Risky Bulletin Newsletter
September 29, 2025
Risky Bulletin: UK to bail out Jaguar Land Rover
Written by

News Editor
This newsletter is brought to you by Authentik . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
The UK government has agreed to underwrite a £1.5 billion loan to Jaguar Land Rover to help the carmaker deal with the increasingly costly aftermath of a recent cyberattack that has crippled its production and shut down factories for almost a month.
The underwrite was approved on Sunday after a visit from UK Business Secretary Peter Kyle to the headquarters of JLR and its main supply chain firm Webasto this week.
JLR fell victim to a ransomware attack—supposedly from the HellCat group —on August 31. Production lines at all JLE factories have been shut down ever since, and are expected to last into October .
While it looked like another benign ransomware attack that hits the back office and the company needs to reinstall some insignificant accounting systems to get back into order, this was not it. Not at all. Systems like CAD (Computer-aided design), engineering software, and product life-cycle software, payments tracking, and customer car delivery systems went down.
The incident has turned into a legitimate catastrophe for both the company, its suppliers, and even the British economy as a whole.
With production lines ground to a halt, hundreds of small companies that supplied Jaguar parts and various services also had to slow their pace and even put workers on leave. Several of the smaller ones are facing bankruptcy proceedings and were expected to go under, since several had just " days of cash " left in their accounts.
With no car sales and no secondary economic activity being generated by its supply chain for an entire month, the JLR cyberattack is likely to impact the UK's economic growth. The company alone employs over 34,000 people, with another 120,000 working throughout its supply chain.
According to a recent report , the company also did not have a cyber insurance deal at the time of the attack and will likely have to foot the bill for the attack and subsequent revenue losses.
Just JLR by itself is expected to lose " hundreds of millions of pounds ," according to reports, which explains the need for an underwrite in the realm of £1.5 billion.
Quite the s***show, but the company is now slowly starting to restore some of its systems.
The government bailing out JLR will send a strong signal to e-crime groups to retarget to the UK.
— Kevin Beaumont (@doublepulsar.com) 2025-09-28T10:02:34.738Z
It also makes me realise how fragile the UK economy is to a few well-placed ransomware/ olympic destroyer style attacks.
— Quentyn (@quentyn.bsky.social) 2025-09-28T10:52:33.052Z
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Moldova election DDoS attack: Moldova's government sites were hit with massive DDoS attacks a day before and during the country's parliamentary election, which took place on Sunday. [ Additional coverage in HotNews ]
RemoteCOM hack: A hacker has breached a company that provides remote monitoring software for US law enforcement. RemoteCOM's software is used to keep track of the internet, PC, and smartphone activity of individuals released on parole in 49 US states. According to Straight Arrow News , a hacker named wikkid leaked data on the software, the police officers who use it, and suspects released on parole.
Mysterious Indian banking leak: Cloud security firm UpGuard has discovered an Amazon S3 bucket that leaked over 273,000 documents containing banking-related data for Indian citizens. The owner of the server is still unknown.
A7 leak: A Moscow IT company has leaked sensitive documents about A7, a newly established Russian payments company. The files reveal how the Kremlin used the A7A5 crypto token to launder money from Russia into the West, to help the Kremlin bypass sanctions, pay bribes, and interfere in elections. The company has been tied to sanctioned Moldovan and Russian oligarch Ilan Shor. Shor fled Moldova after being sentenced to 15 years in prison for stealing $1 billion from the country's banking system. He has been financing pro-Kremlin parties ever since in order to overturn the country's pro-EU leadership.
"The data leak was publicised on social media in recent days and validated by Moldovan news agency IPN. The leak appears to have come from Anykey LLC, a Moscow IT company owned by a Shor associate. Files reveal how the IT firm provides software development and IT infrastructure to Shor's A7 crypto and payments network, the Russian soft-power NGO Evraziya, where Shor is a member of the supervisory council, as well as several connected financial brokers in Kyrgyzstan."
