Risky Bulletin Newsletter
September 03, 2025
Risky Bulletin: YouTubers unmask and help dismantle giant Chinese scam ring
Written by

News Editor
This newsletter is brought to you by Push Security . You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed .
Two YouTube channels named Scammer Payback and Trilogy Media played a crucial role in unmasking and identifying members of a giant scam network that stole more than $65 million from US seniors.
The US Department of Justice used videos posted by the two channels in 2020 and 2021 to identify and then track down the network. Officials arrested 25 of the 28 suspects they identified during this investigation.
The group allegedly used call centers based in India to call US seniors, posing as government officials, bank employees, and tech support agents.
The agents used psychological manipulation and a sense of urgency to trick victims into granting them access to their computers. They used this access to convince victims that they received mistaken refunds, which they needed to return.
Victims were told to send the cash to addresses where members of the Chinese group would pick it up and later launder it within their network.
The YouTubers went to these addresses and often confronted the group's money mules on camera. The DOJ says the raw, unedited footage of these encounters helped them identify the suspects, most of whom were located in Southern California.
Officials say they've tracked down over 2,000 so far, including a San Diego woman who lost her entire life savings to one of the scams.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
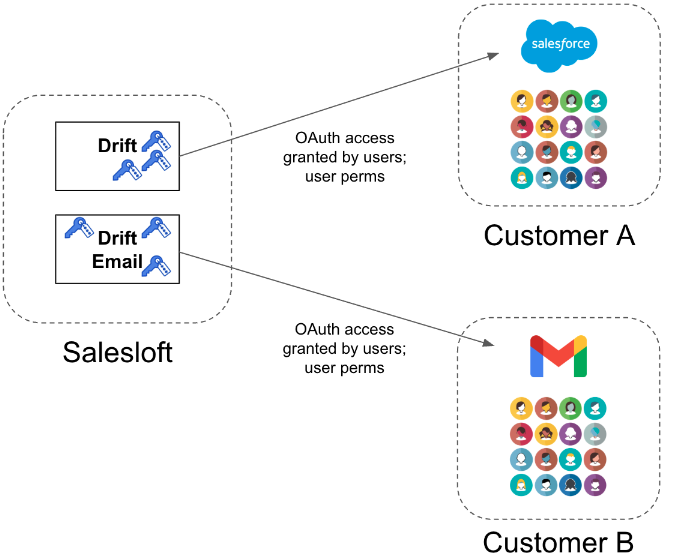
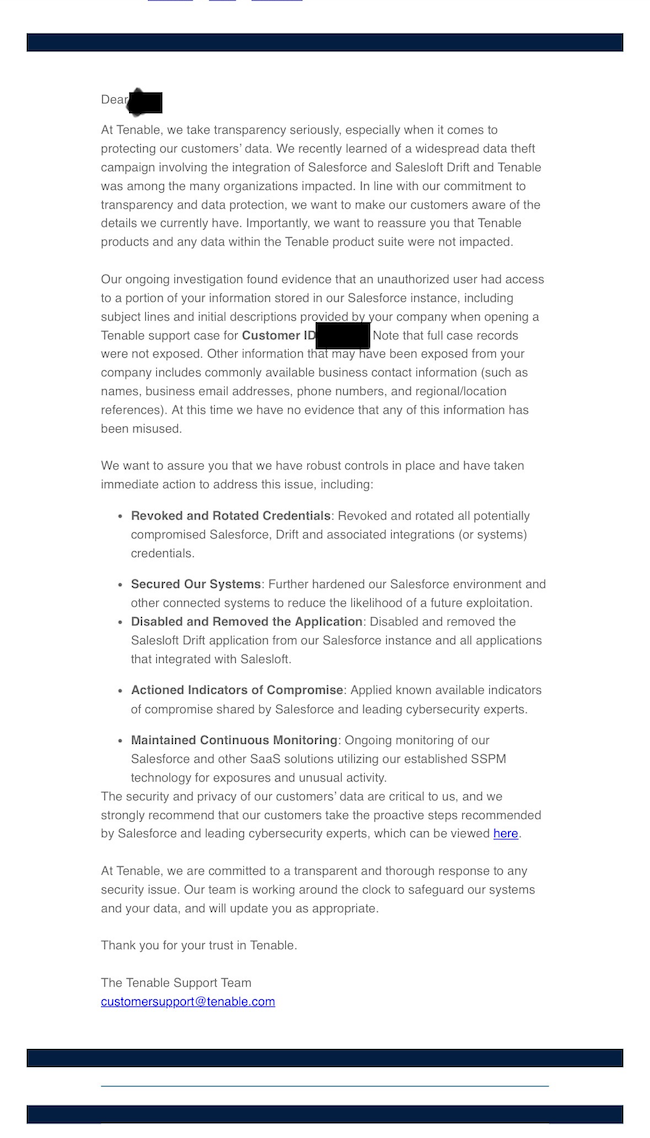
Salesloft hack impacts Zscaler, PAN, more: Victims of the Salesloft hack from last month are starting to notify their customers after hackers used the Salesloft Drift AI chat agent to steal data from their Salesforce accounts. The list of affected companies includes security firms Cloudflare , Zscaler , Palo Alto Networks , Tenable, SpyCloud , and Tanium , along with SaaS platforms PagerDuty and Exclaimer , and cloud platform Cloudinary . These are the first confirmed intrusions. The Salesloft incident is expected to have a much larger impact. [ Additional coverage in HelpNet Security ] [ This item was updated to remove Astrix Security as being affected .]
