details such as names, logins, passwords, location data, and phone numbers.
StopICE denied having such data in the first place and called the hack a stunt designed to intimidate its users.
The only affected users were those who signed up for the optional "location assist" feature that collected their geolocation data in order to deliver fine-tuned alerts for their neighborhoods.
StopICE admin Sherman Austin said the hackers targeted a downstream carrier API, which is how they managed to spam users.
This was not the only incident affecting ICE-tracking apps last week. Hackers claimed to have also accessed the servers of Eyes Up, an app that lets users film and document ICE raids.
Hackers claimed the app's backend database had no authentication, which let them access servers and renamed videos to expressions like "I LOVE ICE" and "Never Gonna Give You Up."
We weren't able to find a statement from Eyes Up confirming the incident.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Chat & Ask AI leaks chatbot messages: The developers of a popular AI chatbot have left their backend database exposed on the internet. The Chat & Ask AI app has leaked more than 300 million chatbot messages due to a misconfiguration of its Google Firebase backend. The app claims to have more than 50 million users. [404 Media]
Nobel Committee hack: The Nobel Committee believes hackers found out the name of the Nobel Peace Prize winner ahead of time. One of Norway's intelligence services is investigating a possible breach. Huge sums of cryptocurrency were placed on Venezuelan opposition leader Maria Corina Machado hours before the official announcement. The possibility of an internal leak is not excluded. [Reuters]
Leak at the Ttareungyi bike-sharing service: South Korean police are investigating a breach of the Seoul public bike sharing service. Hackers are believed to have stolen the personal data of 4.5 million Ttareungyi users in April 2024. Officials say a DDoS attack at the time might have blinded IT staff of the breach. [Yonhap News]
Comcast breach settlement: Comcast has agreed to pay $117.5 million to settle a lawsuit over its 2023 security breach. Hackers stole the personal details of more than 31 million customers after exploiting the CitrixBleed vulnerability. Customers who can prove out-of-pocket losses related to the breach may receive up to $10,000. Those who can't can receive up to $50. [Broadband Breakfast]
Cyberattack disrupts production at Russian oil company: A cyberattack disrupted production at an unnamed Russian oil company last year. Hackers allegedly breached the company through its networking equipment and damaged industrial controllers. According to Alexey Ivanov, the deputy director of the National Coordinating Center for Computer Incidents (NCCCI), hackers also breached 20 Russian telco providers last year. [MK.ru] [h/t Oleg Shakirov]
Aperture Finance and SwapNet crypto-heists: Hackers have stolen more than $17 million worth of assets from cryptocurrency platforms Aperture Finance and SwapNet. The attackers allegedly exploited similar vulnerabilities in their smart contracts. They stole $3.6 million from Aperture and $13.4 million from SwapNet. [Cryptopolitan]
General tech and privacy
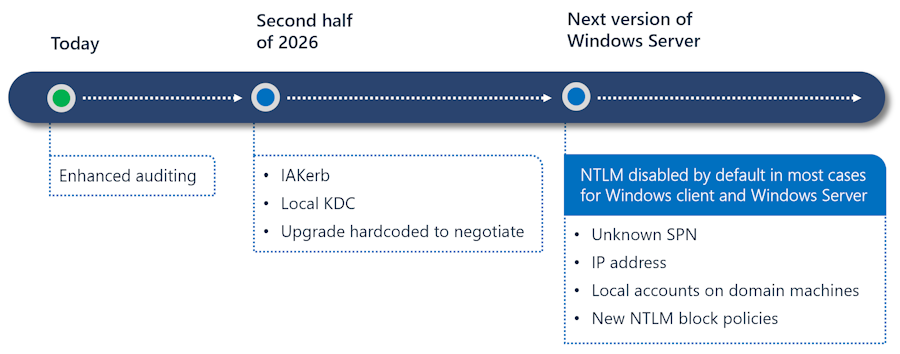
Microsoft will disable NTLM: Microsoft will disable NTLM by default in the next version of Windows Server and associated desktop release. The company formally deprecated the protocol last week and has stopped delivering features and updates. Microsoft will also release new Kerberos features later this year to prepare it for NTLM's future removal. These features will allow Kerberos to work in network topologies where only NTLM previously could.