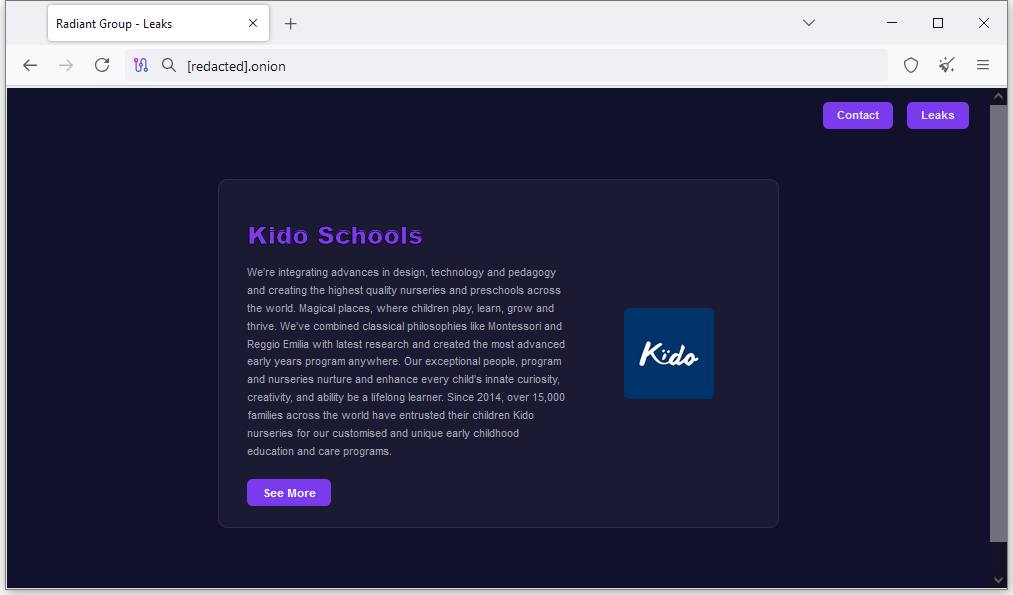
London nursery extortion: Hackers have stolen the personal data of more than 8,000 children from a London nursery. A group calling itself Radiant has released the photo and details of ten children. They are threatening to publish the details of more kids unless the nursery's parent company, Kido International, pays a ransom. Kido operates nurseries and preschools in four countries: the US, the UK, India, and China. [ Additional coverage in Reuters ]
General tech and privacy
Cloudflare Email Service: Cloudflare has launched an email service that lets customers send emails directly from Cloudflare Workers. Expect this to be broadly abused. This is in private beta, for now.
Cracker Barrel bot activity: The online outrage at Cracker Barrel's recent rebrand was almost certainly driven by bots, according to researchers , and most of it on alt-right platforms. [ Additional coverage in Gizmodo ]
Edge sideload protection feature: Microsoft has started work on a new feature for its Edge browser that will detect and block malicious extensions that are sideloaded through its Developer Mode feature. The feature is expected to go live in November.
Google appeals at the Supreme Court: Google asked on Wednesday the US Supreme Court to block a lower court order that would have forced it to make changes to the Play Store rules and allow app makers to list third-party stores and use their own billing systems. The new rules were mandated after Google lost a lawsuit against Epic Games in 2023. [ Additional coverage in gHacks ]
City sends Flock cease and desist: The city of Evanston in Illinois, has sent camera and license plate reader company Flock a cease and desist letter after the company reinstalled all its cameras without permission. The city terminated its contract after it learned that Flock was secretly providing access to the cameras to the US CBP. [ Additional coverage in the Evanston RoundTable ]
Government, politics, and policy
UK announces digital ID scheme: The UK government is introducing a digital ID system for UK citizens and people seeking employment in the UK. The new ID will be stored on people's phones as a regular app. Digital ID will be available but not mandatory to all UK citizens and legal residents. It will only be mandatory in order to seek employment, where it will serve as proof for the Right to Work.