Google denies Gmail breach reports: Google took a rare step this week and issued a statement denying a breach of its Gmail service after several inaccurate reports last week.
4chan returns after hack: Shitposting board 4chan has returned online after a hack in April.
Bunni crypto-heist: Hackers have stolen $8.4 million worth of crypto assets from decentralized exchange Bunni. The company has paused transactions on Tuesday to investigate the hack. The exploit targeted security vulnerabilities in Bunni's Ethereum-based smart contracts. [ Additional coverage in Coinspeaker ]
Jaguar Land Rover ransomware: A ransomware attack has " severely disrupted " vehicle production at UK automaker Jaguar Land Rover. Retail activities have also been impacted. No threat actor has taken credit for the attack. [ Additional coverage in the BBC ]
Jaguar Land Rover is ransomware, I can see network traffic from infrastructure used by multiple e-crime groups over the past week. They (JLR) appear to be doing contain to eradicate, i.e. all UK border services shut, Windows infrastructure offline etc.
— Kevin Beaumont (@gossithedog.cyberplace.social.ap.brid.gy) 2025-09-02T14:26:04.000Z
General tech and privacy
EU pauses Google fine: The EU has paused an antitrust fine against Google's advertising unit following lobbying from US officials. [ Additional coverage in MLex ]
This is exactly how it works: @ec.europa.eu declares that the US cannot interfere with EU legislation, but enforcement will be so weak and slow that legislation becomes effectively null and void. The result of @vonderleyen.ec.europa.eu using enforcement as political currency @douwekorff.bsky.social
— Sophie in't Veld (@sophieintveld.bsky.social) 2025-09-02T08:57:59.929Z
Twitter secretly shadow-bans Turkish opposition leader: The fReE sPeEcH platform, aka Twitter, has allegedly shadow-banned Turkey's main opposition leader.
xAI manipulates Grok answers: A NYT investigation found that Musk's xAI company is manually tweaking Grok's answers to push conservative narratives or other of Musk's political views.
"...Mr. Musk and his artificial intelligence company, xAI, have tweaked the chatbot to make its answers more conservative on many issues, according to an analysis of thousands of its responses by The New York Times. The shifts appear, in some cases, to reflect Mr. Musk’s political priorities."
— Justin Hendrix (@justinhendrix.bsky.social) 2025-09-02T10:52:22.537Z
Great story by my colleagues on the constant political realignment of Grok, the generative AI chatbot over on the other site. This change to Grok’s answer about the greatest threat to Western civilization is particularly ironic/meta. Gift link: www.nytimes.com/2025/09/02/t...
— Kashmir Hill (@kashhill.bsky.social) 2025-09-02T13:44:06.866Z
Government, politics, and policy
US, AU, NZ test a Joint Cyber Hunt Kit: The US, Australia, and New Zealand have tested a prototype for a new cyber defense kit. The new Joint Cyber Hunt Kit is designed to connect and help secure any network. The kits are operated by a nine-person team and are intended to be portable and moved to any location in the world. The US is expected to purchase the first systems by the end of this year. [ h/t DeadMongoose ]

DHS reactivates Paragon contract: The US Department of Homeland Security has reactivated a prior contract with Israeli surveillance vendor Paragon Solutions. The contract was put on hold last October by the Biden administration. Paragon will provide its hacking tools to the cyber division of ICE's Homeland Security Investigations unit. The contract is worth $2 million. [ Additional coverage in All-Source Intelligence ]
UK seeks telecom security rules update: The UK government is seeking proposals from the private sector on how it could upgrade security rules for local telcos.
