Risky Bulletin Newsletter
July 11, 2025
Risky Bulletin: Two billion eSIMs receive crucial security patch
Written by

News Editor
This newsletter is brought to you by Knocknoc . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
Security updates are being shipped out to mobile operators across the world to fix vulnerabilities in more than two billion eSIMs.
The vulnerabilities impact Kigen's eUICC ( embedded Universal Integrated Circuit Card ), a software package provided to mobile network operators to support eSIM technology.
eSIMs allow mobile operators to ship a software-based SIM to a device. The technology is mainly used for issuing temporary SIMs to travelers and to add mobile connectivity to IOT devices that can't fit a SIM card slot.
The team at AG Security Research, publicly known as Security Explorations , has discovered that some mobile operators ship a "test profile" for Kigen's eUICC software that uses a default secret key to safeguard eSIM data.
The team says this secret key can be extracted from devices to which an attacker has physical access and can later be used to sign and deploy malicious Java Card applets to the device.
These subsequent applets can be used to run a second attack against the Java Card VM that runs on a device's eUICC (eSIM) chip.
The attack exploits a 2019 vulnerability that Oracle declined to patch and can be used to dump the VM's memory. This memory can contain sensitive information from multiple other apps running on the device, such as " digital wallets / payment, digital car keys, transportation cards, access / identification cards, etc. ".
It can also be used to dump eSIM profile details in cleartext, which the attacker can use to clone a targeted eSIM and intercept communications or port the eSIM to a new device.
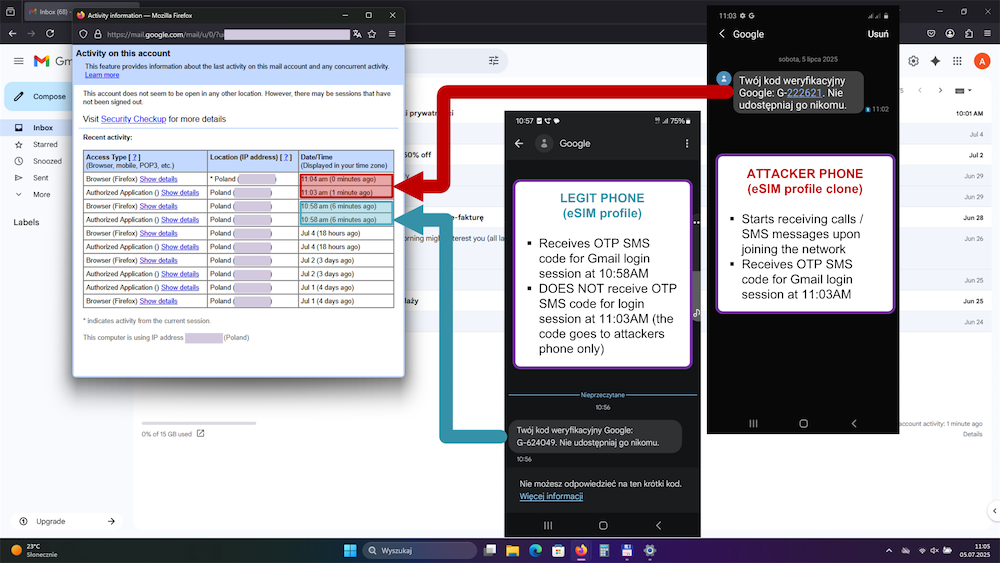
The Security Explorations team says the attack is complex, but it is also reliable, and is likely to be attractive to well-resourced attackers like state-sponsored groups that can easily obtain access to a device.
Kigen awarded the company a $30,000 reward for their report. It issued a security patch for its eUICC software earlier this month with two layers of mitigations. The first fix will prevent the installation of remote applets on the test profile. The second fix is a little more complex, and it removes Remote Applet Management (RAM) keys from test profiles altogether, unless mobile operators specifically configure them to be used. Kigen says future RAM keys will also be randomly generated.