US prosecutor hacked Telegram: A US Attorney's Office asked and received permission to hack Telegram servers. The hack targeted an account linked to a child exploitation case. According to Court Watch News , officials took this route due to Telegram's general refusal to respond to law enforcement requests.
More digital sovereignty: The Austrian Army is replacing Microsoft's Office suite with LibreOffice, an open-source alternative. [ Additional coverage in ZDNet ]
Anatel hosts base station hunting workshop: Brazil's telecommunications watchdog has held a workshop to train experts in finding rogue base stations. Fake base stations, or stingrays, are typically used to power SMS blasters. These are devices that draw nearby mobile phones in their fake cell tower to automatically send them SMS spam and scams. The use of SMS blasters has exploded this year , with cases in over a dozen countries around the globe. [ Additional coverage in CommsRisk ]
Sponsor section
In this Risky Business sponsor interview , Authentik CEO Fletcher Heisler talks to Tom Uren about how identity providers (IdP) are fundamental to everything an organisation does. He explains how organisations are making themselves resilient by managing their redundancy and failover options.
Arrests, cybercrime, and threat intel
Dutch police arrest two teens linked to espionage: Dutch authorities have arrested two teenagers for allegedly spying for Russia. The teens were recruited via Telegram and tasked with hacking-related assignments. They were paid to walk past sensitive locations with a WiFi sniffer. Some of their routes took them near the headquarters of Europol and Eurojust, and the Canadian embassy. Both suspects are 17 years old. [ Additional coverage in NL Times ]
Subdomains-for-rent market: Silent Push looks at the dynamic DNS market that rents subdomains to cybercrime groups. Currently, the company says it tracked more than 70,000 domains that are used to rent out subdomains for this type of activity.
New npm malware: One hundred seven malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details .
Scattered LAPSUS$ Hunters: Resecurity has published a profile on the group calling itself Scattered LAPSUS$ Hunters . The group is responsible for a bunch of the recent hacks of corporate Salesforce accounts and the subsequent extortions.
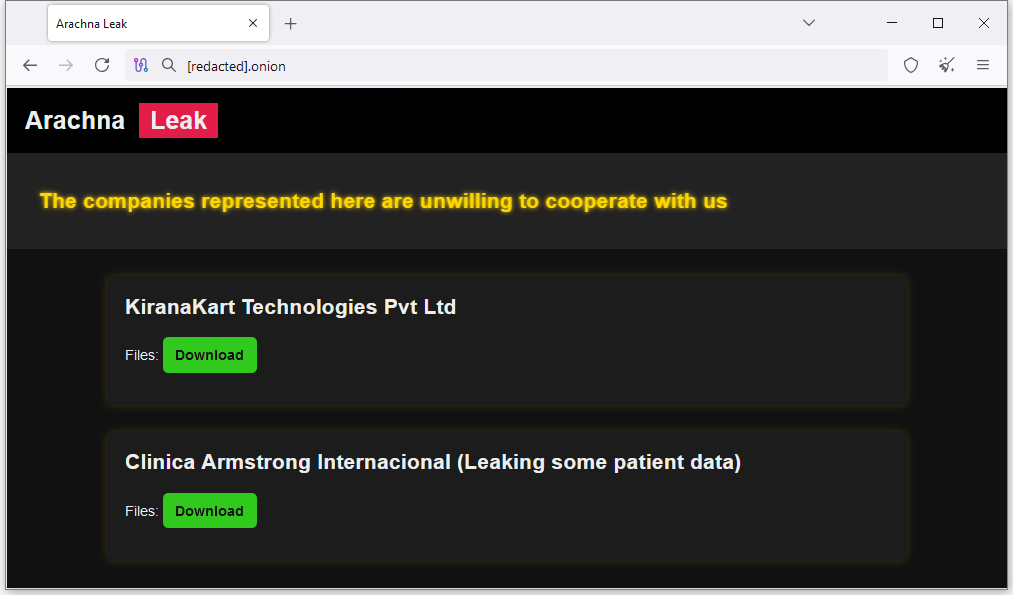
New Arachna Leak: A new dark web data leak site has been spotted. Named Arachna Leak, the site only lists two victims so far.
