Risky Bulletin Newsletter
September 15, 2025
Risky Bulletin: US largest crypto ATM operator sued for profiting from scams
Written by

News Editor
This newsletter is brought to you by application allow-listing software maker Airlock Digital . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
In the podcast version of Friday's Risky Bulletin , we reported that that the personal data of almost 6000 Australian doctors and staff had leaked online. We meant to say 600!
The written newsletter had the correct number.
The District of Columbia Office of the Attorney General has filed a lawsuit against the largest crypto ATM operator in the US, Athena Bitcoin.
The lawsuit alleges the company knew its Bitcoin ATMs were being used to collect funds from scam victims, but instead of stopping the transfers, it charged large hidden fees and then refused to provide refunds to victims.
Officials say that 93% of all deposits made across the seven Bitcoin ATMs the company operates in DC were the result of scams.
Scammers would trick victims into going to an ATM and then deposit funds into one of their accounts.
Athena allegedly knew that allowing users to deposit funds into accounts they don't own would be abused for scams, but did nothing to stop scams besides showing a warning on the ATM screens.
DC Attorney General Brian L. Schwalb claims Athena instead chose to apply giant fees on every transaction. The fees were not visible to customers and reached up to 26%, almost 100 times the fees practiced by its competitors, which go from 0.24% to 3%.
Scammed individuals were basically victimized twice, first by the scammers and then by Athena through the undisclosed fees.
The median loss was $8,000, and the victims' median age was 71, with scammers specifically going after the less technical elderly DC population.
AG Schwalb is suing to force Athena into compliance with anti-fraud measures and secure restitution for victims, as well as financial penalties for the District.
"Athena knows that its machines are being used primarily by scammers yet chooses to look the other way so that it can continue to pocket sizable hidden transaction fees," Schwalb said . "Today we're suing to get District residents their hard-earned money back and put a stop to this illegal, predatory conduct before it harms anyone else."

Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
School district closes for a week after ransomware: The Uvalde school district will shut down this week due to a ransomware attack . The incident impacted phones, security cameras, visitor management, and thermostat controls. The district called these systems critical to its students' well-being. The school was the place of one of the worst school shootings in US history in 2022. School activity is expected to resume on Friday.
Jaguar Land Rover suppliers face crisis: Jaguar Land Rover has yet to fully recover more than two weeks after a ransomware attack. The company expects that at least three of its production lines will resume activity this week. According to the BBC , several of the carmaker's smaller suppliers are now facing bankruptcies due to the prolonged production stoppage. Jaguar has lost between £50m and £100m since the attack. The incident is slowly becoming one of the worst cyberattacks in the country's history and is expected to affect Britain's national economic growth stats.
Israeli actors targeted in phishing campaign: Dozens of Israeli actors were targeted by an Iranian phishing campaign last week. The hackers posed as a director looking for actors for a movie on the October 7 attack. Actors were requested audition videos, home addresses, and ID and passport scans. [ Additional coverage in Ynet ]
LNER breach: LNER (London North Eastern Railway has disclosed a security breach after hackers gained access to a third-party supplier and stole data on customers and past journeys.
US CJIS hack: A hacking group that was behind recent hacks of Salesforce accounts—calling itself "ShinyHunters/ScatteredSpider/LAPSUS$"—has announced its retirement. Immediately after, they shared a screengrab from the DOJ CJIS and hinted at hacking the NCA's internal network. Tempting fate! [ Additional coverage in DataBreaches.net ]
General tech and privacy
Official MCP Registry: Anthropic, Microsoft, and the other organizations part of the MCP Steering Committee have announced the first preview of the MCP Registry, the official repo catalog for MCP servers.
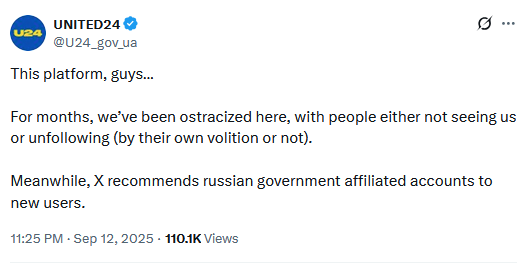
New Twitter low point: There are multiple reports that Twitter is now recommending the widely-sanctioned RT, a Russian state-media outlet that coordinates with Russian intel services , as a must-follow to newly signed users.
Government, politics, and policy
Germany opposes Chat Control: The German government said it would vote against the EU's so-called Chat Control regulation.