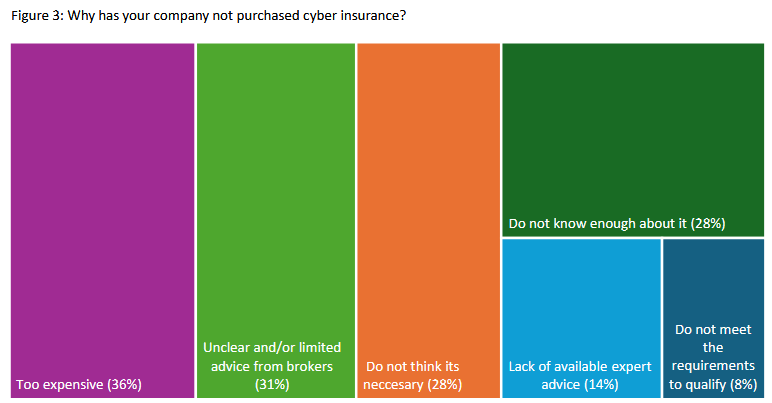
Cyber insurance adoption lags in the UK: A UK government study has found that, despite being aware that cyber insurance exists and is an option, most British companies struggle to understand insurance policy details, which is impeding a broader adoption. [ h/t Ravi Nayyar ]
Digital sovereignty: A study of the digital systems of 58 countries found that many online government services are served and routed from and via foreign networks. A bunch of these networks are also served via HTTP, because of course they are.
EU officials use Signal disappearing messages: According to a Follow The Money investigation, EU officials, including EC President Ursula von der Leyen, use Signal configured with disappearing messages.
EU looks at mandatory age verification: The EU's largest party, the EPP, is seriously looking at a mandatory age-verification mechanism on app stores, social networks, and some online services.
FaceTime in danger in Russia: There are reports in Russian state media that "fraudsters" are now abusing Apple FaceTime to carry out fraud. This is coded language from the Kremlin. They've accused WhatsApp and Telegram of the same thing before blocking the platform's video calling feature last month. In the meantime, Google Meet is still experiencing technical problems , as the Roskomnadzor is looking for ways to block it.
BfV warns of social media recruiting: Germany's Office for the Protection of the Constitution is warning citizens that foreign intelligence agencies are using social media to recruit them as "disposable" agents.
Germany's domestic intelligence service is warning the public about foreign recruitment efforts on social media: "don't become a disposable agent"
— Max Bernhard (@mxbernhard.bsky.social) 2025-09-02T11:35:27.656Z
Sponsor section
In this Risky Business sponsor interview , Casey Ellis chats with Push Security co-founder Jacques Louw. Push's browser plugin gives a unique level of visibility into how users interact with the web and the attacks they face. Jacques talks through what they're seeing and their recently published taxonomy of phishing attacks. It's on GitHub, for everyone to contribute to!
Arrests, cybercrime, and threat intel
Zeppelin ransomware suspect enjoys his freedoms: CyberScoop reports that a Russian national charged with attacks with the Zeppelin ransomware was released on bail shortly after his arrest and is still at large despite multiple run-ins with US police. It's a weird story of how a major ransomware suspect is enjoying freedoms that other cybercriminals charged with the same crimes ever do.
Salesforce IR guide: After two separate waves of hacks that targeted its customer accounts, Salesforce has published a guide on how clients can investigate security breaches.
OldGremlins group returns: An old ransomware group known as OldGremlins has returned with new attacks targeting Russian companies, according to Kaspersky.
Phishing empire evades detection for 3 years: Deep Specter Research has published a report on a phishing group that somehow survived for three years by running infrastructure on Cloudflare and Google servers.
Malicious npm package: Socket Security has found a malicious npm package impersonating the more popular Nodemailer library, and which delivers an infostealer designed to steal crypto-wallet data.
Everyone loves HexStrike: According to Check Point , the release of an AI-powered penetration testing framework named HexStrike has made threat actors salivate on the dark web.