Malware technical reports
XWorm RAT: Forcepoint has spotted a new campaign spreading the XWorm RAT.
Amatera Stealer: Fortinet has spotted a campaign targeting Ukraine and delivering the Amatera Stealer, along with the PureMiner cryptominer.
DarkCloud Stealer: eSentire looks at DarkCloud , an infostealer first seen in April, advertised on Telegram by an individual named BluCoder.
Acreed: French security firm Intrinsec has published an analysis of the Acreed infostealer , which recently began gaining traction among some cybercrime communities after the Lumma Stealer takedown.
Lockbit 5.0: Trend Micro has published a report looking at the supposed new versions of the Lockbit ransomware, tracked as v5.0 . There's some drama around these, as some researchers don't recognize them as "original" versions.
Antidot's PhantomCall campaign: IBM security researchers have spotted an Android malware campaign targeting the users of financial institutions from several countries across the globe. The final payload is the Antidot Android banking trojan. Attackers are using the trojan to set up call redirects via USSD to block incoming calls and reroute them to the attacker, allowing for 2FA bypasses and impersonation attacks.
HeartCrypt: Sophos takes another look at HeartCrypt , an old Packer-as-a-Service that appears to have become more popular than ever.
Oyster/Broomstick backdoor: BlackPoint has spotted an SEO poisoning campaign that has been pushing malicious versions of Microsoft Teams laced with the Oyster/Broomstick backdoor . This has been happening all summer, with a previous campaign targeting popular IT tools like WinSCP and PuTTY.
TamperedChef infostealer: FieldEffect has spotted new PUAs deploying the TamperedChef infostealer on their unsuspecting users.
Botnet loader infrastructure: CloudSEK has discovered an underground operation that hacks routers and servers and rents the compromised devices to other botnet operators. The operation saw a spike in activity this year, when it was spotted deploying payloads for DDoS and cryptomining botnets like RondoDoX, Mirai, and Morte.
Olymp Loader: Outpost24 researchers look at a new malware loader named Olymp that is offered through a MaaS model advertised on Telegram and underground hacking forums.

Sponsor section
Authentik is an open-source identity provider that is also offered with paid enterprise features. In this demo, CEO Fletcher Heisler and CTO Jens Langhammer walk Risky Business host Patrick Gray through an overview and a demo of the technology.
APTs, cyber-espionage, and info-ops
APT35: The Stormshield team has found two servers that appear to be run by Iranian hacking group APT35, also known as Mint Sandstorm and Charming Kitten.
Vulnerabilities, security research, and bug bounty
GoAnywhere MFT exploitation: Hackers are exploiting a recently patched vulnerability in Fortra GoAnywhere MFT file transfer servers. According to WatchTowr Labs , the attacks started a week before patches were released. The vulnerability allows threat actors with a forged license response signature to execute deserialization attacks and run malicious commands on remote systems. The vulnerability has a severity rating of 10. Fortra previously urged customers to take their admin console offline until they patch.
Cisco zero-day exposure in Russia: Russian security firm CyberOK says that over 30,000 Cisco devices across Russia are vulnerable to a recent zero-day patched last week, tracked as CVE-2025-20352.
GitLab security updates: GitLab has released security updates to patch ten vulnerabilities in its main product.
MAX app audit: RKS Global has performed an audit of the Russian government's new MAX instant messenger mobile app. Even if the review found features capable of surveillance, they were not used beyond just powering the app's IM purpose—for now. Machine translation below.
"During two days of observation, no test configurations revealed improper access to the camera, location, microphone, notifications, contacts, photos, and videos. Technically, the application had the ability to collect these data and send them, but experts did not record what happened. After revoking permits, the application does not record attempts to obtain these accesses again through requests or unauthorized."
AgeGO audit: AIForensics looks at the practices of AgeGO , an age verification platform used by some adult sites to comply with age verification laws in Europe.