We did it: DE 🇩🇪 LU🇱🇺 & SK🇸🇰 just decided to oppose Chat Control! 🥳 Thanks everyone for your help and keep fighting the good fight. 🫶 Chat Control will not get a majority - at least not today. More on why it is the most criticized law of all times: tuta.com/blog/chat-co...
— Tuta (@tuta.com) 2025-09-12T06:18:17.984Z
Dutch army to deploy hackers to front lines: The Dutch Army will deploy hackers with frontline units in case of military conflict. The hackers will be tasked with hacking local infrastructure near a unit that can't be reached by the Dutch Cyber Command. The Dutch Army is taking cues from the Russian and Ukrainian armies, which now regularly deploy cyber personnel on front lines to hack captured drones and personal devices. [ Additional coverage in NLTimes ]
DHS failed to retain cyber talent: CISA did not use funds to retain cyber talent properly. The agency dispersed funds from the Cyber Incentive program to all employees. According to a DHS watchdog report, the funds were supposed to go to a select few valuable employees likely to leave for the private sector. The DHS inspector general says CISA paid bonuses from the Cyber Incentive program to more than 240 employees who did not hold cybersecurity roles. [Additional coverage in FedScoop /DHS OIG report PDF ]
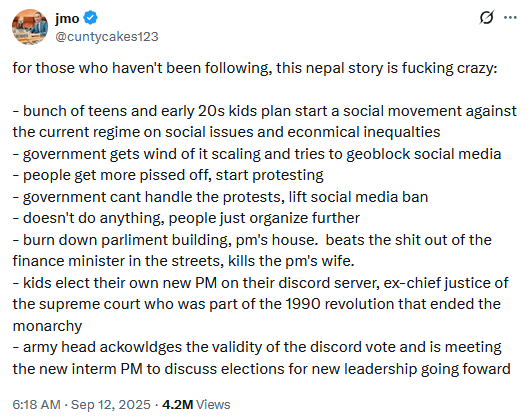
Nepal protesters choose next PM via Discord: The Gen-Z protesters who overthrew the Nepalese government last week have elected a new Prime Minister over a Discord vote. Yes, you read that correctly. [ Additional coverage in Yahoo Finance ]
Sponsor section
In this Risky Business sponsor interview , Casey Ellis chats to David Cottingham and Daniel Schell from Airlock Digital. They discuss the challenge of browser extension management for enterprises, why it’s a priority and how Airlock can help.
Arrests, cybercrime, and threat intel
DFAS takedown: French authorities have seized a dark web marketplace catering to French-speaking users. The Dark French Anti System, or DFAS, was established in 2017 and had more than 12,000 registered users. It sold drugs, hacking tools, and other criminal services. Authorities took control of servers and arrested two suspects, the site's admins and a registered user. This is the fifth French-language dark web platform seized by French authorities since 2018. [ Additional coverage in Zataz ] [ h/t Gabriel Thierry ]

Omnipotent extradition battle: The US and Portugal are in an extradition battle over the administrator of RaidForums. Diogo Santos Coelho, known online as Omnipotent, was arrested in the UK in January 2022 at the request of US authorities. He has been fighting his extradition to the US for three years. Coelho claims he will have better family and medical support for his autism condition in Portugal. According to DataBreaches.net , Coelho had a minor court victory last week when a UK judge ruled that US representatives made several procedural errors.
DVD movie leaker sentenced: An employee of a major DVD and Blu-ray company was sentenced to 57 months in prison. Steven R. Hale stole DVDs and Blu-rays of Hollywood blockbuster movies and sold them before their official release. He linked high-quality versions of movies from the Dune, Fast and Furious, and Marvel franchises.