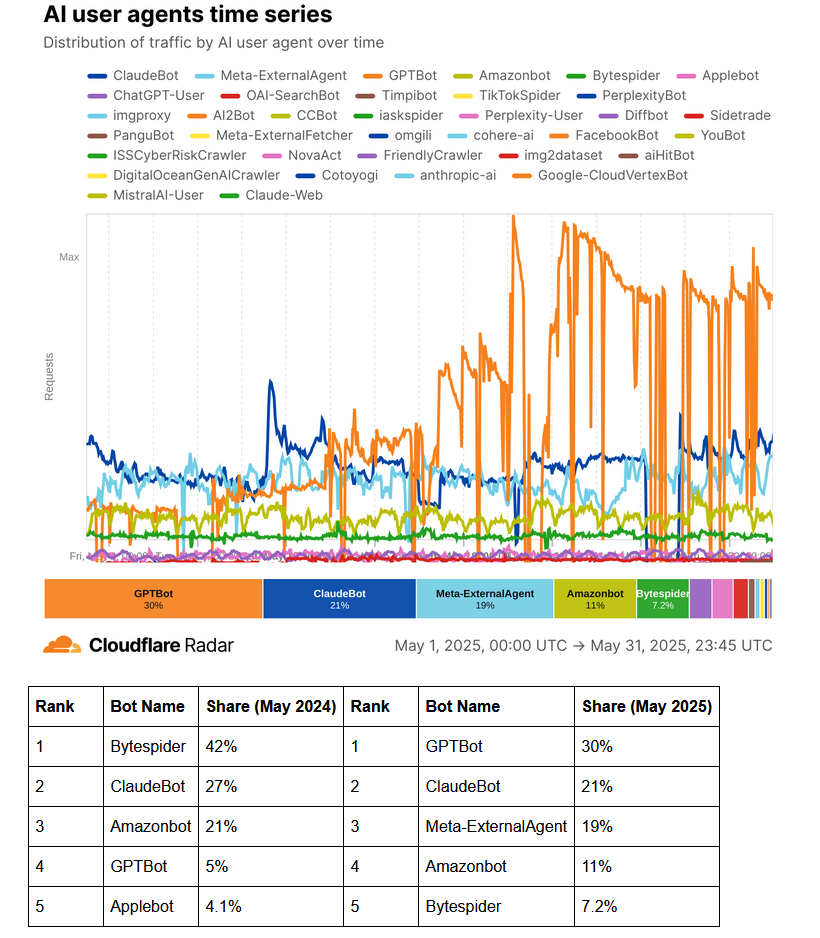
Crawler stats: OpenAI's ChatGPT bot is this year's most aggressive AI crawler, according to Cloudflare stats .
Ollama exposure: Cisco Talos has found more than 1,100 Ollama LLM servers exposed online, with 20% exposing models without authentication.
New DDoS record: Internet infrastructure Cloudflare says it mitigated an 11.5 Tbps DDoS attack. The attack beats the previous DDoS record by more than 4 Tbps (57% larger). Cloudflare says most of the traffic came from Google Cloud infrastructure, and the attack lasted only 35 seconds.
Importance of EDRs and MFA: A report from cyber insurance provider Marsh found that the deployment of EDRs and MFA play a critical role in preventing or containing security breaches. Logging, logon monitoring, security information and event management (SIEM), and security operations center (SOC) capabilities were also deemed critical.
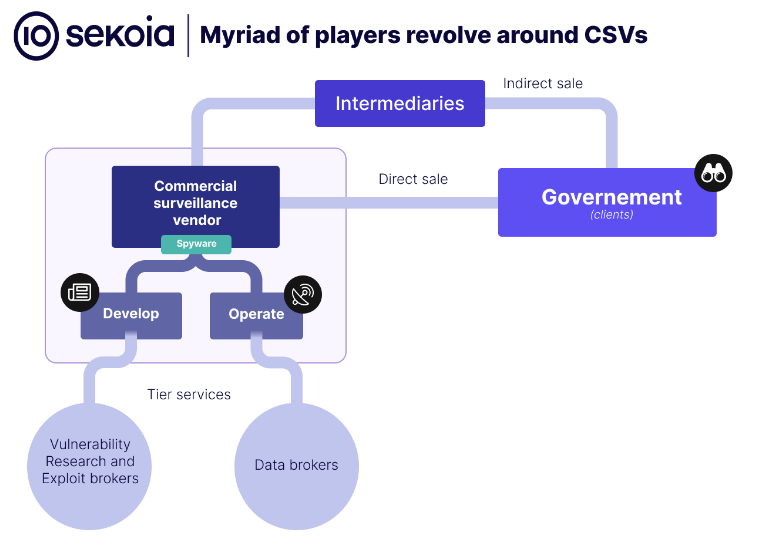
Surveillance vendors landscape: Sekoia has published a top-down look at the market for commercial surveillance vendors (CSVs) and how the market has flourished due to the rising of authoritarianism across the world, driven by the Middle East's desire to contain the Arab Spring popular movement.