Apple updates security guide: Apple did the yearly January refresh of its Platform Security guide [PDF].
New NSA guides: The NSA released two new mega-guides on building zero trust architectures.
NVIDIA RTX on Linux: NVIDIA has released Linux drivers for its RTX gaming series for the first time. The move comes after Valve reported great performance for Windows games ported on Linux through its Proton project but complained about problems with NVIDIA's drivers.
US govt investigates WhatsApp: The US government has launched an investigation of Meta's WhatsApp instant messaging service. Former contractors have filed whistleblower complaints against the company, claiming that some Meta staff have "unfettered" access to WhatsApp messages. The investigation is being led by the US Commerce Department. [Bloomberg]
Tor Browser vandalism: The Tor Browser has released an update to fix its Vietnamese translation after a malicious contributor vandalised the text.
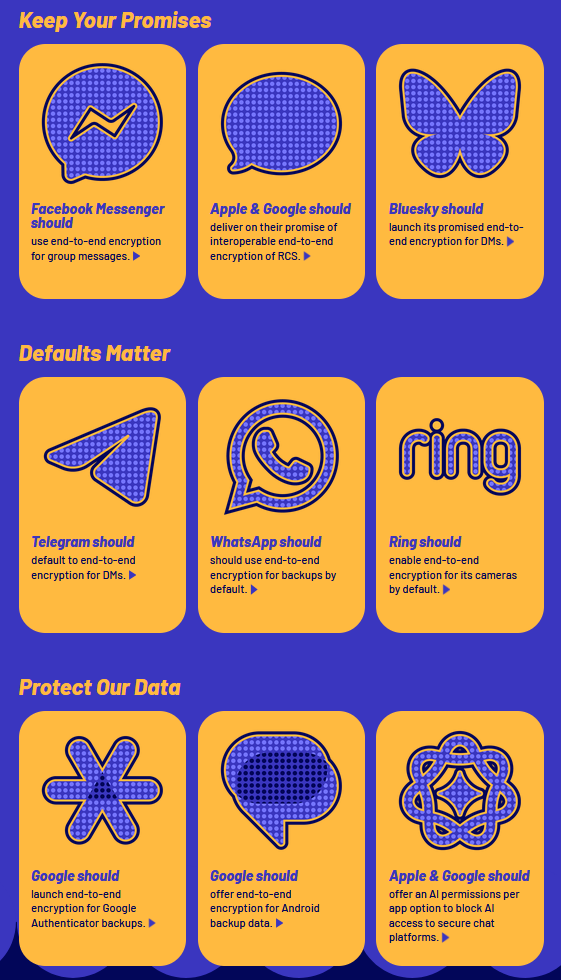
Fix It Already: The EFF has launched a public-awareness campaign to get various service providers to implement end-to-end encryption into their products. The list includes BlueSky, Telegram, Apple, Google, and more.
Government, politics, and policy
Pentagon gets angry at Anthropic: Pentagon officials are trying to convince Anthropic to deactivate guardrails in its AI toolkits. The guardrails are allegedly preventing the US military from using AI for autonomous weapons and to conduct US domestic surveillance. [Reuters]
FBI Operation Winter SHIELD: The FBI has launched Operation Winter SHIELD, a public awareness campaign to get organizations to take 10 basic steps to improve their cybersecurity.
Poland bans Chinese cars from bases: The Polish government has banned Chinese-made cars from entering its military bases. The Warsaw government cited national security concerns over the decision. Chinese officials have allegedly called on Poland to stop abusing the concept of national security. China itself banned Tesla cars from military bases five years ago. [Notes from Poland]
Poland spyware lawsuit drama: A Polish court found that former PiS co-founder Jarosław Kaczyński did not defame a political rival. Kaczyński said it was acceptable to deploy the Pegasus spyware against a political rival because he was trying to prove his rival was committing "abhorrent crimes." It's a weird ruling because it means the past Polish government was allowed to deploy spyware based on "vibes" rather than lawful reasons based on evidence. [Notes from Poland]
Dutch govt wants EU-wide social media age limit: The Dutch government will push the European Union to ban children under 15 from social media. The proposal will effectively raise the minimum age for kids online in the EU from the current 13. The newly formed Dutch ruling coalition is following in the steps of other countries such as Australia, France, and the UK. The same coalition also proposed forming a European version of the Five Eyes alliance.