PassOffice vulnerabilities: Positive Technologies has found several vulnerabilities , such as SQLi and MFA bypass, to run malicious code on PassOffice, a Russian-developed guest management platform.
Jira vulnerability: A security researcher received a CHF1,500 bug bounty for a vulnerability that could have reset the password of any account on the Jira Service Management Cloud.
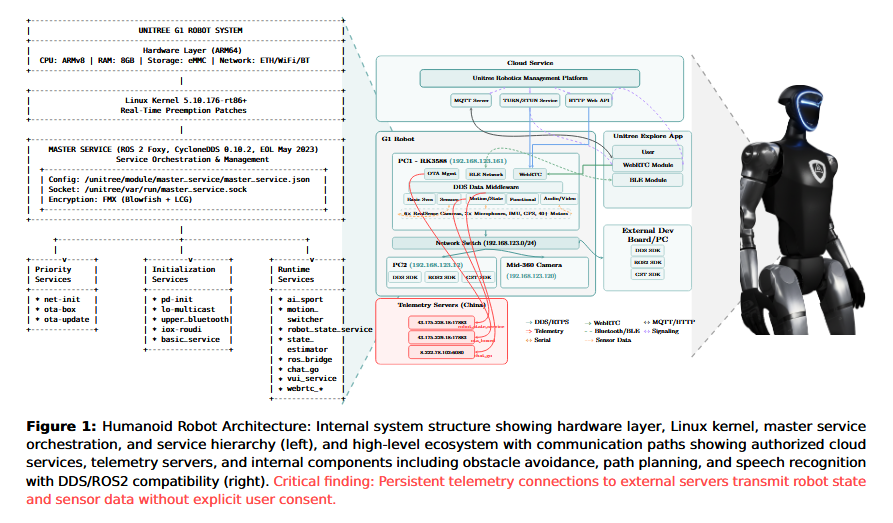
Unitree collects everything: Unitree G1 humanoid robots collect and send sensor and other telemetry data to servers in China without the owner's knowledge or consent. The collection happens every five minutes, according to a team of researchers who reverse-engineered the robot's firmware. The G1 also contains BLE vulnerabilities ( codenamed UniPwn ) that can be exploited to pivot to a customer's internal network. [ Additional coverage in IEEE Spectrum ]
Infosec industry
Threat/trend reports: Allianz , Bitsight , Incogni , and Varonis have recently published reports and summaries covering various threats and infosec industry trends.
New tool—FlareProx: Security researcher Luke Turvey has released FlareProx , a tool to use Cloudflare to create HTTP pass-through proxies for simple IP rotation.
New tool—appledb_rs: Security firm Synacktiv has open-sourced appledb_rs , a server storing various information about Apple device internals and artifacts.
New tool—Titanis: Security firm TrustedSec has released Titanis , a C# library of protocol implementations and command line utilities for interacting with Windows environments.
New tool—TaskHound: ProSec security researcher r0BIT has released TaskHound , a tool that searches for Windows scheduled tasks that run from privileged accounts and with stored credentials.
New tool—pipe-intercept: CyberArk software engineer Gabriel Sztejnworcel has released pipe-intercept , a tool to intercept Windows Named Pipes communication using Burp or similar HTTP proxy tools.
New tool—AuditKit: Software company Guardian Nexus has released AuditKit , an open-source compliance scanner for AWS and Azure with auditor-ready evidence collection guides.
RomHack 2025: Live streams from the RomHack 2025 security conference are available on YouTube .
UniCon 2025: Talks from Scythe's UniCon 2025 security conference, which took place in early April, are available on YouTube . The fall edition live streams are in this playlist .
Risky Business podcasts
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about how the funnel that turns kids into cyber criminals has evolved over the last decade. Cybercrime's reach has broadened, and it is more lucrative and more violent.
In this edition of Between Two Nerds , Tom Uren and The Grugq look at a new Center for Strategic and International Studies report— A Playbook for Winning the Cyber War .