On the other hand, Oracle appears to have remained as uninterested in fixing the issue exploited in its Java Card VM as it was in 2019.
God help us all if this company gets its hands on TikTok! </s>
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Bundeswehr cyberattacks: German authorities are investigating cyber intrusions at two contractors for the country's armed forces. Both incidents took place in June, and it's unclear if sensitive information was compromised. Victims include an IT company for the army's satellite communications and a construction firm building a command center. Authorities assume the hackers are part of the Russian cybercrime scene. [ Additional coverage in Taggeschau ]
Iranian APT hacked Iran International twice: An Iranian APT group has hacked journalists from an independent news outlet and leaked their Telegram chats. Iran International says its reporters were hacked twice in the summer of 2024 and January this year. The news organization, which operates out of London, linked the hacks to a group known as Banished Kitten (Storm-0842, Dune).
McDonald's AI hiring bot leaks user data: Security researchers have discovered major vulnerabilities in Olivia, an AI chatbot used by most McDonald's franchises to hire new staff. The two issues could have allowed attackers access to the Olivia admin panel and dump the personal data of more than 64 million job applications. They included a default admin account with the username and password of "123456" and an IDOR vulnerability inside an internal API that was exploited to gather all the user data. [ Additional coverage in WIRED ]
NS Solutions breach: Hackers breached Japanese cloud and software provider NS Solutions in March using a zero-day against one of its network devices. The hackers stole data on the company's customers, partners, and employees. NS Solutions says it found no evidence that the data was leaked online.
Two sports betting sites hacked: Hackers have breached two UK sports betting brands and stolen customer data. Flutter Entertainment confirmed intrusions at Paddy Power and Betfair. The intruders allegedly stole emails, names, home, and IP addresses in a breach last month. [ Additional coverage in Focus Gaming News ]
GMX crypto-heist: Hackers have stolen $42 million worth of crypto assets from the GMX cryptocurrency exchange. The attacker used an exploit to drain funds from one of GMX's liquidity pools. GMX offered to allow the hacker to keep 10% if they returned 90% of the stolen funds. [ Additional coverage in The Block ]
Bitcoin Depot breach: A hacker stole the personal data of 26,000 users from cryptocurrency ATM company Bitcoin Depot. The hack took place last month and involved details such as names, driver's license numbers, phone, and home addresses. Bitcoin Depot operates more than 8,000 ATMs across North America. [ Additional coverage in The Record ]
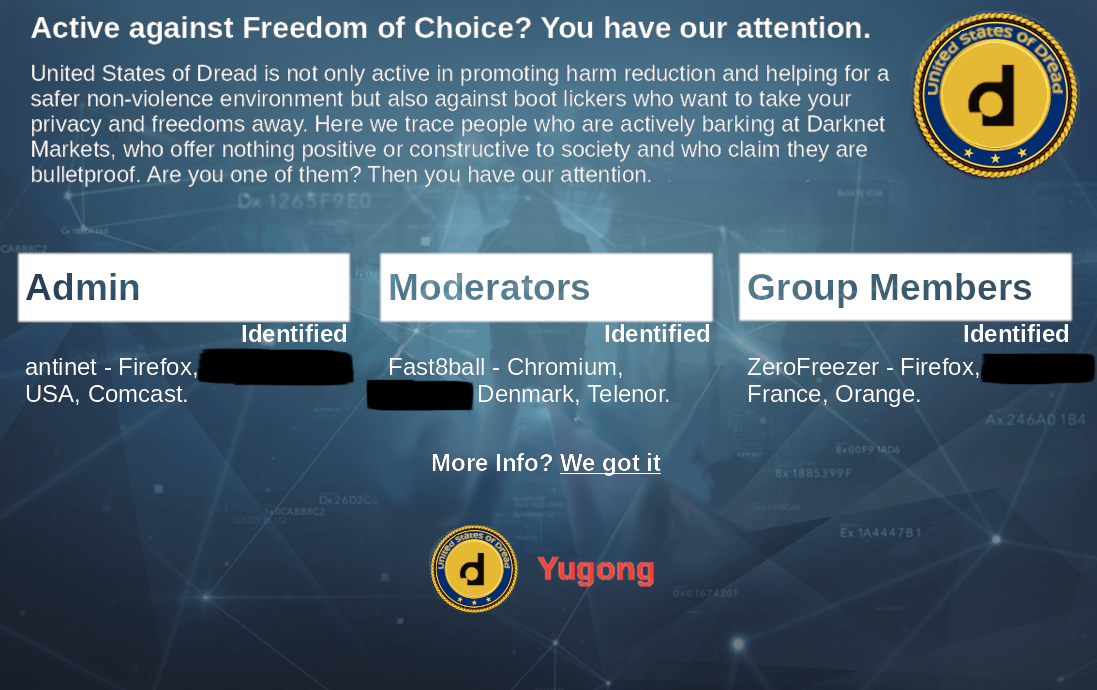
AntiDark defaced: AntiDark , an online community that hunted and exposed cybercrime on the dark web, had its website defaced by a group calling itself the "United States of Dread." The group originates from Dread, a dark web forum where illegal dark web marketplaces advertise their services. The Dread group claims it has identified the real identity of three AntiDark admins.