Russia's flailing critical infrastructure security: Only a third of all Russian critical infrastructure operators have implemented basic cybersecurity measures. Serious advances have been made, according to Russian government officials. The 35% figure is more than double the 13% recorded last year. Russian President Vladimir Putin signed a decree in 2022 mandating critical infrastructure operators to implement basic cybersecurity and switch foreign software to domestic providers. [RBC]
The shift to cyber offense: Dr. Matthias Schulze looks at the general shift in cyber policies across western nations, with some updating their strategies to account for offensive cyber operations during peacetime. [Binding Hook]
"Whether this offensive shift elevates or stabilises security largely depends on the quality of diplomatic and military communication accompanying these operations. To manage the complexities of this environment, allied states must establish common thresholds for intervention, transparency measures, and escalation management protocols. While enhanced cyber capabilities promote burden-sharing among allies and strengthen collective defence, these benefits hinge on harmonising strategies, intelligence sharing, and joint command structures to avoid operational gaps and redundancies."
France's National Cybersecurity Strategy: The French government will prioritize the training of young people in cybersecurity in order to become the "largest pool of cyber talent in Europe." According to the newly released National Cybersecurity Strategy, France will also invest in the private cybersecurity sector to help it grow across the EU, a market currently dominated by American providers. This will be part of a larger push to invest in its own software solutions to ensure digital sovereignty going forward.
"France will continue its active involvement in the Pall Mall Process, which aims to combat the proliferation and irresponsible use of commercially available cyber intrusion capabilities."
— Vas Panagiotopoulos (@vaspanagiotopoulos.com) 2026-01-29T23:29:34.044Z
Sponsor section
In this sponsored interview, Casey Ellis chats to Edward Wu, founder of Dropzone AI about a recent Vanderbilt University report that reveals that foreign adversaries’ resources are growing. Edward says AI capabilities are critical to the future of cyber defence, because the west can’t hire itself out of the shortfall.
Arrests, cybercrime, and threat intel
New scam compound raid: Cambodian authorities have raided the A7 cyber scam compound in the city of Bavet. More than 100 suspects were detained. A7 is one of Cambodia's newest scam compounds and was housing around 2,000 workers. [The Cambodia China Times // The Nation]
A7 is a new addition to Cambodia’s scam landscape and only commenced construction in late 2024 (and is still partially under construction). Location. 3/3 cyberscammonitor.net/profile/a7-p...
— Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2026-01-31T10:25:12.523Z
Red Bull's story: WIRED has published the story of Red Bull, a trapped worker in one of the cyber scam compounds in South East Asia who leaked documents to the publication while he was still captive.
Epstein had a personal hacker: Late sex offender Jeffrey Epstein had allegedly hired a "personal hacker." According to a new batch of the Epstein Files released last week, the hacker was an Italian national born in Calabria. He allegedly developed and sold zero-day exploits to foreign governments, including the Hezbollah paramilitary group. [TechCrunch]
Operation Switch Off: Italian authorities have arrested 31 suspects that ran four illegal IPTV services. The services operated via special websites and Telegram channels to allow users access to pirated TV streams. The sites had millions of registered users. The bust was the work of ACE, a new anti-copyright infringement mega-alliance that formed in 2017 and started going after illegal services last year.
US seizes three Bulgarian piracy sites: The US Department of Justice seized three piracy portals. The ArenaBG.com, Zamunda.net, and Zelka.org domains allowed users to download movies, TV shows, games, software, and ebooks. All three were run from Bulgaria, with one portal being in the country's Top 10 most visited domains.