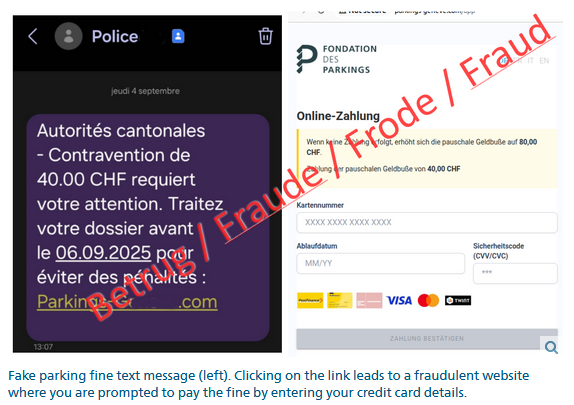
SMS blasters spread to Switzerland: Switzerland's cybersecurity agency says it received reports of SMS spam campaigns that appear to have been sent using SMS blasters. This would mark the first known case of SMS blasters being deployed in the country. Users reported receiving SMS scams about parking fines shortly after visiting that area. All reports of possible SMS blasters came from Western Switzerland. [ Additional coverage in CommsRisk ] [ h/t Steffan S. ]
MAX accounts for sale (already): Hackers are selling access to hacked MAX Russian national messenger accounts for prices of up to $250. Some of the accounts are rented out by the hour. Russian officials say they've already blocked more than 67,000 accounts for suspicious activity, such as spam and sharing malicious files. [ Additional coverage in Kommersant ]
VoidProxy PhaaS: Okta's security team has published an analysis of a new MFA-capable Phishing-as-a-Service named VoidProxy .
Villager abuse: Security firm Straiker reports that an AI-based pen-testing framework named Villager is now being abused in the wild. The tool was developed and released in 2023 by a Chinese threat actor named CyberStrike, which once used to distribute versions of its tools laced with RATs.
Weird SERP poisoning campaign: Fortinet spotted a weird campaign that tries to poison search results for Chinese-speaking users searching for popular software on Google. This is weird because Google is blocked in China, and this likely targets Chinese-speaking users living overseas.
FBI alert on Salesforce attacks: The FBI put out a security advisory [ PDF ] on Friday on UNC6040 and UNC6395, two cybercrime groups engaged in hacks of Salesforce accounts. The former uses social engineering to hack into accounts, while the latter is responsible for the recent Salesloft Drift breach that pivoted to Salesforce accounts.
New npm malware: One hundred fifty-four malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details .
Malware technical reports
ModStealer: Security firm Mosyle has spotted a new infostealer named ModStealer capable of targeting macOS, Linux, and Windows.
DarkCloud Stealer: CyberProof has published a report on the DarkCloud Stealer , an infostealer used in a recent campaign against financial institutions.
HybridPetya ransomware can bypass UEFI Secure Boot: ESET has spotted a version of the NotPetya ransomware that was modified to bypass UEFI Secure Boot. Named HybridPetya , the malware works by installing a malicious EFI application onto the EFI System Partition. HybridPetya was found uploaded to VirusTotal. ESET says there's no telemetry to suggest it was used in the wild.
KillSec ransomware: Resecurity has published a report on the old KillSec ransomware crew and their recent hacking spree targeting Brazilian healthcare orgs.
Akira ransomware: ThreatMon has published a report on the Akira ransomware . This comes after a surge in activity from the group, targeting SonicWall SMA devices.
New Yurei ransomware: A new ransomware group named Yurei has been spotted extorting victims this month. Its dark web leak site currently lists three victims. According to Check Point , Yurei is a minor modification of an open-source ransomware strain known as Prince.
Sponsor section
In this product demo of the Airlock Digital application control and allowlisting solution, Patrick Gray speaks with Airlock Digital co-founders David Cottingham and Daniel Schell.
APTs, cyber-espionage, and info-ops
Sidewinder uses Nepal protests for phishing: Suspected Indian APT group Sidewinder is using the recent Nepalese Gen-Z protests to phish and infect with Android malware whatever is left of the local government.
APT-C-24 (Rattlesnake): Qihoo's security team has spotted a very peculiar APT-C-24 (Rattlesnake) campaign using LNK files as payloads.
"These LNK files use the MSHTA program to execute malicious scripts in remote URLs, which have a distinct characteristic structure and generally end with yui=0/1/2. These scripts are multi-layered and complex obfuscation, which eventually loads the execution attack components in memory to achieve remote control of the target host."
Handala hack-and-leak operation: Canada's cybersecurity agency has published an overview of the recent spat between news outlet Iran International and Iranian APT group Handala Hack. The news org doxed Handala operators in August after Handala leaked personal files from five of its journalists a month before. Canada says Iran's intel agency used an extensive network of AI-powered social media bots to spread its messages.
Kimsuky's use of AI: South Korean security firm Genians has published a report on the Kimsuky APT's (ab)use of AI tools for its operations. This includes the use of ChatGPT to generate text, the use of AI tools to generate deep fake images of South Korean military agency ID cards, and the use of AI to generate malicious scripts.