General tech and privacy
Judge cancels click-to-cancel rule: A US court has struck down a new FTC rule that required companies to provide simple ways for users to cancel subscriptions. The Click-to-Cancel rule passed last year during the last weeks of the Biden-era FTC. Legal experts expected the rule to be challenged and even revoked due to a hurried FTC rulemaking process. [ Additional coverage in ArsTechnica ]
El Faro-v-NSO lawsuit to continue: A US appeals court has overruled a lower court that dismissed a lawsuit filed by El Salvador journalists from the El Faro newspaper against Israeli spyware maker NSO Group. The lawsuit is now free to resume. El Faro journalists sued NSO after they had their devices hacked with the company's spyware. [ Additional coverage in The Record ]
“We’re pleased with today’s decision and look forward to seeking justice on behalf of El Faro journalists in U.S. court, where the case belongs,” says @carriedecell.bsky.social. Learn more & see statement from @elfaroenglish.bsky.social's @carlosdada.bsky.social: knightcolumbia.org/content/appe...
— Knight First Amendment Institute (@knightcolumbia.org) 2025-07-08T19:26:12.054Z
Remove Windows pre-installed apps: Rudy Ooms has found a way to remove Windows pre-installed apps, also known as bloatware.
Postcard is now open-source: The Contraption Company has open-sourced the source code of the Postcard website-building service.
New Samsung phone security features: Samsung's latest flagship phones will ship with quantum-resistant WiFi connections and a new secure storage area. Knox Enhanced Encrypted Protection, or KEEP, will create encrypted storage areas for each app to store its sensitive data. The new features will ship with Samsung's latest phones and the company's phone interface framework, One UI 8.
OpenAI wants to launch a browser: OpenAI, the maker of ChatGPT, wants to launch an AI-driven browser, because their product wasn't creepy enough, and all the other AI-based browsers are such a massive success. </sarcasm> [ Additional coverage in Engadget ]
Twitter CEO resigns: Linda Yaccarino has stepped down as Twitter's CEO a day after the platform's AI assistant Grok turned into a raging fascist, praising Adolf Hitler non-stop and naming itself MechaHitler . [ Additional coverage in the New Republic ]
Must be nice to have the financial security to just quit your job because you released MechaHitler.
— SwiftOnSecurity (@swiftonsecurity.com) 2025-07-09T16:39:51.320Z
Government, politics, and policy
US drops Tornado Cash appeal: The US Treasury Department has dropped its appeal against a court ruling that forced it to lift sanctions against the Tornado Cash cryptocurrency mixing service. [ Additional coverage in Coindoo ]
ODNI purification efforts: A team inside ODNI plans to use an AI agent to scan emails and chat logs at US intelligence agencies and fire employees who don't align with Donald Trump's agenda. Per the Washington Post , none of the agencies have transferred their data to ODNI's AI team.