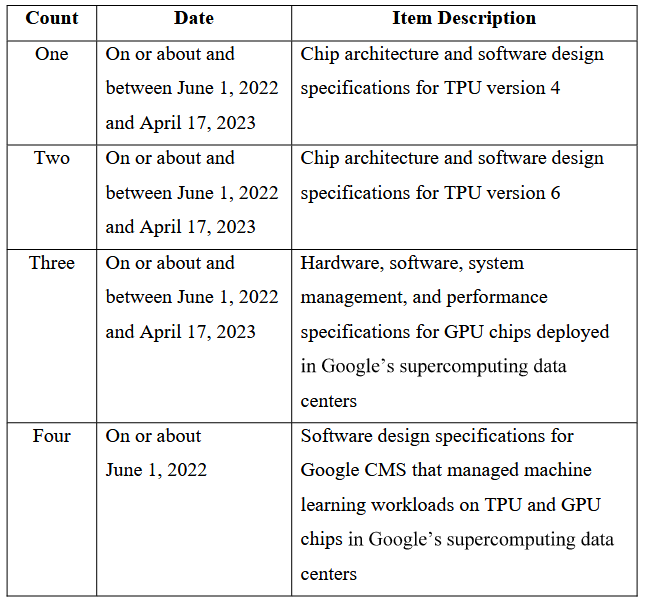
Jury convicts Google engineer: A jury has convicted a former Google engineer for stealing AI trade secrets from his employer. Linwei Ding was arrested two years ago after he was caught transferring more than 500 Google confidential files to his personal account. The files contained data on chip architecture, software designs, performance metrics, and other. He allegedly planned to share the data with two Chinese startups where he'd be appointed in executive positions.
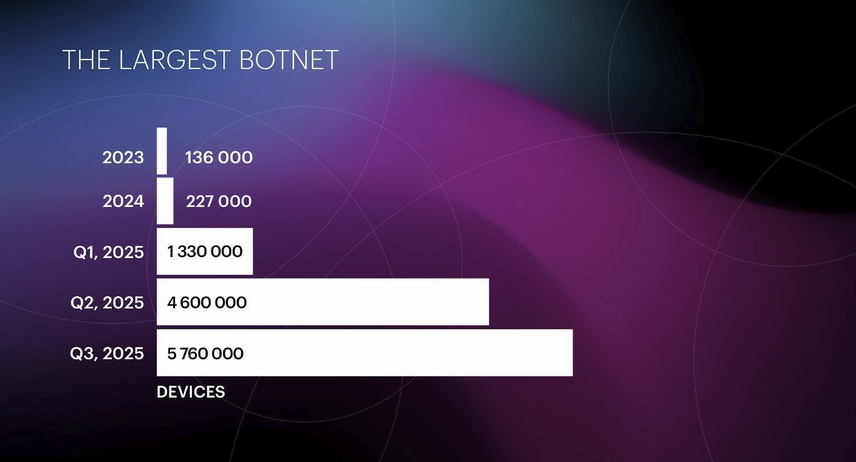
New DDoS record: Cloudflare has mitigated a new record DDoS attack of 31.4 Tbps. The attacks originated from a DDoS-for-hire botnet known as Aisuru or Kimwolf. The botnet has infected up to four million devices across the globe and is regularly used to attack the gaming and hosting sectors.
"The relationship is essentially that of a variant to a parent. Kimwolf is the "Android variant" of the Aisuru DDoS botnet. It uses the core DDoS functionality of Aisuru but is specialized to infect and operate within the Android ecosystem."
Another malicious VS Code extension: Checkmarx has spotted a malicious VS Code extension targeting users of the Solidity programming language. The final payload was a ScreenConnect-based RAT.