TikTok info-ops summary: TikTok has published its monthly report on covert influence operations the company has spotted on its platform in July this year. The company took down influence networks targeting political discourse in Thailand, Ukraine, and Azerbaijan. It also took down networks targeting audiences with info-ops related to the Israel-Palestine and Russia-Ukraine war.
Rwanda info-ops: Something that I recently found buried deep in my bookmarks (oops, sorry!) is this one-year-old report on a Twitter influence operation in support of Rwanda's President Paul Kagame.
"Involved at least 464 accounts and issued over 650,000 messages since January 2024, with output accelerating over time. Made extensive use of AI, through the integration of large-language models (ChatGPT) and AI-generated imagery. Centralized and coordinated messaging, but decentralized account operation to a large set of individual posters."
Vulnerabilities, security research, and bug bounty
Samsung patches zero-day: Samsung has patched a zero-day ( CVE-2025-21043 ) in the Android OS version that ships with its devices. The vulnerability was part of an exploit that targeted WhatsApp users. A similar zero-day was also patched in Apple phones. The exploit chain was used to deploy spyware on targeted devices.
DELMIA Apriso exploitation: Hackers are exploiting a recent vulnerability in the DELMIA Apriso manufacturing line management platform. Active exploitation began this month after the bug was patched in June . The software is typically installed in factories, and a successful compromise could be used for IP theft, sabotage, or ransomware. The bug, tracked as CVE-2025-5086, was also added to CISA's KEV catalog.
Kiosk card bug lets hackers generate money: A vulnerability ( CVE-2025-8699 ) in NFC cards used with self-service payment kiosks can let threat actors generate funds on the cards. The exploit works because the funds balance is stored on the card and not in a remote online database. NFC cards for KioSoft kiosks are vulnerable. The company has released a firmware patch to address the issue. KioSoft also plans hardware changes, with secure cards and new card reader components. [ Additional coverage in SecurityWeek ]
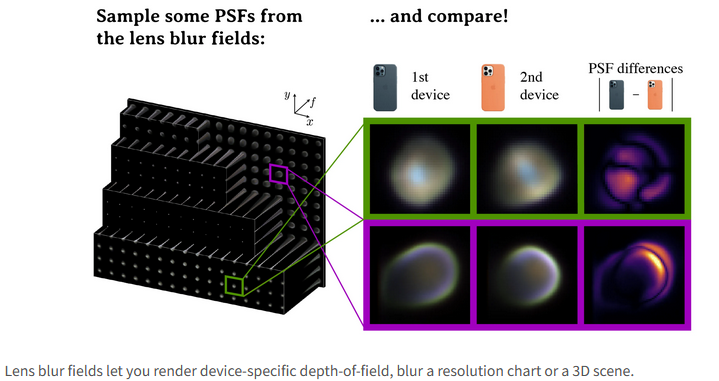
Lens blur patterns can identify cameras: Smartphone cameras produce different lens blur patterns that can be used to individually identify and track devices. Called a lens blur field , the effect is described as a camera fingerprint. The fingerprint, discovered by a team of academics, can be used for forensic and other investigative purposes.
Infosec industry
Threat/trend reports: Check Point , CyFirma , and HP Wolf Security have recently published reports and summaries covering various threats and infosec industry trends.
New tool—wpswag: Security firm SensePost has released wpswag , a utility to read a WordPress REST definition and generate an OpenAPI/Swagger v3 spec. [ h/t Dominic White ]
New tool—WSASS: Red teamer Two Seven One Three has released WSASS , a tool to dump LSASS with Windows Error Reporting on Windows 11.
New tool—sneaky_remap: Red teamer Stuart McMurray has released sneaky_remap , a tool to hide the name of a loaded shared object file (library) on Linux.
New tool—Raw Disk Parser: Workday has open-sourced Raw Disk Parser , a Python script to dump sensitive and restricted files (SAM, SYSTEM, NTDS.dit) directly from the physical disk and without triggering alerts.
New tool—Synthient proxy database: Security firm Synthient has launched a free-to-use and searchable online database of known proxy IPs.
Risky Business podcasts
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about the Salesloft Drift incident. It is a great example of the sprawling impact that the breach of a single service provider can have. We expect these single-compromise-large-blast-radius attacks will become the new norm.
In this edition of Between Two Nerds , Two Nerds Tom Uren and The Grugq talk about the trend toward outrageously complicated exploits and what it means for hacking and cyber espionage.