Go-ahead for GDPR relaxation: Two EU data protection agencies have given their approval for the European Commission to relax GDPR rules. The European Data Protection Board ( EDPB ) and European Data Protection Supervisor ( EDPS ) have welcomed a recent EU proposal to simplify the GDPR administrative burden on small and medium businesses. The proposal extends an exemption from certain record-keeping to companies with fewer than 750 employees. Previously, this was for companies with 250 or fewer.
Dutch cyber subsidy: The Dutch government is reestablishing a cybersecurity grant that will provide funds to small companies to acquire cybersecurity products and services. The "My Cyber Resilient Business" grant was established last year, and the government awarded more than €1.3 million to over 1,300 companies. Dutch companies can apply until the end of October and receive up to €1,250 for planned purchases.
Russia rejects white-hat hacker law: The Russian Duma has rejected a project meant to legalize vulnerability and white-hat hacking research in the country. Officials said the proposed bill didn't take into account the special conditions of critical infrastructure systems and the need to also change criminal law. A new proposal is already under development. Russian officials have been working on legalizing vulnerability research and disclosure since 2022. [ Additional coverage in RBC ]
Russia prepares foreign software ban: The Russian government is preparing to ban the use of foreign software for the storage of Russian user data. A final version of the ban is expected by December. The finalized ban is scheduled to enter into effect starting September 2027. [ Additional coverage in Kommersant ]
Former Mexican president linked to spyware bribes: Mexican authorities are investigating the country's former president for allegedly taking bribes from the spyware industry. Enrique Peña Nieto allegedly received $25 million in bribes from two Israeli businessmen during his 2012 presidency. Nieto allegedly helped the NSO Group secure contracts worth $60 million with several Mexican government organizations. [ Additional coverage in Diario Red / English coverage in JFeed ]
Sponsor section
In this Risky Bulletin sponsor interview, Patrick Gray chats with the CEO of Knocknoc, Adam Pointon. They talk about the woeful state of internal enterprise networks and how many control system networks aren't appropriately segmented. Adam also explains why Knocknoc released a very simple identity-aware proxy: For too long, the Zero Trust "industry" has focused on securing access to critical applications, while everything else is left behind to get owned. This is Zero Trust for crappy apps! Zero Trust, for the rest of us!
Arrests, cybercrime, and threat intel
Russian basketball player arrested in ransomware case: French authorities have arrested a Russian basketball player for his alleged role in ransomware attacks. Daniil Kasatkin was arrested on June 21 at the Charles de Gaulle Airport in Paris at the request of US authorities. The US claims Kasatkin helped an unnamed ransomware gang negotiate ransoms. Kasatkin's lawyer denied the charges and claimed his client has no technical skills. [ Additional coverage in The Moscow Times ]
Four Scattered Spider members detained: UK police have detained four members of the Scattered Spider group for the recent attacks against UK retailers Marks & Spencer, Co-op, and Harrods. The four suspects include two British males, one female, and a Latvian national. They are aged 17 to 20 and all live in the UK.
One of them is one of the LAPSUS guys who got picked up last time 🤣
— Kevin Beaumont (@doublepulsar.com) 2025-07-10T14:45:25.845Z
China cyber-scammers arrests: The Chinese government detained over 570 cyber scammers last year, linked to over 294,000 complaints. [ Additional coverage in China Daily ]
Fraud center raided in Pakistan: Pakistani authorities have detained 149 suspects linked to online fraud and hacking operations. The suspects were arrested following a raid on a factory in the city of Faisalabad. A third are Chinese nationals. They are suspected of having hacked banks and being involved in other cybercrimes. [ Additional coverage in DAWN ]
Telegram phishing in Russia: Russian security firm BI.ZONE says phishing attacks for Telegram have doubled over the past quarter in Russia.