"The persistence of CSV activity despite scandals has been made possible by the complexification of their structures, making it more challenging to identify specific business branches responsible for operating or selling the spyware. In addition, CSV relied on the strategy of rebranding to restore their image after public exposure, and to hide the tracks left by their business with autocratic regimes."
Malware technical reports
RapperBot: BitSight has published a technical analysis of the now-defunct/seized RapperBot DDoS botnet.
Phantom Stealer: Russian security firm F6 looks at a new infostealer named Phantom Stealer that is being distributed to Russian and English-speaking audiences using nude-related lures.
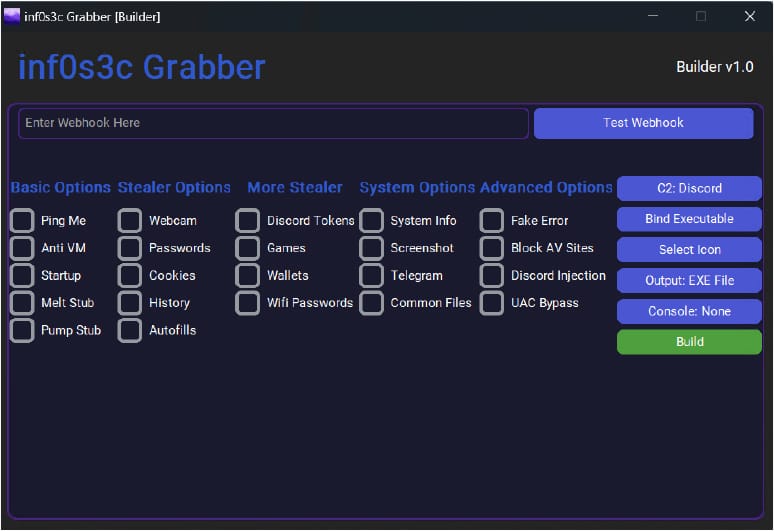
Inf0s3c Stealer: CyFirma researchers have spotted a new Python-based Windows infostealer named Inf0s3c Stealer . The malware appears to have been coded by the same individual behind Blank Grabber and Umbral-Stealer. Both are open-source, but not this one.
Sponsor section
In this wholly sponsored Soap Box edition of the show, Patrick Gray chats with Adam Bateman and Luke Jennings from Push Security. Push has built an identity security platform that collects identity information and events from your users' browsers. It can detect phish kits and shut down phishing attempts, protect SSO credentials, and find shadow/personal accounts that a user has spun up.
APTs, cyber-espionage, and info-ops
Possible APT36 campaign/malware: Nextron Systems looks at a phishing campaign delivering a MeshAgent binary, a legitimate remote administration tool. The phishing campaign is similar to past APT36 Operation Sindoor operations from earlier this year.
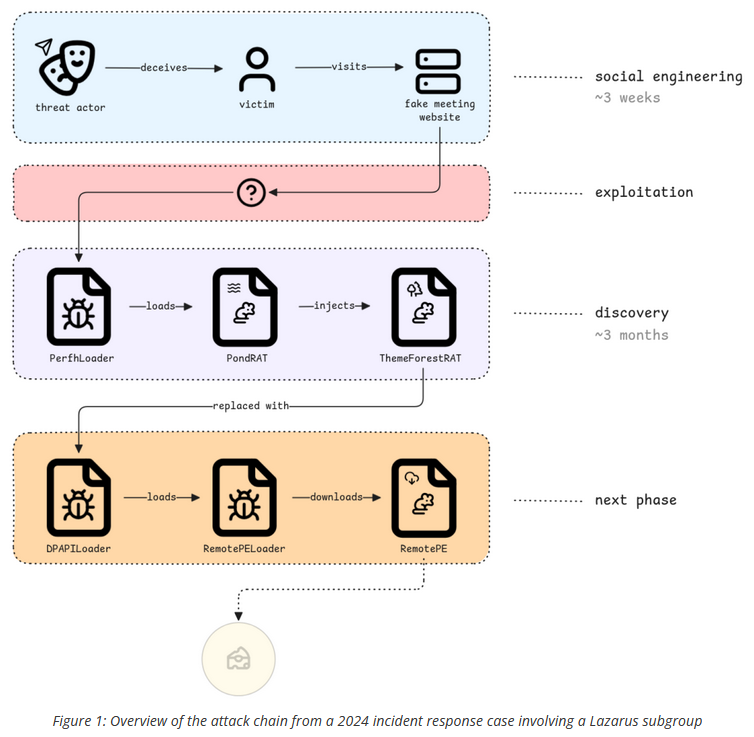
Three Lazarus APT RATs: FoxIT has published a technical analysis of three remote access trojans—PondRAT, ThemeForestRAT, and RemotePE—deployed by North Korean APTs in the wild.