Malicious skills on ClawHub and GitHub: Security researchers have discovered 28 malicious skills published on GitHub and the ClawHub portal. The malicious skills masquerade as cryptocurrency trading tools but instead infect macOS and Windows users with infostealers. Skills work as plugins and allow MoltBot (formerly ClawdBot) users to perform automated actions for specific topics. Most of the malicious skills are still available on both GitHub and ClawHub. [OpenSourceMalware]
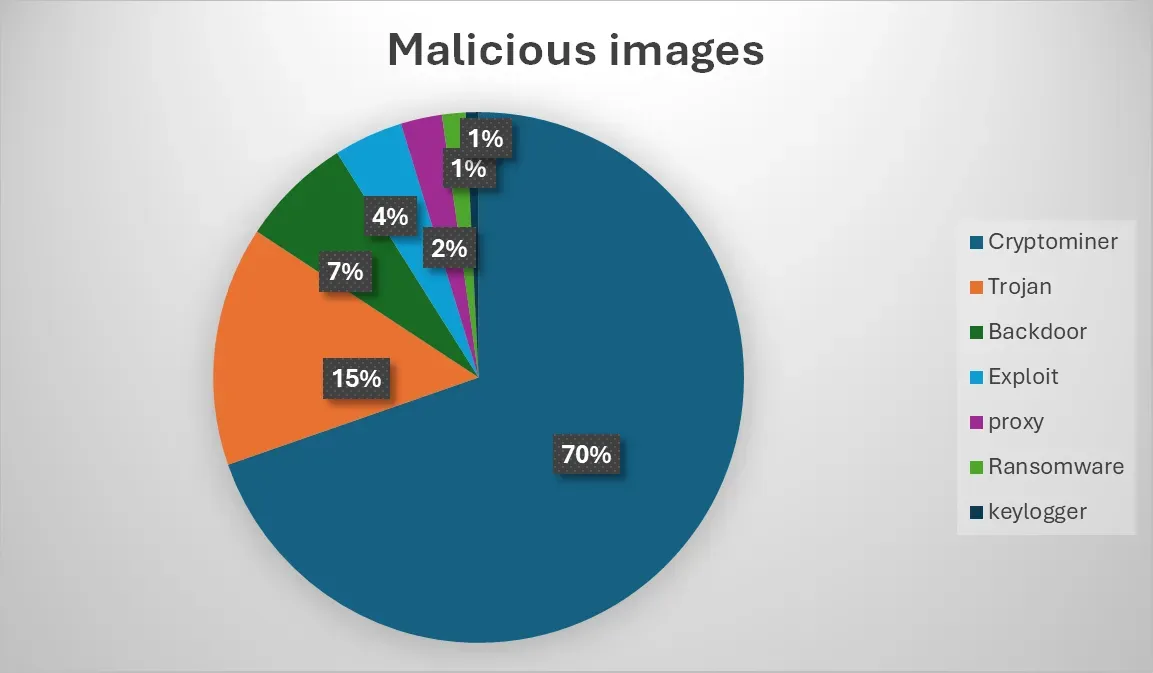
Malicious container images: Qualys has discovered more than 2,500 malicious images hosted on the Docker Hub. Around 70% of the images contained a hidden cryptominer. Others included , backdoors, exploits, ransomware, keyloggers, and even proxy infrastructure.
AI exposure: Censys and SentinelOne have uncovered more than 175,000 publicly accessible hosts running some sort of AI compute infrastructure, with a persistent core of 23,000 hosts generating the majority of activity.
OpenClaw exposure: Similarly, Censys says more than 21,000 instances of the OpenClaw open-source AI assistant have been set up over the past week and are now exposed on the internet. This is like the MongoDB exposure of the early 2010s, but with more computing power behind the servers. Le sigh!
AsyncRAT exposure: Censys also found 57 C&C servers for the AsyncRAT malware that are accessible on the public internet, ready for takedowns or hacking.
Slow PQC email adoption: Only 0.26% of the top 1 million email servers support post-quantum cryptography protections for STARTTLS as of January 2026. [Jan Schaumann]
WhiteSnake interview: Threat intelligence analyst g0njxa has published an interview with the developer of the MioLab infostealer, also known as NovaStealer.
StopLamers profile: Software engineer Illia Datsiuk has published a profile on StopLamers, a threat actor behind the SeksVirus trojan and some old destructive attacks against Android and Linux devices.
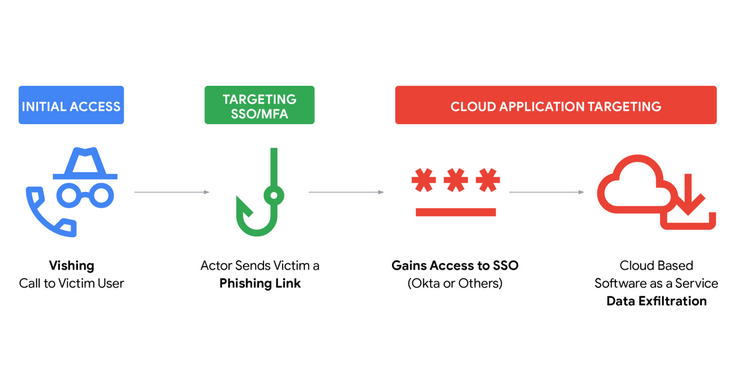
New SLH report: Google has published a report on the new vishing attacks that target SSO accounts conducted by the Scattered Lapsus$ Hunters group, which the Mandiant team tracks as UNC6661, UNC6671, and UNC6240. Similar reports on this campaign are also out from Okta and Silent Push.