Social media scams continue to target crypto users: Darktrace has spotted a new social media campaign designed to trick users with fake crypto startups and gaming companies and then steal their assets.
New scraper botnet spotted: GreyNoise has spotted a new botnet involved in web scraping activity. Most of the botnet's infected points are located in Taiwan.
RansomedVC returns, leaks Medusa chats: A ransomware group has returned after a two-year absence and leaked the internal comms of a rival gang. The RansomedVC group says it leaked internal data from the Medusa gang after one of its admins went inactive. The group claims Medusa may either be trying an exit scam or might have been compromised by law enforcement. Threat intel analyst Rakesh Krishnan has published an initial analysis of the leak.
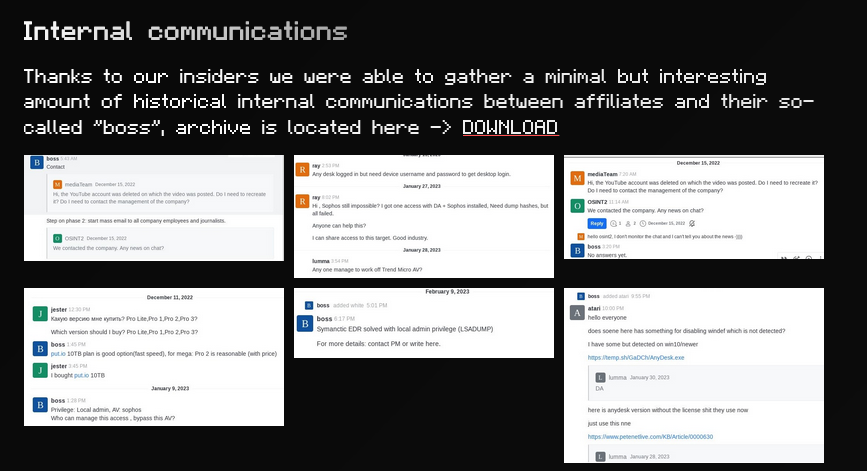
Devman RaaS launches: Back in May, an initial access broker was advertising a new RaaS. That platform has appeared to have launched now.
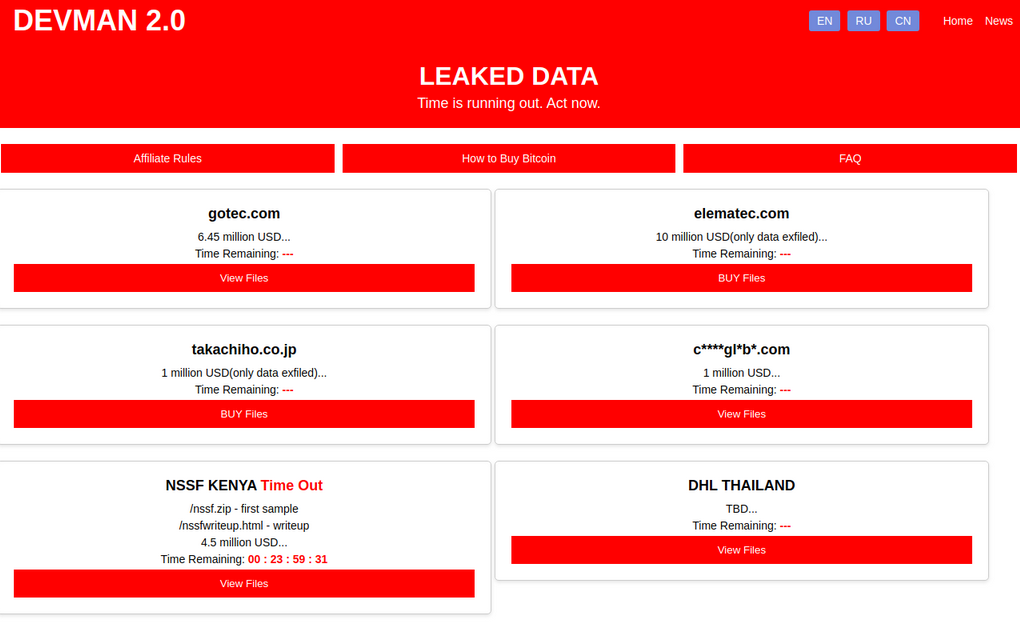
New D4Rk4Rmy RaaS: A new ransomware group named D4Rk4Rmy was spotted in the wild this week. Its dark web leak site currently lists eight victims.