Vulnerabilities, security research, and bug bounty
Unpatched TP-Link router vulnerability: Chinese company TP-Link has failed to patch a vulnerability in its routers for more than a year. The bug is in a protocol that allows ISPs to manage routers deployed at customer premises, also known as CWMP or TR-069. It allows attackers to take over TP-Link routers remotely via their ISP management ports. TP-Link was notified of the bug in May last year but has yet to release a patch.
Frostbyte10 vulnerabilities: American tech company Copeland has released a firmware update to fix ten vulnerabilities in two of its supervisory controllers. The chips are used to manage energy efficiency inside HVAC and refrigeration systems. The ten vulnerabilities were discovered by security firm Armis and are named Frostbyte10 . They can allow remote access and unauthorized manipulation of device parameters. They can be used to sabotage refrigeration systems, disable emergency functions, and crash equipment.
Pudu Robotics bugs: A security researcher found vulnerabilities that granted them access and control over all robots from Chinese company Pudu Robotics. Pudu allegedly fixed the issues after the researcher started reporting some of the bugs to some of its customers directly.
Infosec industry
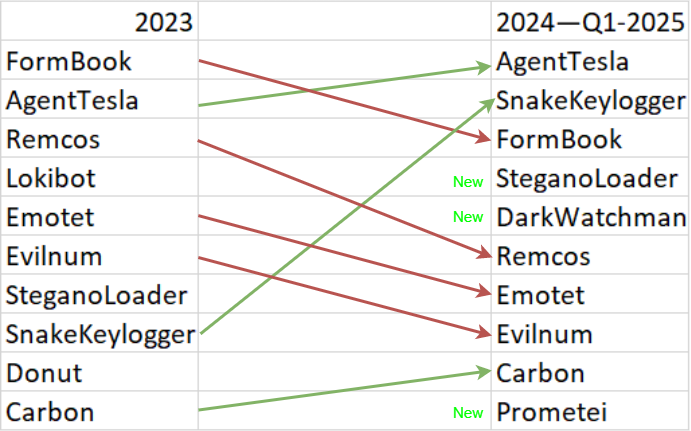
Threat/trend reports: Cloudflare , EU NIS Cooperation Group [ PDF ] , F6 , Marsh , Positive Technologies , Quorum Cyber , and SI-CERT have recently published reports and summaries covering various threats and infosec industry trends.
Acquisition news: Varonis has acquired AI email security firm SlashNext for $150 million.
PHDays 2025: Talks from the Positive Hack Days 2025 security conference, which took place in May, are available on YouTube . PHDays is Russia's largest cybersecurity conference, and all the talks are in Russian.
HackInBo 2025: Talks from the HackInBo Spring 2025 security conference, which took place in early June, are available on YouTube, in two playlists . Some of the talks are in Italian.
New tool—DiffRays: Security firm PwnFuzz has open-sourced DiffRays , an IDA Pro plugin for binary patch diffing.
Infosec drama, part 2334...whatever: Trend Micro has been accused of stealing another company's research on a Microsoft Copilot vulnerability . This has now been " fixed ," with proper credits.
Risky Business podcasts
In this edition of Between Two Nerds , Tom Uren and The Grugq talk about how cyber threat actors are using AI tools to fill in resource and skills gaps that they have.
In this edition of Seriously Risky Business , Tom Uren and Amberleigh Jack talk about proposed legislation that would allow the President to license private sector hackers to go after cybercrime groups. The bill won't pass, but letting hackers loose on industrial-scale scam farms actually makes sense.