"This recent activity is similar to prior operations associated with UNC6240, which have frequently used vishing for initial access and have targeted Salesforce data. It does, however, represent an expansion in the number and type of targeted cloud platforms, suggesting that the associated threat actors are modifying their operations to gather more sensitive data for extortion operations. Further, the use of a compromised account to send phishing emails to cryptocurrency-related entities suggests that associated threat actors may be building relationships with potential victims to expand their access or engage in other follow-on operations. Notably, this portion of the activity appears operationally distinct, given that it appears to target individuals instead of organizations."
Malware technical reports
DynoWiper: ESET has finally published a technical analysis of DynoWiper, the data wiper used in the attack on Poland's energy grid at the end of last year.
GlassWorm is back, again: Socket Security has spotted a new attempt to distribute the GlassWorm self-replicating VSCode worm on the OpenVSX extensions portal. This new push came after attackers compromised a developer's account and pushed the malware to their four extensions.
PhantomVAI: Intrinsec has published a report on PhantomVAI, a custom malware loader built on an old RunPE utility. The malware has been used in the wild for the past year to deploy other payloads, such as Remcos, XWorm, AsyncRAT, DarkCloud, and SmokeLoader.
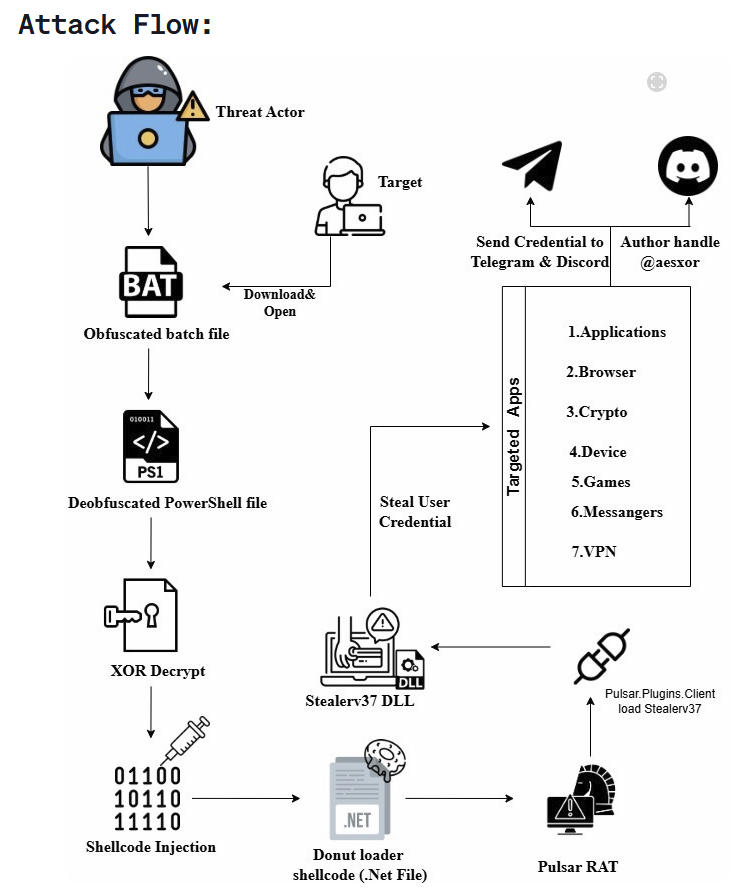
Pulsar RAT: Point Wild looks at a Donut Loader campaign delivering the Pulsar RAT.
Sponsor section
In this sponsored product demo, Dropzone founder and CEO Edward Wu walks Risky Business podcast host Patrick Gray through the company's AI SOC analyst.
APTs, cyber-espionage, and info-ops
Google's disinformation takedowns: Google has published its quarterly takedowns of disinformation operations active on its platforms. During the last quarter of last year, the company saw huge activity from clusters promoting Chinese, Russian, and Indonesian narratives. Moldova, Azerbaijan, Armenia, and the EU saw the brunt of Russia's ops, while China was busy attacking the US and complimenting itself.