Malware technical reports
SafePay ransomware: The Acronis security team has published an analysis of SafePay , the ransomware that recently hacked US IT product distributor Ingram Micro.
ZuRu backdoor: SentinelOne has spotted a new version of the old ZuRu macOS backdoor. This one was being distributed via a boobytrapped version of the Termius app.
Sponsor section
In this product demo, Knocknoc CEO Adam Pointon walks Patrick Gray through the Knocknoc secure access platform. Knocknoc is a platform that restricts network and service availability to authenticated users via existing network security equipment. Users don't need to install an agent. It also has an identity-aware proxy component that supports web applications and RDP.
APTs, cyber-espionage, and info-ops
DoNoT APT: Per Trellix , a suspected Indian APT group named the DoNoT Team is now targeting European foreign affairs ministries.
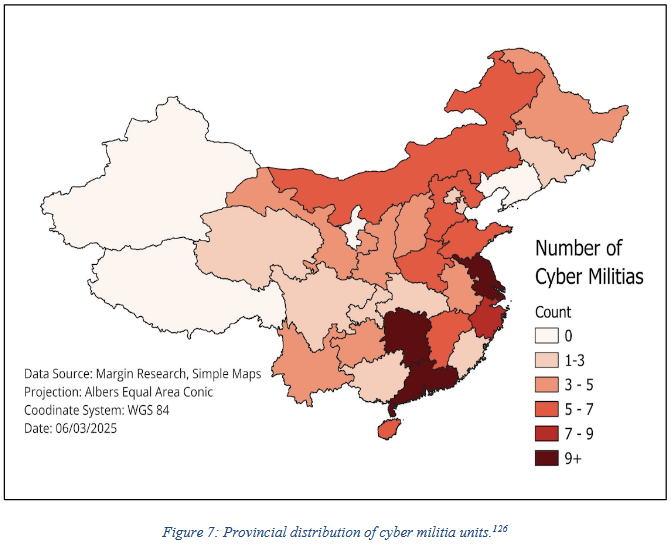
China's cyber militia system: The Chinese government is operating at least 136 cyber militia units. Most of the units are based in the country's east. They are composed of civilians tasked with the cyber defense of critical infrastructure. Margin Research has uncovered new documents showing Beijing also plans to use the units for offensive operations. Two high-end private cybersecurity firms, Antiy Labs and Qihoo 360, have also established cyber militia units and are at "the vanguard of this effort."
Vulnerabilities, security research, and bug bounty
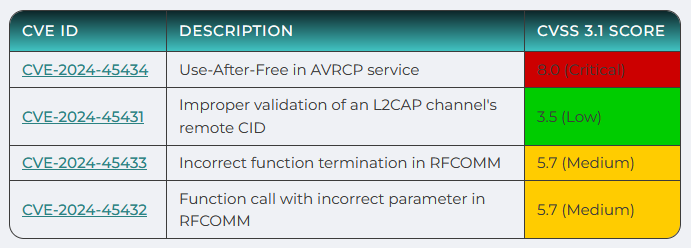
PerfektBlue attack: Four vulnerabilities in a popular Bluetooth software stack can be chained together to run malicious code on cars from at least three major automakers. The PerfektBlue attack impacts the OpenSynergy BlueSDK framework, used in cars from Mercedes-Benz, Volkswagen, and Skoda. Exploiting the vulnerabilities requires at least one user interaction during the pairing process. Successful exploitation allows attackers to extract data from a car or eavesdrop on conversations. OpenSynergy released patches for the attack last September, but not all carmakers have deployed them to customers.
Unpatched Ruckus bugs: Ruckus Wireless has failed to patch nine vulnerabilities in two WiFi and network management products. The issues include authentication bypasses, hardcoded secrets, and unauthenticated remote code execution bugs. They impact Ruckus Virtual SmartZone and the Network Director platforms. Security firm Claroty and the Carnegie Mellon University CERT recommend blocking access to the two products' management interfaces until the issues are patched.
RCE in mcp-remote: The JFrog security team has found an RCE in the mcp-remote library that could be abused for OS command executions inside LLM clients interacting with malicious MCPs.
Lenovo EoP #1: TrustedSec researcher Oddvar Moe has discovered a privilege escalation vulnerability in Lenovo laptops that abuses a daily scheduled task that launches the TPQMAssistant app.
Lenovo EoP #2: Atredis Partners researcher Bryan Alexander has published details on three EoP bugs in the Lenovo Vantage app, preinstalled on all Lenovo laptops, that can be exploited for privilege escalation attacks.
Wing FTP exploitation: Threat actors are exploiting a recently disclosed vulnerability in Wing FTP servers. The vulnerability ( CVE-2025-47812 ) allows attackers to bypass authentication on the FTP server's web interface by appending a null byte to the username. According to Huntress Labs , the attacks began a day after the vulnerability was publicly disclosed.
Jenkins update: The Jenkins project has released a security update to fix vulnerabilities in 20 plugins.
GitLab security updates: GitLab has released security updates to patch four vulnerabilities in its main product.
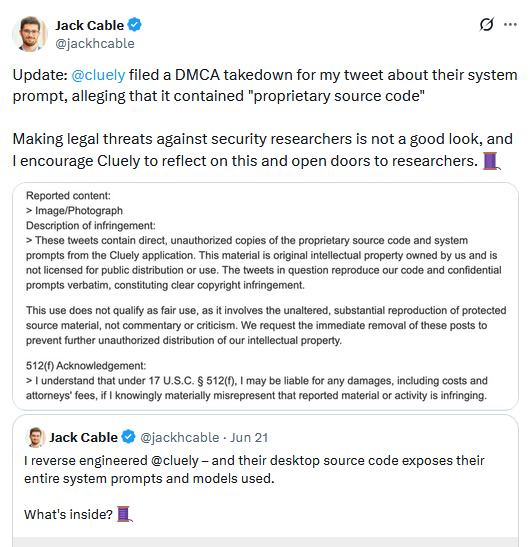
Streisand effect hits Cluely: AI company Cluely used a DMCA to take down a security researcher's tweet that exposed a security issue, and managed to draw even more eyes to its issue. Good job, y'all!
Infosec industry
x33fcon videos: Talks from the x33fcon 2025 security conference, which took place last month, are now available on YouTube . Only 3 videos for now, but there's a new one being added every day.
New tool—go-euvd: Security researcher Kaan Sadik Karadag has published go-euvd , a Go library for interacting with the EU's vulnerability database.
New tool—Deptective: Security firm Trail of Bits has released Deptective , a tool to automatically determine the native dependencies required to run any arbitrary program or command.
Threat/trend reports: BlackKite , GuidePoint Security , and Forescout have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about our developing understanding of the group that people call Scattered Spider. Independent security firms agree that there are a small number of key people who are driving the group's outrageous success.
In this edition of Between Two Nerds , Tom Uren and The Grugq talk about how there is an opportunity for the US to expand its zero-day and talent acquisition pool to Asia. They revisit a paper comparing the Chinese and American zero-day acquisition strategies and have some quibbles.