Fidesz disinformation network: A Facebook troll farm pushing pro-Orban disinformation has ties to a local non-profit organization with ties to the Fidesz political party. Hungarian journalists claim more than 100 employees of the Digital Democracy Development Agency manage Facebook accounts that promote the party and attack the opposition online. The agency allegedly buys Facebook groups and accounts and then floods discussions with their comments. Hungary is set to hold parliamentary elections in April. [444 // Telex]
Prospect Call campaign: Daylight Security looks at a social engineering campaign using Microsoft Teams meetings to trick attendants into installing macOS malware. Researchers believe the campaign may be part of the broader GhostCall campaign by the BlueNoroff group.
RedKitten campaign: HarfangLabs has identified an Iranian spear-phishing campaign that is targeting participants and organizations that documented Iran's brutal crackdown and the murders of protesters in the January 2026 anti-government protests. The activity overlapped with different APTs, so it's unclear which particular group or agency was behind it.
APT42's TAMECAT: Pulsedive has published a technical analysis of TAMECAT, a PowerShell backdoor used in past APT42 operations. APT42 is an Iranian cyber espionage unit.
Common Chinese APT trends: Intel471 looks at the common TTPs observed from China-linked threat groups and how they tie back to Chinese policy.
Ukrainian phishing op: Digital Security Lab Ukraine has spotted a phishing campaign targeting local orgs with a RAT as a final payload.
"Given the impersonation of a national regulator, this campaign is best classified as targeted espionage-oriented phishing, not commodity malware."
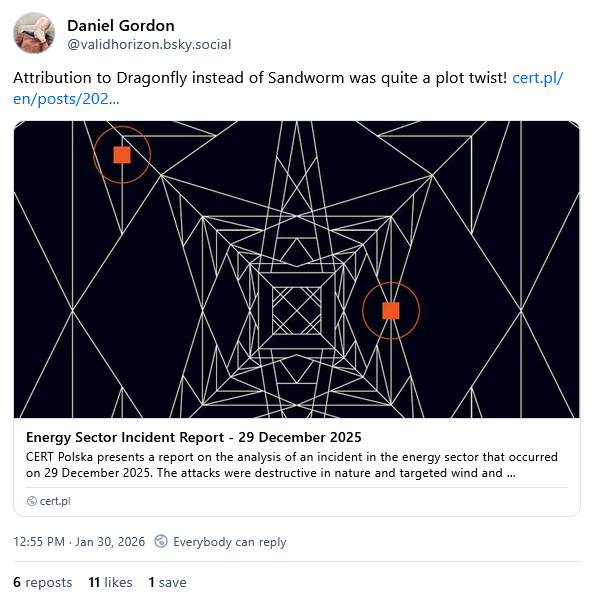
New attribution for the Poland energy grid attack: Polish officials have attributed the data-wiping attack on its national power grid to a Russian hacking group known as Dragonfly (Static Tundra, Berserk Bear, Ghost Blizzard). An initial report from ESET linked the attack to Sandworm, a cyber unit inside Russia's military. Dragonfly is a group widely considered to be associated with Russia's FSB intelligence service. Threat intel researcher Joe Slowik believes multiple Russian groups may have collaborated on the attack. A report published by Poland's CERT found that the affected energy providers failed to adequately secure their networks, which aided the attack.
Vulnerabilities, security research, and bug bounty
Pentesters get justice: The Dallas County in Iowa was ordered to pay $600,000 to two pentesters that were unjustly arrested in 2019. Gary DeMercurio and Justin Wynn were arrested after they broke into the Dallas County Courthouse. They were arrested and charged even if they were hired by the state to assess the courthouse's security. The charges were later dropped. [The Des Moines Register]
Ivanti patches two zero-days: Ivanti has released security updates to patch two actively exploited zero-days (CVE-2026-1281 & CVE-2026-1340). Both vulnerabilities are code injection bugs that allow unauthenticated code execution. Ivanti says it's aware of attacks against a "very limited number of customers." According to GreyNoise, the web reconnaissance infrastructure for this campaign appears to originate from networks in Romania and Moldova. WatchTowr Labs has also published a technical analysis of the two bugs.
Tails emergency update: The Tails operating system has released an emergency security update. The patch incorporates fixes from the OpenSSL project. One of the patched bugs can allow remote code execution attacks against systems running the library.
ICONICS Suite bug: PAN Unit42 researchers have found and helped patch a vulnerability in ICONICS Suite, an automation and monitoring solution for SCADA devices.
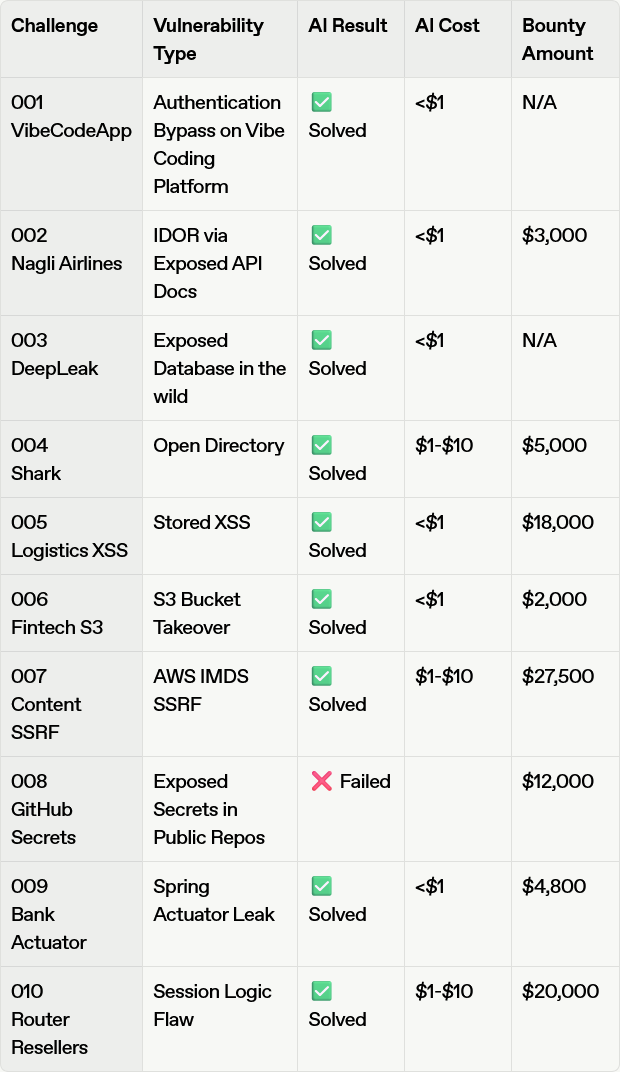
The economics of AI bug hunting: Popular AI models solved bug hunting scenarios based on real-world hacks for costs of less than $1. Tests included agents like Claude Sonnet, GPT-5, and Gemini. Attacks weren't just cheap, compared to hiring a human pen-tester, but also almost instantaneous.
ComfyUI RCE: Tencent's security team has found a major vulnerability in ComfyUI, an app for managing genAI models. Tracked as CVE-2025-67303, the bug is an unauthenticated file upload vulnerability that can lead to remote code execution attacks. It impacts the official extension manager, the component used for the installation and maintenance of custom nodes, models, and dependencies. ComfyUI zero-days have been previously used in attacks last year to deploy the Pickai backdoor.
LoDash security overhaul: Following the report of a major security flaw last year, the LoDash JavaScript framework decided to overhaul its entire base to account for better security practices. More in their blog.
Infosec industry
Threat/trend reports: Bellsoft, Chrome, CSC, Firefox, GreyNoise, ITRC, Keyfactor, Namecheap, NCC Group, PCI SSC, Qrator Labs, and ThreatMon have recently published reports and summaries covering various threats and infosec industry trends.
New tool—Julius: Security firm Praetorian has open-sourced Julius, an LLM service fingerprinting tool for security professionals.
New tool—Offensive Security MCP Servers: Security firm FuzzingLabs has published a list of production-ready MCP servers for offensive security tools.
BlueHat Asia videos: Talks from the BlueHat Asia 2025 security conference, which took place last November, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about the Pall Mall Process, an international effort to reign in abusive spyware. The pair also discuss news that Chinese Salt Typhoon hackers compromised the calls of senior UK officials in Downing Street.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss how getting pinged hurts state hackers by introducing uncertainty. Publishing technical reports on the hack can actually improve the situation by removing uncertainty about how attackers were detected.
